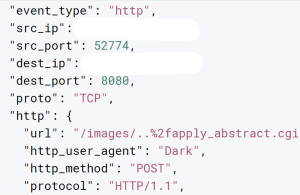
In August, the bipartisan U.S. Senate Committee on Homeland Security and Government Affairs released an update on the state of cybersecurity among federal agencies. The report, “Federal Cybersecurity: America’s Data Still at Risk,” noted that, even two years after a similar 2019 report revealed glaring cybersecurity shortcomings, there were still countless areas of concern.
Cybercriminals have always had an incentive to launch cyberattacks on the federal government, such as obtaining national secrets, disrupting a country’s operations at the highest possible level, and influencing politics. But now that they’ve been put on notice — twice — that launching a successful cyberattack might be far easier than they imagined, it’s no wonder we’ve seen attacks on federal, state and local governments rise at a pace far exceeding other industries.
Ransomware
As reported in the mid-year update to the 2021 SonicWall Cyber Threat Report, ransomware for the first half of 2021 increased an unprecedented 151% overall. But the increase in attacks for federal, state and local governments was actually much higher.
In the first half of 2020, there were 4.4 million attacks against government customers. During the same period in 2021, that number had risen to 44.6 million — a staggering 917% increase, the largest jump of any industry examined by SonicWall.
As if having government data encrypted wasn’t bad enough, many of these attacks employed a tactic known as double extortion in order to increase the likelihood the targets would pay. In such attacks, cybercriminals exfiltrate large quantities of data before encrypting files and issuing a ransom demand. Then, they use the threat of releasing this sensitive data as a sort of “insurance policy” in case the target has followed best practices such as keeping up-to-date backups, etc.
One such incident, in April 2021, targeted the Washington, D.C., police department. In this attack, the ransomware group threatened to share data about informants and other such sensitive information with local gangs if the department failed to pay the ransom demand.
A similar attack targeted the Illinois Attorney General’s Office. In February 2021, a state audit had warned the office that it lacked adequate cybersecurity protections. But the department failed to heed the recommendations, and two months later a ransomware group launched a double extortion attack, with some of the stolen data eventually posted online.
Cybercriminals have since evolved the malicious tactic to triple extortion, where payment is demanded from customers, partners and other third parties.
The number of ransomware attempts per customer remained far higher for government than for any other industry.
Cryptojacking
Very few cryptojacking incidents made the headlines in 2021. This is unsurprising for a couple of reasons: first of all, anyone targeting the federal government is likely to find much more profit in demanding ransom or stealing data than in mining cryptocurrency. Secondly, illegal mining’s impact on the government in 2021 hasn’t been nearly as newsworthy as government’s impact on mining. (In fact, bans on mining in China, Iran and elsewhere are largely cited as one of the reasons cryptocurrency prices fell from their record highs in April.)
Still, the numbers don’t lie, and according to SonicWall’s threat data for the first six months of 2021, the volume of attacks on federal, state and local governments isn’t just up — it’s way up.
Across all industries, the number of cryptojacking attacks in the first half of 2021 rose 23% year to date. But for government customers, cryptojacking attack volume rose a whopping 329%.
IoT Attacks
In August, CISA issued an advisory about a public report detailing vulnerabilities in multiple real-time operating systems (RTOS). Known as “BadAlloc,” the report details a number of vulnerabilities in IoT devices that affect “a variety of sectors for every aerospace, robotics [and] rail industrial control system,” according to Vincent Sritapan, Cyber Quality Service Management Office Chief at CISA.
Unfortunately, attacks on similar systems have already been occurring. In February, an attacker took control of the Oldsmar, Fla., water supply, increasing the amount of sodium hydroxide, or lye, in the water to 110 times normal levels.
SonicWall threat research data indicates that IoT attacks on federal, state and local governments are rising — but the good news is that they seem to be rising more slowly than attacks as a whole. While the number of IoT attacks recorded overall in the first half of 2021 rose 59% year over year, for government customers, attack volume rose only 17% — not good news, per se, but better than it could be considering this attack type’s potential for disruption.
While it’s too early to say what the second half of 2021 will hold for government customers, a lot of it will depend on how federal, state and local governments and agencies respond to warnings like the one issued in August. If we see renewed efforts among these organizations to adhere to cybersecurity best practices, some of these trends may begin to slow or even reverse.
Otherwise, we’re likely to see an increase in the sorts of attacks that have dominated headlines recently, as cybercriminals increasingly shift to targeting the biggest game of all.
In the meantime, you can access all of SonicWall’s first-half threat data — including location-specific information and data on other industries and threat types — by downloading the mid-year update to the 2021 SonicWall Cyber Threat Report.