Hafnium Uses Zero-Day Vulnerabilities Against Microsoft Exchange: What to Do Next
While the industry is still reeling from the impacts of the SolarWinds Orion supply-chain attack, another salvo has been launched at the already burnt-out response teams.
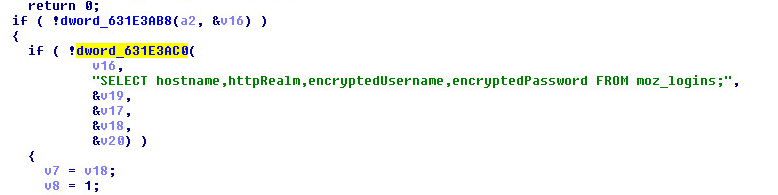
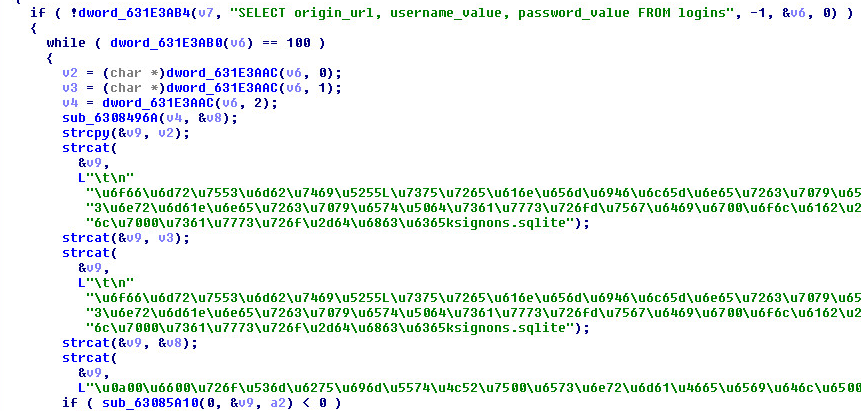
Researchers at DEVCORE discovered and reported several vulnerabilities in Microsoft Exchange Server software, dating back to Server 2010, that when chained together result in pre-authentication remote code execution capabilities.
If you have an on-prem Microsoft Exchange Server, patching it and ensuring that your system has not been compromised should be your absolute top priority.
“Microsoft has detected multiple zero-day exploits being used to attack on-premises versions of Microsoft Exchange Server in limited and targeted attacks,” Microsoft stated in a real-time blog used to communicate mitigation steps. “In the attacks observed, the threat actor used these vulnerabilities to access on-premises Exchange servers, which enabled access to email accounts and allowed installation of additional malware to facilitate long-term access to victim environments.”
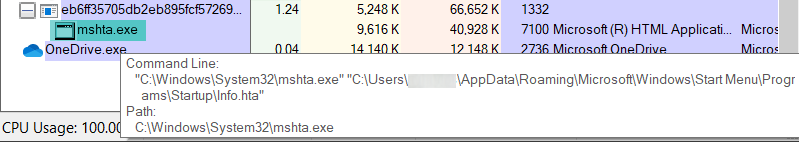
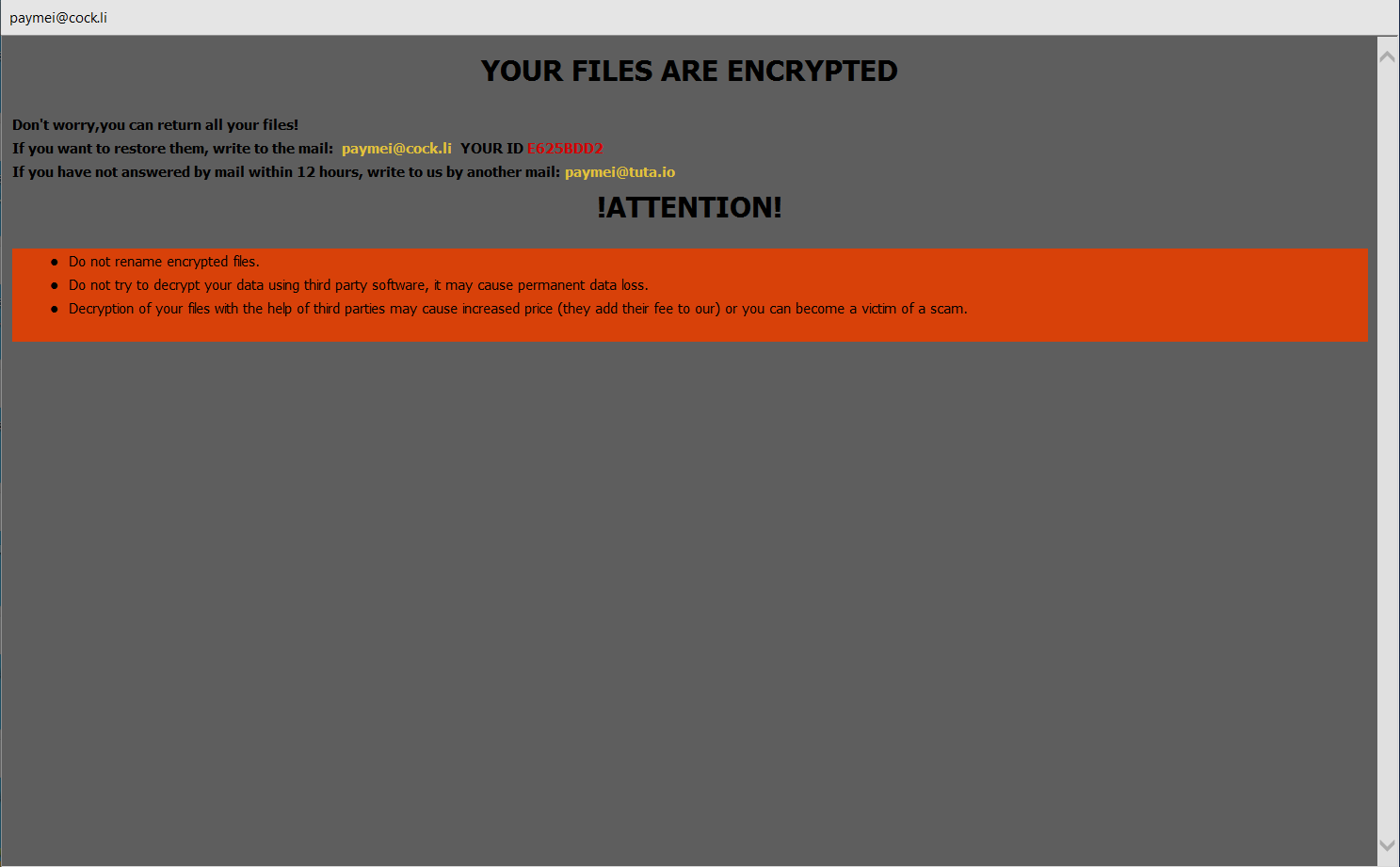
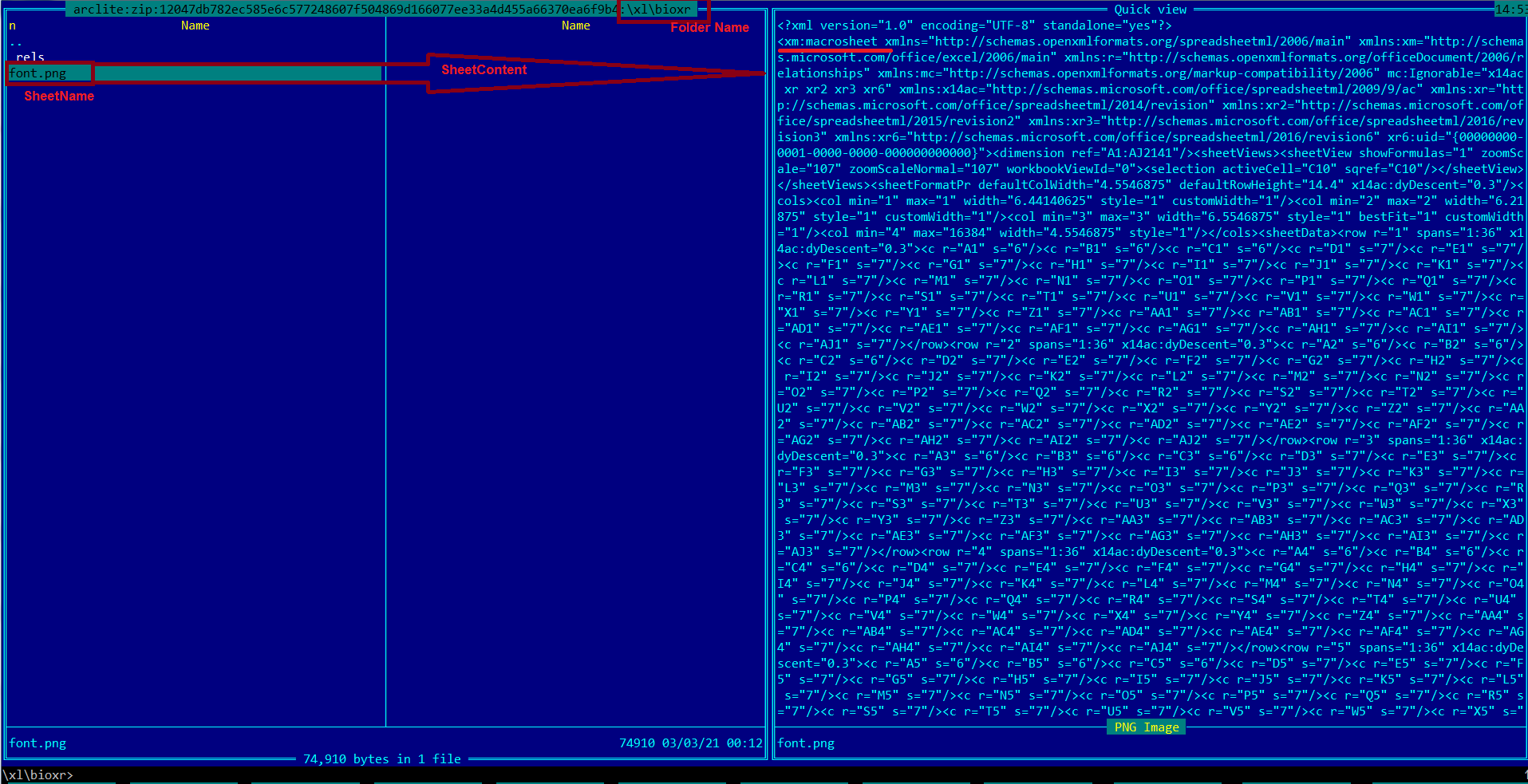
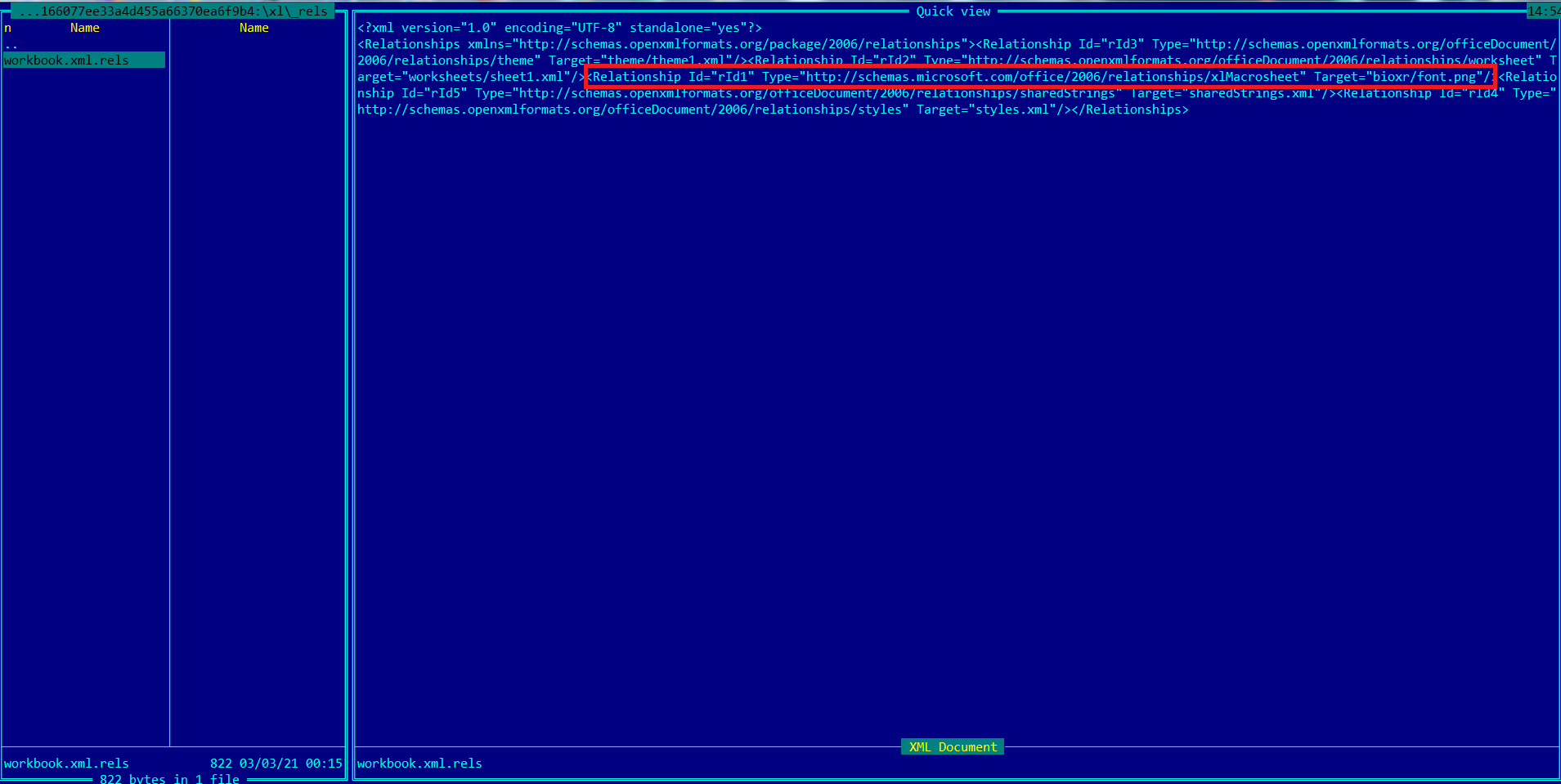
According to Microsoft, Hafnium exploited these vulnerabilities to gain initial access, then “deployed web shells on the compromised server. Web shells potentially allow attackers to steal data and perform additional malicious actions that lead to further compromise.”
How do I prevent Exchange Server attacks?
First, immediately patch your Exchange Server. Even though Exchange Server 2010 is in End of Life (EOL), Microsoft also released a “Defense in Depth” update for Exchange Server 2010.
To protect customers, SonicWall released four IPS signatures to defend against potential attacks that exploit the outlined vulnerabilities:
- IPS: 15418 WEB-ATTACKS Microsoft Exchange Server Remote Code Execution (CVE-2021-26857)
- IPS: 15419 WEB-ATTACKS Microsoft Exchange Server Remote Code Execution (CVE-2021-26855) 1
- IPS: 15420 WEB-ATTACKS Microsoft Exchange Server Remote Code Execution (CVE-2021-26855) 2
- IPS: 15421 WEB-ATTACKS Microsoft Exchange Server Remote Code Execution 1
To be effective, server-side DPI-SSL must be enabled for incoming traffic in order to intercept these attacks, since they’re inside of HTTPs traffic. The following KB article provides step-by-step guidance on configuring DPI-SSL capabilities: How To Configure Server DPI-SSL.
You may also enable Geo-IP blocking on the firewall to restrict traffic to your geographic region only, although you should not rely on this measure since Geo-boundaries can be easily bypassed by attackers staging attacks from VPN or TOR services.
Who is Hafnium, and why are the Exchange Server vulnerabilities so critical?
While RCE vulnerabilities are always of top concern, what’s worse is that there’s an ongoing mass exploitation campaign underway, which may result in network persistence by attackers. The group behind the mass exploitation is dubbed Hafnium and is believed to be operating out of China.
The vulnerabilities are so concerning, government officials were warning of the ramifications.
“This is a significant vulnerability that could have far-reaching impacts,” said U.S. White House Press Secretary Jen Psaki during a March 5 briefing. “First and foremost, this is an active threat. And as the National Security Advisor tweeted last night (below), everyone running these servers — government, private sector, academia — needs to act now to patch them … We are concerned that there are a large number of victims and are working with our partners to understand the scope of this.”
We are closely tracking Microsoft’s emergency patch for previously unknown vulnerabilities in Exchange Server software and reports of potential compromises of U.S. think tanks and defense industrial base entities. We encourage network owners to patch ASAP: https://t.co/Q2K4DYWQud
— Jake Sullivan (@JakeSullivan46) March 5, 2021
While the breach has impacted an estimated 60,000 victims worldwide so far, threat actors also appear to have found a way to automate the attack process, allowing them to target a massive number of victims in a very short period of time.