OBFUSCATED JAVASCRIPT BEING USED BY WSHRAT V2.0
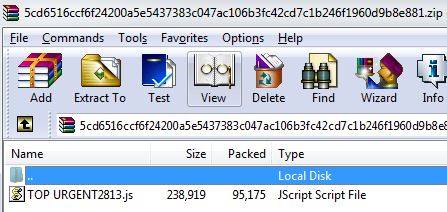
SonicWall RTDMI engine has been detecting obfuscated JavaScript malware files since last two weeks. After analysis, we found that these files belong to WSHRAT malware family. Archive file carries the WSHRAT JavaScript file shown below:
Background:
WSHRAT was first spotted in the wild in year 2013, since then it has been periodically upgrading its Remote Access Trojan (RAT) capabilities. The current version is 2.0, this version information is present in the RAT itself. The programming language used by this malware separates it from other RATs because it has been completely written in JavaScript. The malware has been also written in VBScript.
RAT Capabilities:
- Installing, uninstalling and upgrading itself
- Key logging and stealing passwords
- Downloading, uploading and executing files
- Remote desktop access
- Executing various commands and sending data to the Command and Control (C&C) server.
- Reversing proxy
- Browser’s log stealing
- Process enumeration and termination
- USB drive infection
Persistence:
WSHRAT copies itself in the Startup folder and makes Run entry in the registry. It uses “%temp%\wshsdk\” directory to install its components.
Network:
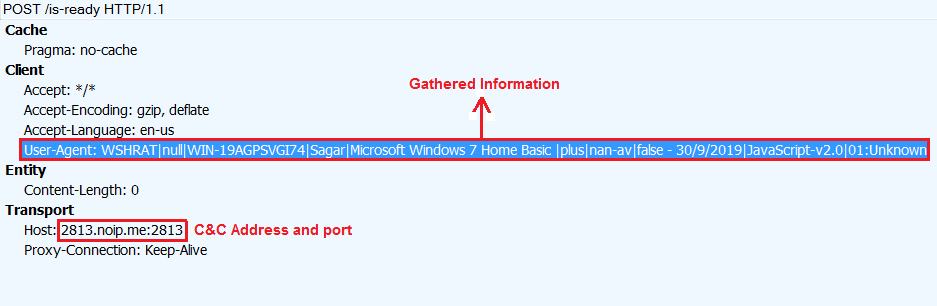
WSHRAT collects and sends system information to its Command and Control (C&C) server. It uses “|” as separator while sending information to the C&C server.
C&C Communication:
WHSRAT supports large number of commands which are listed below.
| Command | Action |
| disconnect | Terminates itself |
| reboot | Reboots the system |
| shutdown | Turns the system off |
| execute | Executes the command using “eval” function |
| install-sdk | If %temp%\wshrat\python.exe file is present, malware sends status “SDK+Already+Installed” else downloads wshsk.zip from “hxxp://2813.noip.me:2813/moz-sdk”. Malware extracts downloaded file into %temp%\wshrat and sends SDK+Installed” message to the C&C server. |
| get-pass | Retrieves and sends specified browser’s passwords to the C&C server. |
| get-pass-offline | Retrieves and send all installed browser’s passwords to the C&C server. |
| Update | Downloads and executes latest JavaScript file from the C&C server. |
| Uninstall | Deletes all the registry entries, Startup entries and all file system traces related to WSHRAT and terminates the execution of malware. |
| up-n-exec | Downloads and executes the specified executable file from the C&C server. |
| bring-log | Sends specified log file to the C&C server. |
| down-n-exec | Downloads and executes the specified executable file from the specified URL. |
| filemanager | Downloads executable file from specified URL and saves it as “fm-plugin.exe”. The malware executes downloaded file with parameters “m-plugin.exe 2813.noip.me 2813 \{Gathered Information}” |
| rdp | Drops rd-plugin.exe, which is present in base64 encoded form inside the WSHRAT JavaScript file. The malware executes dropped file with parameters “rd-plugin.exe 2813.noip.me 2813 \{Gathered Information}\ true (is_offline_flag)” |
| rev-proxy | Drops rprox.exe, which is present in base64 encoded form inside the WSHRAT JavaScript file. The malware executes dropped file with parameters “rprox.exe 2813.noip.me 2813 {filearg}” |
| exit-proxy | Terminates rprox.exe process. |
| keylogger | Drops kl-plugin.exe, which is present in base64 encoded form inside the WSHRAT JavaScript file. The malware executes dropped file with parameters “kl-plugin.exe 2813.noip.me 2813 \{Gathered Information}\ false (is_offline_flag)” |
| offline-keylogger | Drops kl-plugin.exe, which is present in base64 encoded form inside the WSHRAT JavaScript file. The malware executes dropped file with parameters “kl-plugin.exe 2813.noip.me 2813 \{Gathered Information}\ true (is_offline_flag)” |
| browse-logs | Enumerates “wshlogs” directory and sends collected information to the C&C server. |
| cmd-shell | Executes specified command on “Command Shell” and sends the output to the C&C server. |
| get-processes | Enumerates running processes using WMI query (select * from win32_process) and sends process names, process ids and executable paths to the C&C server. |
| disable-uac | Modifies values of EnableLUA, ConsentPromptBehaviorAdmin and DisableAntiSpyware registry keys. The malware acknowledges changes to the C&C server by sending “UAC+Disabled+(Reboot+Required)” message. |
| check-eligible | If specified file present in the system, malware sends “Is+Eligible” message to the C&C server, otherwise it sends “Not+Eligible”. |
| force-eligible | If specified file present in the system, malware executes the file with specified parameters and sends “SUCCESS” message to the C&C server, otherwise it sends “Component+Missing” message. |
| elevate | If the malware is not elevated already, it restarts itself with elevated privileges and sends “Client+Elevated” message to the C&C server. |
| if-elevate | If the malware is elevated, it sends “Client+Elevated” message to the C&C sever otherwise sends “Client+Not+Elevated” message. |
| kill-process | Terminates process attached with specified process id. |
| sleep | Performs sleep operation for the specified time. |
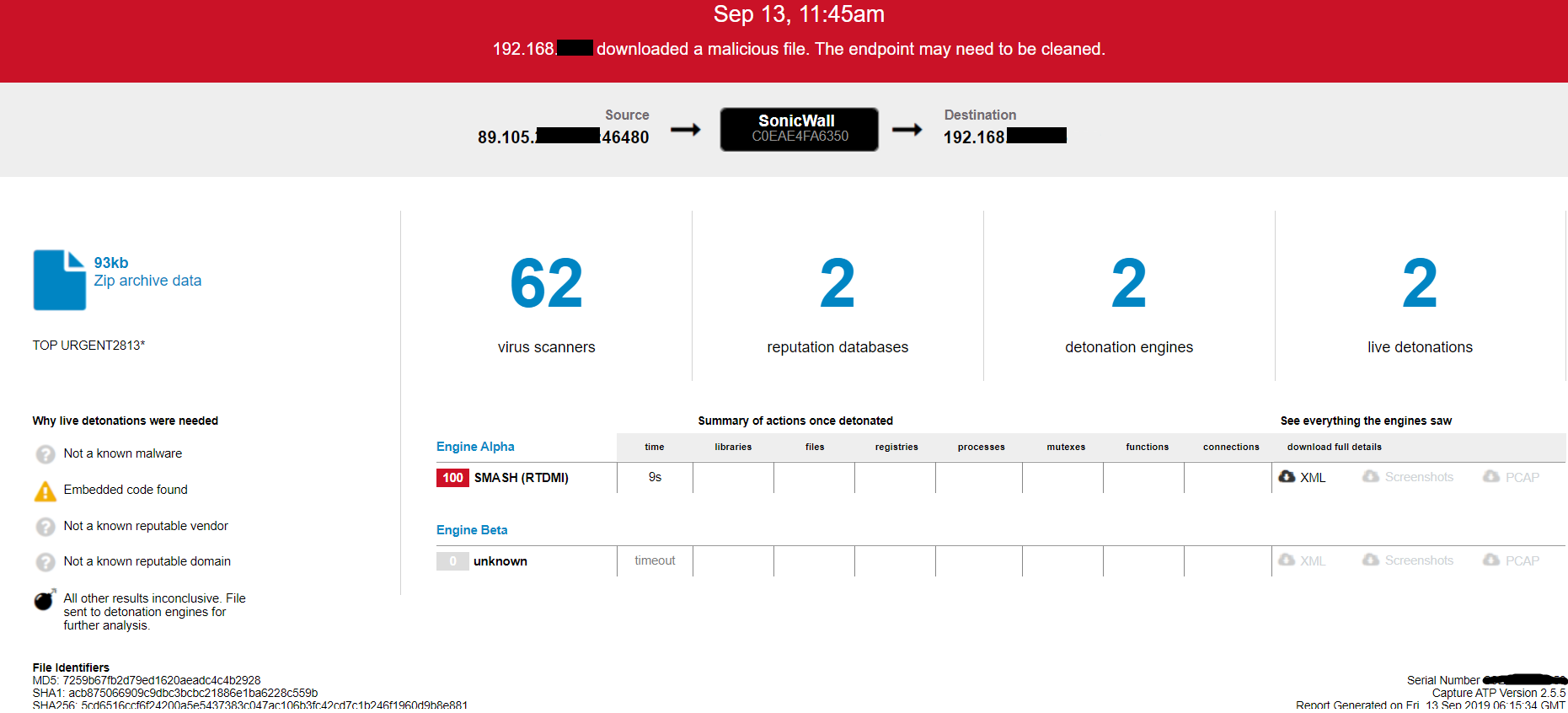
Evidence of the detection by RTDMI engine can be seen below in the Capture ATP report for this file:
Additional Remark:
Please note that the RTDMI engine analyzed and gave us a verdict for these samples as ‘Malicious’ on September 13, 2019 as visible in the report:
Whereas these samples (both the zipped and unzipped versions) were first seen on Virustotal 3 days later – on September 16, 2019 – as evident by the ‘First Submission’ date: