Zyxel IKE Remote Command Execution
The SonicWall Capture Labs Threat Research team has observed attackers targeting vulnerable Zyxel devices by exploiting a Zyxel IKE Remote Command Execution vulnerability.
Zyxel website provides the following description of their products:
“The Zyxel USG FLEX Series supports IPsec, SSL, and L2TP-based VPNs, making it an ideal solution for providing a secure network to access remote or home-based workers. Zero-configuration remote access removes complicated setup challenges making it easier for employees to establish VPN connections to the office without the need for IT support.
The Zyxel ZyWALL ATP series is an Advanced Threat Protection Firewall empowered by cloud intelligence leveling up network protection, especially in tackling unknown threats.
Improper error message handling in Zyxel ZyWALL/USG,VPN,USG FLEX and ATP firmware series could allow an unauthenticated attacker to execute some OS commands remotely by sending crafted packets to an affected device.”
OS Remote Command Execution
Portswigger describes OS command injection as a web security flaw that permits a malicious actor to run arbitrary operating system (OS) commands on the server where an application is running. This causes OS remote command execution which in turn can potentially lead to a complete compromise of the application and its associated data. Furthermore, attackers frequently use OS command injection vulnerabilities as a stepping stone to compromise additional components of the hosting infrastructure. This is achieved by exploiting trust relationships to extend the attack to other systems within the organization.
Zyxel IKE Remote Command Execution | CVE-2023-28771
There is a command injection vulnerability in the Internet Key Exchange (IKE) packet decoder. This vulnerability can be exploited remotely over UDP port 500 on the WAN interface of several Zyxel devices. Importantly, these affected devices are vulnerable even in their default configuration, and if exploited, this vulnerability allows for command execution with root privileges.
Rapid 7 researchers identified that the vulnerability could be triggered during the decoding of an IKEv2 Notify payload. When an IKEv2 Notify message with a message-type of NO_PROPOSAL_CHOSEN is processed, the attacker can provide arbitrary commands in the Notification Data field. These commands will be executed with root privileges.
Let us look at an example of exploitation :

![]() is a command injection attempt that tries to establish a reverse shell connection to the IP address on port 4444. If successful, it would open a shell on the target machine and potentially give the attacker control over it.
is a command injection attempt that tries to establish a reverse shell connection to the IP address on port 4444. If successful, it would open a shell on the target machine and potentially give the attacker control over it.
IOCs
Since the vulnerability exists within a logging function it is possible to monitor the log files to potentially understand if a compromise has occurred. The log file /tmp/sdwan/vpndebug.log would display the message “[cgnat] 4th cgnat convert wrong” if the vulnerable code path was trigger. It is important to note this would not confirm exploitation occurred, only that the vulnerable code path was triggered.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- IPS 15876 : Zyxel IKE Remote Command Execution
- IPS 15898 : Zyxel IKE Remote Command Execution 2
Following Zyxel versions are vulnerable:
Affected series Affected version
ATP V4.60 to V5.35
USG FLEX V4.60 to V5.35
VPN V4.60 to V5.35
ZyWALL/USG V4.60 to V4.73
Zyxel has issued a patch for this vulnerability.
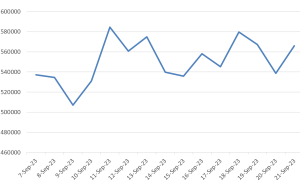
Threat Graph
IPS 15898 signature hits in the past two weeks have maintained a consistent trend suggesting attackers are trying to exploit this vulnerability.