According to a report in The Journal, as of early August, more than 60% of parents were hesitant to send their children back to school this fall due to a large uptick in pediatric COVID-19 cases. As we have seen since, many of these fears were well-founded, as schools in Texas, Georgia, Florida, Tennessee and elsewhere have been forced to close almost as quickly as they opened due to widespread exposures, quarantines and staff shortages.
This unpredictable and ever-shifting education landscape has wreaked havoc on a back-to-school season that was once expected to herald a return to normalcy. But unfortunately for school leadership and IT administrators already dealing with a learning environment subject to change from day to day, this level of upheaval and uncertainty has historically been compounded by another crisis: cybercrime.
Toward the beginning of the pandemic, attacks on K-12 schools and higher education began rising as hackers realized that schools were frequently both overwhelmed and underprotected.
“K-12 institutions have limited resources to dedicate to network defense, leaving them vulnerable to cyberattacks,” the FBI warned in an alert sent in late June 2020.
It’s been more than a year since that initial report — enough time to collect the sort of data needed for an apples-to-apples comparison of 2020 and 2021. Unfortunately, as reported in the mid-year update to the 2021 SonicWall Cyber Threat Report, even as schools have reopened, any expected reprieve has remained elusive. Almost every type of cyberthreat against education has continued to rise drastically in the first half of 2021, painting a frightening picture of what might lie ahead as our K-12 and higher-education institutions face increasing challenges.
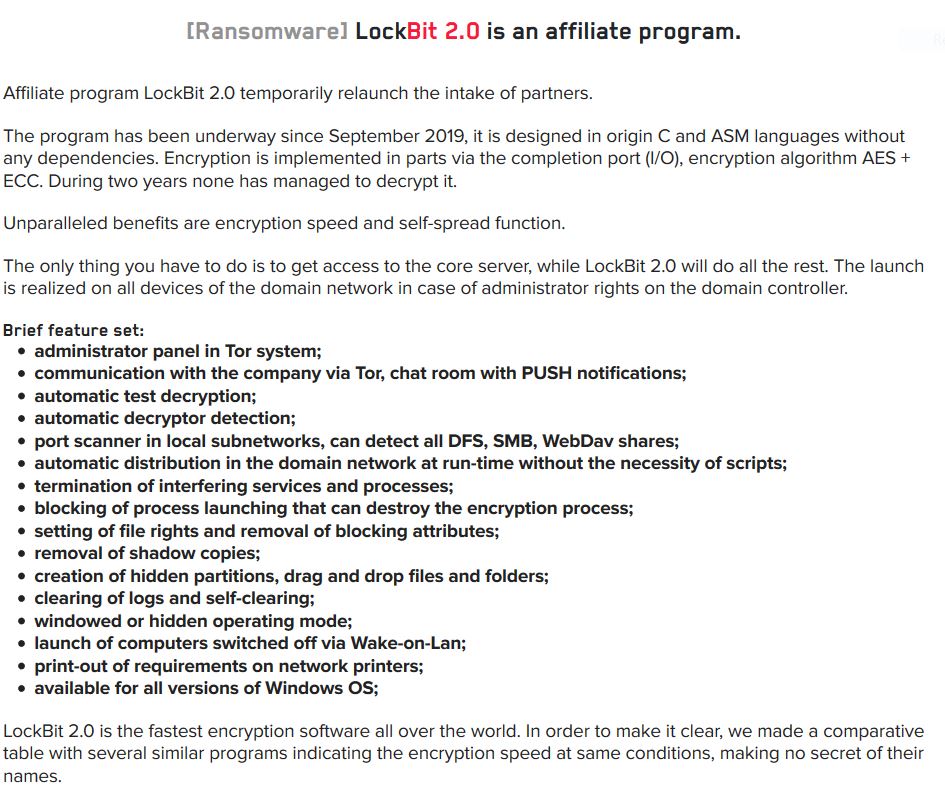
Ransomware
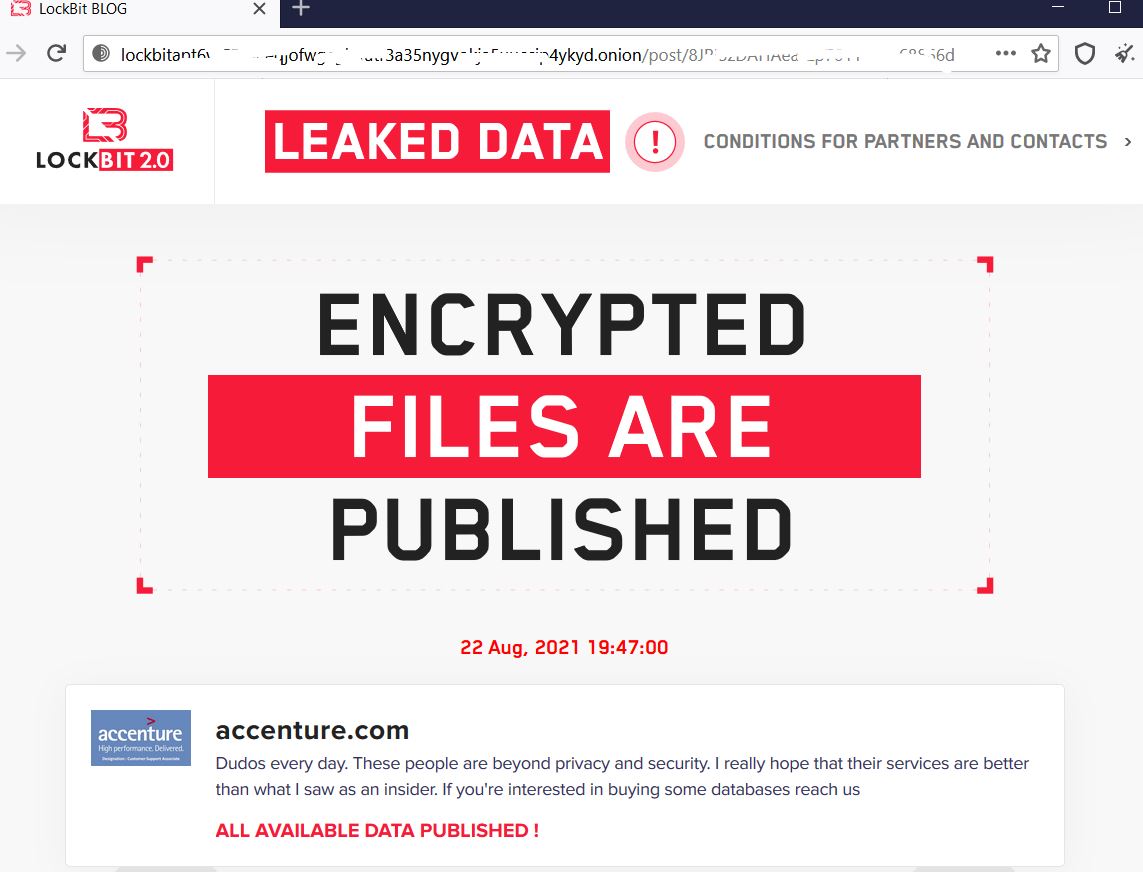
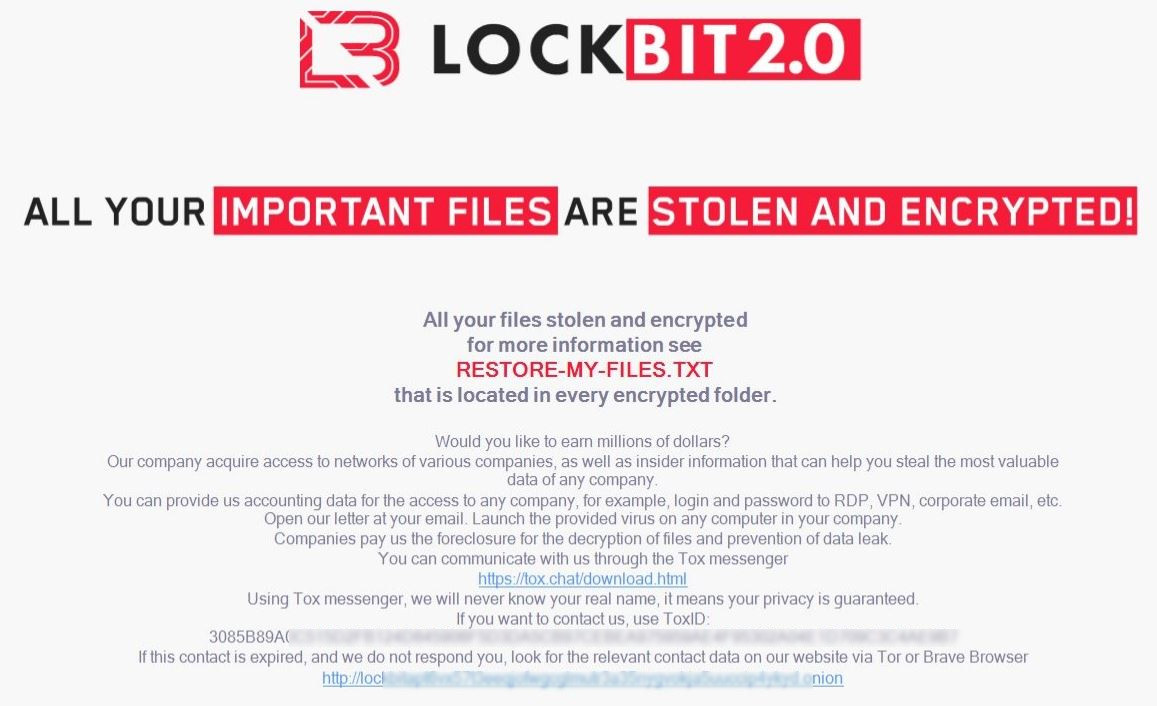
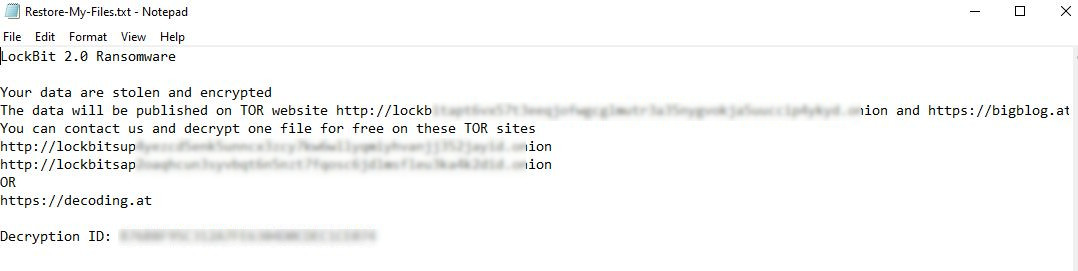
In April 2021, Broward County Public School District, one of the largest in the U.S., received a ransom demand of $40 million, the second-highest to date. To help ensure they received payment, the criminals threatened to publish student and employee data online — an increasingly popular tactic among cybercriminals known as “double extortion.”
But while this may be an extreme example, it represents a trend of increasingly audacious demands on schools. And as more schools show a willingness to pay at least something, the number of attacks has begun to rise even faster.
In the first half of 2020, SonicWall threat researchers recorded 1.4 million ransomware attacks on K-12 and higher education institutions. By the first half of 2021, this number had risen to 10.1 million — an increase of 615%.
As observed by SonicWall, education was top vertical targeted by ransomware in three of the first six months of 2021.
IoT Attacks
When students and teachers made the shift to online learning in early 2020, they introduced millions of new devices to the network, widening the attack surface considerably.
Mirroring the trends we saw among organizations as a whole, IoT attacks rose over the course of 2020, as cybercriminals recognized an opportunity to access unprotected or inadequately protected networks.
While IoT attacks in general rose 59% in the first half of 2021 over the same time period in 2020, those in education saw an even larger jump, despite the fact that many students had returned to in-person classes. Among schools and colleges, IoT attacks rose 78% year-to-date — a gap we may see continue to widen if more students are sent home for remote learning.
Cryptojacking
In April 2021, Washington educational organizations discovered that they’d been hit by a cryptojacking attack dating back to at least February. Given what was happening in the crypto market at the time, the timing was unsurprising: Cryptojacking is largely tied to the price of cryptocurrency, and in early 2021, cryptocurrency was soaring to record highs.
But in late spring, amid warnings of increased tax enforcement on cryptocurrency earnings and news of mining bans in China and elsewhere, the prices of cryptocurrency — and cryptojacking — crashed hard.
For schools, which saw a mind-boggling 1,917% increase in the number of cryptojacking attacks in the first half of 2021 over the first half of 2020 (versus a 23% increase among organizations as a whole), this was welcome news. But with the prices of most cryptocurrencies continuing to rebound, it’s possible we could see a sustained rise, rather than a drop, once the data from the second half of 2021 is in.
In March 2021, the K-12 Security Information Exchange and the K-12 Cybersecurity Resource Center released a report stating, “The 2020 calendar year saw a record-breaking number of publicly-disclosed school cyber incidents,” with many of these incidents “resulting in school closures, millions of dollars of stolen taxpayer dollars, and student data breaches directly linked to identity theft and credit fraud.”
Unfortunately, as the data from the first half of 2021 shows, attacks on K-12 and higher education institutions have only risen since then. While government programs such as the CARES Act, ARP and more will certainly help, unless we see sustained investment in cybersecurity in the coming years, K-12 and higher education will likely continue to be targeted.