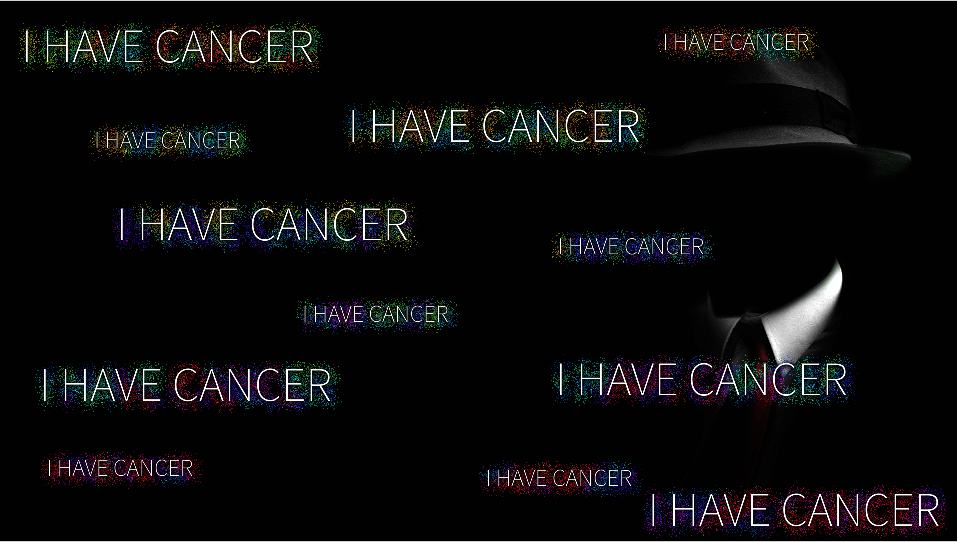Catching Cerber Ransomware
Since the release of SonicWall Capture Advanced Threat Protection (Capture ATP) in August 2016 on SonicWall firewalls, we have seen a lot of unique behavior from authors of malicious code, namely ransomware.
Up until Christmas 2016, Locky received a lot of attention from security firms but then took a backseat during the holiday season. One thing I noticed around that time was that a ransomware variant called Cerber would actually be one of the more persistent pups in the litter. I started seeing Cerber show up on Capture ATP’s daily reports and wanted to understand why we were still catching this on the sandbox instead of the firewall.
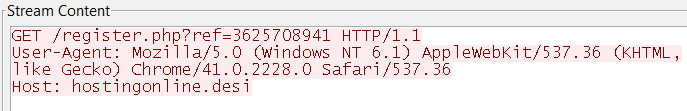
In short, we were catching this on the firewall because SonicWall’s Capture Labs research team was creating a large amount of signatures for Cerber, but what I was seeing were “updated” versions of Cerber being caught in the wild; as many as two versions a day. This was done to get around Cerber signatures created to stop older versions of itself. To make things more interesting, these Cerber variants were utilizing seven different tactics to evade detection.

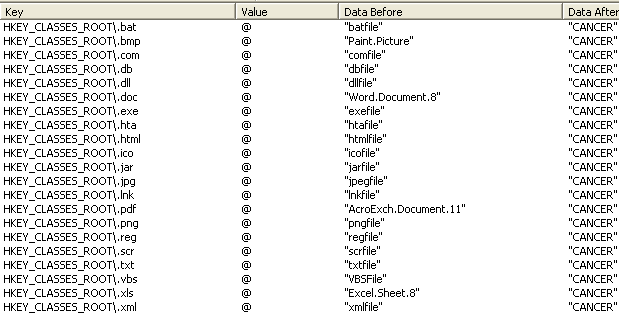
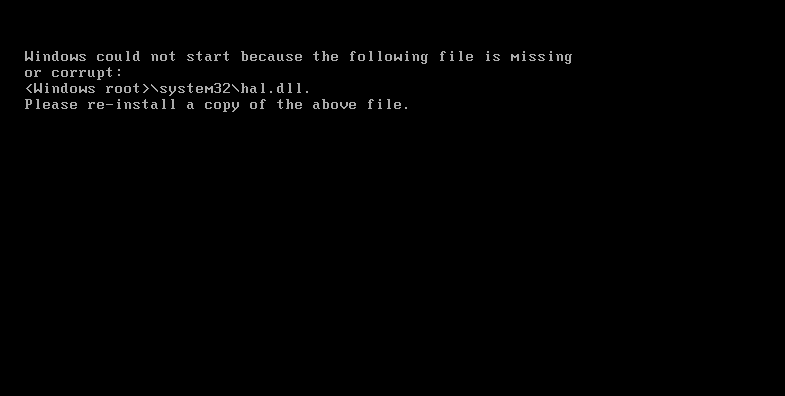
The image above is a snippet of a very long report that partly shows what Cerber wants to do. Did you notice the seven different evasion tactics? Malware did not do this in the past; at least one that I remember fondly. In that past, the security industry was really trying to get the upper hand with the “explosive growth” of malicious code that was being authored and wanted to use virtual environments to run and test code. About five years ago, the industry introduced the network sandbox to the market and it was a hit, because we now had a tool where we could run potentially malicious code in an isolated environment to see if we could white or blacklist it.
So, do you think that attackers folded up their laptops and found real jobs? Nope, they learned how to evade them, the real essence of what a hacker truly is. If you read third-party reports on network sandboxing, you will read skeptical and bearish reports about its effectiveness and ability to evade a sandbox at a medium difficulty. When you see the image above, you have to believe that the reports are real and Cerber’s evasion tactics rank up there with some of the best I have seen recently; truly an advanced persistent threat. So why am I able to show this to you? Although it is evading other sandboxes, it is not able to get past ours. But how?
In short, we leverage Capture ATP, a multi-engine sandbox that first runs suspicious code through a set of pre-filters that analyzes the code and compares it against a real-time list to see if anyone we collaborate with knows about it. This step eliminates a lot of newly minted malware within milliseconds; almost at the same speed as lightning strikes the Earth.

After that, the code will go through a parallel set of engines that will help us determine what a new batch of code wants to do from the application, to the OS, to the software that resides on the hardware. We run it through real-time deep memory inspection, virtualized sandboxing, hypervisor level analysis and full-system emulation. Naturally, when we get to this point it does take a little time but it’s worth it.