With the cyber security skills gap being a point of contention for closing in on five years now, the managed security services provider (MSSP) industry has responded in kind.
In fact, Gartner predicted that 40 percent of all managed security services contracts will be bundled with other security services and IT outsourcing projects by 2020.
But the fact is, not every IT vendor, distributor or value-added reseller (VAR) is cut out to be an MSSP. For each MSSP that truly adds value in protecting their customers, there are others that fall short of what the cyber security industry — and prospective customers — requires.
I recently attended the MSP Expo in Las Vegas, Nev., to participate on an engaging panel of cyber security experts, including Guy Cunningham, VP of Channel Sales and Alliances at EventTracker; Jonathan Morgan, Director of Security Operations and Development at Area 1 Security; and DV Dronamraju, Managing Director at InfoSecEnforcer.com.
While we were able to collectively field and discuss many of the day’s top questions, I felt it prudent to republish these topics to help a broader audience of existing and future MSSPs.
What should business customers be most concerned about relative to cybersecurity, and why?
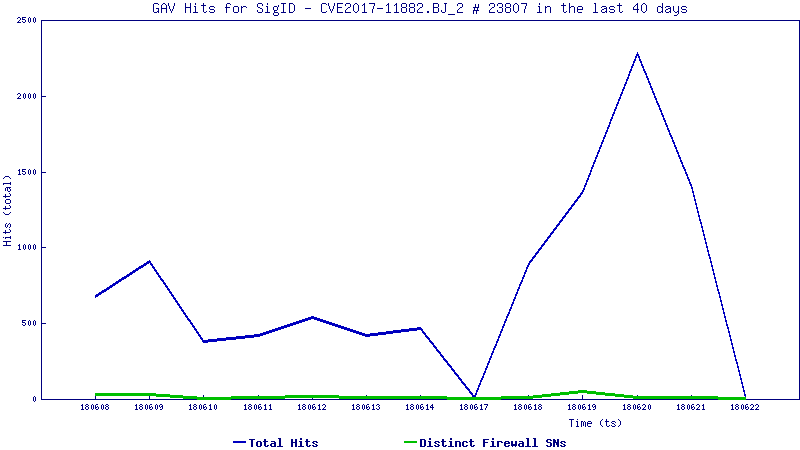
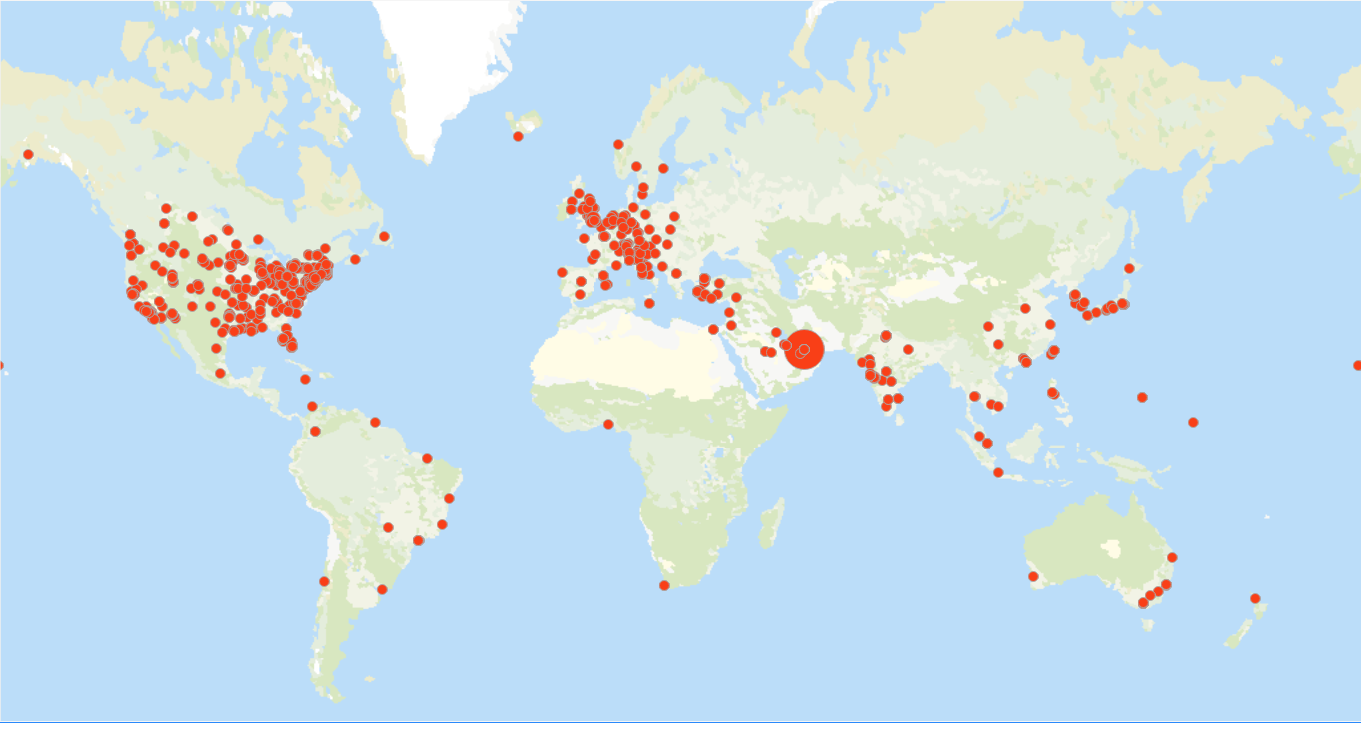
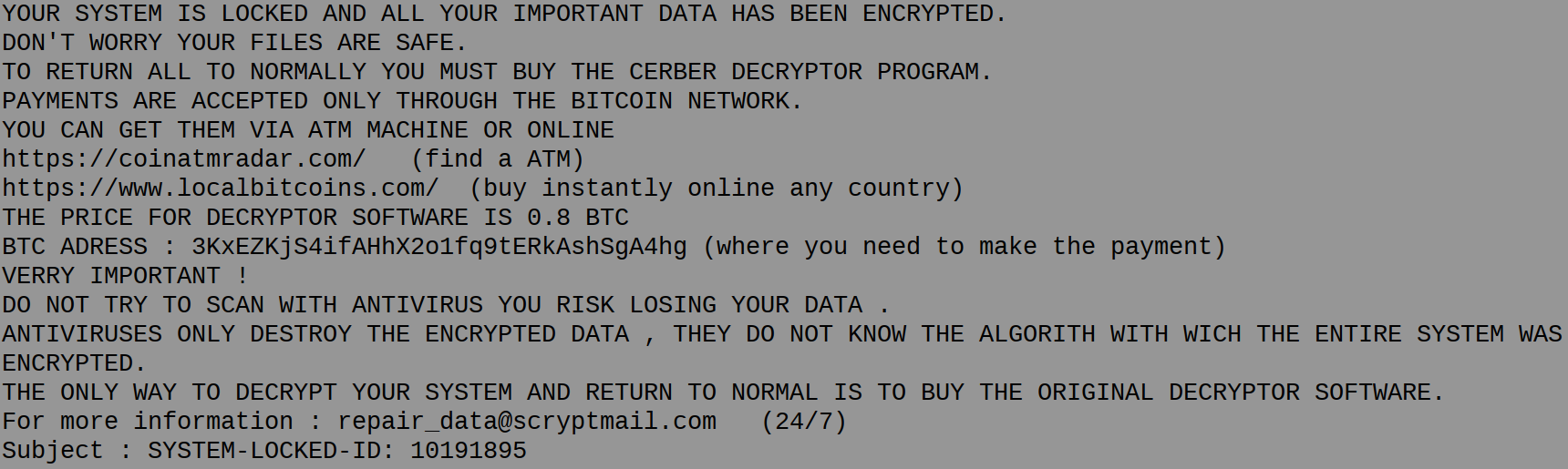
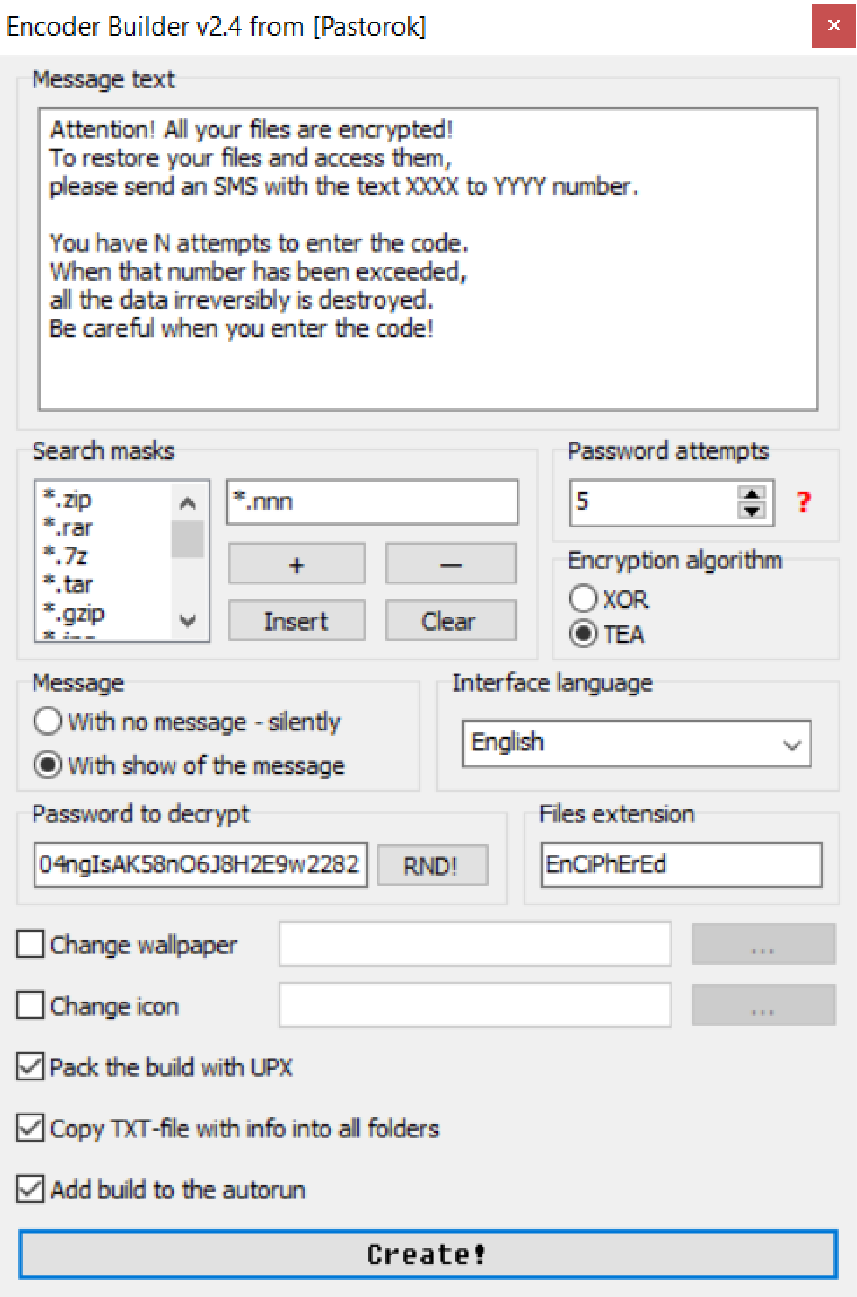
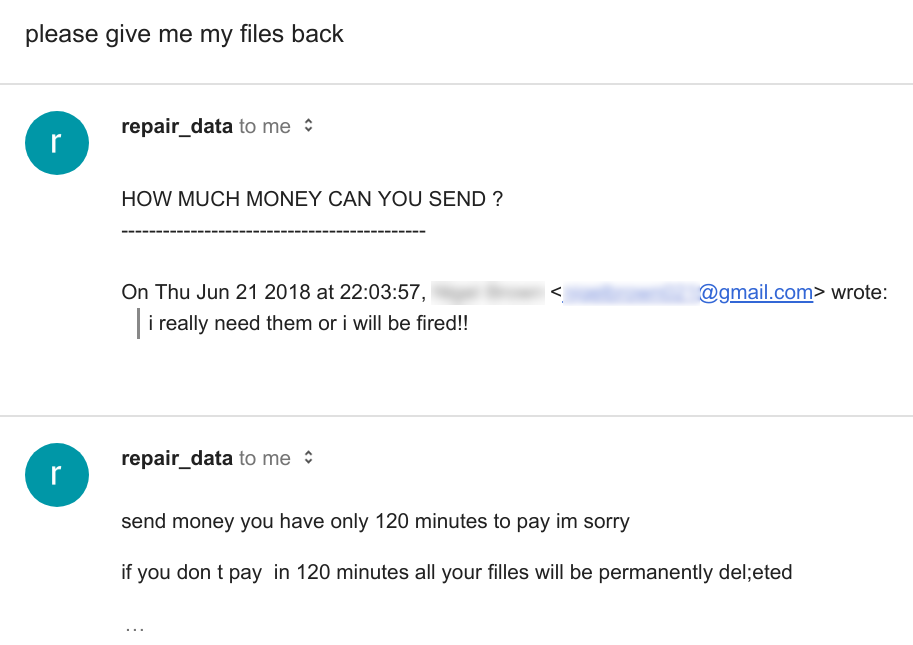
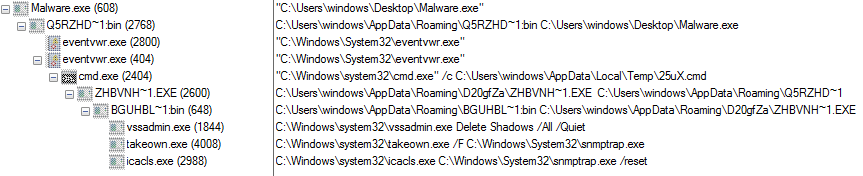
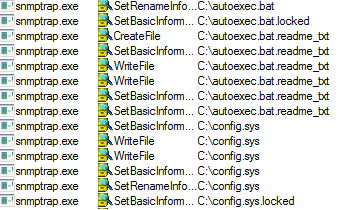
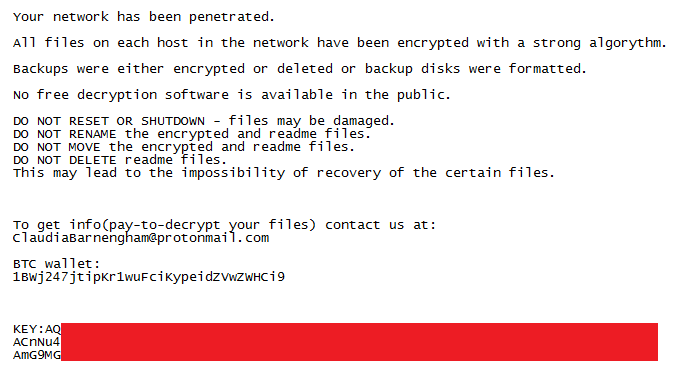
It’s rapidly changing threat landscape. For instance, we are seeing crypto-jacking this year as a new cyber threat. And while ransomware volume was somewhat down in 2017, new threat intelligence already shows a massive 299 percent year-to-date increase in 2018. So, the landscape continues to be agile and cybercriminals are diligent in seeking out new ways to impact organizations.
What can MSPs do to protect their customers from cyberattacks?
It’s important to consistently employ basic best practices: patching, updates, segmentation, etc. For MSP/MSSPs, the reality is that customers need help with this. So, developing services that take care of the basics is a great place to start. From there, you can scale your services and offerings to enhance their security postures.
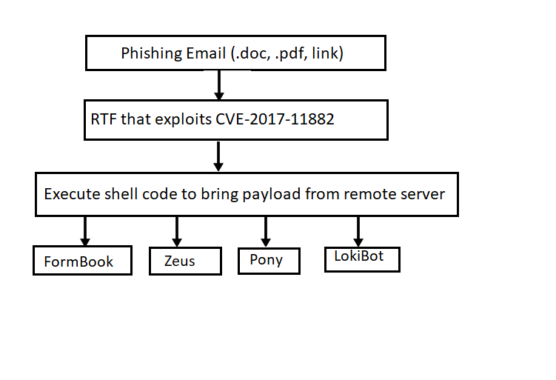
Phishing is the root cause of data breaches and financial losses. How do anti-phishing solutions work?
They’re valuable in a variety of ways, but most email security solutions revolve around maturing the hygiene capabilities of corporate email platforms. Whether deployed on-premise or in the cloud, email security should automatically protect inboxes against links and attachments that are commonly used in phishing attacks.
More advanced offerings will use URL filtering and integrate with cloud sandboxes for protecting against known and unknown malware attacks. So, I believe strongly that we need to work to get advanced email security solutions more widely adopted in the market. Hygiene solutions, which most people think of when they hear security, just isn’t good enough anymore.
What kind of margins do email security solutions offer for MSSPs?
While there are many variables in play here, an MSSP could expect a margin of 10-15 percent for an email security product, or 30-50 percent margins if you provide email security as a service.
Since more than 89 percent of breaches have a financial or espionage motive, how are companies supposed to protect their intellectual property?
At a basic level, organizations should map their data so they know what’s most valuable and requires the most security. Depending on what’s being protected, consider using industry compliance guidelines (e.g., PCI, HIPAA, GDPR, etc.) as a baseline, but understand that compliance does not equal automatic security.
From there, layered strategies should include everything from network security firewalls, endpoint protection, secure email and even protection for remote access workers.
What do Security Information and Event Management (SIEM) solutions do, and why are they important? Aren’t they expensive to buy and difficult to operate?
Anybody who has ever used a SIEM will tell you, much like many cyber security tools, it will depend on the investment — time, staff, technology and resources – you put into it.
At the core, SIEMs help organizations correlate event logs (e.g., endpoint protection, threat intelligence, user information, etc.) to search for patterns based on defined rules. They then provide a correlated output that flags potential risks or threats. They are extremely powerful and give organizations the ability to tune and customize rules for their specific environment(s).
But you have to know what you’re doing. And you have to have strong security engineers to get the most out of a SIEM.
Operationally, some MSSPs leverage a centralized SIEM model (i.e., all customer data flows through a single SIEM), where other MSSPs rely on a decentralized model that leverages whatever SIEM each customer already has in place. In both MSSPs and enterprises, SIEMs are typically used by Tier 1 security operations center (SOC) analysts to monitor alerts and identify events in real time.
How can MSSPs use artificial intelligence and automation to detect threats, trigger alerts, troubleshoot and address security situations?
The reality is that building your own artificial intelligence (AI) capabilities is probably not realistic unless you are a very, very large MSSP. So, ideally, you want to rely on the AI already built in to security products to help you identify and block cyberattacks to protect customers.
For example, SonicWall engineered very smart AI that we integrate into the real-time engines that power our Capture Advanced Threat Protection (ATP) sandbox capabilities. This can allow you to leverage AI without the overhead and complexity of building it yourself. Then you can use an intelligent SIEM to help make sense of the logs and alerts.
Finding and/or developing cyber security talent can be a challenge. There seems to be a constant shortage of affordable, qualified cyber security practitioners. What do MSPs need in terms of technical, sales and support talent?
The key here is retaining the talent that you train. Companies like SonicWall provide entire platforms to train people — both internal staff and partners — on cyber security best practices, products and emerging threat trends. We call it SonicWall University. Our SecureFirst partners can leverage this platform to train their employees, significantly improving value for their customers. It’s best to consistently use engaging tools to train people and then build a culture that makes them want to stay.
How can MSPs provide enhanced security without adding complexity and overhead?
In a way, MSSPs are supposed to take away the complexity and overhead. We talk a lot today about getting the basics right and the transition from MSP to MSSP. Complex, enterprise-class MSSPs have lots of money, but if you are making the transition from MSP, start with taking the burden of the basics off the customer.
Make sure security devices are installed correctly, patched and have good policies. Make sure good endpoint security is deployed and managed. Provide useful reporting so customers know how well they’re doing. Removing the complexity from the customers is absolutely critical to success.
How does compliance figure in to being an MSSP?
This is massively important. A lot of mid-market MSSPs focus almost exclusively on a vertical. We see healthcare-focused MSSP or others targeting financial services (e.g., PCI). Compliance regulations drive need, so focusing on a vertical is definitely an option — particularly for MSSPs that can’t quite scale to solve all security challenges across an untold number of industries.
But especially if you are just starting in the MSSP space, trying to solve all compliance needs is a tough challenge. So, pick your spots when it comes to compliance.
How can MSSPs protect themselves from financial ruin and lost reputation if their customers do experience an outage or breach?
Good question. But the short answer is you have to indemnify yourself. And also have some level of insurance. And make sure your service-level agreements (SLA) make sense.
What kind of security guarantees/SLAs should an MSSP offer?
This is a very broad topic and also very dependent on the services being offered. The key for the market is that you are selling to match up the SLAs in a way you know you can hit. Take response times for rule changes, for example. You can’t promise you’ll have them done in 30 minutes, 24/7, if you don’t have people on staff around the clock.
How can MSSPs differentiate their security offerings in the marketplace?
We touched on this a bit with the challenge of removing complexity for the customer. Strive to make the entire experience transparent and frictionless.
One of my SonicWall colleagues, Conrad Bell, actually penned an outstanding strategy, “Inside the Modern MSSP,” for MSSP Alert. It outlines how proactive MSSPs are adopting bundled, end-to-end approaches for simplifying cyber security for their customers.
Become a SonicWall MSSP Partner
Are you interested in expanding your security offerings? SonicWall offers the dedicated SecureFirst MSSP Partner Program to help you expand your portfolio to include a full range of flexible managed security services built on SonicWall’s robust security platform.
The SonicWall SecureFirst MSSP program offers training, enablement, support and financial benefits designed to help SecureFirst Partners grow their managed security business.
Build your MSSP offerings by implementing SonicWall MSS blueprints, or work with SonicWall to create customized MSS offerings leveraging your existing managed services expertise.