Cancer Ransomware forgets how to ransomware (Feb 10, 2017)
With Locky ransomware activity at an all time low, new smaller players in this scam has been observed to continue to proliferate in the wild. This week, SonicWALL Threats research team has received reports of yet another variant seemingly still in its early stages. This Trojan behaves like a ransomware, but during our analysis it failed to show a warning or instructions on how to regain files and send the payment – the most common sign of a ransomware infection. It ended up being more of an annoyance than a Trojan trying to defraud its victim.
Infection Cycle:
This Trojan arrives as a fake VirusTotal-related file. It uses the following icon and file properties:
![]()
Upon execution, it tries to send an ID to a remote server presumably to “register” the infection.
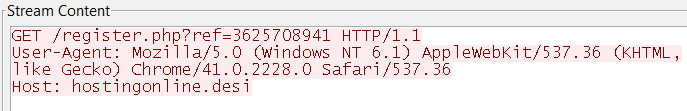
It creates a copy of itself in the AppData directory and also drops the following files:
- %APPDATA%Local~~42340900CANCER~~.dat
- %APPDATA%Localewwwwww~cancer.png
The png file looks like an image that will be used to change the victim’s desktop background after a successful infection:
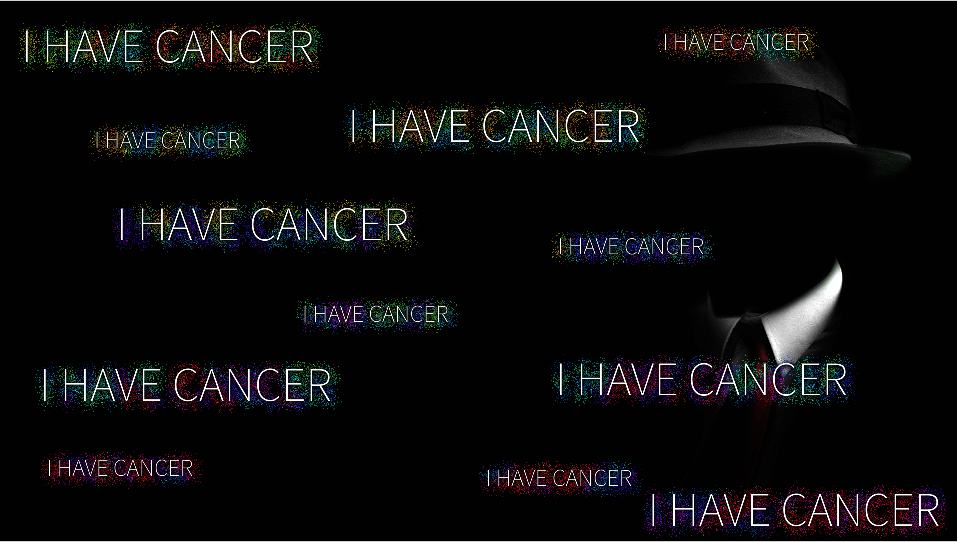
While the dat file has nothing but some strings with no use. This might be a placeholder for a file that can later be used to log infection data.

During infection, an image of a face will start floating on the desktop like a screensaver.
At this point, the victim’s files are not encrypted but they are overwritten.

Filenames stay the same as well as file extensions but they will no longer function as expected. File associations are modified and any overwritten file will now have the fake Virustotal icon and will launch the Trojan when executed.

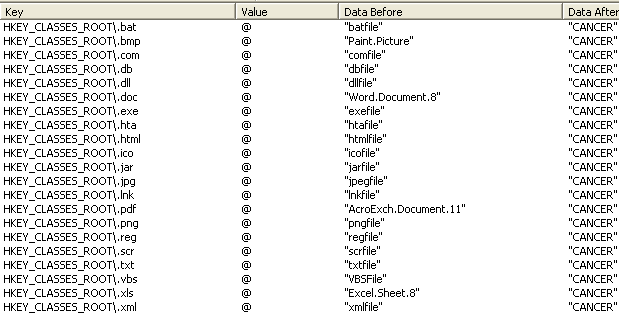
The following registry changes were also made:
When opened with a text editor, the victim’s files will now just bear the string “_cancer” and nothing else.

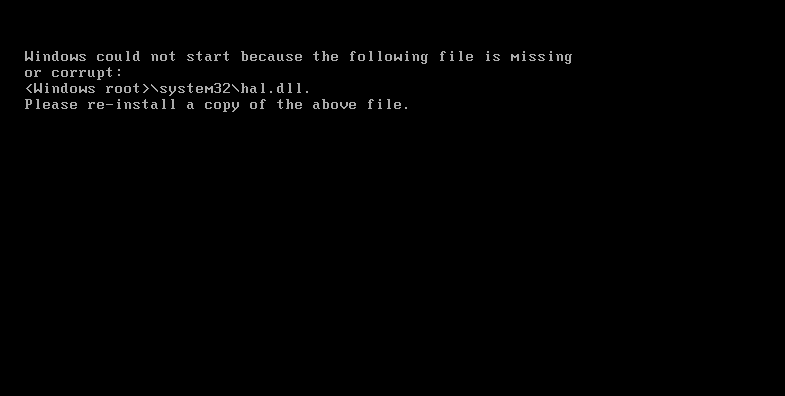
At this point, the machine became so unstable that it bluescreened. No warning note or any file with payment instructions has been observed during the analysis. The victim will be unable to reboot his machine since operating system boot related files are also encrypted which will render the machine useless.
Because of the prevalence of these types of malware attacks, we urge our users to back up their files regularly.
SonicWALL Gateway AntiVirus provides protection against this threat with the following signature:
- GAV: Cancer.KOI (Trojan)





