What’s scarier than Dracula, trickier than a haunted house and more expensive than a giant bucket of Halloween candy? Cyberattacks — and they can devastate individuals and organizations alike. Fortunately, however, they can be prevented if we all contribute. Today marks the beginning of the 17th annual National Cybersecurity Awareness Month, and this year SonicWall will bring you tips, best practices and more to ensure you’re ready to “Do Your Part. #BeCyberSmart.”
Each October, the National Cyber Security Alliance collaborates with the Cybersecurity and Infrastructure Security Agency (CISA) to launch a month-long campaign highlighting new and emerging threats and helping ensure all Americans have the resources they need to be safer and more secure online.
“While technology — a luxury turned necessity — continues to improve the quality of lives and economies around the world, some individuals will naturally try to navigate around it or simply bypass it altogether, placing themselves and their organization at risk,” said SonicWall President and CEO Bill Conner. “Now that mobile and remote workforces rely upon extended distributed networks that include everything from corporate offices to homes, global cybersecurity awareness initiatives are key to educating the masses on the importance of doing their part to protect everything from personal devices, home networks, critical data and infrastructure.”
The theme for 2020, “Do Your Part. #BeCyberSmart,” encourages individuals and organizations to own their role in protecting their part of cyberspace. Being more secure online is a shared responsibility, but by taking proactive steps toward lasting, positive cybersecurity behaviors at work and at home, each of us can help create a safer cyber environment.
As National Cybersecurity Awareness Month Champions, SonicWall’s cybersecurity experts will spend the next month exploring ways to help organizations and individuals protect their information and secure their systems and devices. We’ll explore several topics in depth, but in the meantime, here are some steps each of us can take today:
- LOCK DOWN YOUR LOGIN
Use long, unique passphrases that are hard to break but easy to remember for each account, and utilize two-factor or multifactor authentication wherever possible. - WHEN IN DOUBT, THROW IT OUT
Email, social media posts, texts and more aren’t always what they seem — sometimes they harbor malware or malicious links. If you’re unsure about it, hit “delete.” - KEEP A CLEAN MACHINE
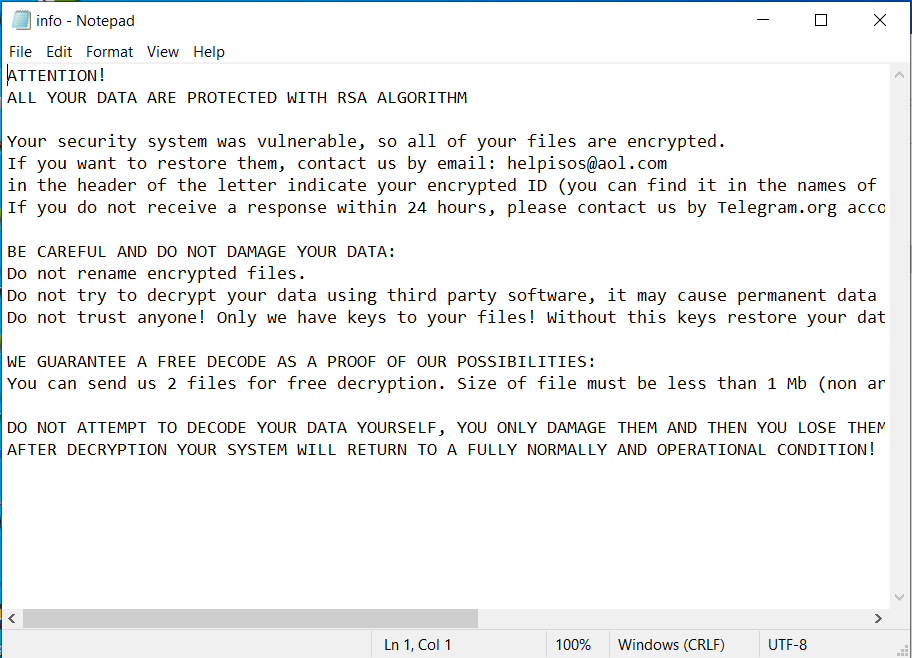
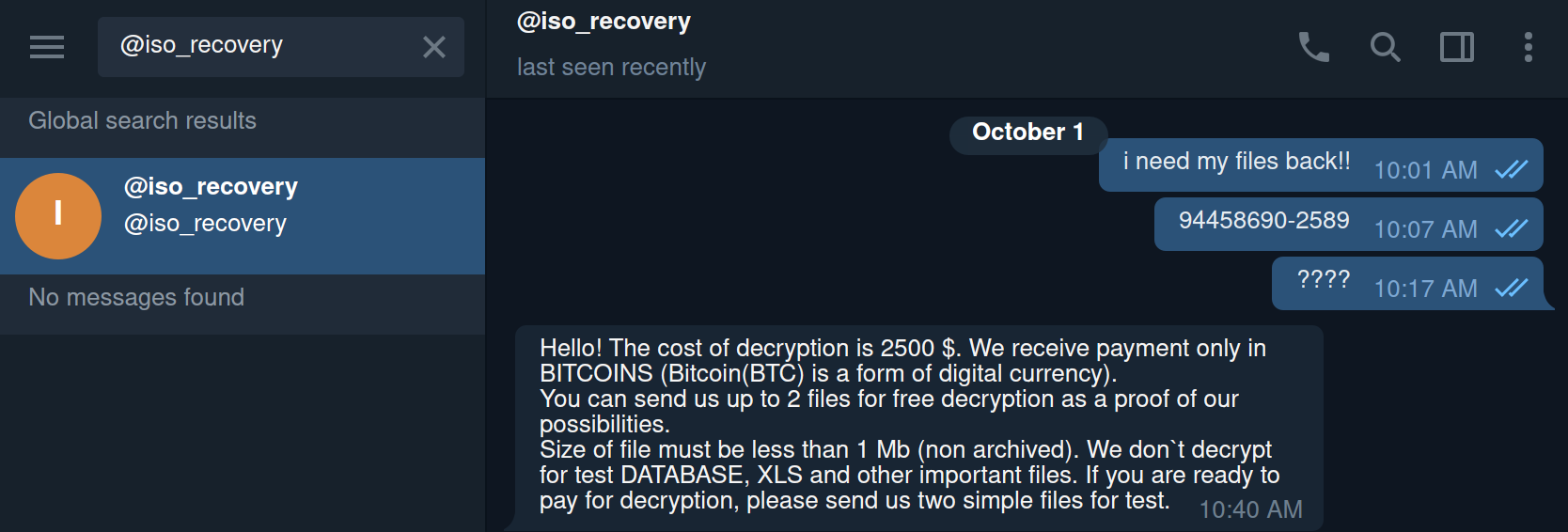
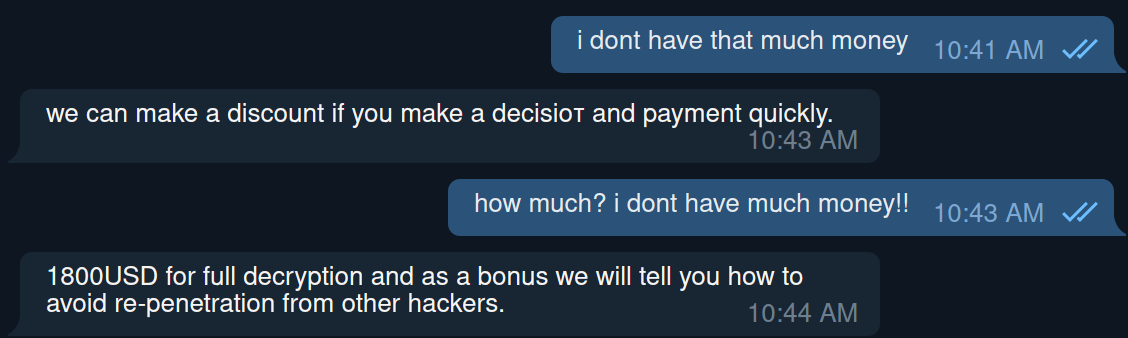
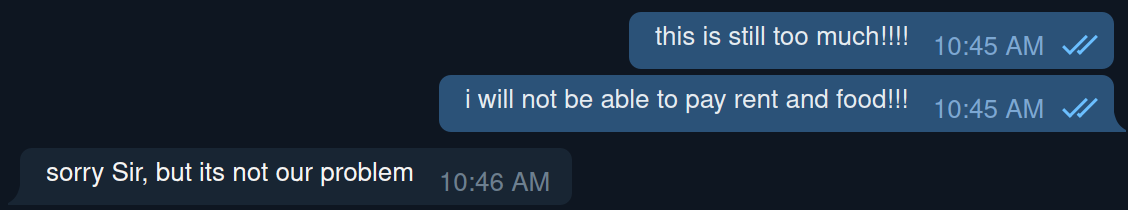
Keep all software current to reduce risk of infection from ransomware and malware. - BACK IT UP
Create backups of valuable data. In the case of ransomware or other threats, they can help prevent permanent loss. - OWN YOUR ONLINE PRESENCE
Set up privacy and security settings immediately and check them regularly to ensure they’re still configured to your comfort. - SHARE WITH CARE
Think about the potential consequences before posting personal info about yourself or others. - GET SAVVY ABOUT WI-FI HOTSPOTS
These are not secure, meaning anyone could see what you’re doing while you’re connected to them. Consider a VPN or mobile hotspot for greater security.
“In the physical world, we all know a chain is only as strong as its weakest link,” said Chad Sweet, founder and CEO, The Chertoff Group. “The same is true in cyber. None of us want to be that weak link — failing to protect ourselves, our families or our businesses. As key players like NCSA, DHS and SonicWall have rightly challenged us to do, we need to use National Cybersecurity Awareness Month as a call to action for all of us to recommit to strengthening the ‘links’ where we play a critical role at home, in the office and in our communities.”
About NCSAM
National Cybersecurity Awareness Month was launched by the National Cyber Security Alliance (NCSA) and the U.S. Department of Homeland Security (DHS) in October 2004 as a broad effort to help all Americans stay safer and more secure online. Following wide success of the ‘Our Shared Responsibility’ theme in years past, CISA and NCSA have shifted strategic focus to a message that promotes personal accountability.
To learn more about NCSAM, please visit StaySafeOnline.org.