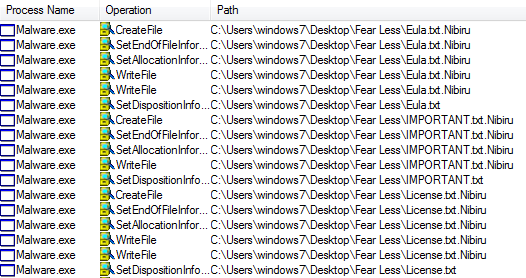
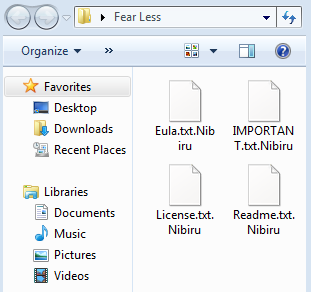
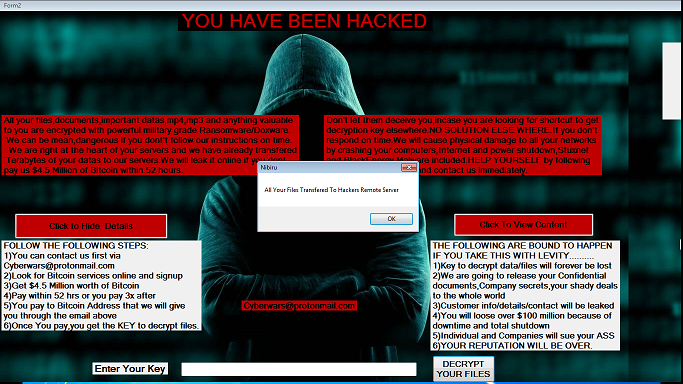
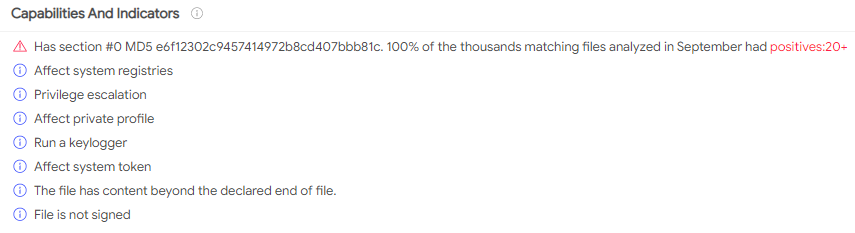
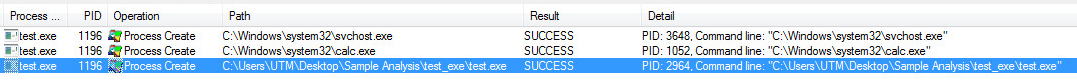
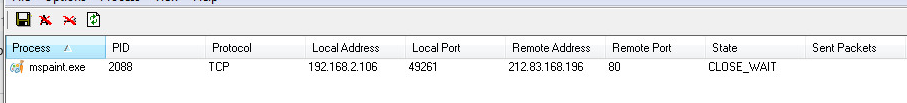
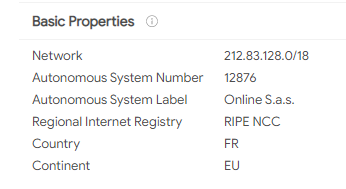
It’s an idea so ingrained in our culture that it’s been repeated by action movie stars, debated at length by political scholars, and cited in literature from young-adult fiction to parenting advice books: Do not negotiate with terrorists.
The rationale, according to Peter R. Neumann, director of the Center for Defense Studies at King’s College, London, is simple: “Democracies must never give in to violence, and terrorists must never be rewarded for using it. Negotiations give legitimacy to terrorists … undercut international efforts to outlaw terrorism, and set a dangerous precedent.”
If you’re an everyday civilian, it’s hard to imagine any practical application for this knowledge aside from the occasional action movie daydream. But there is, in fact, a situation in which everyday people are routinely given the choice of whether to negotiate with criminals: Ransomware.
Ransomware is a growing problem, and the COVID-19 pandemic seems to have accelerated this growth. According to the mid-year update to the SonicWall Cyber Threat Report, ransomware overall rose 20% during the first half of 2020. While some areas, such as the U.K., saw a year-over-year decline, the spike in ransomware in North America more than made up for it. The U.S., in particular, saw a staggering 109% increase in ransomware during the first half of 2020.
Last year, the monthly ransomware totals followed a neat, sine-wave-like pattern. In 2020, the numbers have been much more erratic. The late summer trough of 2019 never materialized this year — instead, numbers reversed course in July and have been skyrocketing since. The data from September, the most recent data we have, shows a staggering 34,112,981 ransomware attacks — more than double the total for September of last year. It’s too soon to see what the totals for October will be, but if the trends from last year hold, that number could climb even higher.
Worse still, the percentage of overall attacks focused on SMBs, education, local governments, public administration agencies, and even hospitals has been increasing as well. Because these organizations are usually smaller, and are working within tighter budgets, they often lack the security of larger companies — meaning ransomware attempts are more likely to succeed.
Should you pay a ransomware ransom?
Modern companies are built on, depend on and, in some cases, owe their existence to data. Faced with the prospect of starting over from square one, enduring major operational disruption and facing damage to customer relationships and reputation, some ransomware victims are tempted to pay the ransom just to make the problem go away.
But this isn’t advisable, for several reasons. For one, the criminals could simply abscond with your money — while ransomware operators tend to uphold their end of the bargain based on a very twisted concept of honor, not all do. Even dealing with an “ethical” ransomware operator gives no guarantees — it isn’t at all rare for the decryption key to be granted, only for the victim to find it didn’t decrypt the data entirely … or at all. According to a recent survey by research and marketing firm CyberEdge Group, nearly 1 in 5 ransomware victims surveyed paid the ransom and still lost all their data for good.
There’s also the matter of reinforcement: If you pay the ransom, your experience becomes a case study in why ransomware works and is a profitable and worthwhile undertaking. The more successful ransomware appears to be, the more attractive it becomes to those wishing to make a quick buck — potentially for the purpose of funding even more unsavory activities.
But if all of this isn’t enough of a deterrent — and obviously for some companies it isn’t, or we wouldn’t still be seeing ransomware — there’s also the chance that paying the ransom could get you in trouble with Uncle Sam.
On Oct. 1, the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) issued an advisory stating that in some cases, paying ransoms could be illegal. Any organizations that do so — regardless of whether it’s the victim company or a third party that facilitated the ransom payment — could be violating OFAC regulations and thus be subject to prosecution and hefty fines.
At issue here isn’t the payment of the ransom itself — it’s who the ransom is going to. The U.S. Department of the Treasury administers sanctions against countries and regimes, terrorists, and others recognized as threats to national security or the U.S. economy based on US foreign policy and national security goals. These individuals, groups and entities are recorded in the OFAC Sanctions List— which includes “numerous malicious cyber actors under its cyber-related sanctions program and other sanctions programs, including perpetrators of ransomware attacks and those who facilitate ransomware transactions,” according to the advisory.
In short, if the ransomware you’re infected with has been associated with an individual or group deemed to be a threat to the United States, you could have to pay.
Among the groups and individuals mentioned by name are some of the most well-known and prolific cybercriminals: Evgeniy Mikhailovich Bogachev (developer of Cryptolocker), individuals associated with the SamSam ransomware, the Lazarus Group and two subgroups (linked to WannaCry), and Evil Corp (cited for its involvement with Dridex malware, but also recently connected with WastedLocker). Note, however, that these were listed as examples, and not an all-inclusive list: There are other cybercriminals on the list, and more could be added at any time.
While the advisory does state that “a company’s self-initiated, timely and complete report of a ransomware attack to law enforcement” could be considered a significant mitigating factor in evaluating possible enforcement, remember that even in a best-case scenario — one that results in no federal fines or penalties whatsoever — you’re still left between ransomware’s proverbial rock and a hard place. In other words, by the time you’re impacted by ransomware, there are no good options left. Your opportunity for a “good” outcome to a ransomware attack depends entirely on the actions you take before the fact.
Fortunately, there are many things you can do to nip ransomware in the bud, including regular patching, creating and maintaining quality backups, implementing employee education initiatives and more.
In the meantime, follow the latest trends in ransomware, such as where and how ransomware operators are attacking, by checking out the mid-year update of the SonicWall 2020 Cyber Threat Report.
Get the Updated Cyber Intelligence
Download the complimentary mid-year update to the 2020 SonicWall Cyber Threat Report to gain the latest cyber threat intelligence for navigating the new business normal.
READ THE UPDATE