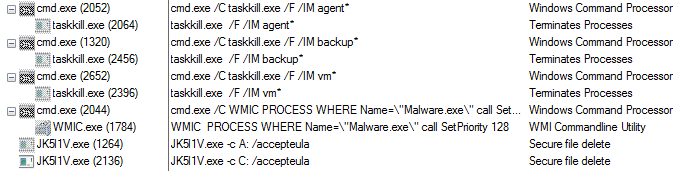
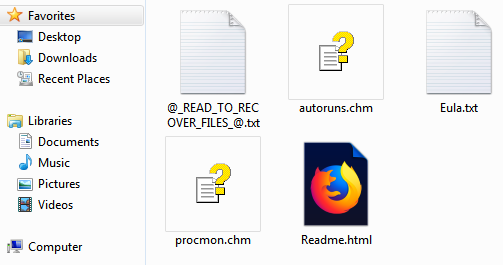
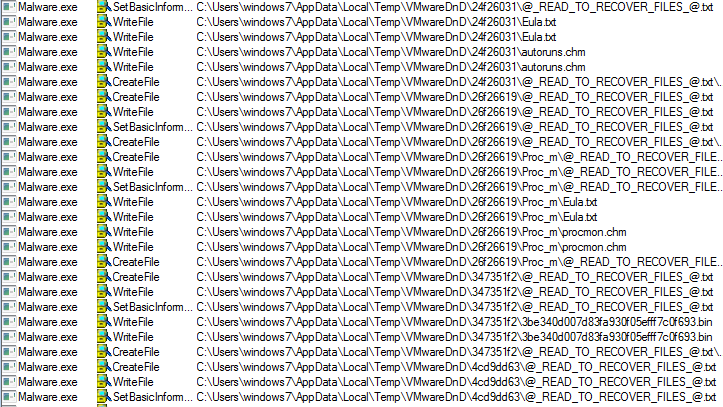
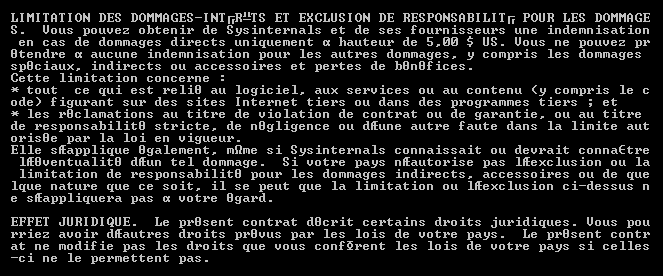
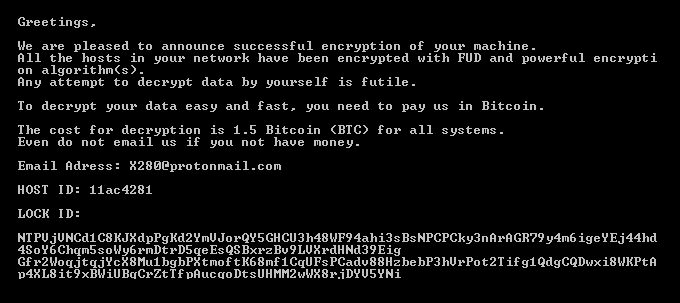
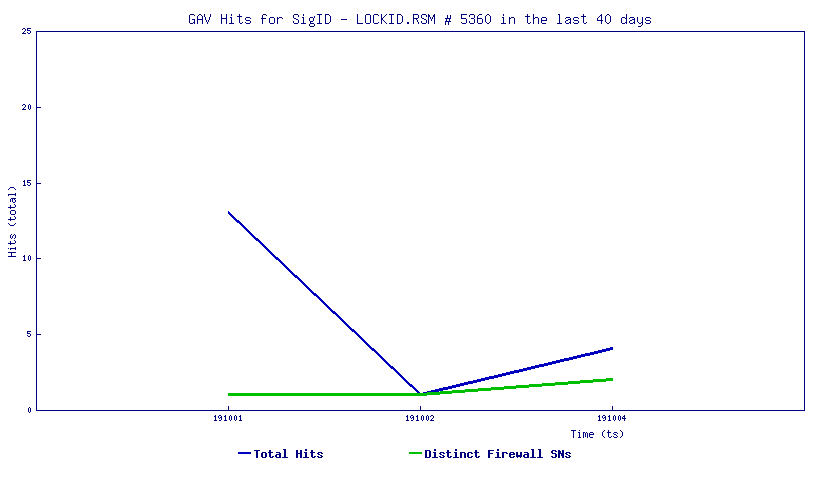
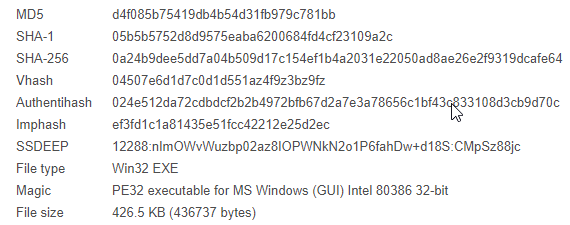
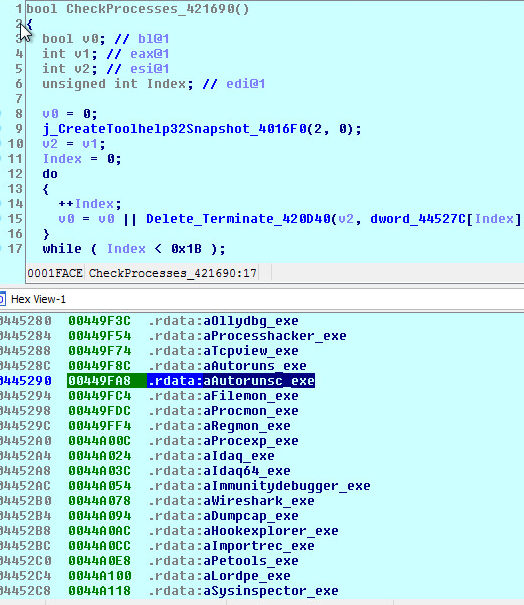
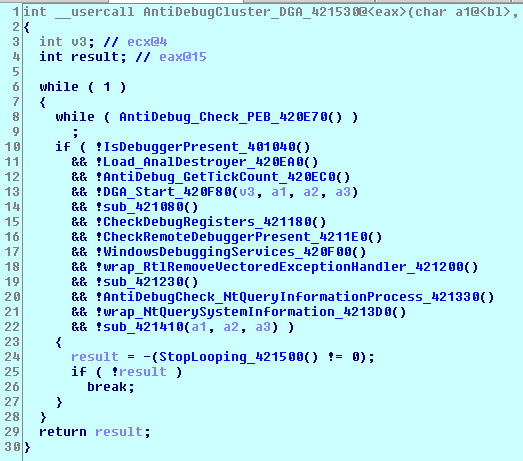
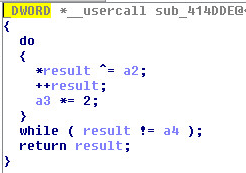
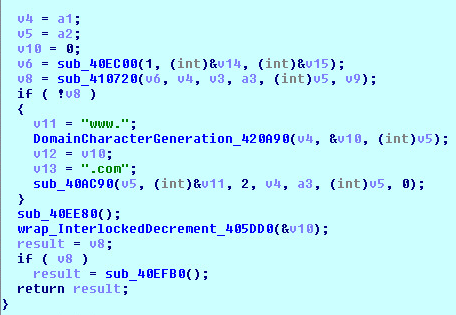
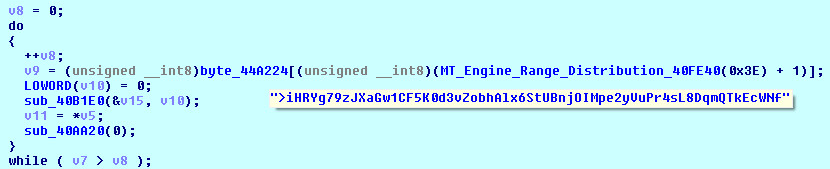
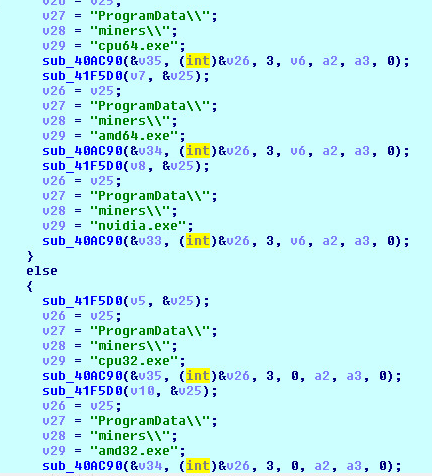
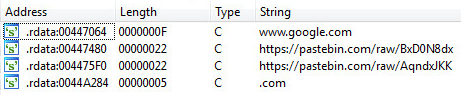
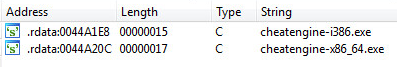
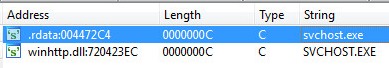
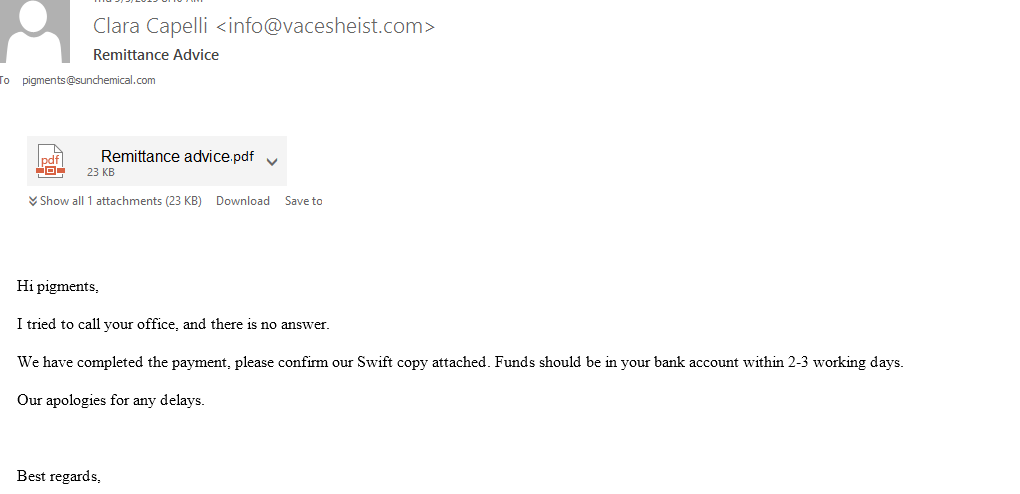
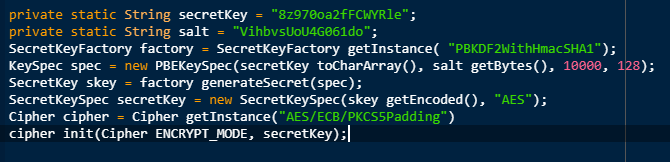
2019 North America Roadshow Series: SonicWall Showcases Complete Cybersecurity Portfolio, Capture Cloud Platform
As a company 100% committed to the channel, SonicWall has a proud, long-held tradition of putting our partners and customers first. Our 2019 North America Roadshow Series is one of our favorite opportunities to get some direct time with our committed partners and provide exciting and useful information to our customers.
This year, we are continuing our roadshow with remaining events taking place Oct. 1 through Dec. 5 in select cities across North America. We’re taking a unique, targeted approach to this year’s roadshow structure, by having separate dedicated sessions for our SecureFirst Partners, and additional demonstrations, meetings and activities opened up to both our partners and customers.

For SonicWall partners
The roadshow will give SecureFirst partners an exclusive opportunity to learn about the future direction of the company, spend valuable time with SonicWall product experts, and learn new ways to build their business. Partners will also get the opportunity to hear valuable feedback from each other and exchange ideas with their local SonicWall team.
In our partner-only sessions we will cover a variety of topics, including:
- Introduction to the complete SonicWall portfolio and the Capture Cloud Platform
- Overview of the newest elements added to the SecureFirst Partner Program
- SonicWall Overdrive, the Partner Marketing Engine
- Promotions and incentives
- Unique insights into SonicWall’s product roadmap
This is an exciting opportunity for our SecureFirst partners to gain insight into our 2019/20 focus areas and go-to-market strategy.
For SonicWall customers
During our roadshow, SonicWall customers will experience an immersive day of practical content, including training and updates, on a variety of valuable areas:
- Introduction to the complete SonicWall portfolio
- Technical demos of Zero-Touch Deployment, Capture Security Center, Secure Wireless, Cloud App Security and Capture Client
- Q&A sessions with SonicWall technical experts
Customers will also get the opportunity to hear valuable feedback from each other and exchange ideas with their local SonicWall team.
We are also delighted to provide meals, entertainment activities and opportunity for business networking during our events, ensuring the day is not only useful, but fun as well. The activities vary for each location. Please check out the registration page for each individual event for more details.
Register now
If you are interested in attending an upcoming roadshow event in North America, please reference the table below and register for a city near you.
| Date | Location | Partners Only | Partners & Customers |
|---|---|---|---|
| October 1 | Los Angeles, CA | Registration Full | Registration Full |
| October 3 | San Diego, CA | Registration Full | Registration Full |
| October 3 | Hartford, CT | Registration Full | Registration Full |
| October 8 | Montreal, QC | Registration Full | Registration Full |
| October 8 | Detroit, MI | Registration Full | Registration Full |
| October 9 | Charlotte, NC | - | Registration Full |
| October 10 | Nashville, TN | - | Registration Full |
| October 10 | Raleigh, NC | - | Registration Full |
| October 10 | Pittsburgh, PA | - | Registration Full |
| October 16 | San Jose, CA | - | Registration Full |
| October 16 | Toronto, ON | Registration Full | Registration Full |
| October 17 | Sacramento, CA | - | Registration Full |
| October 17 | Phoenix, AZ | Registration Full | - |
| October 23 | Denver, CO | - | Registration Full |
| October 24 | Kansas City, KS | Registration Full | Registration Full |
| October 24 | Orlando, FL | Registration Full | Registration Full |
| October 28 | Baltimore, MD | - | Registration Full |
| October 30 | Ashburn, VA | - | Registration Full |
| November 8 | Seattle, WA | - | Registration Full |
| November 12 | New York, NY | Registration Full | Registration Full |
| November 14 | King Of Prussia, PA | - | Registration Full |
| December 5 | Milwaukee, WI | - | Registration Full |
Please note availability is strictly limited and this event is targeted to the SonicWall SecureFirst partner community.
More partner news
Keep up with partner news from SonicWall by following us on social media and by following our dedicated partner-focused Twitter account: @SNWLSecChannel