phpPgAdmin Deserialization Vulnerability
Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
phpPgAdmin is an open-source, web-based administration tool for managing PostgreSQL, an advanced, enterprise-class, and open-source relational database system. phpPgAdmin is written in PHP and provides a user-friendly interface that allows users to perform various database management tasks. Users can create, modify, and delete databases, tables, and records through this interface, making it a valuable tool for those who prefer a graphical user interface over command-line interaction.
It has been reported that phpPgAdmin 7.14.4 and earlier versions have a deserialization vulnerability. Deserialization vulnerabilities occur when an application unsafely processes external input during the deserialization process, potentially leading to code execution, denial of service, or elevation of privileges. This vulnerability underscores the importance of using secure coding practices and regularly updating software to protect against known vulnerabilities.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2023-40619.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 8.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:P/RL:O/RC:C).
Base score is 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 8.8 (E:P/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is proof of concept code.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
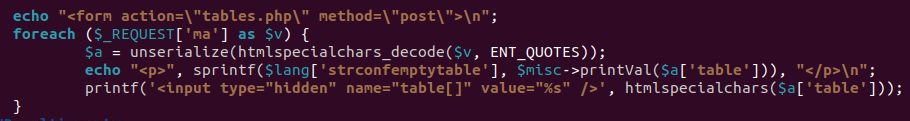
The doEmpty function in the tables.php file is responsible for emptying tables in a database, and it is designed to handle both single and multiple table emptying operations. It works by taking user input from the $_REQUEST[‘ma’] or $_REQUEST[‘table’] global variables, which are populated by the client through HTTP GET or POST requests. When multiple tables are specified through $_REQUEST[‘ma’], the function iterates over each table, unserializes the user input, and performs the emptying operation on each specified table. The use of the unserialize function here is critical as it exposes a potential security vulnerability known as PHP Object Injection due to the way it handles serialized objects.
PHP Object Injection vulnerabilities occur when user-supplied input is passed to the unserialize function, which can result in the instantiation of objects and the execution of the magic method __wakeup. In this specific case, the user could potentially pass a serialized object with a malicious __wakeup method to the $_REQUEST[‘ma’] variable, leading to the execution of arbitrary PHP code. This could allow an attacker to perform various malicious activities, such as executing system commands, creating, deleting, or modifying files, or even launching attacks against other systems. Consequently, the use of unserialize on user-supplied data in this function poses a severe security risk and could lead to a full server compromise if exploited successfully.
To mitigate the risks associated with this vulnerability, it is crucial to avoid using the unserialize function on user-supplied input. Instead, alternative methods for handling user data, such as JSON encoding and decoding, should be employed. Additionally, input validation and sanitization should be implemented to ensure that only expected and safe data is processed by the application.
Triggering the Problem:
• The target system must have the vulnerable product installed and running.
• The attacker must have network connectivity to the affected ports.
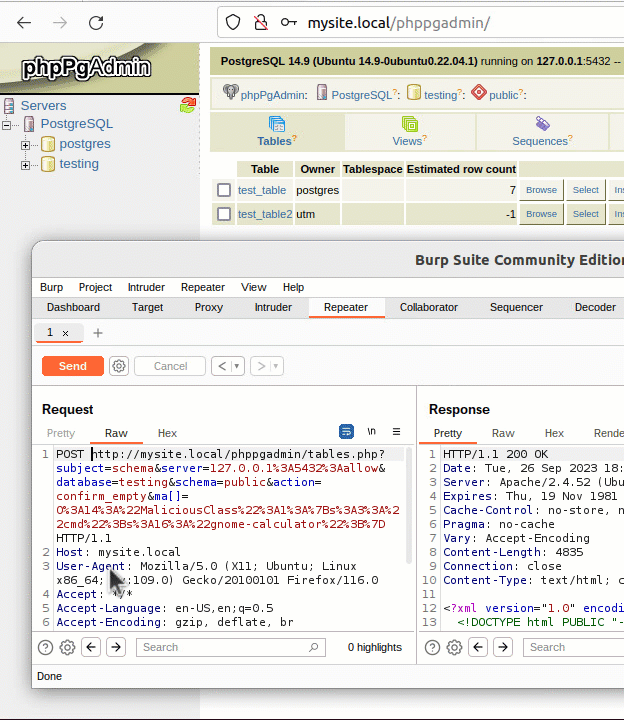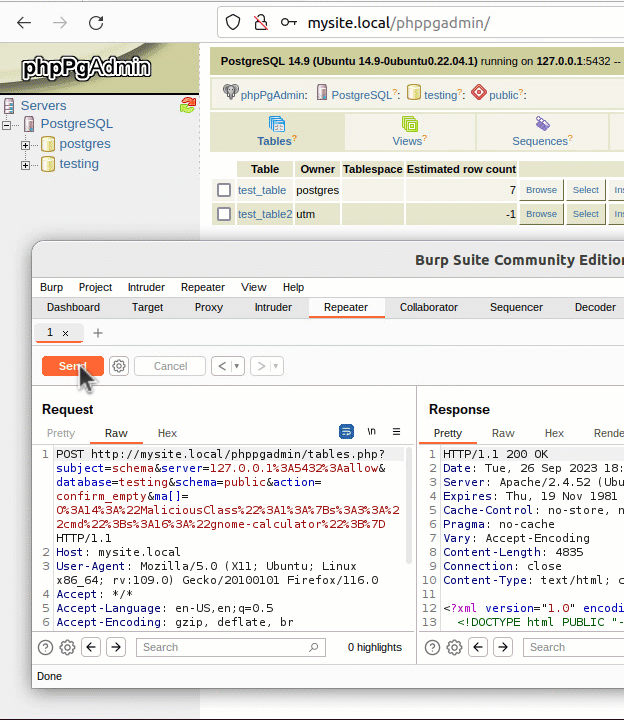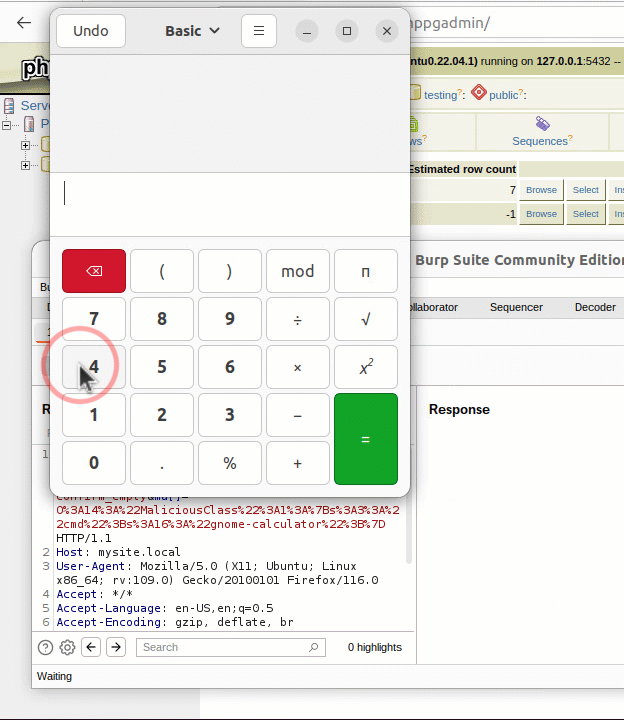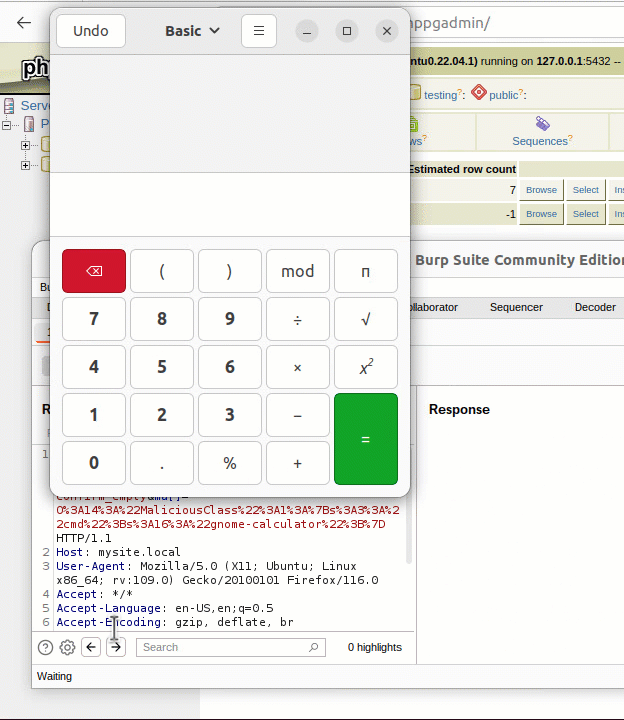
• The attacker must send malicious serialized payloads to the tables.php endpoint.
• The query string parameter ‘ma’ is used to trigger the ‘unserialize’ function by injecting serialized data.
Triggering Conditions:
The unserialize() deserialization vulnerability in PHP occurs when the unserialize() function is passed user input without adequate validation, consequently triggering magic methods like __wakeup() or __destruct() in an object-oriented context. These magic methods are invoked automatically during deserialization, providing an avenue for attackers to execute malicious code or carry out other harmful activities. The vulnerability underscores the importance of validating or sanitizing user input and avoiding the use of unserialize() with untrusted data, to prevent potential exploitation.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP
• HTTPS
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS:15919 phpPgAdmin Insecure Deserialization
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Configure the vulnerable product to allow access to trusted clients only.
• Update to a non-vulnerable version of the product.
• Filter attack traffic using the signature above.
A Third Party has released the following advisory regarding this vulnerability:
Third Party Advisory