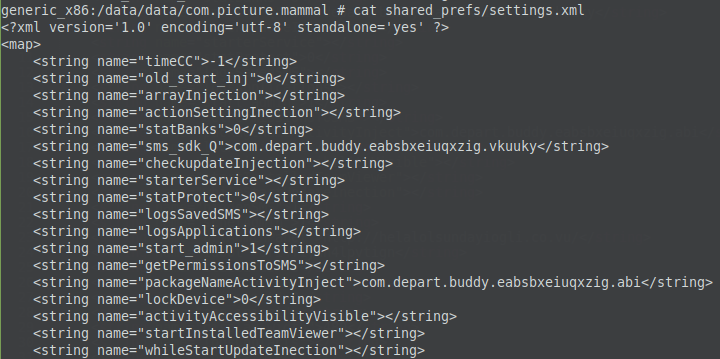
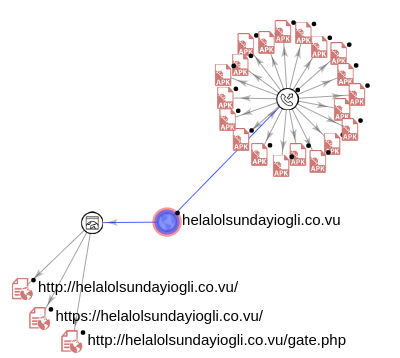
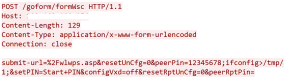
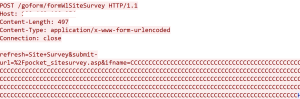
Lots of big news today. SonicWall’s upcoming Boundless 2022 global virtual event continues to rack up record registrations. See the video here and visit this page to register. Then there’s the release of the 2022 SonicWall Cyber Threat Report, which had the best first-day launch in its history. Attention garnered by the annual report toppled all previous company records. In industry news, turmoil in Ukraine ratchets up cyber threat fears, Iranians targeting VMWare, hackers targeting US defense contractors, hackers breaking into Microsoft Teams, and much more.
SonicWall News
Fortune Magazine: Governments worldwide saw a 1,885% increase in ransomware attacks, and the health care industry faced a 755% increase in those attacks in 2021, according to the 2022 Cyber Threat Report released Thursday by SonicWall, an internet cybersecurity company. According to the report, ransomware also rose 104% in North America, just under the 105% average increase worldwide.
The Telegraph (UK): UK ransomware climbed by 227 percent last year, the just-published SonicWall Threat Report also shows, while attempted cyberattacks also reached a record high.
The Register: Public and private sectors are under attack as malware evolution accelerates. SonicWall’s annual cyber-threat report shows ransomware-spreading miscreants are making hay and getting quicker at doing so.
Maddyness (UK): The global spike in ransomware due to the pandemic is alarming; according to the SonicWall Cyber Threat Report, there has been a 62% increase in ransomware globally.
CEPro: Research by SonicWall finds that ransomware attacks more than doubled last year, but IoT malware threats and cybersecurity attacks also continued to climb, hitting 60.1 million such attacks in 2021, the highest number ever recorded by the company in a single year.
Venture Beat: new data released today by cybersecurity vendor SonicWall reveals that the total number of ransomware attacks more than doubled in 2021 — jumping 105% during the year compared to 2020.
TechTarget: According to researchers at SonicWall, who said in its annual threat report that ransomware attacks have grown by an eye-watering 105% over the last year, with 20 attacks being attempted every second.
Charged Retail Tech News (UK): Cybercriminals have targeted the retail sector over the past 12 months, with a 264% surge in ransomware attacks on eCommerce and online retail businesses.
InfoSecurity: According to SonicWall, corporate IT teams were faced with a triple-digit (105%) growth in ransomware attacks last year to over 623 million.
InfoRisk (UK): The massive amount of malware strains that cybercriminals can leverage today enables them to “concoct new cocktails capable of thwarting both past and present security systems,” Bill Conner, CEO and president of cybersecurity firm SonicWall, says.
City AM (UK): Global ransomware attacks doubled to 623m incidents in 2021, with some 91.7m crypto-jacking incidents taking place, up by almost a fifth compared to the previous year, according to a new report from cyber security company SonicWall.
ZDNet: According to an analysis by cybersecurity researchers at SonicWall, the volume of attempted ransomware attacks targeting their customers rose by 105% in 2021 to a total of 623.3 million attempted incidents throughout the year.
ITProPortal: A separate report from SonicWall said that, for the first three quarters of 2021, attempted ransomware attacks grew 148 percent, year-on-year. At the same time, the average ransom demand rose 36 percent to $6.1 million.
Planet Storyline: SonicWall’s 2022 Cyber Threat Report has come to some alarming, but likely unsurprising, conclusions: Pretty much every category of cyberattack increased in volume throughout 2021.
TECHIO: In the latest indicator of just how severe the ransomware problem became last year, new data released today by cybersecurity vendor SonicWall reveals that the total number of ransomware attacks more than doubled in 2021 – jumping 105% during the year compared to 2020.
TechRepublic: The only category to decrease was malware attacks, but SonicWall said in its report that even that number was deceptive.
TechDecisions: SonicWall’s Cyber Threat Report reveals that ransomware volume has exploded over the last two years, rising 232% since 2019.
Information Security Buzz: It’s been confirmed the Red Cross cyber attack was the work of nation-state actors. SonicWall’s latest report, released today, confirms this is not a standalone development, revealing a +1885% and +755% of ransomware attacks on the global government and healthcare sectors, respectively.
HotHardware: The ransomware threat is rising at an alarming rate, and a new report by SonicWall fleshes out the picture. 2020 alone saw 304 million ransomware attacks. As if that wasn’t enough, the doubling of ransomware attacks in 2021 over 2020 amounts to a total of 623 million ransomware attacks globally in 2021. Together, these two years represent a 232% rise in the volume of ransomware attacks since 2019.
MSSP Alert: Nearly all monitored threats, cyberattacks and malicious digital assaults increased in 2021, according to the 2022 SonicWall Cyber Threat Report.
SCMagazine: The healthcare sector saw the largest increase in target IoT malware attacks in 2021, according to the latest annual SonicWall Cyber Threat Report. Compiled from data collected from 1.1 million global sources, researchers saw a 71% increase in IoT malware against healthcare clients.
ReadITQuik: The 2022 SonicWall Cyber Threat Report is now out, announced SonicWall. The report identified a 167% year-over-year increase in encrypted threats, a 6% volume rise in IoT malware, totaling 60.1 million hits by year’s end, as well as a ransomware volume rise of 232% since 2019.
Infopoint Security (De): SonicWall today released their annual Cyber Threat Report for 2022. As the bi-annual report shows, ransomware attacks have increased significantly, with 623.3 million attacks worldwide.
AAS (De): Over 623 million ransomware attacks worldwide – a whopping 105% increase + ransomware attacks up 232% since 2019 + ransomware up a whopping 98% in US and UK respectively.
Industry News
Defense One: US companies, particularly in the defense industry, should be prepared for an increase in cyberattacks aimed at stealing data or disrupting operations due to new aggressive Russian activity aimed at Ukraine, a top Department of Justice official said on Thursday. The remarks come one day after a recent alert from the FBI, National Security Agency, and the Cybersecurity and Infrastructure Security Agency, or CISA, warning that Russian hackers had hit defense contractors and were likely to continue their attempts.
CNN: A high-volume cyberattack that temporarily blocked access to the websites of Ukrainian defense agencies and banks on Tuesday was “the largest [such attack] in the history of Ukraine,” according to a government minister. Speaking at a press conference Wednesday, Ukrainian Minister of Digital Transformation of Ukraine Mykhailo Fedorov added that it is too early to tell who was responsible for the attack. However, officials said the distributed denial of service (DDoS) attack — which bombarded Ukrainian websites with phony traffic — was coordinated and well planned.
The Hacker News: A “potentially destructive actor” aligned with the government of Iran is actively exploiting the well-known Log4j vulnerability to infect unpatched VMware Horizon servers with ransomware. Cybersecurity firm SentinelOne dubbed the group “TunnelVision” owing to their heavy reliance on tunneling tools, with overlaps in tactics observed to that of a broader group tracked under the moniker Phosphorus as well as Charming Kitten and Nemesis Kitten.
Gizmodo: US Intelligence authorities say that a multi-year hacking campaign has resulted in sensitive IT information being stolen from Pentagon-linked defense contractors and subcontractors. According to the report, the goal is to steal sensitive data and information using spear phishing, brute force attacks, credential harvesting, and other typical intrusion techniques. The purpose of the hacking campaigns appears to have been to acquire “sensitive information” about things like US weapons and missile development, intelligence, surveillance, and reconnaissance capabilities, vehicle and aircraft design, and command, control, and communications systems, officials said.
PC Magazine: Hackers have been spotted infiltrating Microsoft Teams meetings to circulate malware to unsuspecting users. Last month, email security provider Avanan noticed the attacks, which involve hackers dropping malicious executable files on Microsoft Teams through in-session chats. “Avanan has seen thousands of these attacks per month,” the company warned in a Thursday report. The hackers are likely infiltrating Microsoft Teams after first compromising an email account belonging to an employee. The email account can then be used to access Teams meetings at their company. Also reported by Bleeping Computer, if you are one of the 270 million people who use Microsoft Teams every day, it may be time to make sure your account is locked down. Part of the onus here does fall on Microsoft, too. Teams isn’t precisely feature-rich when it comes to security and scanning files for malicious content. The ability for guests and other temporary users to share files also poses a security risk, though that isn’t necessarily how the hackers spread this particular malware.
In Case You Missed It