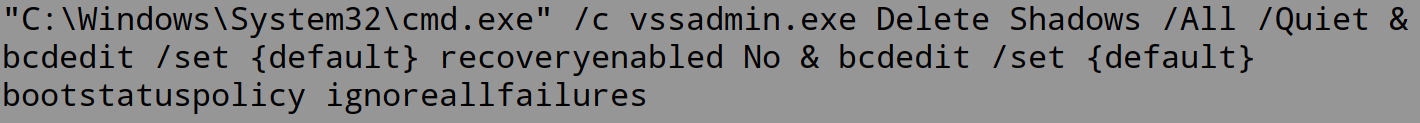
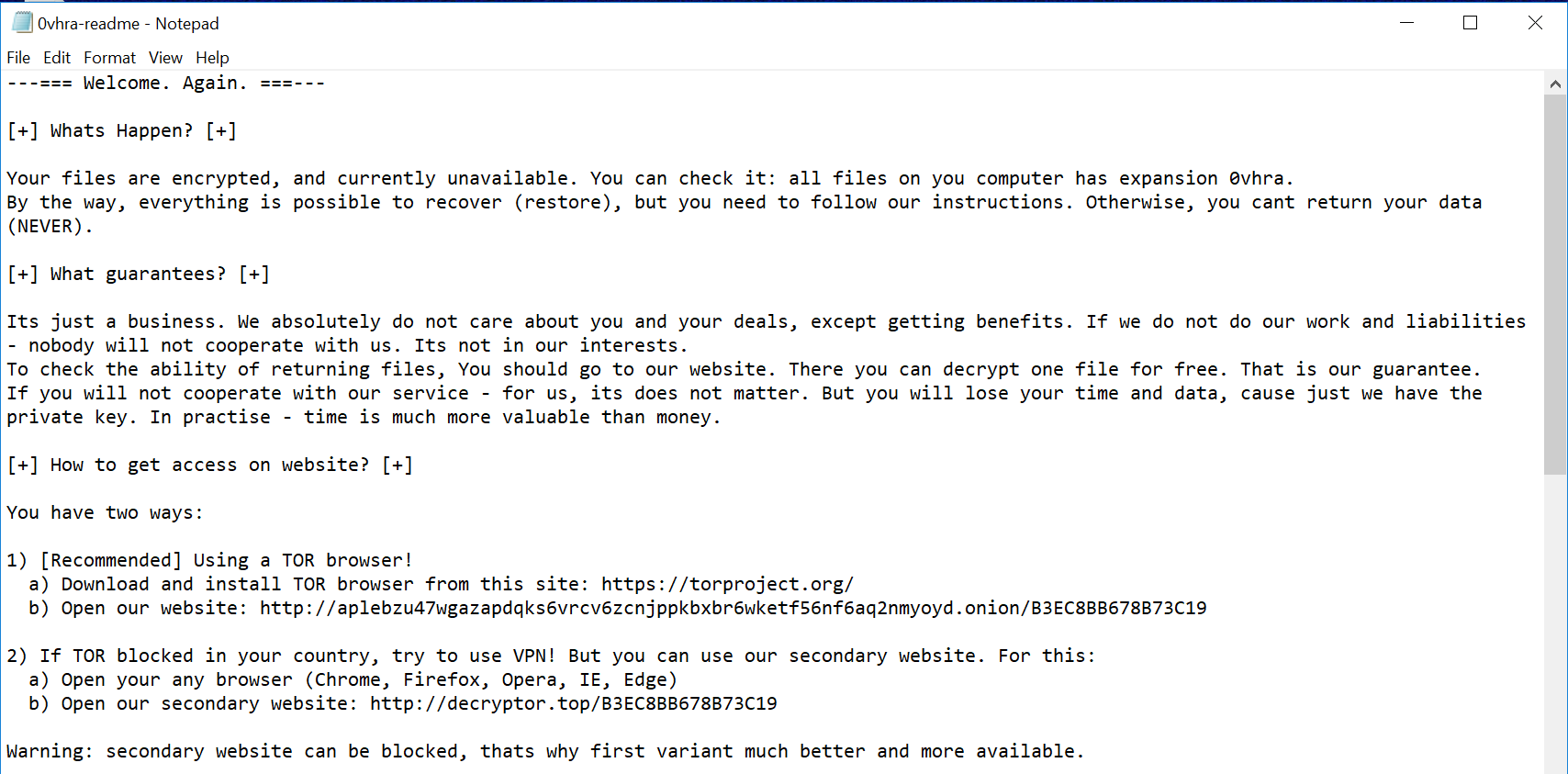
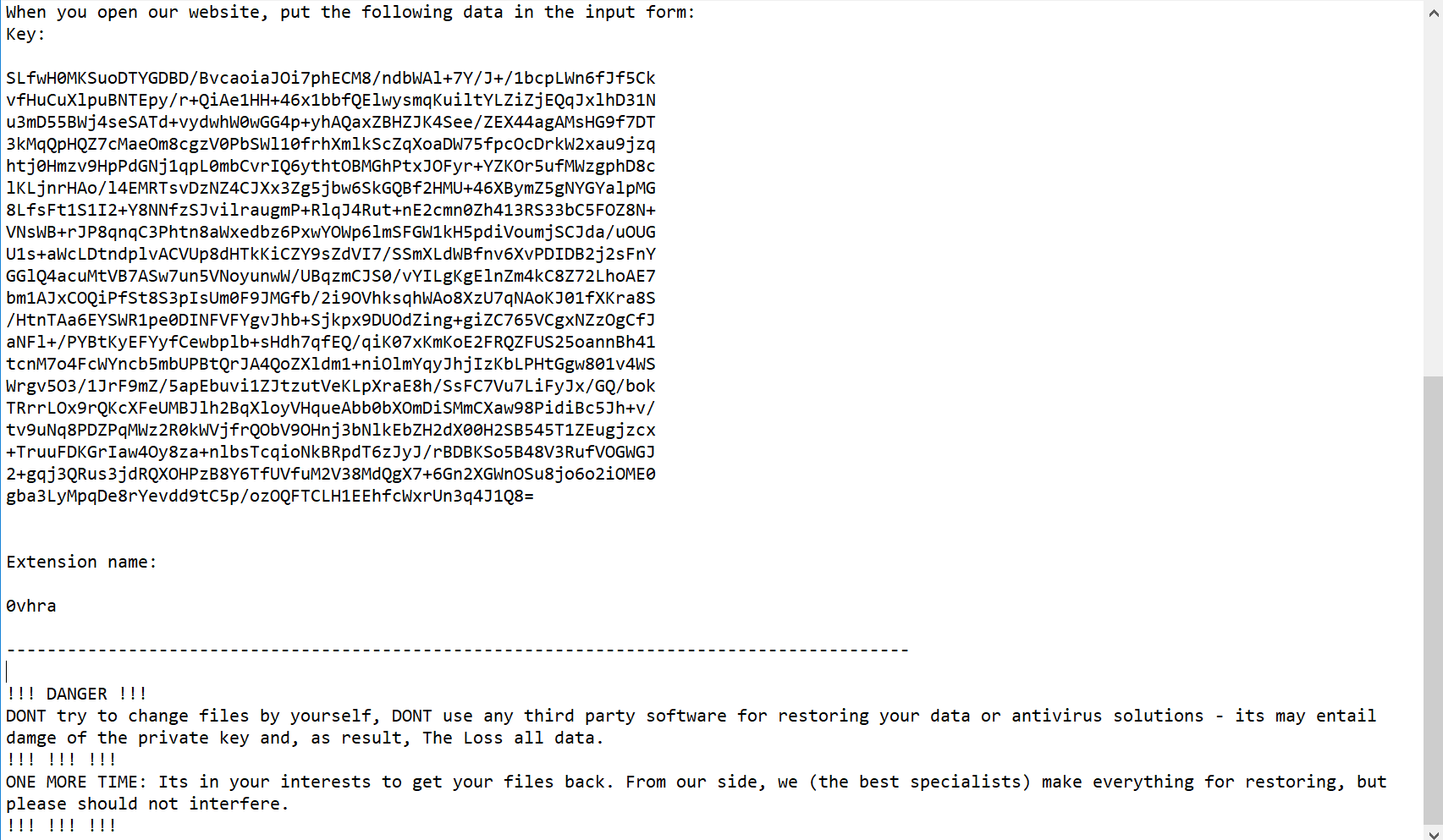
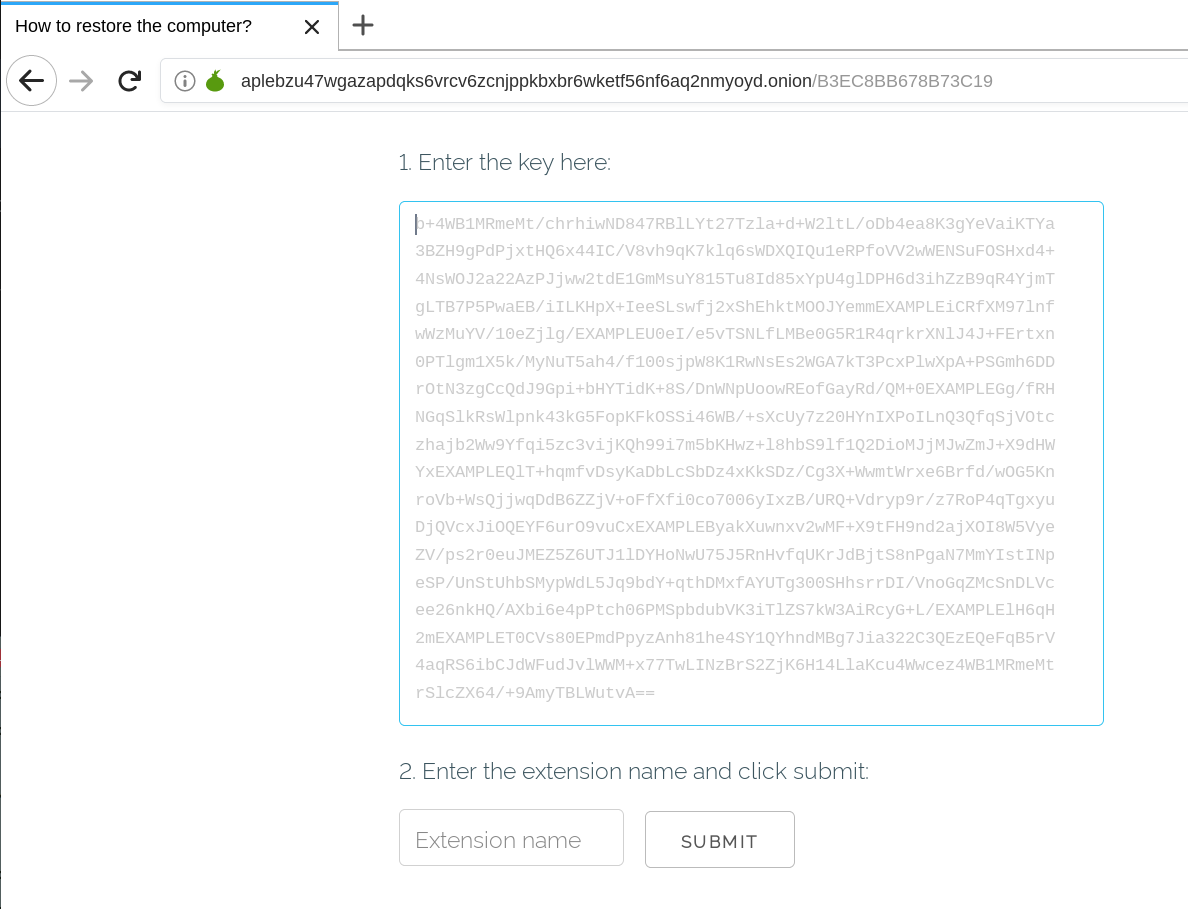
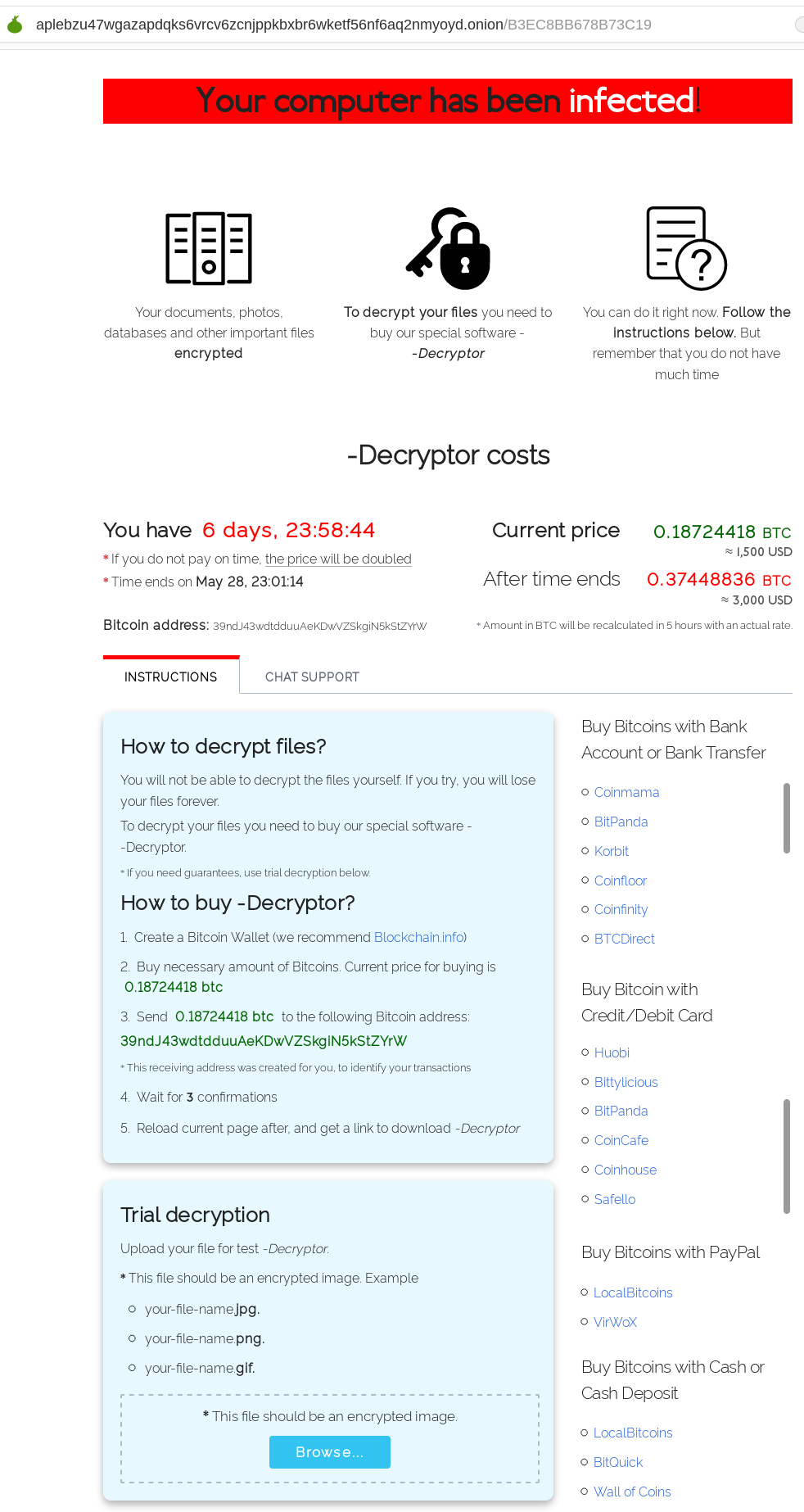
Participating in your first E-rate season can be overwhelming. It is important to understand eligibility requirements of the program since the forms and terminology can become confusing. To better understand the ins and outs of the E-rate program, watch Episode 2 of the SonicWall E-rate video series below.
Episode 2: Navigating the E-rate Program
On the second episode of the E-rate Fear Less series, Komplement CEO Holly Davis highlights key elements of the E-rate program to help you navigate the process. You will learn about the filling cycle, ESL, 470 and 471 forms, and rules of the program.
Before you get started, it’s important to remember some key dates. First, the E-rate program operates on a fiscal year (FY) calendar. This year, FY2020 is July 1, 2019, to June 30, 2020. From here, there are two primary dates to remember:
- 470 Filing: July 1, 2019 (RFP Posting)
- 471 Filing: January 11, 2020-March 22, 2020
Each year, before the FCC Form 471 application filing window opens, the FCC releases Eligible Services List (ESL) for the upcoming funding year (it is typically released between September and November).
The ESL contains a description of the products and services that will be eligible for discounts, along with additional helpful information such as eligibility conditions for each category of service for each specified funding year.
Be sure to review the list before you post a form 470 request for services to properly align your products and service needs.
SonicWall and E-rate
Through its global channel of more than 23,000 technology partners, SonicWall is actively involved in helping K-12 education organizations cost-effectively obtain and deploy network security solutions. SonicWall provides a broad array of E-rate-eligible products and services, including firewalls and turnkey Security-as-a-Service solutions.
SonicWall can discuss its products and services prior to the posting of a school/library Form 470, which begins the competitive bidding process. Once Form 470 is filed, SonicWall and its partners are restricted to rules and regulations of the program and are respondents to the bidding.
If you are utilizing E-rate funding to assist you in buying your networking and cyber security solutions, SonicWall can help. Our team of E-rate funding experts ensure your SonicWall solution aligns with the rules and regulations of the E-rate program. SonicWall provides services in the following areas:
- Managed Internal Broadband Services
- Internal Connections
- Basic Maintenance for Internal Connections
SonicWall integrated solutions meet the needs of school districts at the highest efficacy and at price points that fit within K-12 budget constraints. SonicWall helps reduce the total cost of ownership (TCO) for these under-funded organizations.
If you are an eligible K-12 organization, please contact your preferred SonicWall reseller for information on E-rate benefits and discounts, or visit the SonicWall E-rate page for information, tools and guidance.
What is E-rate?
To help offset funding and staffing shortages, the U.S. Department of Education and the FCC launched the E-rate program, which helps make telecommunications and information services more affordable for schools, campuses, districts and libraries.
“Eligible schools and libraries may receive discounts on telecommunications, telecommunications services and internet access, as well as internal connections, managed internal broadband services and basic maintenance of internal connections,” explains the FCC website. “Discounts range from 20 to 90 percent, with higher discounts for higher poverty and rural schools and libraries. Recipients must pay some portion of the service costs.”
The E-rate program is operated by Universal Service Administration Company (USAC), which has a core focus of providing underfunded verticals the access to affordable technology and security services. This includes schools, libraries, rural healthcare organizations and more.
USAC provides a yearly Eligible Services List (ESL), which outlines which types of products and services can be procured via E-rate program discounts.
E-rate Episode Video Series for K-12 School Districts
Webinar: How K-12 Districts Use Wireless Security to Protect Students, Faculty and Staff
Safeguarding K-12 networks is a delicate yet critical undertaking. Register for our unique webinar, which brings together a panel of experts from security, networking and education to outline how districts can expand wireless security to the edge — even without firewalls.
REGISTER NOW