10 Tips for a Safe and Happy Holiday
They’re not interested in peace on earth, a hippopotamus or their two front teeth. You won’t find them decking the halls, dashing through the snow or even up on the housetop. But that doesn’t mean cybercriminals aren’t out in force this time of year — and they’re relying on you being too wrapped up in your holiday preparations to see them coming.
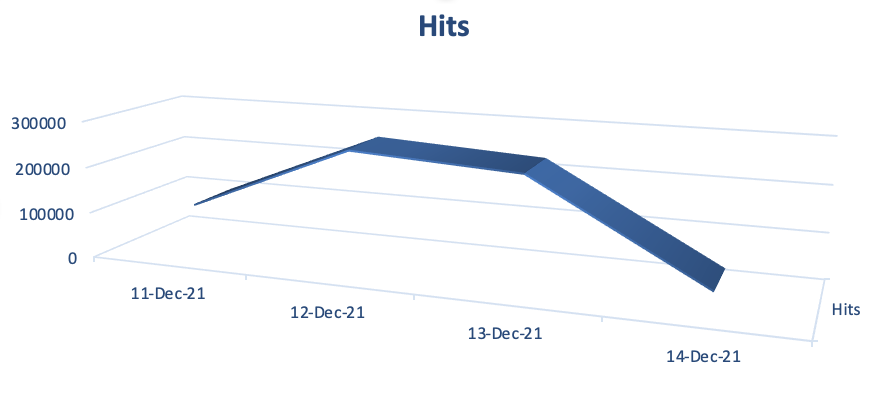
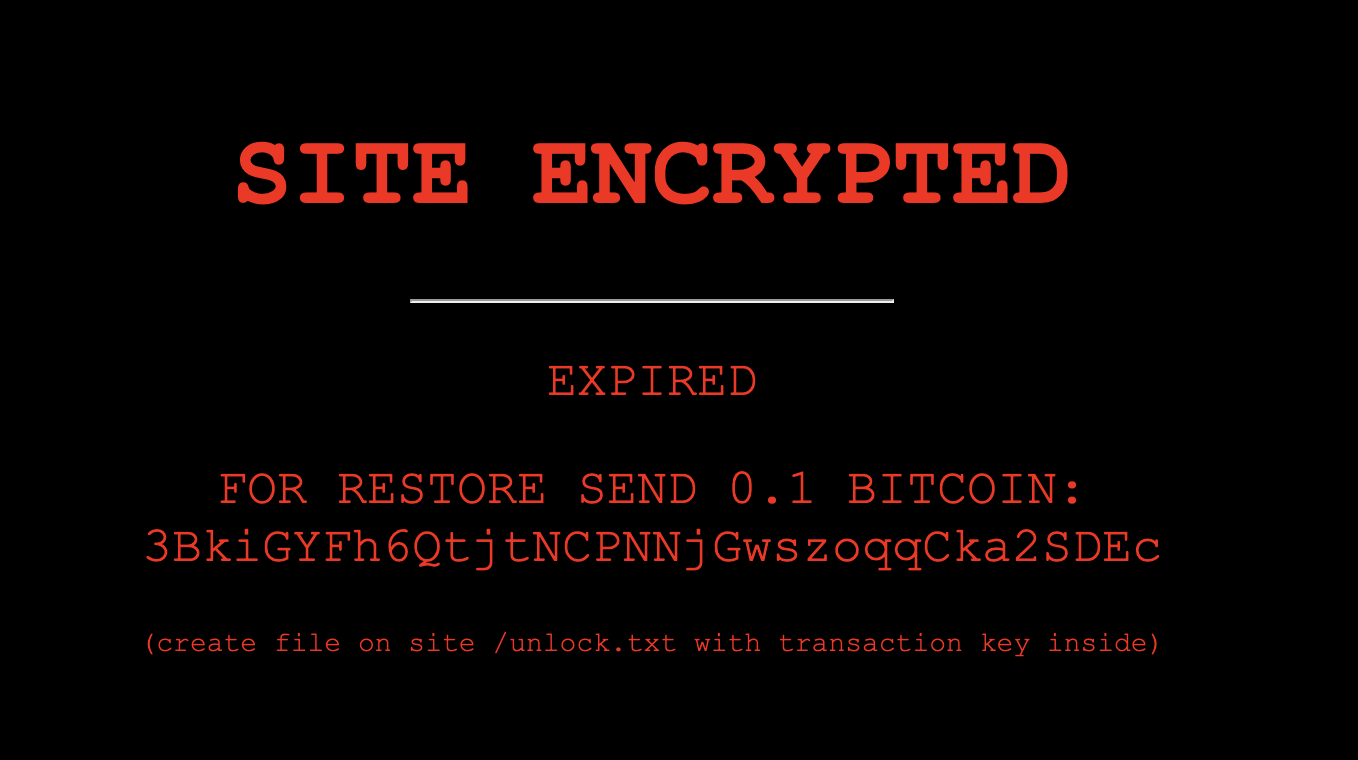
They’re successful far too often: The last quarter of 2020 saw by far the most ransomware, with attacks in November reaching an all-time high in an already record-breaking year. If 2021 follows suit, this could be the worst holiday season for ransomware SonicWall has ever recorded — but fortunately, there are many things you can do to minimize your risk:
It’s the Most Wander-ful Time of the Year: Travel Tips
Roughly 63% of American adults plan to travel for the holidays this year — a nearly 40% jump over last year, and within 5% of 2019 levels. While it’s easy to become preoccupied by traffic jams, flight delays and severe weather, don’t forget that attackers love to leverage this sort of chaos. Follow these five travel best practices to keep cybercriminals grounded this holiday season.
1. Free Wi-Fi =/= Risk-Free Wi-Fi
When you stop for a coffee during your layover, or stumble into a greasy spoon on hour nine of your road trip back home, you might be tempted to log on to the free Wi-Fi. But unless your organization has implemented zero-trust security, beware. Try bringing a novel and coloring books to keep everyone occupied on the road, and if you must connect, use a VPN to access employer networks and avoid logging in to your bank, email or other sensitive accounts. Because some devices may try to connect to these networks automatically, you may need to disable auto-connect to fully protect against man-in-the-middle and other attacks.
2. Put Your Devices on Lockdown
Due to border restrictions finally beginning to ease in countries such as Canada, Australia, India and South Korea, and the United States, international travel is expected to be robust. In the U.S., roughly 2 million travelers are expected to pass through airports each day over the Christmas holiday. In crowds like this, it’s easy for a device to be misplaced, left behind or stolen. To limit potential damage from smartphones, laptops, tablets, etc. falling into the wrong hands, ensure they’re protected with facial recognition, fingerprint ID or a PIN. (This doesn’t just protect against data theft, it can also help combat regular theft: One study found that locked devices were three times more likely to be returned to their owners.)
3. Don’t Let Criminals Track You
Nearly 43% of Americans and 42% of Brits feel more comfortable traveling this year — but this doesn’t mean they should be comfortable with everyone knowing they’re traveling. Any location data you share on social media can be tempting to those wanting to break into homes or hotel rooms — whether to steal and exfiltrate data, or steal gaming consoles, jewelry, medications or even gifts under the tree.
4. Use Only Your Own Cords/Power Adapters
In our mobile-dependent society, it’s no surprise that cybercriminals have learned how to install malware in airport kiosks, USB charging stations and more. And while that “forgotten” iPhone charge cable might look tempting when your device is running on empty, even those can harbor malware. If you can’t find a secure charging area, ensure your device is powered off before plugging it in.
‘Tis the Season for Giving: Online Safety Tips
Even if you’re not traveling this year, chances are you’re buying gifts. While supply-chain challenges, pandemic considerations and more have made for a unique holiday shopping season, it’s important to put safety first when shopping online. Here are six things to look out for:
1. Holiday Phishing Emails
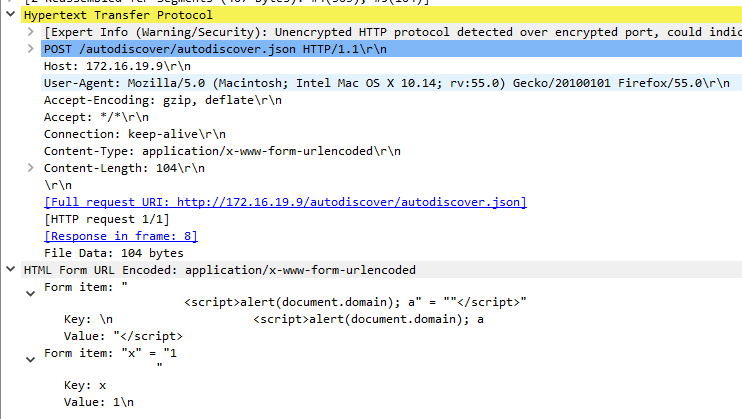
Perhaps you’ve received an invite to the Jones’ holiday party, a gift card or coupon, or an email from HR with details of an unexpected holiday bonus. If there’s an attachment, exercise extreme caution: It may harbor malware.
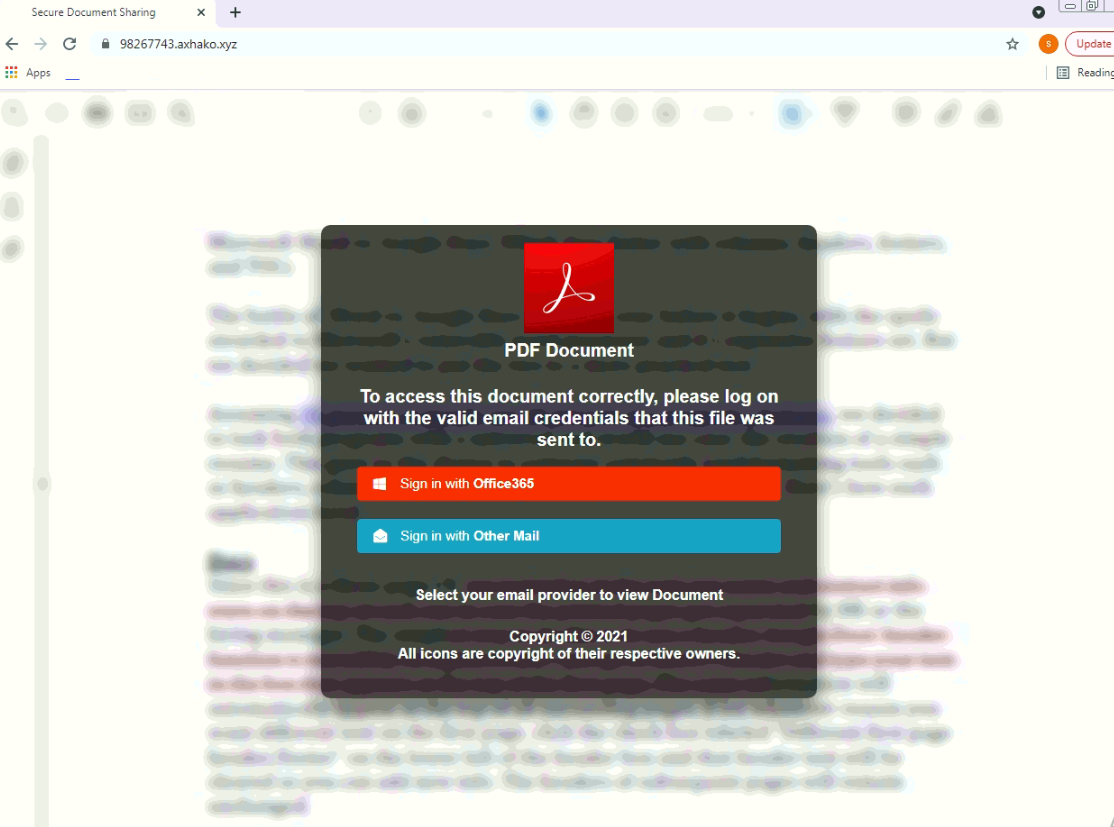
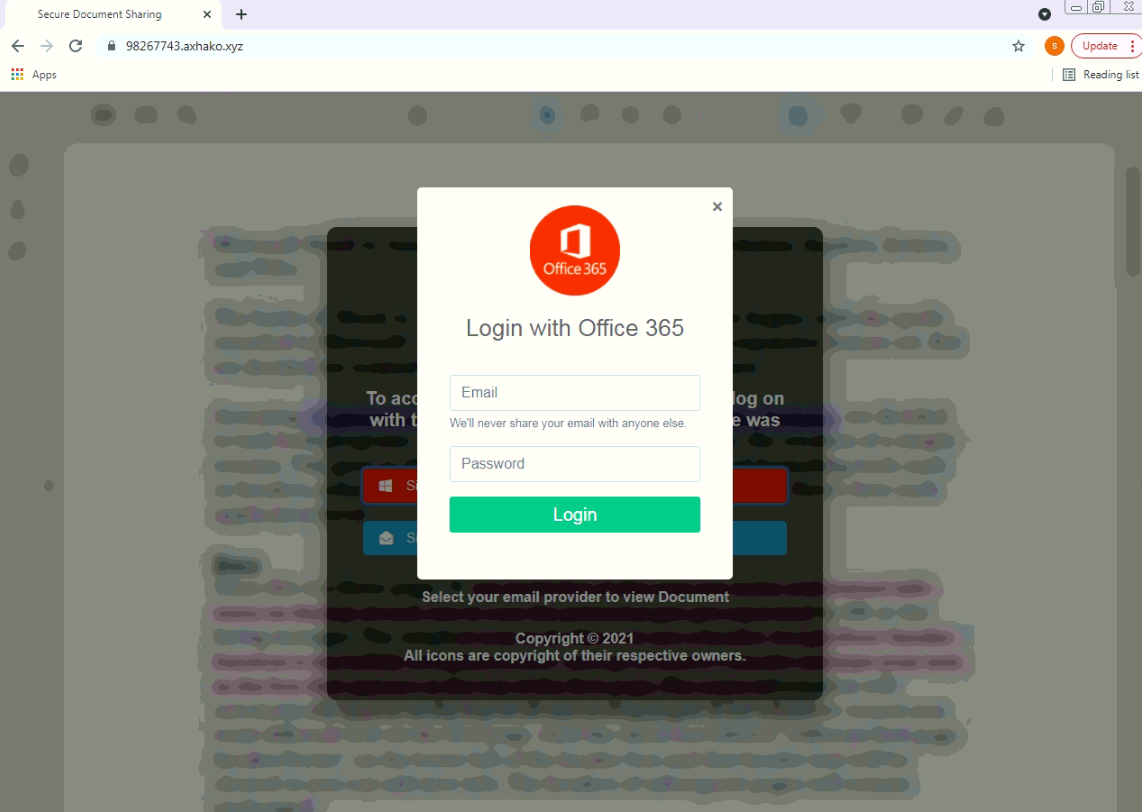
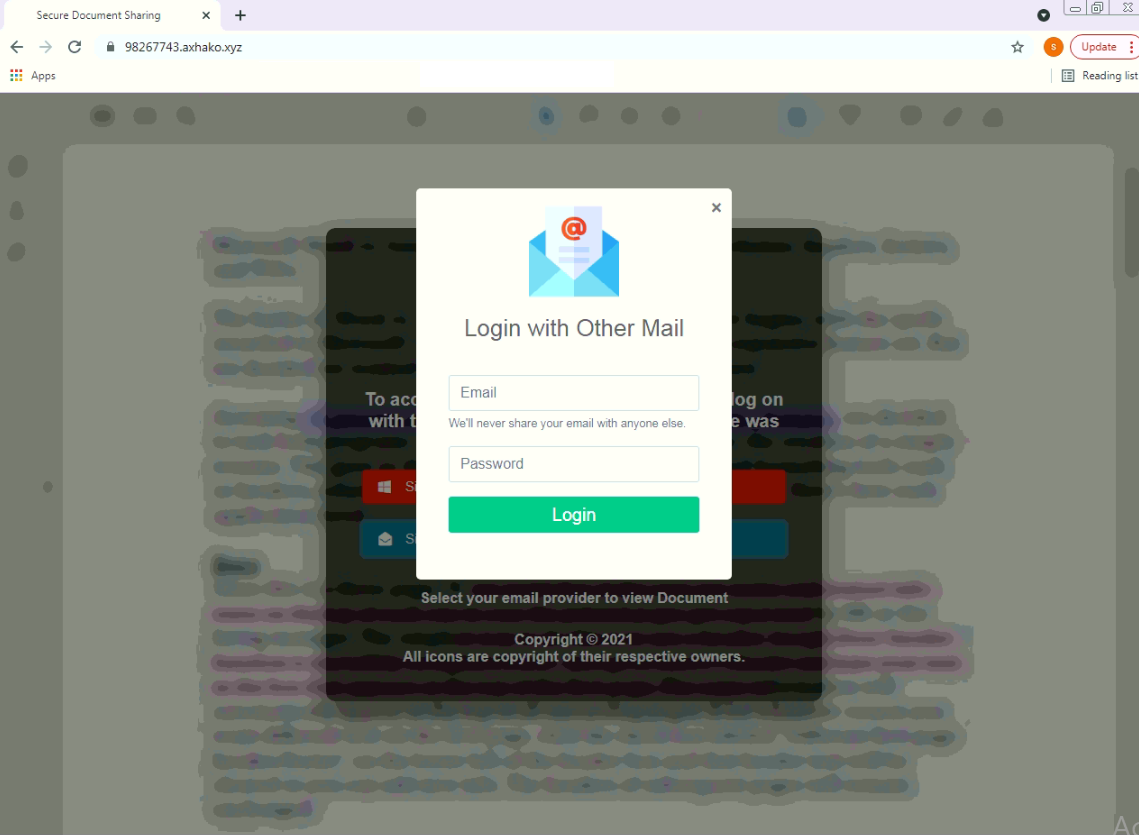
2. Spoofed Websites
Unfortunately for your wallet, emails boasting huge discounts at popular retailers are likely bogus. Walmart isn’t offering 70% off, and nobody is selling PlayStations for $100, not even during the holidays. If you enter your info into one of these lookalike retail (or charity) sites, the only thing you’re likely to get is your credentials stolen.
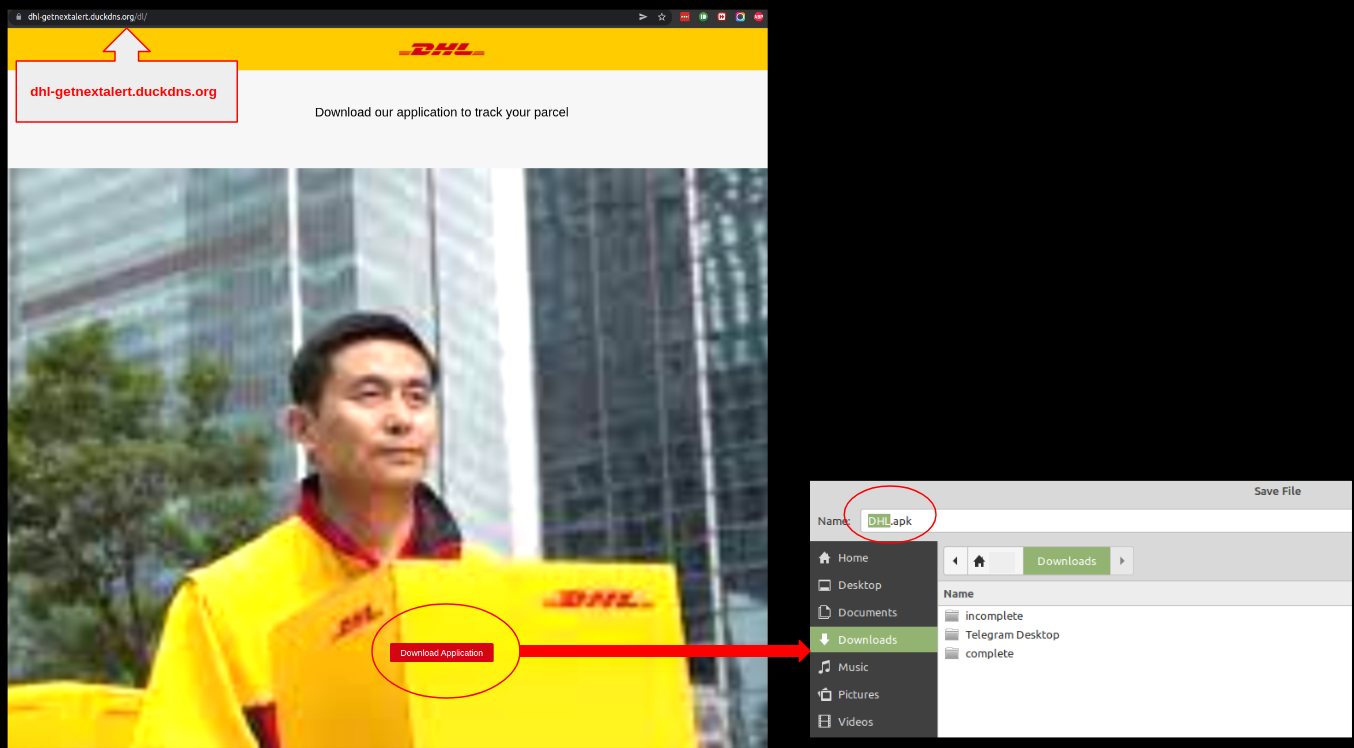
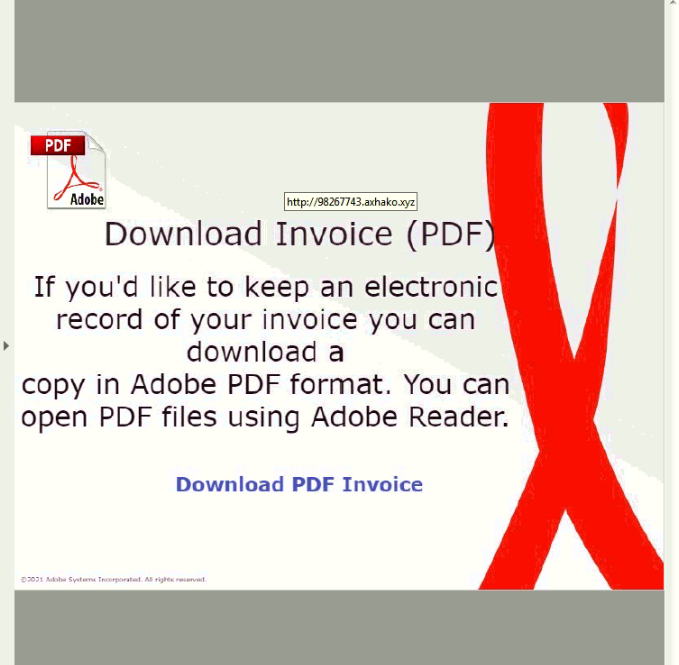
3. Fake Shipping Invoices
You’ve finished your shopping, and your gifts are on their way! But now FedEx is emailing to say your packages may not arrive in time and referring you to updated tracking information. Or your retailer is sending you a shipping label for returns, or verifying your gifts are being sent … to a completely different address. Look closely before you click: These emails usually aren’t from who they say they are.
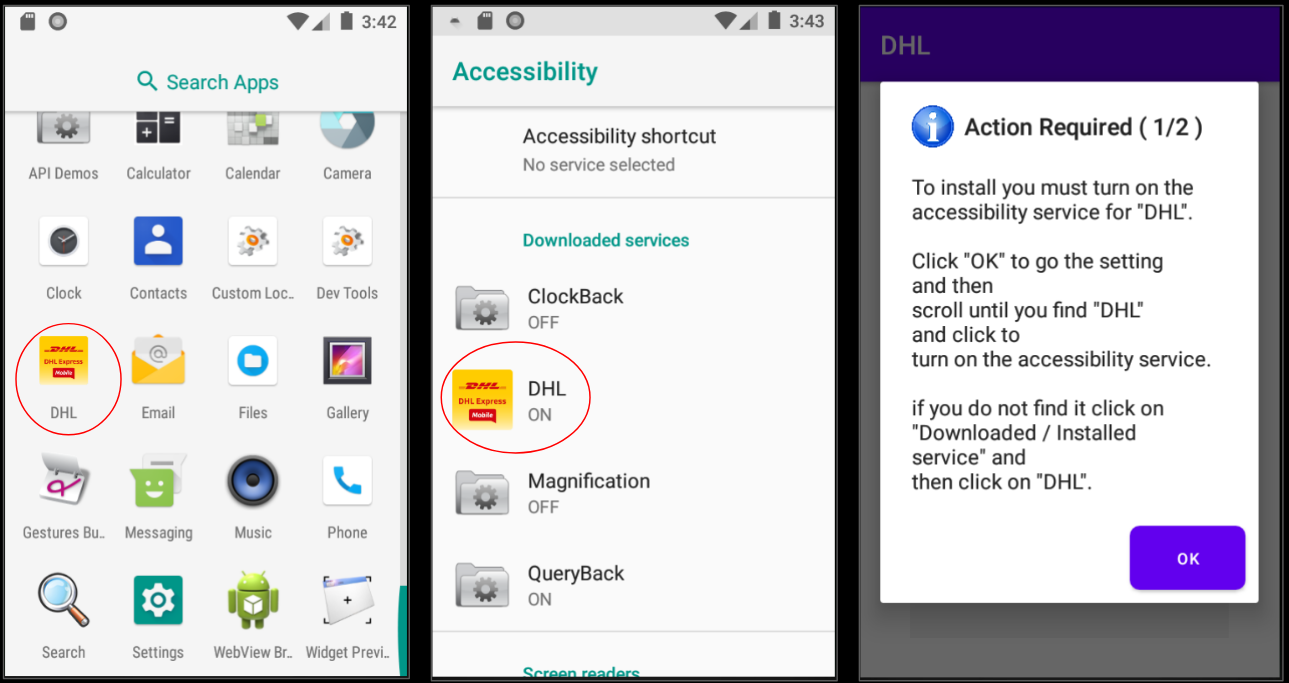
4. Counterfeit Apps
Is that really the Target app or just a lookalike? Better double-check before you download and enter your payment information. Apple’s App Store and Google Play have safeguards in place to stop counterfeit apps, but some still occasionally get through.
5. Gift Card Scams
These originally took the form of “You’ve won a free gift card! Click here to claim!” In recent years, however, they’ve become more targeted, and may appear to offer gift cards as a bonus from your employer or a holiday gift from a friend. The easiest way to avoid being scammed? If you weren’t expecting a gift card from someone, ask them about it.
6. Santa’s Little Helpers
There are many services designed to send your child a letter from Santa for a small fee. But many times, these so-called “Santas” are really cybercriminals attempting to get you to click on a link and enter your payment information. A recent variation has scammers offering kits designed to take the stress and mess out of your elf’s holiday shenanigans (just move your elf and call it good!)
While the holiday season offers more than its share of scams, many can be put on ice with a little extra due diligence. Keep these holiday best practices in mind, and have a safe and happy holiday!