Cyber Security News & Trends – 07-26-19
This week, SonicWall releases a mid-year update to the 2019 SonicWall Cyber Threat Report, hackers breach the FSB, and Johannesburg hit by ransomware.
SonicWall Spotlight
SonicWall 2019 Mid-Year Threat Report Shows Worldwide Malware Decrease of 20%, Rise in Ransomware-as-a-Service, IOT Attacks and Cryptojacking – SonicWall Press Release
- SonicWall refreshes its data from the first months of 2019 for the Cyber Threat Report Mid-Year Update. The Cyber Threat Report provides insights into the cybersecurity industry’s top threats and trends, major finds include:
- Ransomware volume up 15% globally year to date
- Encrypted threats spike 76%
- IoT malware attacks up 55%
- Malware attacks across non-standard ports dips to 13%
- With bitcoin value spiking, cryptojacking volume up 9%
SonicWall CEO on McAfee IPO Rumours and Symantec’s Possible Sale – CRN ChannelWeb
- Channel Web interviews SonicWall CEO Bill Conner discussing business and government reactions to changes to the cybersecurity industry where the threat landscape which is “is getting very, very real.”
UK Ransomware Attacks Soar 195% – Malware Cocktails Proliferate – CBROnline
- The SonicWall Cyber Threat Report Mid-Year Update data is covered in the press; further coverage includes Dark Reading, Security Boulevard, The Next Web, Computerweekly Microscope, and IT Pro.
Cybersecurity News
NSA Launches Cybersecurity Directorate – NextGov
- The National Security Agency has announced the launch of a new division aimed at defending the country’s national security infrastructure from digital attacks. The Cybersecurity Directorate will bring the agency’s foreign intelligence and cyber operations together under the same roof.
Hackers Breach FSB Contractor, Expose Tor Deanonymization Project and More – ZDNet
- A contractor for the FSB, Russia’s national intelligence service, has been hacked with over 7.5 terabytes of data taken. Information exposed includes data on secret developments like a Tor deanonymization project and the ability to disconnect the Russian internet from the rest of the world.
Two Charged With Terrorism Over Bulgaria’s Biggest Data Breach: Lawyer – Reuters
- Police raided the offices of cybersecurity firm Tad Group following last month’s cyberattack and data breach in which personal data for nearly every adult Bulgarian was stolen. Two workers have been charged with terrorism, both deny wrongdoing.
Louisiana Governor Declares State Emergency After Local Ransomware Outbreak– ZDNet
- Following a series of cyberattacks on school districts Louisiana Governor John Bel Edwards declared a cybersecurity state of emergency. This is only the second time a state has declared a state of emergency over cybersecurity, the first being Colorado in February 2018.
Facebook to Pay $100 Million SEC Fine Over Cambridge Data Use – Bloomberg
- Facebook has agreed to pay $100 million in a U.S. Securities and Exchange Commission settlement over the Cambridge Analytica scandal. In the settlement Facebook refuse to admit or deny any wrongdoing.
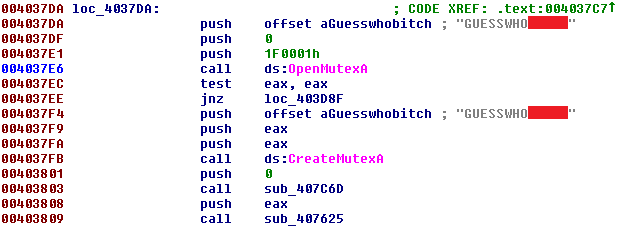
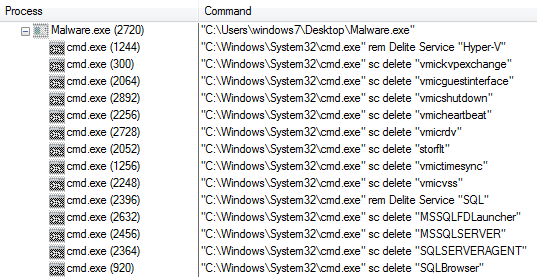
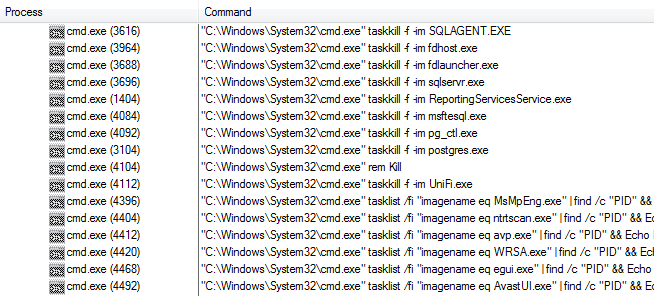
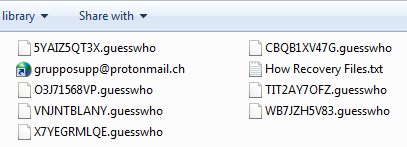
Ransomware hits Johannesburg electricity supply – BBC
- Johannesburg’s City Power has been the latest high-profile victim of a ransomware attack with more than a quarter of a million people affected. The City of Johannesburg says no customer data has been compromised.
And finally:
UK, EU Police Pilot Scheme to Give Wayward Teen Hackers White Hats – ZDNet
- A new UK and EU scheme called “Hack_Right” is currently being trialled. The scheme is aimed at staging interventions for teenagers who are involved in hacking, encouraging them to change their behavior rather than punishing them with jail time or fines.
In Case You Missed It
- Mid-Year Update: 2019 SonicWall Cyber Threat Report – Geoff Blaine
- 5 Best Practices for Fast, Secure Wi-Fi on K-12 Campuses – Srudi Dineshan
- Switch to SonicWall: 8 Reasons to Trade In Your Old Firewall – Bob Vankirk
- AI, Threat Intelligence and The Cyber Arms Race: SonicWall CEO Bill Conner Joins Chertoff Group Security Series Event – John Lynch
- Defending Endpoints from Fast, Ferocious Ransomware Attacks – Brook Chelmo