7 Key Security Risks to Address when Adopting SaaS Applications
Infrastructure? Who needs it. The modern organization is ditching traditional on-premise software and related infrastructure in favor of software-as-a-service (SaaS) offerings. SaaS provides attractive and often essential options for reducing CapEx, operational overhead and decreased deployment time — all of which translate into increased business agility.
But the increased agility isn’t without risks. Eager to keep projects moving, many internal business units will procure new SaaS applications without the guidance or approval of appropriate IT or security teams. Multi-SaaS organizations are often left to manage, protect and report on each SaaS service separately, further increasing risk with inconsistent security policies.
If your business is deploying more and more SaaS applications, be on the lookout for these seven primary security risks to understand where proper SaaS security should be applied.
-
Phishing is still a threat.
Email remains the most common threat vector with over 90% of the successful cyberattacks starting with a phishing email. Cybercriminals use phishing email to trick victims into delivering payloads using malicious attachments or URLs, harvest credentials via fake login pages, or commit fraud through impersonation.But modern phishing attacks also are increasing in sophistication and are often highly targeted.
In addition, phishing has evolved to cloud-based attacks as organizations continue to accelerate the adoption of SaaS email (e.g., Office 365 or G Suite) and other productivity apps. Cloud applications present the next frontier for phishing since users need to authenticate to access their accounts, and the authentication is driven through industry-standard protocols, such as OAuth.
For example, cybercriminals targeted O365 with highly sophisticated phishing attacks — including baseStriker, ZeroFont and PhishPoint — to bypass Microsoft security controls. Many secure email gateways, such as Mimecast, also could not stop these phishing emails.
In another case, Google’s Gmail suffered a mass phishing attack in 2017 with an authentic-looking email that asked for permission and opened access to their email accounts and documents. The attack exploited Google’s OAuth protocol.
-
Account takeovers open the door.
Account takeover (ATO) attacks involve threat actors compromising an employee’s corporate credentials by either launching a credential phishing campaign against an organization or buying credentials on the Dark Web due to third-party data leaks. A threat actor then leverages the stolen credentials to gain additional access or escalate privileges. It is possible that a compromised account may remain undiscovered for a long time — or never be found at all.
-
Data theft still profitable no matter where it’s stored.
The risk of data breach is a top concern for organizations moving to the cloud. Sanctioning SaaS applications implies moving and storing data outside the corporate data center, where the organization’s IT department does not have control or visibility, but is still responsible for data security.The data stored in SaaS applications could be customer data, financial information, personally identifiable information (PII) and intellectual property (IP). Cybercriminals typically initiate a targeted attack or exploit poor security practices and application vulnerabilities to exfiltrate data.
-
Loss of control may result in unauthorized access.
Another risk of moving to the cloud is that the IT department no longer has complete control over which user has access to what data and the level of access. Employees may accidentally delete data resulting in data loss or expose sensitive data to unauthorized users resulting in data leakage.
-
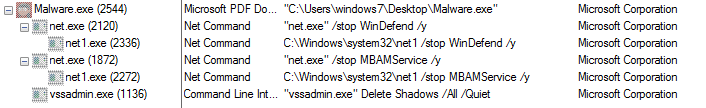
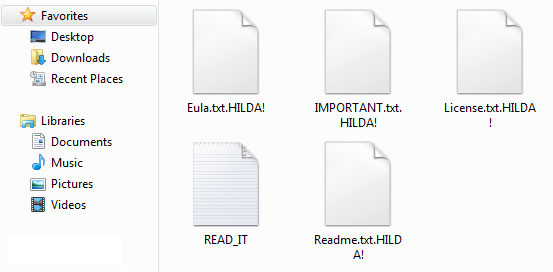
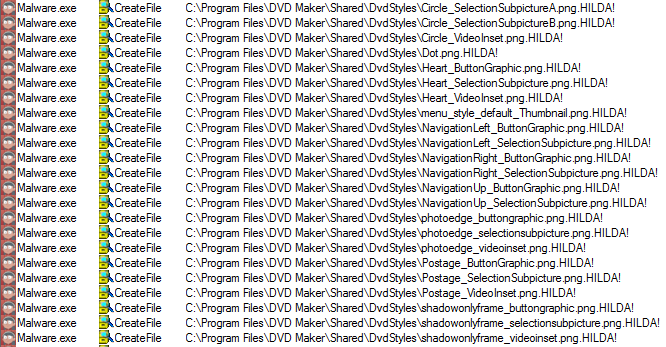
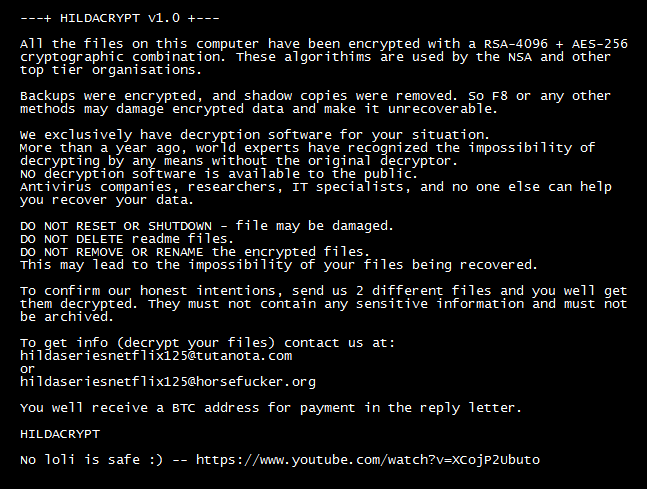
The unknown of new malware and zero-days threats.
SaaS applications, especially file storage and file-sharing services (e.g., Dropbox, Box, OneDrive, etc.), have become a strategic threat vector to propagate ransomware and zero-day malware.According to Bitglass, 44% of scanned organizations had some form of malware in at least one of their cloud applications. Attacks taking place within SaaS environments are difficult to identify and stop as these attacks can be carried out without users’ awareness.
One advantage of using SaaS applications is that the files and data automatically sync across devices. This can also be a channel for malware to propagate. The attacker would only have to upload a malicious PDF or Office file to the file-sharing or storage SaaS apps; the syncing features would do the rest.
-
Compliance and audit.
Government mandates, such as GDPR, and regulations for industries such as healthcare (HIPAA), retail (PCI DSS) and finance (SOX) require auditing and reporting tools to demonstrate cloud compliance, in addition to data protection requirements. Organizations must make sure sensitive data is secured, deploy capabilities to log user activities and enable audit trails across all sanctioned applications.
-
The threats within.
When it comes to security, employees are often the weakest link. Insider threats don’t always include malicious intent. User negligence can result in the accidental insider attack, which remains a top risk for organizations of all sizes. This risk isn’t isolated to weak passwords, shared credentials or lost\stolen laptops. It extends to data stored in the cloud, where it can be shared with external sources and often accessed from any device or location.
The darker side of insider threats includes malicious intent. Insiders, such as staff and administrators for both organizations and CSPs, who abuse their authorized access to an organization’s or CSP’s networks, systems and data can cause intentional damage or exfiltrate information.
How to secure SaaS applications
Rapid adoption of SaaS email and applications, coupled with continuous technological advances, has resulted in multiple options for securing both SaaS email and data.
Geared toward the large enterprise, security vendors introduced Cloud Access Security Brokers (CASB) as a solution providing visibility, access control and data protection across cloud computing services using a gateway, proxy or APIs.
While traditional CASBs provide robust capabilities for the large enterprise, this isn’t always practical for every organization. In additional to being costly — with often complex deployments — few CASBs provide email security for SaaS-based email like Office 365 Mail and Gmail, leaving organizations to implement and manage separate security controls.
Expanded adoption of SaaS email and applications across organizations has created a need for an affordable, easy-to-use SaaS security solution. Thankfully, there are some approaches that can help close or eliminate new risks caused by SaaS applications.
Secure Your Entire Cloud Office Suite, Including Office 365 or G Suite
For example, SonicWall Cloud App Security (CAS) combines advanced email protection and data protection for SaaS email and applications. This approach delivers advanced threat protection against targeted phishing attacks, business email compromise, zero-day threats, data loss and account takeovers.
Cloud App Security also seamlessly integrates with sanctioned SaaS applications using native APIs. This approach provides email security and CASB functionalities that are critical to protecting the SaaS landscape and ensure consistent policies across the cloud applications being used.
When used with Capture Security Center Analytics, and integrated with SonicWall next-generation firewalls, Cloud App Security delivers Shadow IT visibility and control through automated cloud discovery.