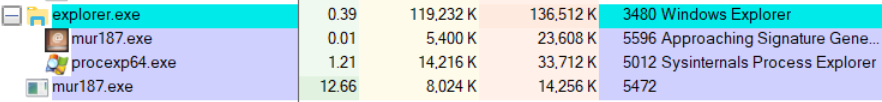
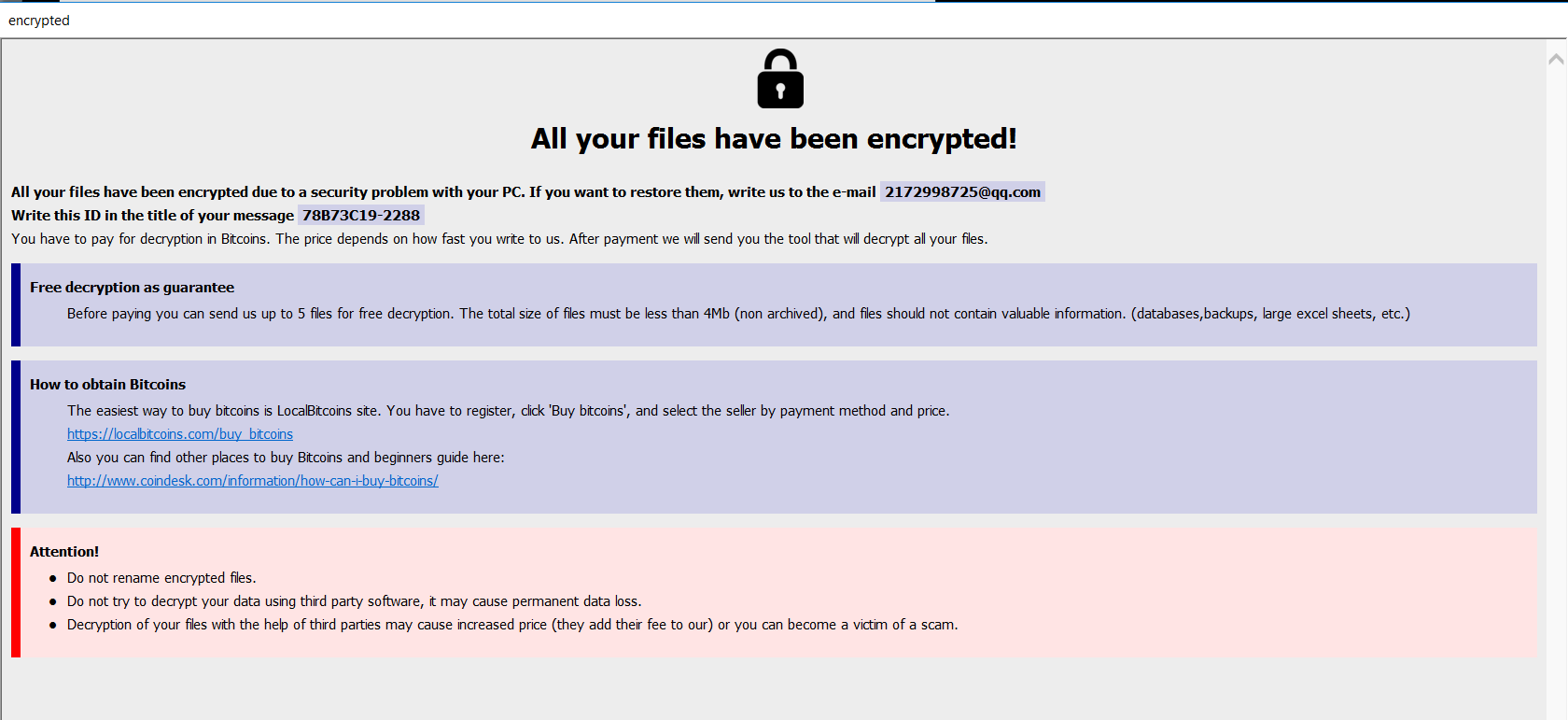
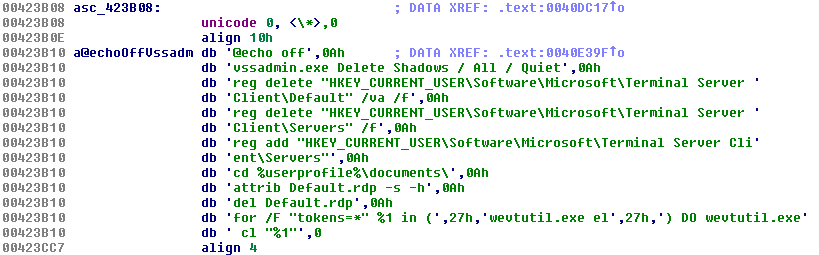
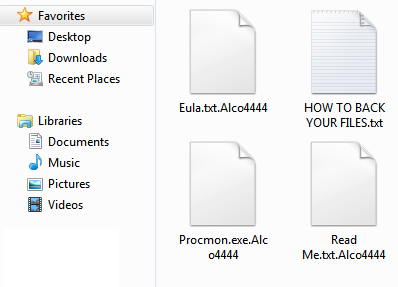
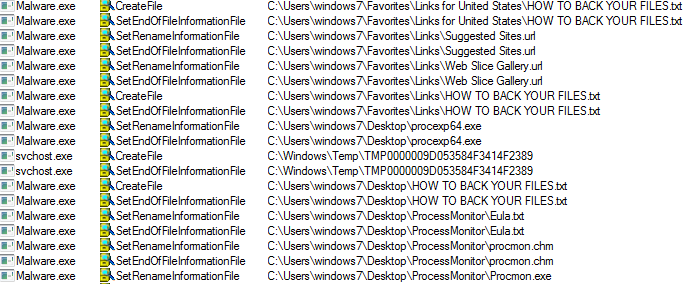
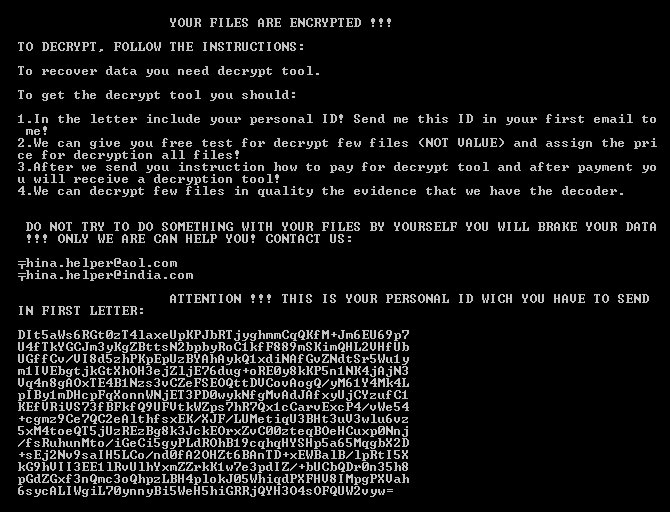
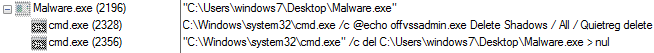SonicWall Capture Labs Threat Research Team has analyzed and addressed Microsoft’s security advisories for the month of August 2019. A list of issues reported, along with SonicWall coverage information are as follows:
CVE-2019-0714 Windows Hyper-V Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2019-0715 Windows Hyper-V Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2019-0716 Windows Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2019-0717 Windows Hyper-V Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2019-0718 Windows Hyper-V Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2019-0720 Hyper-V Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-0723 Windows Hyper-V Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2019-0736 Windows DHCP Client Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-0965 Windows Hyper-V Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1030 Microsoft Edge Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2019-1057 MS XML Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1078 Microsoft Graphics Component Information Disclosure Vulnerability
ASPY 5601:Malformed-File exe.MP.91
CVE-2019-1131 Chakra Scripting Engine Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2019-1133 Scripting Engine Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2019-1139 Chakra Scripting Engine Memory Corruption Vulnerability
IPS 14344:Chakra Scripting Engine Memory Corruption Vulnerability (AUG 19) 3
CVE-2019-1140 Chakra Scripting Engine Memory Corruption Vulnerability
IPS 14345:Chakra Scripting Engine Memory Corruption Vulnerability (AUG 19) 4
CVE-2019-1141 Chakra Scripting Engine Memory Corruption Vulnerability
IPS 14346:Chakra Scripting Engine Memory Corruption Vulnerability (AUG 19) 5
CVE-2019-1143 Windows Graphics Component Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2019-1144 Microsoft Graphics Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1145 Microsoft Graphics Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1146 Jet Database Engine Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1147 Jet Database Engine Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1148 Microsoft Graphics Component Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2019-1149 Microsoft Graphics Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1150 Microsoft Graphics Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1151 Microsoft Graphics Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1152 Microsoft Graphics Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1153 Microsoft Graphics Component Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2019-1154 Windows Graphics Component Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2019-1155 Jet Database Engine Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1156 Jet Database Engine Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1157 Jet Database Engine Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1158 Windows Graphics Component Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2019-1159 Windows Kernel Elevation of Privilege Vulnerability
ASPY 5608:Malformed-File exe.MP.97
CVE-2019-1160 Azure DevOps Server Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2019-1161 Microsoft Defender Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2019-1162 Windows ALPC Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2019-1163 Windows File Signature Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2019-1164 Windows Kernel Elevation of Privilege Vulnerability
ASPY 5602:Malformed-File exe.MP.92
CVE-2019-1168 Microsoft Windows p2pimsvc Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2019-1169 Win32k Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2019-1170 Windows NTFS Elevation of Privilege Vulnerability
ASPY 5603:Malformed-File exe.MP.93
CVE-2019-1171 SymCrypt Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2019-1172 Windows Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2019-1173 Windows Elevation of Privilege Vulnerability
ASPY 5604:Malformed-File exe.MP.94
CVE-2019-1174 Windows Elevation of Privilege Vulnerability
ASPY 5605:Malformed-File exe.MP.95
CVE-2019-1175 Windows Elevation of Privilege Vulnerability
ASPY 5606:Malformed-File exe.MP.96
CVE-2019-1176 DirectX Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2019-1177 Windows Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2019-1178 Windows Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2019-1179 Windows Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2019-1180 Windows Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2019-1181 Remote Desktop Services Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1182 Remote Desktop Services Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1183 Windows VBScript Engine Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1184 Windows Elevation of Privilege Vulnerability
ASPY 5607:Malformed-File dll.MP.5
CVE-2019-1185 Windows Subsystem for Linux Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2019-1186 Windows Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2019-1187 XmlLite Runtime Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2019-1188 LNK Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1190 Windows Image Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2019-1192 Microsoft Browsers Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2019-1193 Microsoft Browser Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2019-1194 Scripting Engine Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2019-1195 Chakra Scripting Engine Memory Corruption Vulnerability
IPS 14340:Chakra Scripting Engine Memory Corruption Vulnerability (AUG 19) 1
CVE-2019-1196 Chakra Scripting Engine Memory Corruption Vulnerability
IPS 14341:Chakra Scripting Engine Memory Corruption Vulnerability (AUG 19) 2
CVE-2019-1197 Chakra Scripting Engine Memory Corruption Vulnerability
IPS 14340:Chakra Scripting Engine Memory Corruption Vulnerability (AUG 19) 1
CVE-2019-1198 Microsoft Windows Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2019-1199 Microsoft Outlook Memory Corruption Vulnerability
IPS 14342:Microsoft Outlook Memory Corruption Vulnerability (AUG 19) 1
CVE-2019-1200 Microsoft Outlook Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1201 Microsoft Word Remote Code Execution Vulnerability
ASPY 5600:Malformed-File doc.MP.47
CVE-2019-1202 Microsoft SharePoint Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2019-1203 Microsoft Office SharePoint XSS Vulnerability
There are no known exploits in the wild.
CVE-2019-1204 Microsoft Outlook Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2019-1205 Microsoft Word Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1206 Windows DHCP Server Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2019-1211 Git for Visual Studio Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2019-1212 Windows DHCP Server Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2019-1213 Windows DHCP Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1218 Outlook iOS Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2019-1222 Remote Desktop Services Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1223 Windows Remote Desktop Protocol (RDP) Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2019-1224 Remote Desktop Protocol Server Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2019-1225 Remote Desktop Protocol Server Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2019-1226 Remote Desktop Services Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2019-1227 Windows Kernel Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2019-1228 Windows Kernel Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2019-1229 Dynamics On-Premise Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2019-9506 Encryption Key Negotiation of Bluetooth Vulnerability
There are no known exploits in the wild.
CVE-2019-9511 HTTP/2 Server Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2019-9512 HTTP/2 Server Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2019-9513 HTTP/2 Server Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2019-9514 HTTP/2 Server Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2019-9518 HTTP/2 Server Denial of Service Vulnerability
There are no known exploits in the wild.