Beginning of new malicious campaign through fake apps targeting Indian android users
SonicWall Capture Labs Threats Research Team identified few fake apps that have a worm-like spreading capability via WhatsApp messages. These applications were not seen to be present on the Play Store, based on our analysis these apps spread via WhatsApp messages or from third party app stores.
Initial Observations
During installation, these fake apps request following permissions:
- ACCESS_COARSE_LOCATION
- INTERNET
- READ_CONTACTS
- READ_PHONE_STATE
- READ_SMS
- SEND_SMS
- WRITE_EXTERNAL_STORAGE
- ACCESS_NETWORK_STATE
- ACCESS_WIFI_STATE
- READ_EXTERNAL_STORAGE
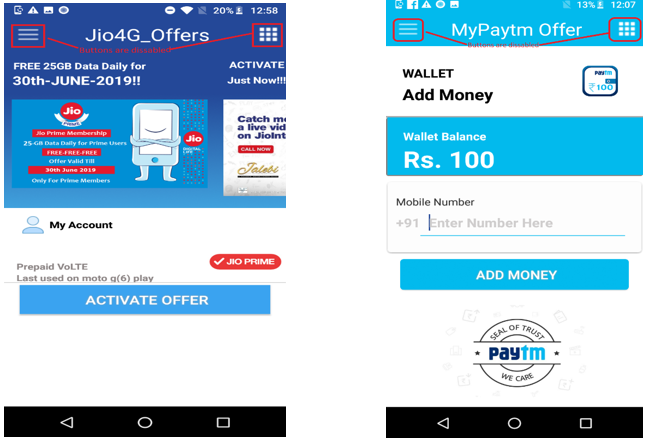
These applications use the icons, images and initial functionality of popular Indian Android applications namely Jio and Paytm. These factors indicate that this campaign is mainly targeting applications used in the Indian market with attractive promotional offers.
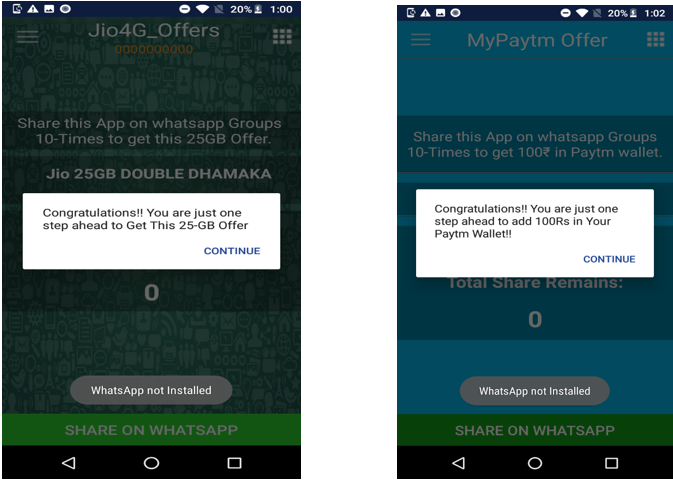
Below images show the applications post installation on the device:
As can be seen below, the navigation buttons on the top left corner in these apps are disabled (not clickable).
Functionality
Once installed the user is shown offers in the form of a popup. To avail the promotional offer, the user need to provide a 10 digit mobile number. Legitimate applications usually validate the user mobile number via either OTP or some other mechanism. On the contrary, these applications do not even care to validate the mobile number. The app accepts the number and direct the user to follow process to avail the offers.
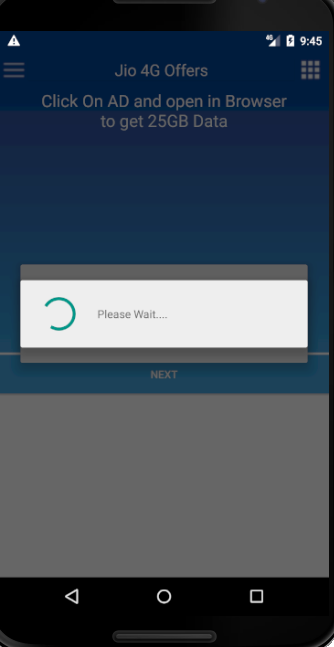
In the background, the app sends user’s device information like location, IMEI number, Service provider, device manufacturer name to a remote server (hxxp://global.appnext.com). This data is used later to display advertisements.
Spreading capability
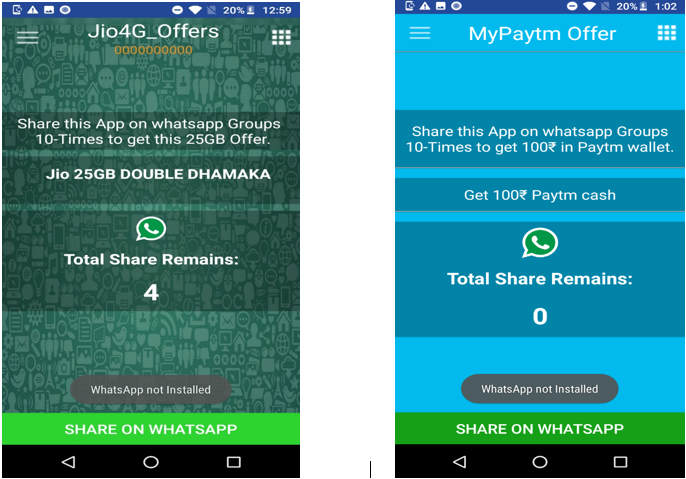
To increase distribution, the app requests the user to share download link over WhatsApp to at-least 10 of the contacts
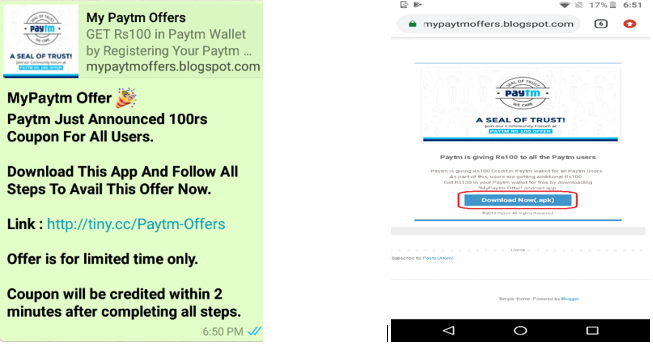
On clicking the “SHARE ON WHATSAPP” button, below message is sent to the contacts chosen by the user. Fake App (Jio or Paytm offer) download link is also present in the message.
Even in the absence of WhatsApp on the user’s device, the share count could be reduced to zero by clicking the “SHARE ON WHATSAPP” button as shown below:
After the count approaches zero, the user is displayed congratulatory message and informed about the steps remaining to avail the offer.
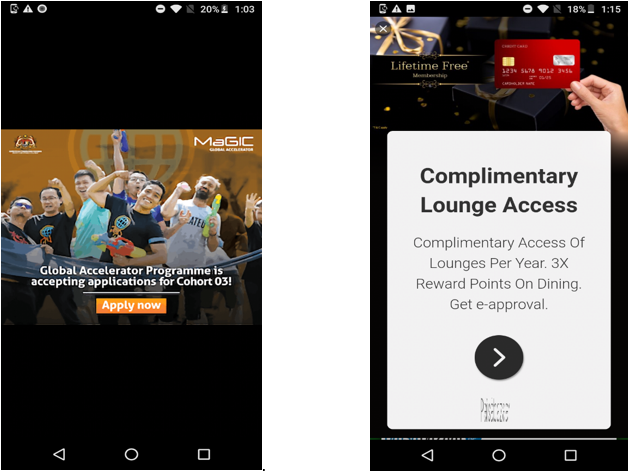
The offer now appears to be a distant dream when the user is asked to click on advertisements. To monetize, random advertisements are displayed in the web browser, which keep changing at regular intervals.
The back navigation button is rendered non-functional. The user has to either kill the app or press the home button to come out of the application.
Few Indicators to identify fake apps
- Look and feel of the app is similar to the actual JIO and Paytm applications but none of the controls in the application work. (Navigation bar on top left corner is disabled)
- Lack of user input validation.
- Inappropriate use of messaging apps like WhatsApp.
- Enable the Unknown Sources setting to install the app.
SonicWALL Capture Labs provide protection against this threat via the following signature(s):
- AndroidOS.FakeAd
Indicators of compromise:
op.voiice.a4g.anew.new4gvoicev – 7091d3b58d9680ab257ba328048d1e4142bbbade4e424062a1ed6af26b92005b
bhadva.chromva.jio4goffers – 7fb502ce2f6c8edcd4a801eeee4393c2b27d4988a7e1261df98facc7c72868ed
op.voiice.a4g.anew.new4gvoicev – 8c393609732d6f8cf2e10a75aebed11f3a869791461469a9a9927f8a77be94ed
bab.navi.newnavi – 9c574a77979532eb36c602b73cab9c627c79af38f9331736beba59a82d984d81
bhadva.chromva.jio4goffers – 991b4ded04820306eb59e3086c967e7473b5f547b0a0c1003ca3347a84b4bef6
bhadva.chromva.jio4goffers – d3d8a1505549d876dbf95df8b00f623cd3074873231b3374a7dd7812de8ecc06
sdffn.bobl.offerva.myjio_offers – daa7b780e7a2be97378f16376e89e9adc34e7cebb3a1d1e95f82e654a88bd83a