Cyber Security News & Trends – 05-03-19
This week, SonicWall CEO Bill Conner is interviewed by on Federal Tech Talk, the potential of a 5G future is considered, and more details emerge about the Citrix data breach.
SonicWall Spotlight
Federal Tech Talk’ Hosts SonicWall CEO Bill Conner to Examine Cybercriminal Strategies that Threaten Federal Agencies – SonicWall Blog
- SonicWall CEO Bill Conner joins John Gilroy on Federal Tech Talk, a radio show and podcast on the Federal News Network. They discuss emerging cyber threats including attacks over non-standard ports, encrypted threats and malicious PDFs and Office files.
SonicWall Reports Dramatic Rise in Fraudulent PDF Files in Q1 2019 – Tech Observer (India)
- With SonicWall Capture Labs researchers releasing details on the growth of fraudulent PDFs and Office files, SonicWall’s Debasish Mukherjee talks to Tech Observer about how Real-Time Deep Memory Inspection (RTDMI) can detect new malware almost instantly.
Cyber Security News
Cybersecurity: The Key Lessons of the Triton Malware Cyberattack You Need to Learn – ZDNet
- The Triton malware attack of 2017 was unsuccessful but still managed to shut down industrial operations at a critical infrastructure firm in the Middle East. ZDNet explore how real-world physical security problems intersected with cyber security problems and allowed a cyberattack to go very far before being caught.
P2P Weakness Exposes Millions of IoT Devices – Krebs on Security
- Peer-to-peer communications software iLnkP2P includes several critical security flaws that leaves millions of Webcams, baby monitors and more open to a cyberattack.
The Terrifying Potential of the 5G Network – The New Yorker
- While some claim 5G technology will usher in a fourth industrial revolution, there’s a worry that such a huge change could have disastrous effects and policymakers may not be taking the cyber security concerns seriously enough.
“Denial of Service” Attack Caused Grid Cyber Disruption: DOE – E&E News
- A “cyber event” interrupted power grid operations in the western United States on March 5 of this year. Initially details on what happened were scarce but it has now been confirmed that a denial-of-service (DDOS) attack occurred against an unnamed energy company.
Putin Signs Law to Isolate Russian Internet – Financial Times
- Russian president Vladimir Putin signed a law that will allow the Kremlin to disconnect Russia from the global internet. Critics are casting it as an attempt to curb free speech or internal dissent within Russia, but the Kremlin says the law is a cyber security safeguard that would allow the Russian internet to continue running in the event of a hostile cyberattack on its infrastructure.
DC Metro Vulnerable to Cybersecurity Attacks, Says Inspector General – The Hill
- The Washington D.C. Metro has vowed to hire experts to help with cyber security vulnerabilities present in its current systems.
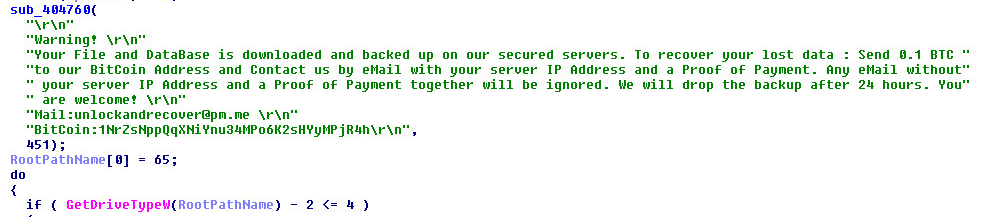
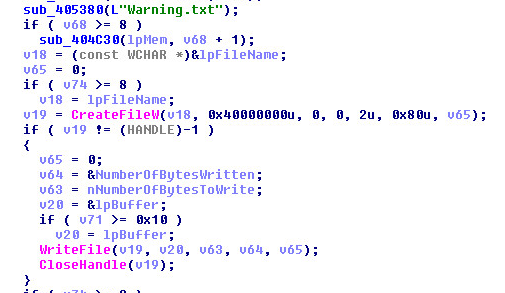
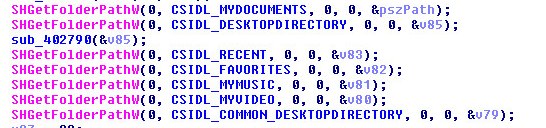
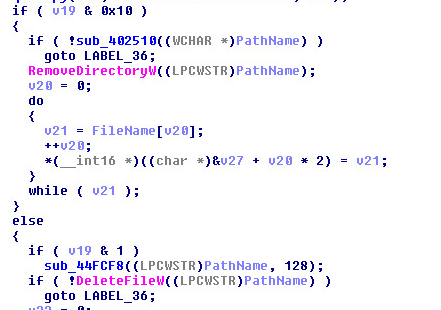
Hackers Lurked in Citrix Systems for Six Months – ZDNet
- The FBI has become involved in an ongoing investigation into an “intermittent” but long-lasting data breach at Citrix. Information on what data was accessed by hackers is not yet known but it is possible that the data stolen includes names, Social Security numbers, and financial information.
Financial Data for Multiple Companies Dumped Online in Failed Extortion Bid – Dark Reading
- 516GBs of potentially sensitive stolen data was dumped online after German digital infrastructure service provider Citycopy refused to pay up in an attempted cyber-extortion attempt. The data dump has not been verified or fully examined yet, but the would-be extortionists claim it includes “financial and private information on all clients include VAG, Ericsson, Leica, MAN, Toshiba, UniCredit, and British Telecom (BT).”
Docker Hub Breach Hits 190,000 Accounts – SecurityWeek
- Docker Hub, the world’s largest library and community for container images, suffered a data breach with 5% of users affected. Usernames and hashed passwords were accessible. Docker says the company breach has now been sealed and that they are working to ensure it cannot happen again.
In Case You Missed It
- Dragonblood Vulnerability: Is your WiFi secure? – Srudi Dineshan
- What to Look for in a CASB Solution – Ganesh Umapathy
- New PDF Fraud Campaign Spotlights Shifting Cybercriminal Phishing Tactics – Dmitriy Ayrapetov
- Stopping PDF Attacks: 5 Ways Users & Organizations Can Work Together – Brook Chelmo
- ‘Chase & Capture’: The Chertoff Group Hosts SonicWall CEO Bill Conner on Latest Podcast – Geoff Blaine