Cybersecurity News & Trends – 11-13-20
This week, SonicWall expanded its Capture Cloud Platform with four new firewalls and a new Zero-Trust security solution.
SonicWall in the News
SonicWall Expands Boundless Cybersecurity With New High-Performance, Low-TCO Firewalls; Company Debuts Cloud-Native Ztna Solution to Secure Work-From-Anywhere Environments — Company Press Release
- SonicWall today announced the expansion of its Capture Cloud Platform with the addition of the high-performance NSa 2700 firewall, three new TZ firewall options, and SonicWall Cloud Edge Secure Access, which delivers easy-to-deploy, easy-to-use zero-trust security.
SonicWall Capture Advanced Threat Protection Collects ICSA Labs Certification — Company Press Release
- For the third consecutive quarter, cloud-based Capture Advanced Threat Protection (ATP) sandbox service has been vigorously tested in the detection of today’s most evasive threats and awarded the coveted ICSA Labs Advanced Threat Defense certification.
The 2020 Tech Innovators Awards — CRN
- SonicWall was recognized as the winner of the networking category for its TZ570 and TZ670 series (slide 22) and was a finalist in the security network category for its Network Security Services Platform 15700 (slide 37).
Cybersecurity Industry in Detroit Is Growing and Mentors Are Starting With Young People — Detroit Free Press
- In an article on how Detroit’s cybersecurity industry is growing, Bill Conner offers cybersecurity tips for more secure remote work.
Four New SonicWall Firewalls Announced — Storage Review
- Storage Review covers SonicWall’s latest launch, focusing on Cloud Edge Secure Access and four all-new firewalls.
SonicWall Research: Ransomware, IoT Malware Attacks On The Rise — MSSP Alert
- In a feature article on SonicWall’s Q3 Threat Data, MSSP Alert spotlights the surge in ransomware and IoT malware.
Industry News
Campari Site Suffers Ransomware Hangover — ThreatPost
- Italian spirits brand Campari has restored its company website following a recent ransomware attack.
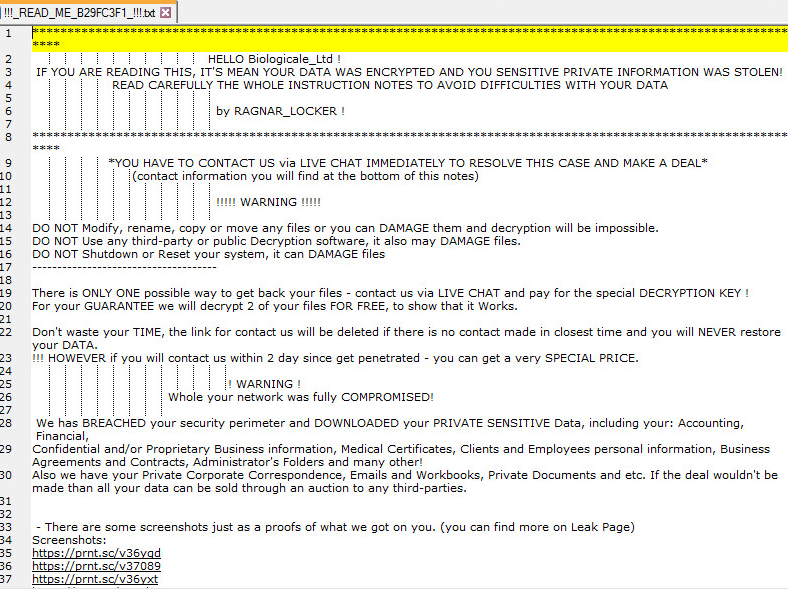
Ragnar Locker Ransomware Gang Takes Out Facebook Ads in Key New Tactic — Threat Post
- Following the Nov. 3 ransomware attack against Campari, Ragnar Locker group took out public Facebook ads threatening to release stolen data.
Pressure grows to reinstall White House cyber czar — The Hill
- Pressure to reinstate a cyber czar within the White House is growing, with bipartisan allies lining up on Capitol Hill to push such a proposal.
Zoom settles charges with FTC over deceptive security practices — Cyberscoop
- The FTC has reached a deal with Zoom to settle allegations that the communications technology company misrepresented its security and privacy protections.
How to Avoid Paying Ransomware Ransoms — Data Center Knowledge
- As private experts and government officials advise against indulging the bad guys, here are some tips for following that advice.
Treasury Asks if External Cyber Acts Qualify for Terrorism Risk Insurance Program — Nextgov
- A request for comment reflects recommendations made by the Cyberspace Solarium Commission.
Major ransomware strain jumps from Windows to Linux — SC Magazine
- A recently discovered file-encrypting Trojan, built as an executable and linkable format (ELF), encrypts data on machines controlled by Linux-based operating systems.
Hospital network hit by cyber attack restoring services — The Washington Times
- Computer experts at the University of Vermont Medical Center are working to restore systems disabled in a cyberattack that has affected the hospital’s ability to provide some cancer treatments.
Vietnamese hacking group OceanLotus uses imitation news sites to spread malware — Cyberscoop
- Suspected Vietnamese government-linked hackers are behind a series of fake news websites and Facebook pages meant to target victims with malicious software.
Microsoft Exchange Attack Exposes New xHunt Backdoors — Threat Post
- An attack on the Microsoft Exchange server of an organization in Kuwait revealed two never-before-seen PowerShell backdoors.
U.S. seizes over $1 billion in bitcoin tied to ‘Silk Road’ — Reuters
- The U.S. Justice Department announced it had seized over $1 billion worth of bitcoin associated with the underground online marketplace Silk Road.
Ransomware Attacks Surge 40% Globally In Q3: Report — Express Computer
- While overall malware volume declined for the third consecutive quarter, ransomware attacks globally surged 40% to reach 199.7 million hits in the third quarter of this year.
In Case You Missed It
- New SonicWall Products Drive Innovation; Offer Greater Flexibility, Performance and Low TCO — Atul Dhablania
- SonicWall TZ270/370/470: Accelerating Digital Transformation for SMBs & Secure SD-Branches — Sathya Thammanur
- New SonicWall NSa 2700: High Performance and Consolidated Security at Lower TCO — Ajay Uggirala
- SonicWall Enters the SASE Race with Zero-Trust Security Integrated into a Worldwide Network-as-a-Service — Sony Kogin
- SonicWall Capture ATP Receives ICSA Labs ATD Certification — Kayvon Sadeghi
- Healthcare and Cybersecurity During the Pandemic — Brook Chelmo
- Capture Client 3.5: Built for Managing Tenants — Brook Chelmo
- SonicWall NSM 2.1: Centralized Firewall Management Just Got Better — Ken Dang