Citrix Bleed: Leaking Session Tokens Vulnerability
Overview
SonicWall Capture Labs Threat Research Team became aware of the threat Citrix Bleed, assessed its impact and developed mitigation measures for the vulnerability.
Citrix NetScaler is an Application Delivery Controller (ADC) and load balancer designed to enhance the performance and security of web-based applications. Produced by Citrix Systems, NetScaler ensures the swift, reliable and secure delivery of applications to devices everywhere. It combines advanced traffic management, application security, content switching and optimization features in one platform.
Citrix NetScaler, encompassing both ADC and NetScaler Gateway, recently came under scrutiny for a vulnerability identified as CVE-2023-4966. As of October 18th, CISA has reported active exploitation of this vulnerability. This flaw pertains to a sensitive information disclosure that can occur when the system is set up as a Gateway (encompassing VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or an AAA “virtual” server. Notably, the vulnerability corresponds to CWE-119, which is described as “improper restriction of operations within the bounds of a memory buffer”. In some configurations, the sensitive information disclosed can include a valid session token.
The affected versions are:
• NetScaler ADC and NetScaler Gateway 14.1 before 14.1-8.50
• NetScaler ADC and NetScaler Gateway 13.1 before 13.1-49.15
• NetScaler ADC and NetScaler Gateway 13.0 before 13.0-92.19
• NetScaler ADC 13.1-FIPS before 13.1-37.164
• NetScaler ADC 12.1-FIPS before 12.1-55.300
• NetScaler ADC 12.1-NDcPP before 12.1-55.300
This vulnerability has been patched by Citrix on October 10th and can be mitigated by upgrading to the latest version of NetScaler.
CVE Details
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2023-4966.
The overall CVSS score is 9.4 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:L/E:X/RL:X/RC:X).
Base score is 9.4 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:L), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is Low.
Temporal score is N/A (E:X/RL:X/RC:X), based on the following metrics:
• The exploit code maturity level of this vulnerability is Not Defined.
• The remediation level of this vulnerability is Not Defined.
• The report confidence level of this vulnerability is Not Defined.
Technical Overview
In an effort to pinpoint the vulnerability, a comparative analysis was conducted between the two specific versions of the software: the older 13.1-48.47 and the newer 13.1-49.15. By meticulously examining the differences and updates between these versions, we were able to identify the exact location of the patch and gain a deeper understanding of the vulnerability’s nature. In Figure 1 the differences can be seen by using the tool BinDiff.
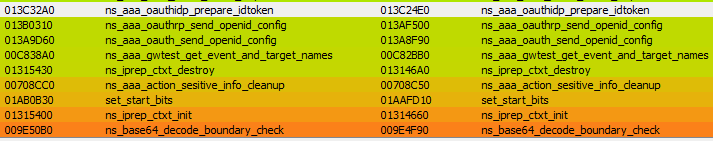
The ns_vpn_process_unauthenticated_request function has been meticulously crafted to build and validate the URL /oauth/idp/.well-known/openid-configuration. Within its implementation, there is a significant call to ns_aaa_oauth_send_openid_config, which makes use of the snprintf function as seen in Figure 2.
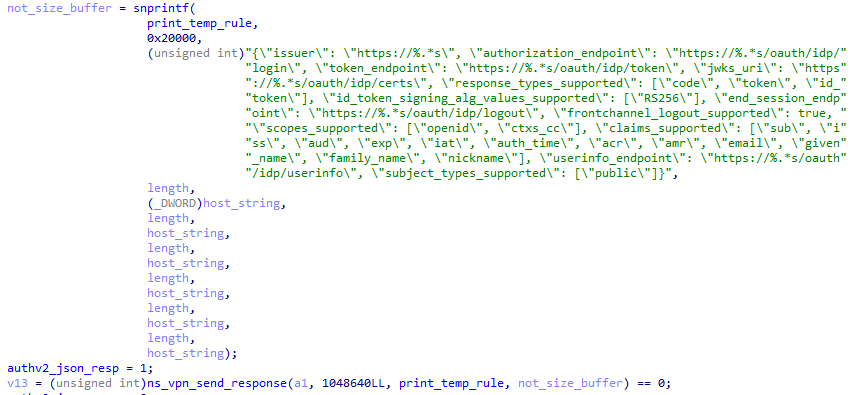
The primary role of this function is to format and populate the print_temp_rule buffer with a series of characters and values. Delving into its specifics: the destination buffer is print_temp_rule, and it has a Maximum Size of 0x20000, which is equivalent to roughly 128 KB. The format string, a comprehensive JSON object, as seen in Figure 3, details the OpenID Connect configuration.
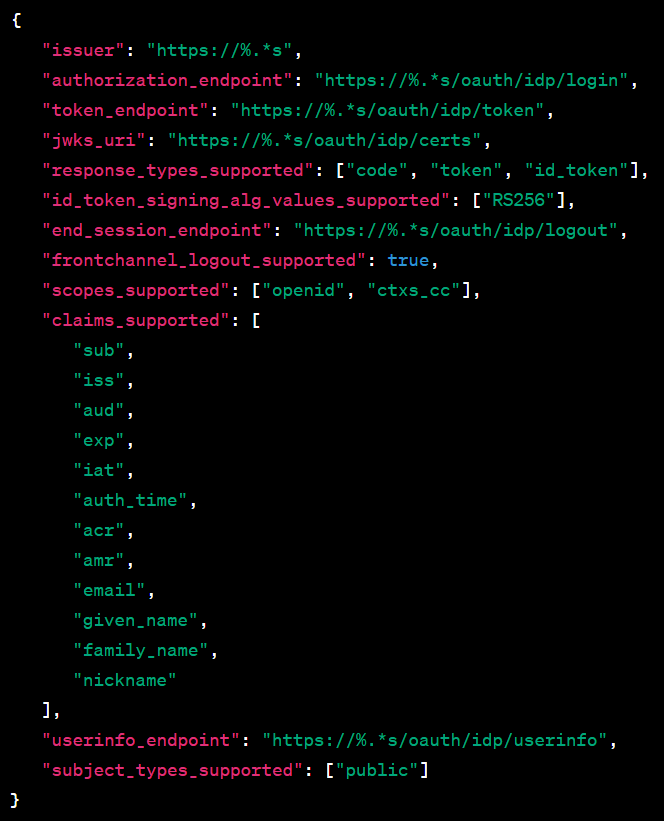
The snprintf as seen in Figure2, employs multiple %.*s format specifiers which expect a length and a string as paired arguments. These specifiers are used to define various OAuth and OpenID Connect endpoints, with the base URL or domain inferred from the variable host_string. To shed light on the arguments (figure 2): length denotes the length of the host_string and ensures only up to length characters from host_string are printed. The host_string reference is the base URL or domain that fills in the respective URLs in the JSON.
In the aftermath of this operation, not_size_buffer will hold the count of characters intended for print_temp_rule, excluding the null byte, if there were no buffer constraints. This behavior of snprintf is typical: It returns the number of characters it aims to write, irrespective of the size limit that might truncate the actual write-up. Thus, not_size_buffer captures the length of the fully constructed JSON string.
This function’s design intricacies go beyond just formatting; there’s a security facet to it. Initially, the function would instantly send out the response. But in its patched form, a response is dispatched only if snprintf yields a value less than 0x20000.
There’s a vulnerability in how the return value of snprintf is used to determine how many bytes are sent to the client through ns_vpn_send_response. Contrary to what one might expect, snprintf doesn’t return the number of bytes it actually writes to the buffer. Instead, it returns the number it would have written if the buffer was large enough. This is where the security risk comes into play. The return value is being incorrectly used as the number of bytes written to the buffer.
Triggering the Vulnerability
• The target must be running NetScaler Citrix Firmware version prior to 13.1-49.15.
• The attacker must have network access to the vulnerable software.
• Sending a GET request to the endpoint: /oauth/idp/.well-known/openid-configuration,
containing Host: a (any ‘char’ to the power of 24,576).
Exploitation
To exploit this vulnerability, the attacker’s goal is to generate a response that exceeds a buffer size of 0x20000 bytes. If successful, the application would send not only the filled buffer but also the memory following the print_temp_rule buffer, potentially exposing sensitive data or causing other unexpected issues. Proof of concept code has been published and active exploitation of this vulnerability has been reported by CISA on October 18th. Included in the leaked information, depending on the appliance’s configuration, is a 65 byte long hex string which is a valid session cookie. As a resulted an attacker can use this session key to impersonate an active user.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
• IPS:4130 NetScaler ADC/Gateway Information Disclosure
Threat Graph
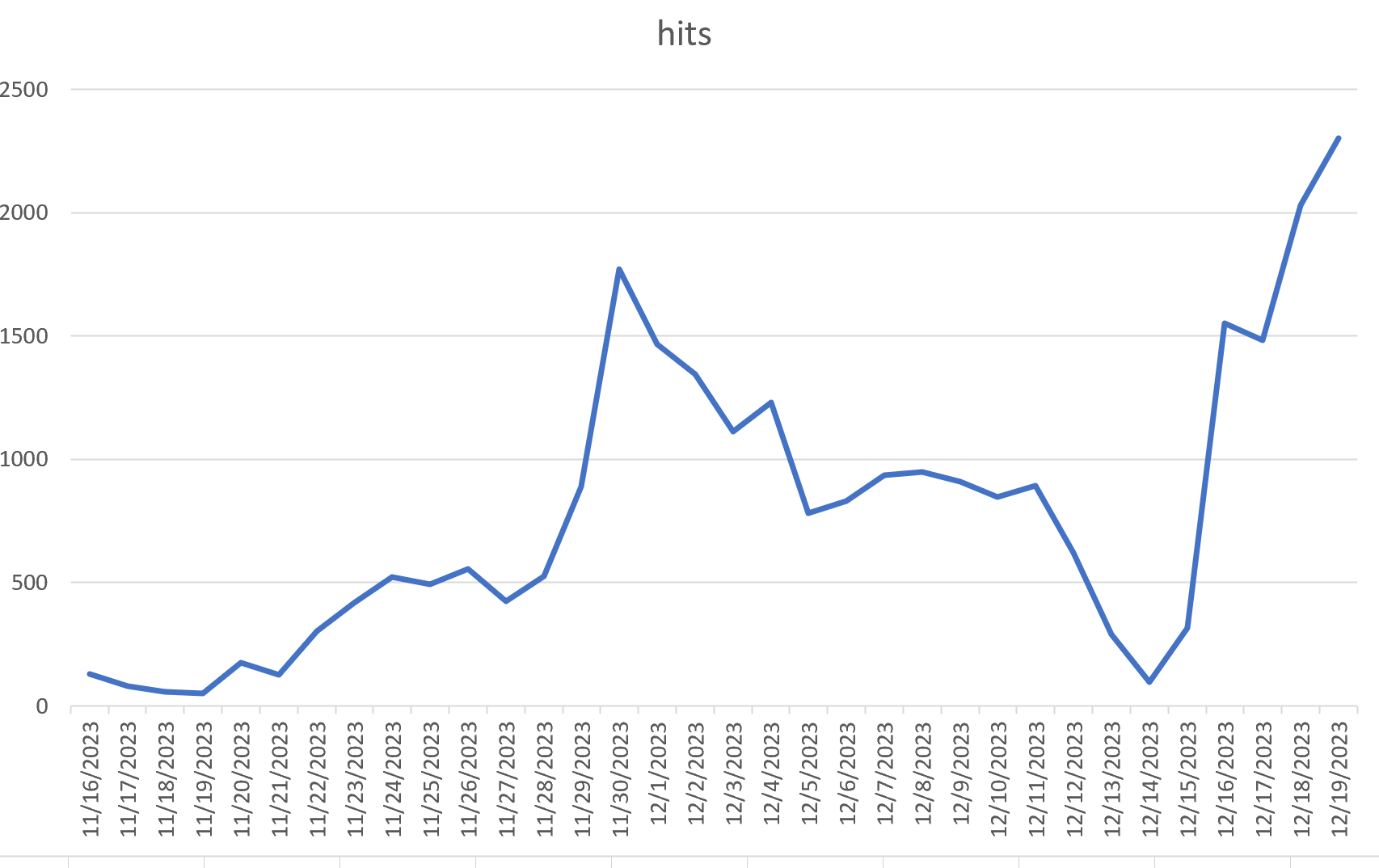
Figure 4: SonicWall signature hits data (Updated 12/20/23)
Remediation Recommendations
The risks posed by this vulnerability can be mitigated or eliminated by:
• Applying the vendor-supplied patch to eliminate this vulnerability.
• Utilizing up-to-date IPS signatures to filter network traffic.
• Alternatively, consider taking the server offline.
Relevant Links




